Application Control
An overview of the application control features in Cisco Secure Firewall
Application Control Overview
The Cisco Secure Firewall Threat Defense (FTD) provides multiple means of controlling and providing visibility to network applications. The system currently identifies nearly 6,000 specific applications. To view the current list of application detectors, visit: https://appid.cisco.com/home. Application traffic can be allowed, blocked, or passed on for deep packet analysis by the system’s Snort inspection technology. In addition, specific file types can be allowed or blocked for various application protocols.
Customers can target and exclude specific application traffic from SSL/TLS decryption. The system can even identify client applications in encrypted traffic based on proprietary fingerprinting technology without the need for CPU-intensive traffic decryption.
The Secure Firewall identifies operating systems and applications for internal network hosts based on passive traffic analysis. This allows tailoring threat inspection policies based on vulnerabilities specific to a unique customer’s environment.
Customers can create traffic profiles based on application usage. The system can then detect unusual or malicious activity diverging from normal traffic patterns by creating a traffic baseline.
Access Control
One of the primary means for controlling applications is with rules in the Access Control policy. Using Access Control rules, application traffic can be trusted, blocked or allowed but passed on for deep packet analysis and threat inspection.
Applications can be identified whether or not they are operating on standard network ports. In some cases, the presence of specific applications operating over non-standard ports may indicate a policy violation or an attempt to evade firewall controls. The Secure Firewall can identify these non-standard connections and generate alerts or block traffic as needed.
In addition to identifying specific applications by name, the system includes additional application filters such as:
- Risk (Very Low, Low, Medium, High, Very High)
- Business Relevance
- Type (Application Protocol, Client Application, Web Application)
- Category (email, financial, news, peer to peer, social networking, etc.)
Applications can be readily identified in clear text or decrypted traffic. However, the system can also perform application detection on encrypted traffic. This is based on the TLS certificate returned from the server. By inspecting the Common Name (CN) or Subject Alternative Name (SAN), the system can identify many applications such as Software as a Service (SaaS) without the need to decrypt traffic.
Rules can even be configured with day and time criteria to help customers align their firewall rules with organizational policies regarding using systems during working hours. In the example below, selected applications are blocked during regular business hours only.
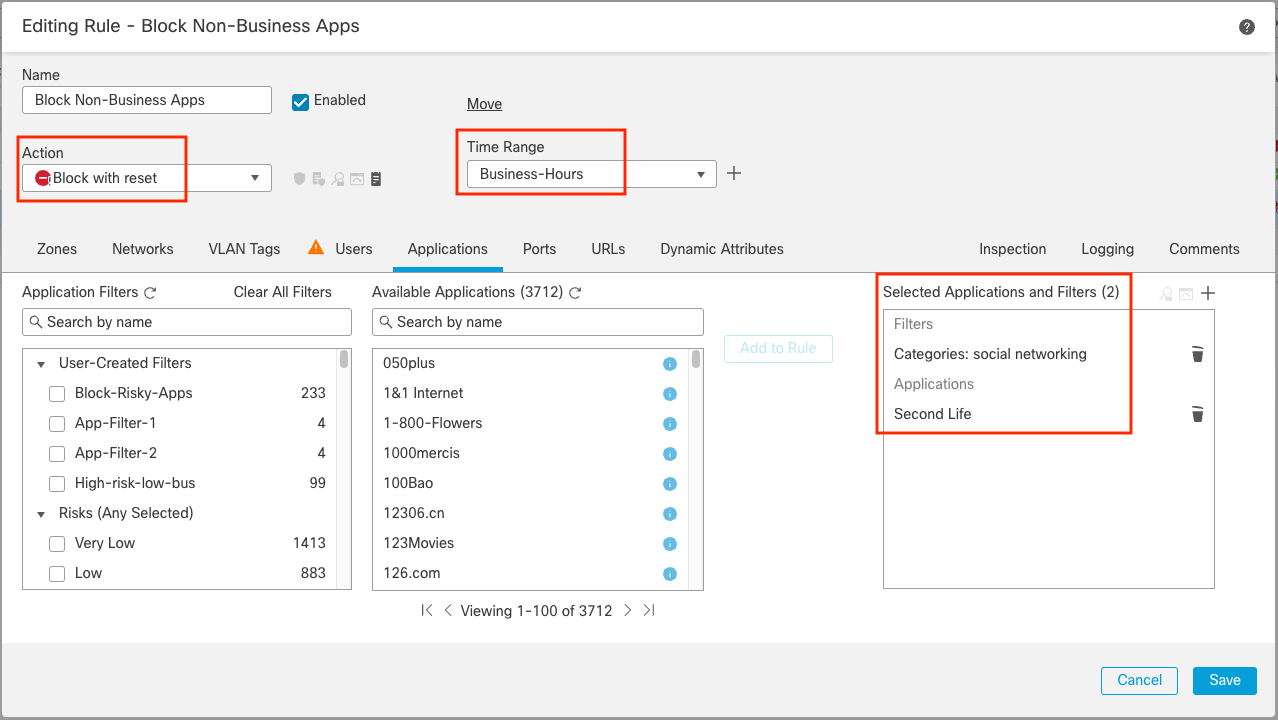
Figure 1: Application blocking in an Access Control rule
When coupled with TLS decryption, the Secure Firewall also offers granular control for popular applications. There are 18 micro applications within the Facebook app in the example below. Administrators can configure access control for the entire Facebook site or block/allow access on a more specific feature level.

Figure 2: Application and Micro Applications
Further controls are available through features like Safe Search.
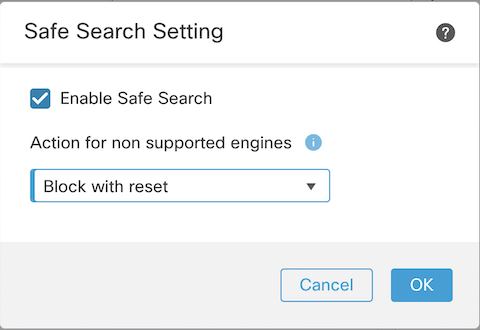
Figure 3: Safe Search
Some cloud-based applications require a different type of control technology. For example, Microsoft Office 365 access is controlled via a dynamic object feed using the Cisco Secure Dynamic Attributes Connector. This leverages a Microsoft web service that publishes a list of IP addresses and URLs. The firewall is then dynamically updated with the IP and Universal Resource Locator (URL) information needed to identify Office 365 traffic.
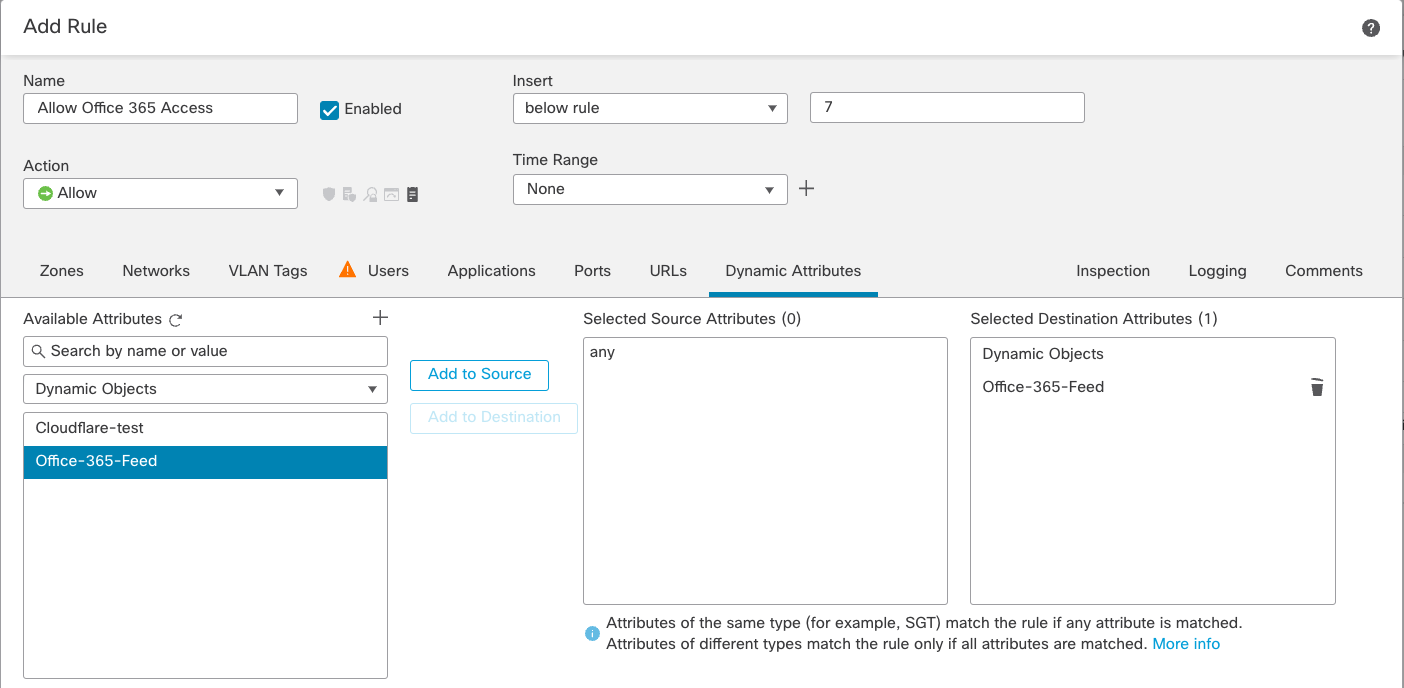
Figure 4: Using Cisco Secure Dynamic Attributes Connector
File Control
The system also allows or blocks file transfers based on direction (upload/download), application and file type. The example below is a Malware & File Policy rule which blocks the download of executable file types via the HTTP protocol.
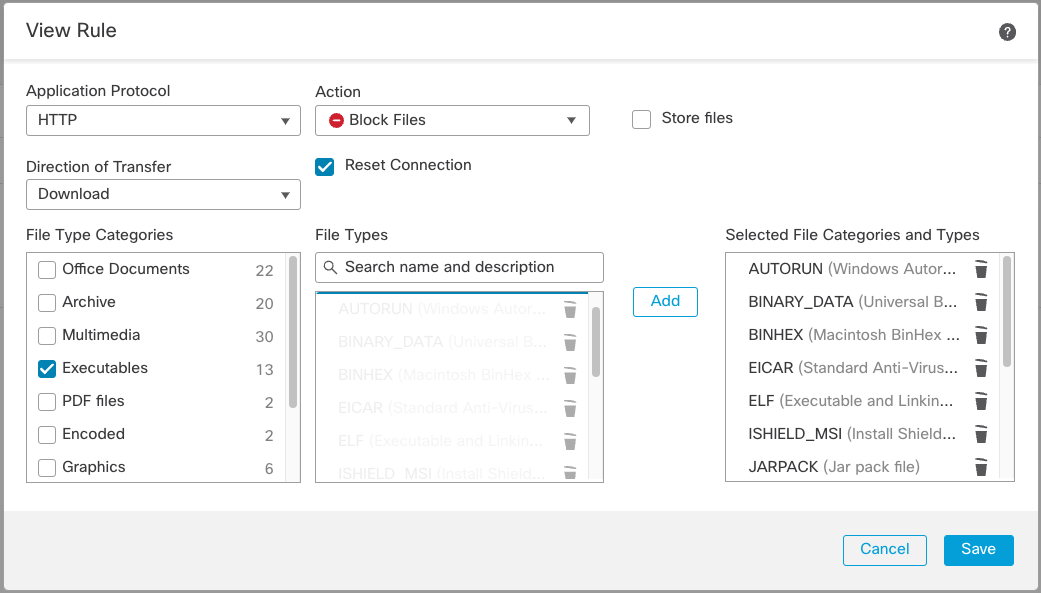
Figure 5: File Policy Block Rule
This is accomplished by inspecting the first packet of the file transfer and identifying the specific signature at the beginning of the file. This means that simply renaming a file or changing the file extension will not bypass this control.
SSL/TLS Control
Secure Firewall customers can also use applications within decryption rules in the SSL policy. By combining Application with other criteria such as Category (Finance, Shopping, Social Networking, etc.), the system can make traffic decryption decisions to ensure compliance with privacy regulations while at the same time decrypting untrusted traffic for inspection. SSL policy can also determine how to handle traffic that is not decryptable – either allow or block.
The system will not decrypt outbound traffic for financial, government or health care services in the example below.
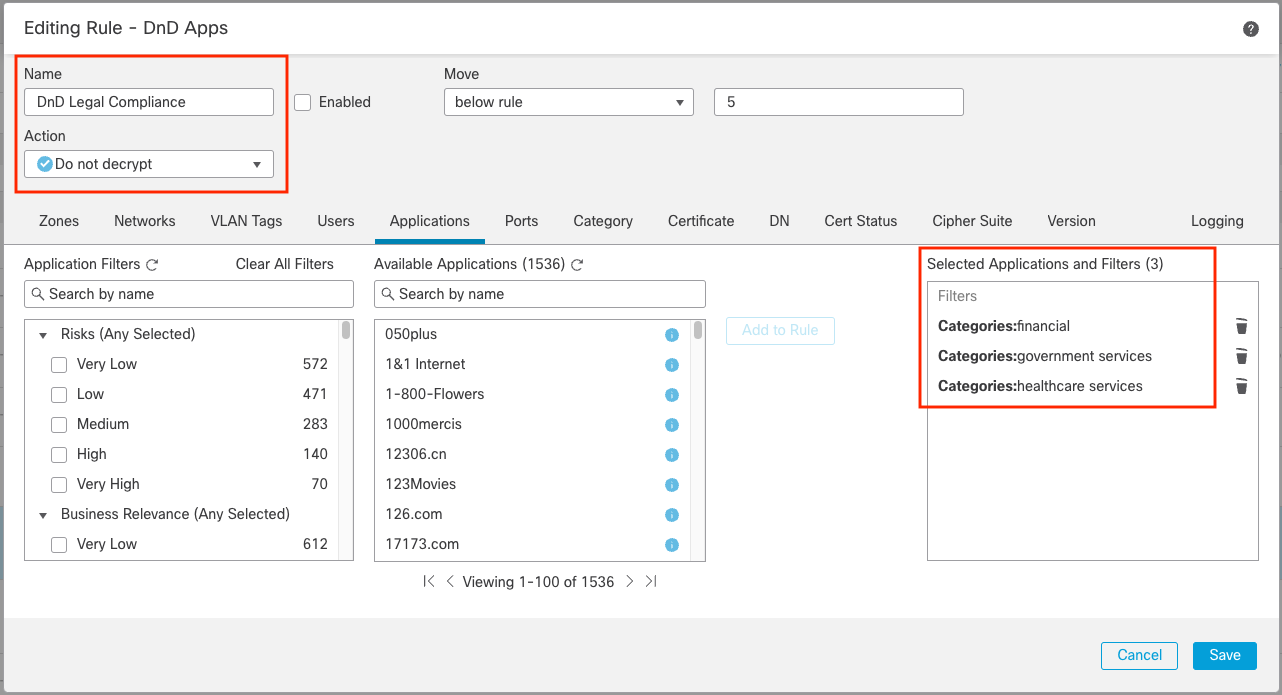
Figure 6: Do not decrypt SSL Policy rule
Beginning in Release 7.2, the Secure Firewall can also decrypt TLS 1.3 traffic by simply enabling a check box in the SSL policy.
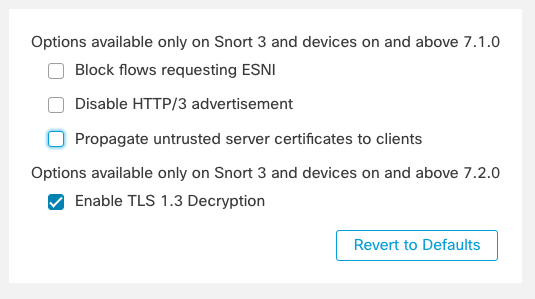
Figure 7: TLS 1.3 Decryption
Encrypted Application Traffic
Today, most application traffic is encrypted using Transport Layer Security (TLS). While the Secure Firewall provides hardware-accelerated decryption capability, there are still performance and operational ramifications to consider. In addition, features like certificate pinning make decryption impossible for some traffic. Because of this, many customers only perform selective decryption or no decryption on inbound and outbound traffic. This leaves blind spots which cannot be addressed with traditional deep packet inspection technologies.
The Secure Firewall offers two unique features to reduce these blind spots and identify applications within encrypted connections. These are TLS Server Identity and the Encrypted Visibility Engine (EVE).
TLS Server Identity
TLS Server Identity allows the identification of the destination server within a TLS 1.3 encrypted connection. As noted above, for TLS 1.2 traffic, the Secure Firewall can inspect the server certificate in a TLS connection and identify the Common Name or the Subject Alternative Name. These are then used to determine the server host and domain names. However, for TLS 1.3 traffic, this server certificate is encrypted - this makes viewing the certificate contents impossible without decryption.
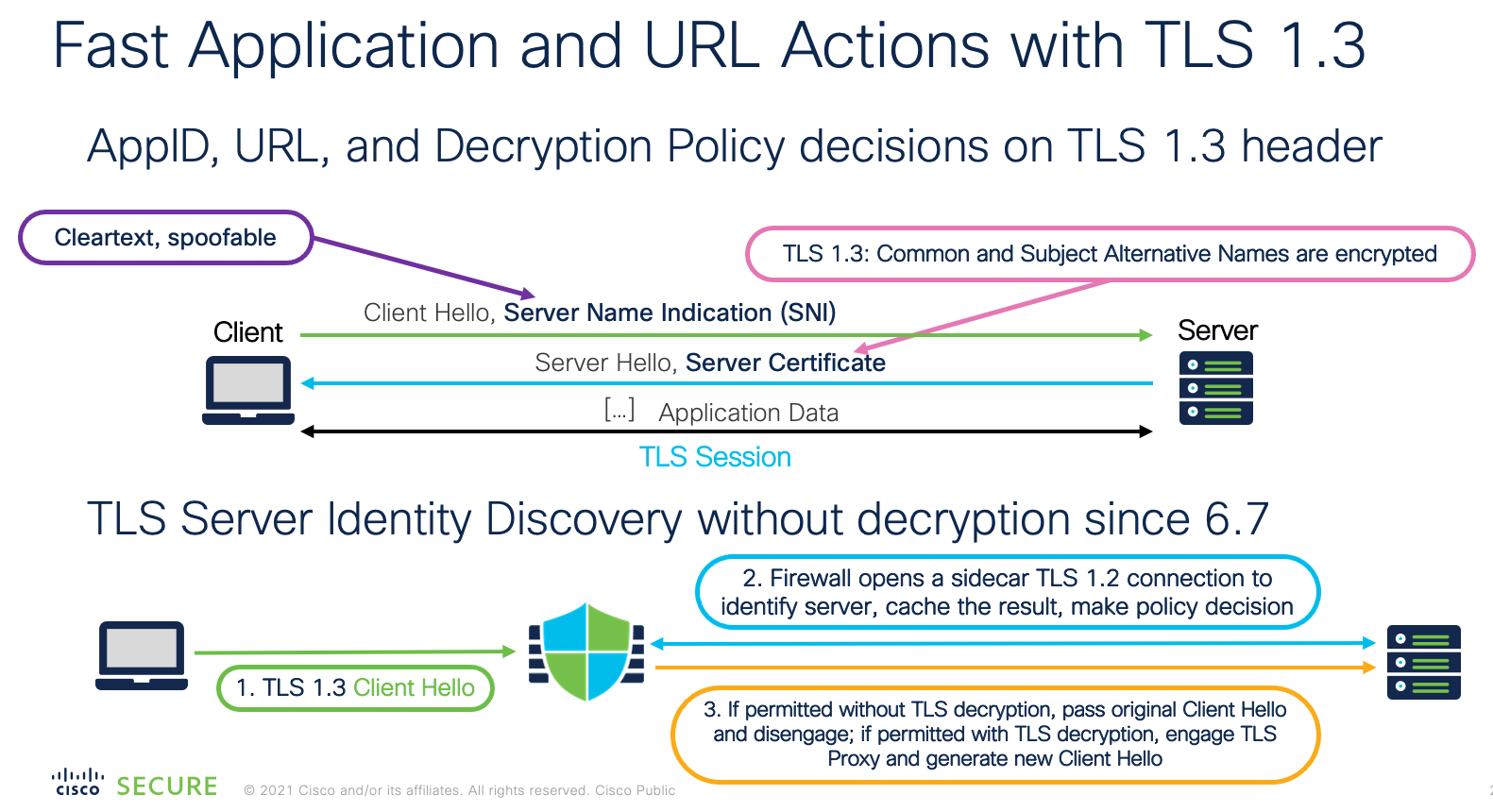
Figure 8: TLS Server Identity
By leveraging the fact that nearly all TLS 1.3 servers also support TLS 1.2, the Secure Firewall can detect a connection request (Client Hello) to a TLS 1.3 server and quickly send a TLS 1.2 connection request instead. By doing so, the system can inspect the server certificate and positively identify the CN or SAN. Once this is done, the system can decide if the connection should be allowed, blocked, or passed on for decryption. The original Client Hello is passed to the server and the Secure Firewall disengages inspection if the connection is allowed.
Encrypted Visibility Engine
Another method of identifying applications is the Encrypted Visibility Engine (EVE). While TLS Server Identity focuses on the server response, EVE looks at the Client Hello component of the TLS connection. By fingerprinting the Client Hello, the system can identify what process is initiating the connection. This information is then used to identify the application and match the appropriate rules.
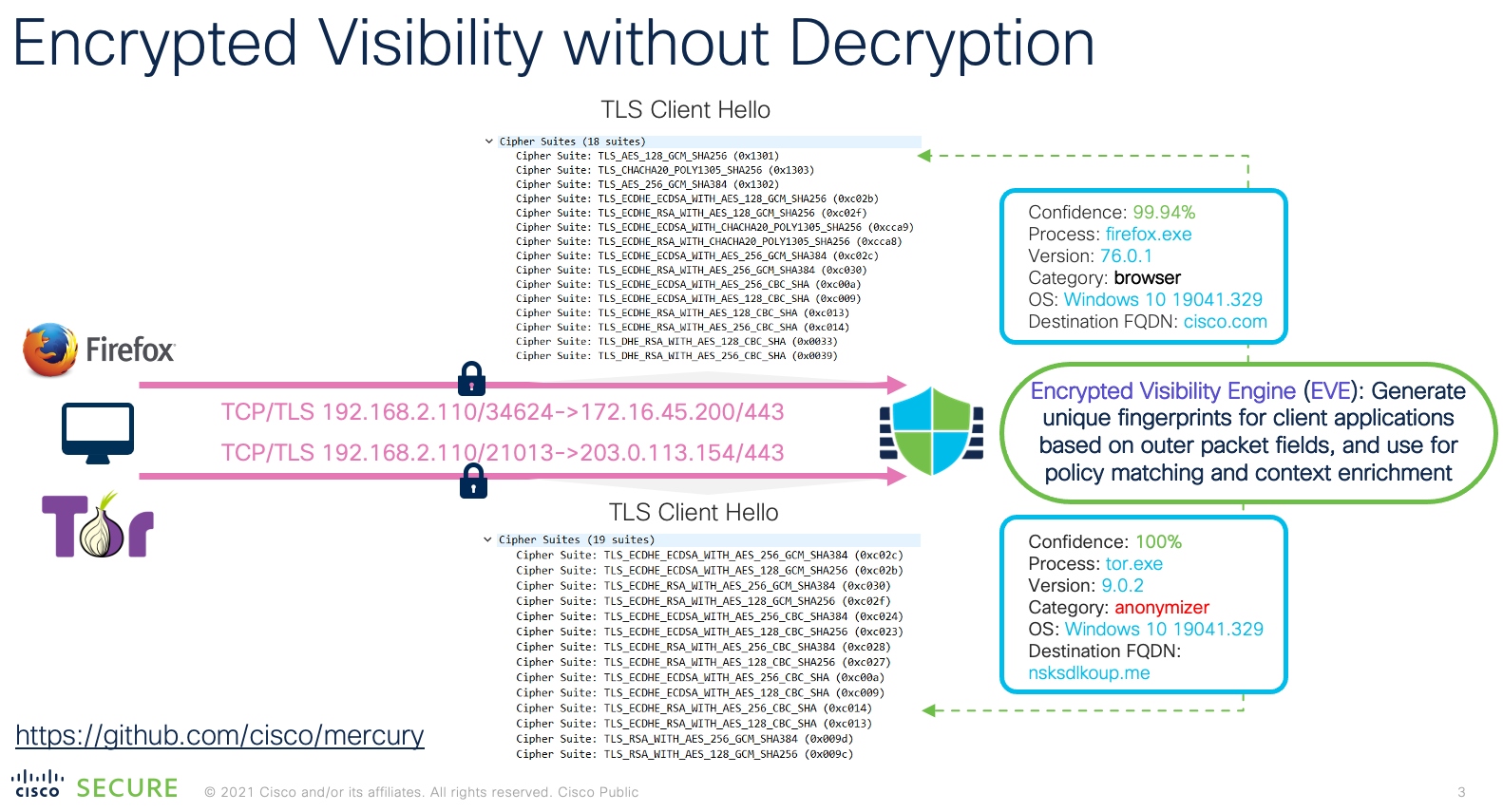
Figure 9: Encrypted Visibility Engine
An important element of EVE and TLS Server Identity is that they just work. The firewall administrator does not have to take additional steps to leverage these technologies. By simply adding the application criteria to rules, the system will use all the technologies available to positively identify the application(s) in use. Both of these features are also included in the firewall Threat license at no additional cost.
Application Discovery
In addition to identifying application traffic traversing firewall devices, the Secure Firewall can also catalog the applications running on internal hosts. The system gathers this information through passive analysis of network traffic. As applications and operating systems are discovered, the Firewall Management Center (FMC) builds a database of all the hosts on the network. Through the use of Firepower Recommended rules, customers can use this information to automatically tailor intrusion policies specific to the vulnerabilities on their network. The system also uses this data to set impact levels on intrusion events. Finally, application data can help identify hosts running malicious or unauthorized applications. Organizations can then use this information to remediate these hosts and reduce overall risk exposure.
Traffic Profiling and Correlation
Application detection can also be used to profile network traffic. By creating a baseline of normal application traffic, organizations can identify significant deviations, which are often indicators of unusual or malicious activity.
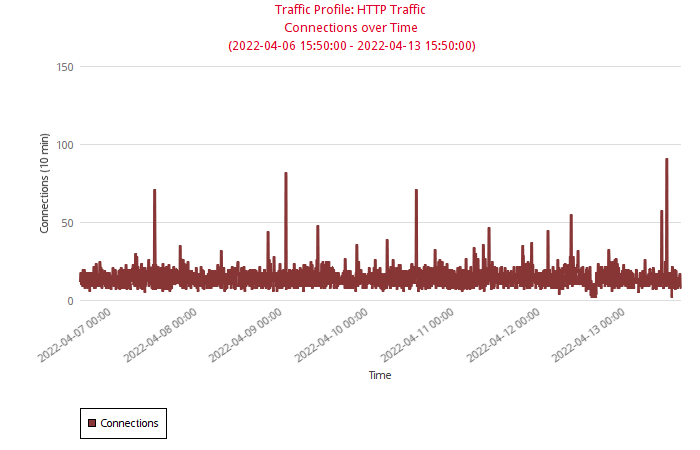
Figure 10: Traffic Profiling
Application Based Routing
Secure Firewall recently introduced an easy to use Policy Based Routing feature that allows users to create routing policies based on criteria such as application. We have created an Extended Access List Object to identify video applications in the example below. This object can be added to a policy based route to direct this traffic to a specified egress interface. Customers could use this to direct video traffic to take a different path than other core business applications.
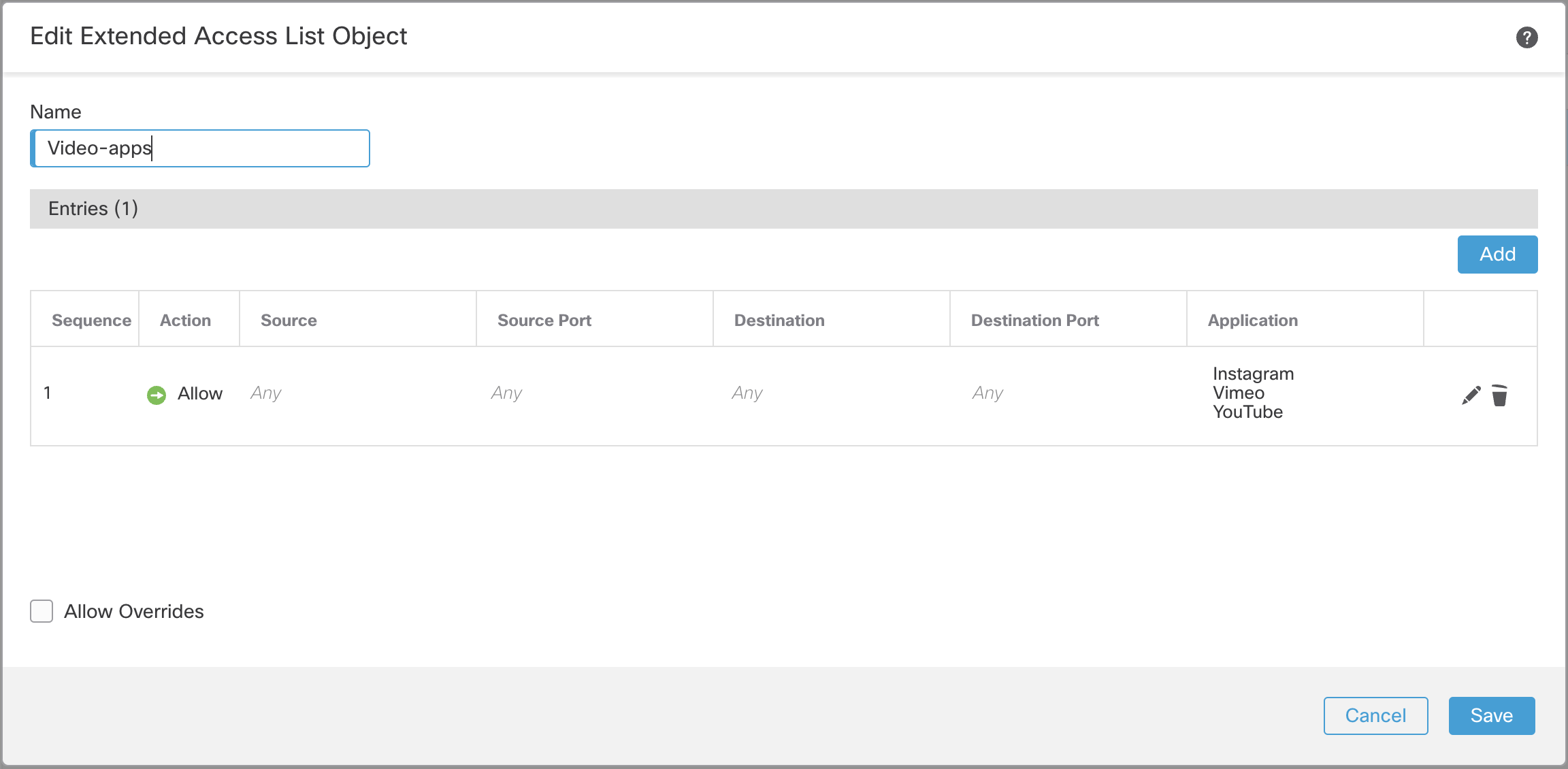
Figure 11: Extended Access List
Application Insights
The system includes a number of preconfigured dashboard widgets to provide insight into application usage. These can also be customized as needed to display application data tailored to customer needs.
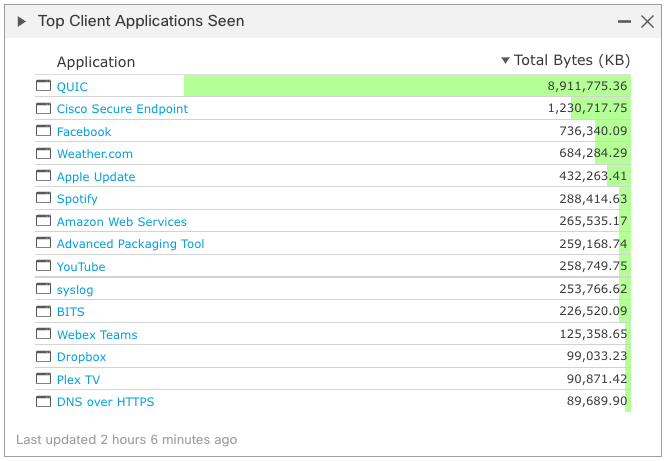
Figure 12: Top Client Applications
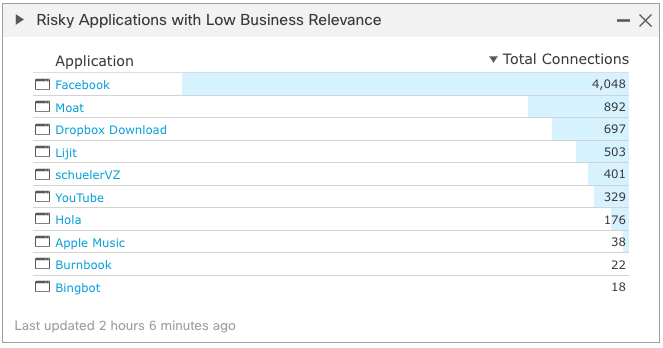
Figure 13: Application Business Relevance
Summary
The Cisco Secure Firewall provides several options for identifying and controlling application traffic on the network. Customers can use these features to enforce policies regarding the allowed use of organization resources and limit exposure to threat actors or applications with high risk or low business relevance. They can also identify unwanted applications running within the organization and even block their usage if desired. The ability to identify applications within encrypted traffic without the need to decrypt is a unique capability available exclusively to Cisco Secure Firewall customers.
Updated about 3 years ago
