Rule Optimization
Overview
Due to the changes made over time by different administrators working on the same firewall, some rules may become redundant and never triggered. Resulting in a continuously growing number of rules and objects that increase the Secure Firewall memory utilization to a point that causes network degradation. This document aims to familiarize administrators with features that can be utilized to optimize Firewall Management Center (FMC) and Firewall Threat Defense (FTD).
FMC Optimizations
The FMC optimizations help reduce policy deployment times by reducing the time it takes to create a snapshot during policy deployment.
FTD Optimizations
The FTD optimizations reduce memory usage through access control element optimizations.
Prerequisites
Cisco recommends that you have knowledge of:
- Working with Cisco Secure Firewall.
- Configuring Access Control Policies on an FMC.
- An understanding of Secure Firewall rule expansion logic.
Rule Optimization Options
Access Control Policy Hit Counts
Access Control Policy Hit Counts indicate the number of times a rule has triggered for a matching connection to determine which Access Control Policy rules are frequently triggered. A non-zero hit count associated with the rule indicates that the traffic flowing through the network triggered the rule, whereas a zero-hit count indicates the rule was never triggered by the traffic passing through the device.
Note
The policy hit count is reset if the device (FTD) is rebooted or the hit count is manually reset to zero.
Usage
Navigate to FMC > Policies > Access Control , select and Edit a policy to analyse. Once the policy has opened, click Analyze Hit Counts.
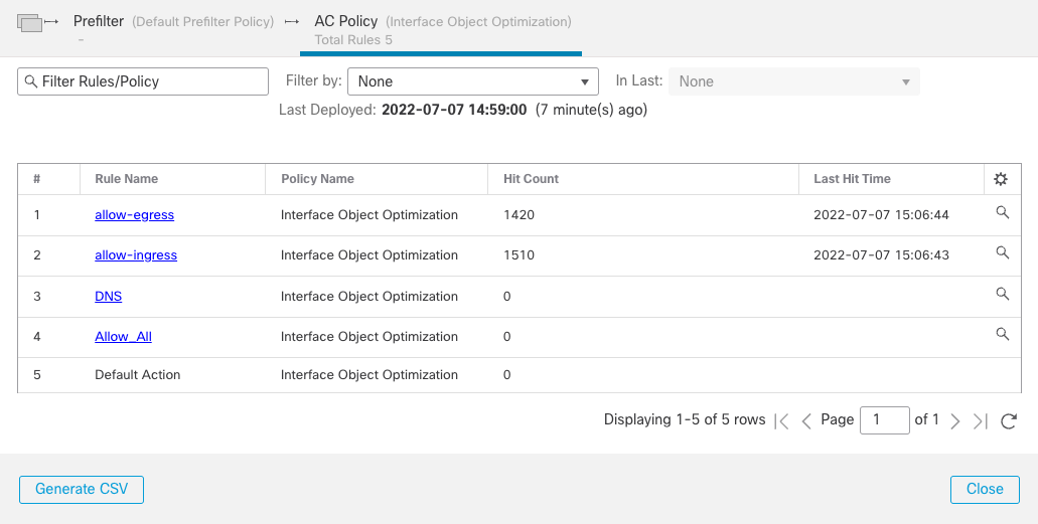
Use the hit count information to identify rules that have not been triggered.
Rule Conflicts
Upon enabling the Show Rule Conflicts option, the system analyzes the rules in the selected Access Control Policy to determine conflicts. A rule conflict occurs when a rule never matches traffic because an earlier rule matches the traffic first. Once the conflict detection process completes, the Show Warnings option displays the rule conflict warnings.
Note
The process of determining rule conflicts is resource-intensive and may take some time to display all of the rule conflicts.
Usage
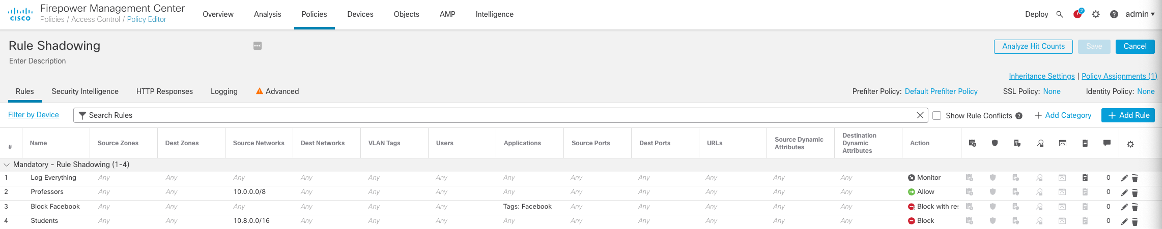
Review the FMC Access Control Rules with the Show Rule Conflicts option disabled:
Enabling the Show Rule Conflicts option prompts the Show Warnings option to display:
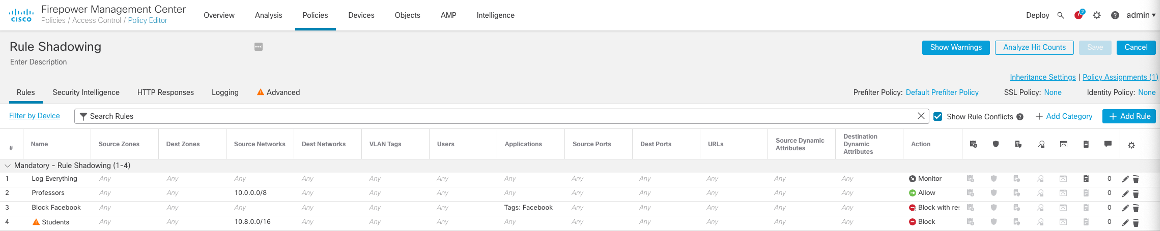
Inspecting the warnings, the Students rule is preempted by rule 2: Professors.
Note
It is recommended to import the Access Control Policy into a lab or development FMC to perform the process above to ensure no impact on the production FMC due to the processing overhead. The lab or development FMC should run the same software release and cloud updates.
Secure Firewall Access Control Rule Expansion Script (Release 6.5 and above)
The Secure Firewall Access Control Policy expands into multiple Access Control Elements (ACE) when deployed from the FMC to the firewall. It is important to understand how and why rule expansion occurs. Starting with release 6.5, the FMC contains a pre-built script that provides a way to compute expansion before policy deployment. The script provides the total ACE count per rule and does not account for rule conflicts.
Script Usage
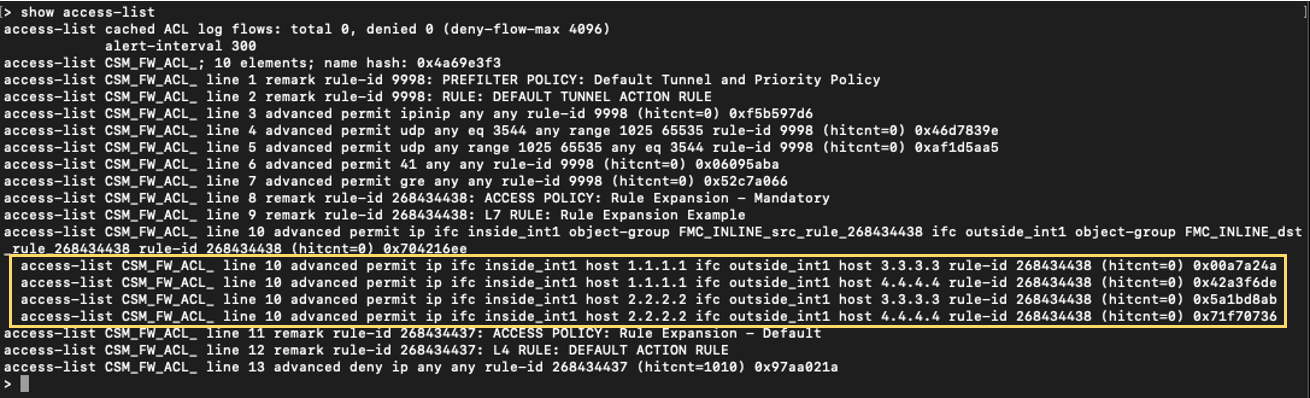
Review the Access Control Rule below:
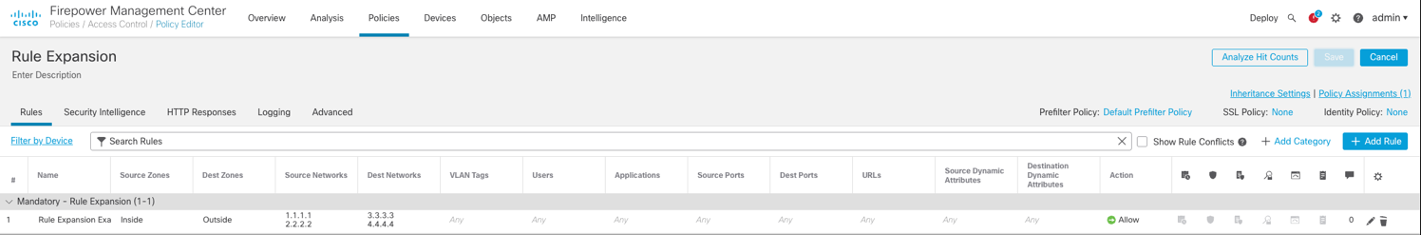
The Access Control Rule expands to four access-lists:
Before deployment, running the Access Control Rule Expansion Script will provide the total number of Access Control Elements. Note the device UUID:
- Navigate to FMC > Devices > Device Management.
- Edit the device by clicking on the pencil icon. Click on the Device tab.
- The device page URL contains the device UUID:
- https:///ddd/#NGFWDevice;id=b32cedc6-fd4d-11ec-a1cd-ded079ec2bdc
Enter the following commands on the FMC CLI:
- Enter
expert - Log in as the root user. Enter
sudo su - Initiate the script.
perl /var/opt/CSCOpx/bin/access_rule_expansion_count.pl - Enter the UUID noted from the previous steps.
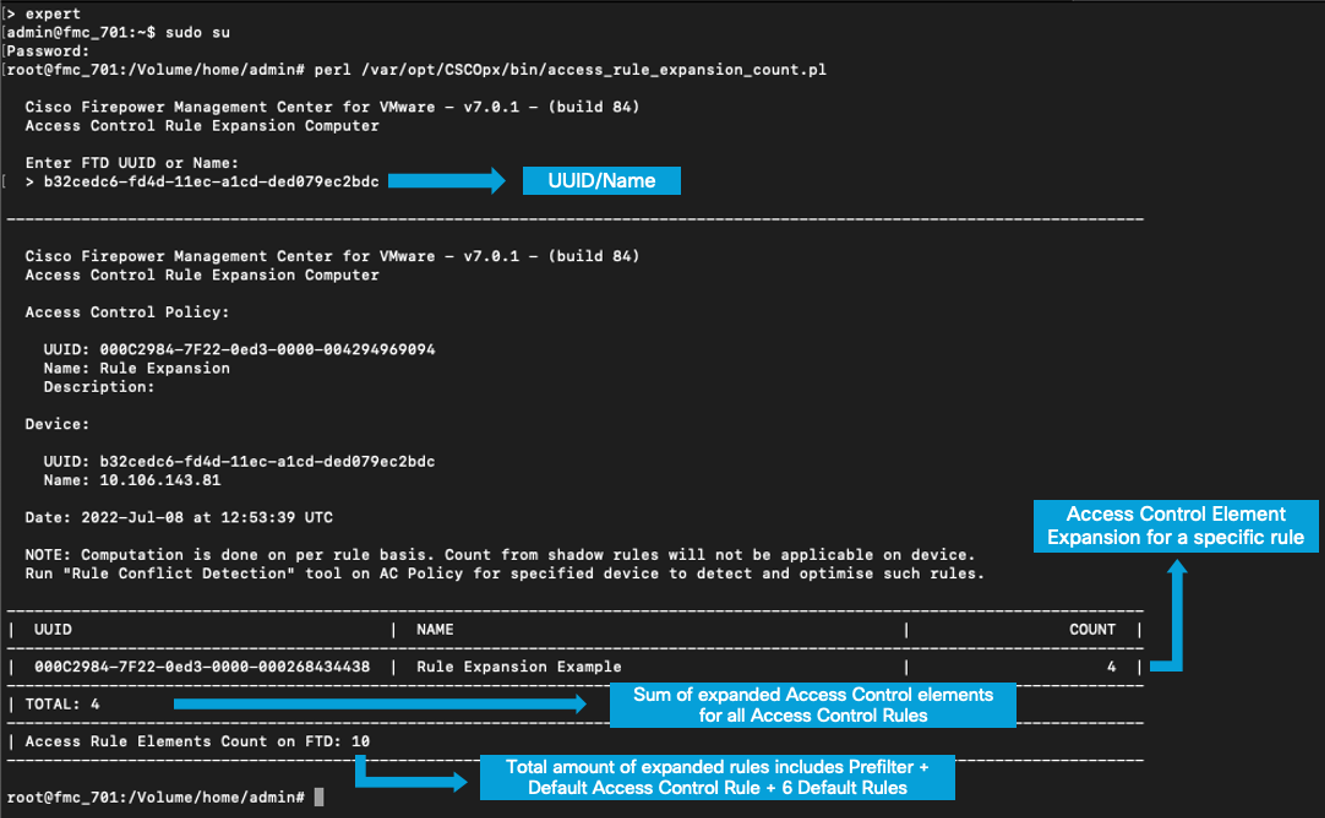
Note
The Access Rule Elements Count on FTD is higher than the total due to six Access Control rules being added as part of the default Prefilter and Access Control Policies.
Interface Object Optimization (6.7 and above)
Security zones and interface groups are configured as part of the source and destination when creating rules on the FMC. Upon deployment, security zones and interface groups used in the Access Control Policies generate separate rules for each source/destination interface pair. Resulting in rule expansion. The number of access-lists is computed as the multiplier of elements in the source and destination.
Note
If the rule contains "N" interfaces in the source security zones/interface groups and "M" interfaces in the destination zones/interface groups when performing deployment, this results in "N * M" access-lists.
The FMC no longer generates separate rules and expands the Access Control Rules upon enabling Interface Object Optimization. Thereby simplifying the device configuration and improving deployment performance.
Note
Interface Object Optimization applies to both Access Control and Prefilter Policies.
Usage
Review the Access Control Rules below:
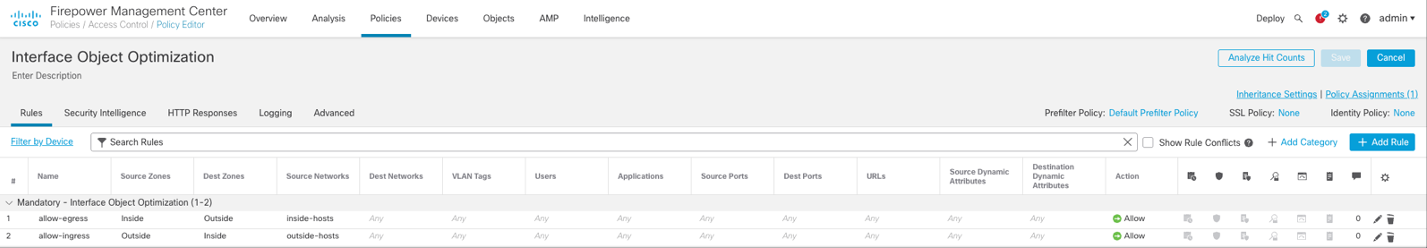
Note
Two interfaces are assigned to the source and destination security zones, respectively.
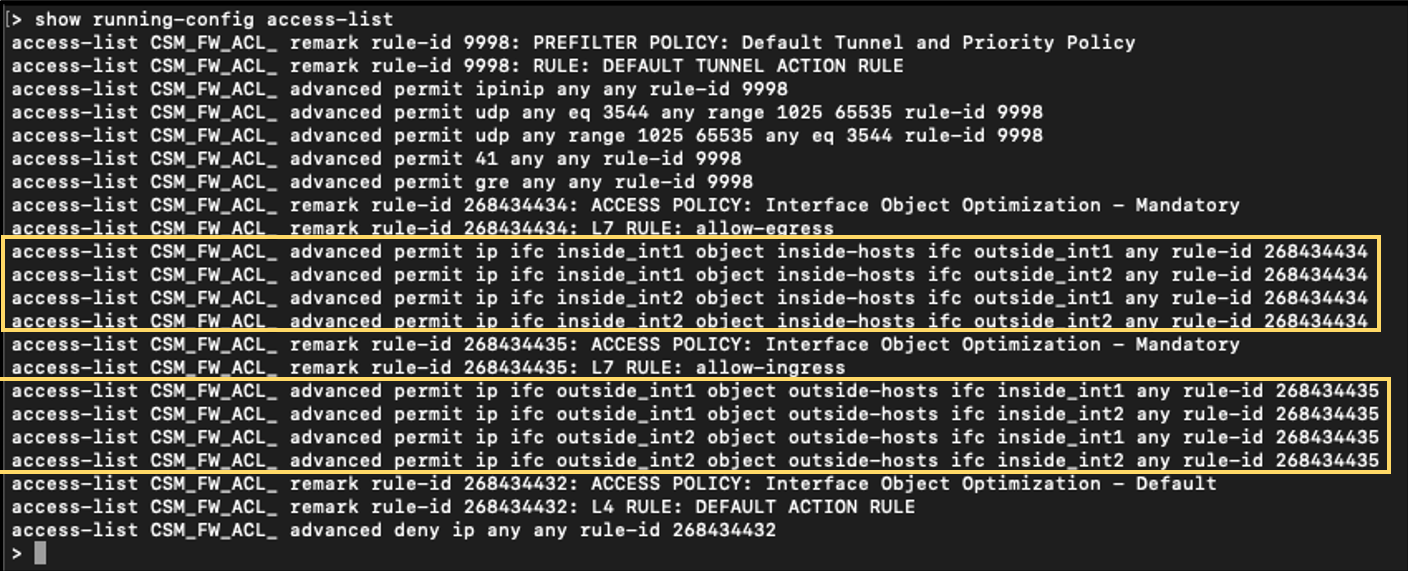
The Access Control Rules expand to eight access-lists:
Enable Interface Object Optimization, navigate to FMC > Devices > Device Management.
a. Edit the device by clicking the pencil icon. Click on the Device tab.
b. Click the pencil icon on the Advanced Settings section.
c. Click the check box next to Interface Object Optimization and click Save.
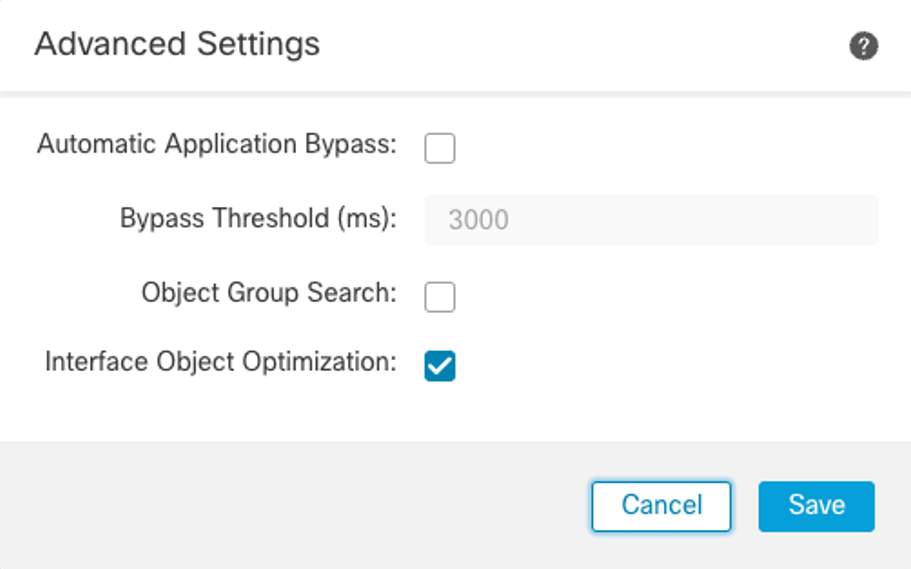
d. Click Deploy > Deployment to deploy the changes.
Note
A warning appears, noting that interface groups and security zones generate separate rules for each source/destination interface pair until Interface Object Optimization is enabled.
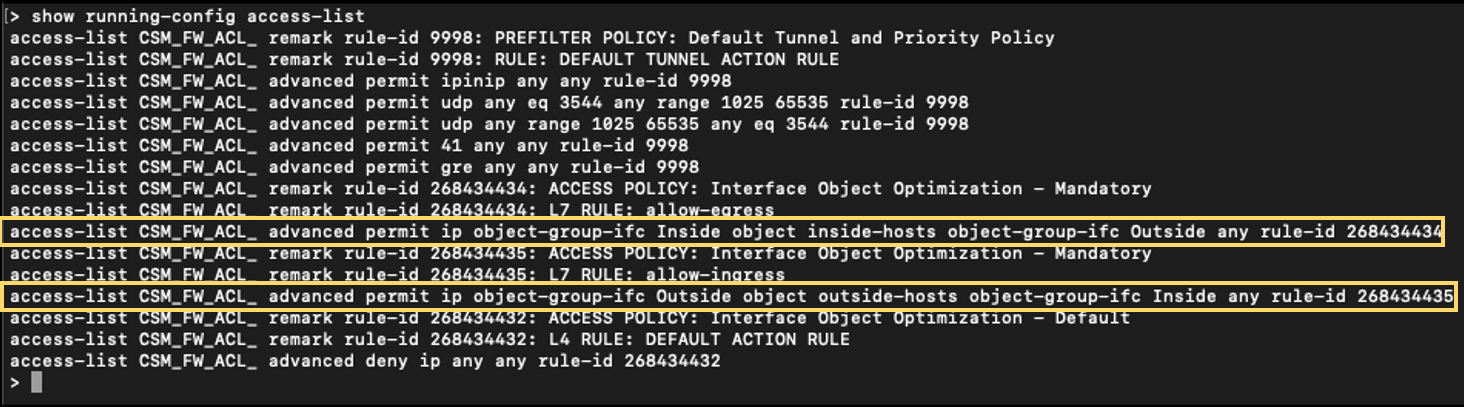
Upon enabling Interface Object Optimization, the number of access-lists is reduced to two:
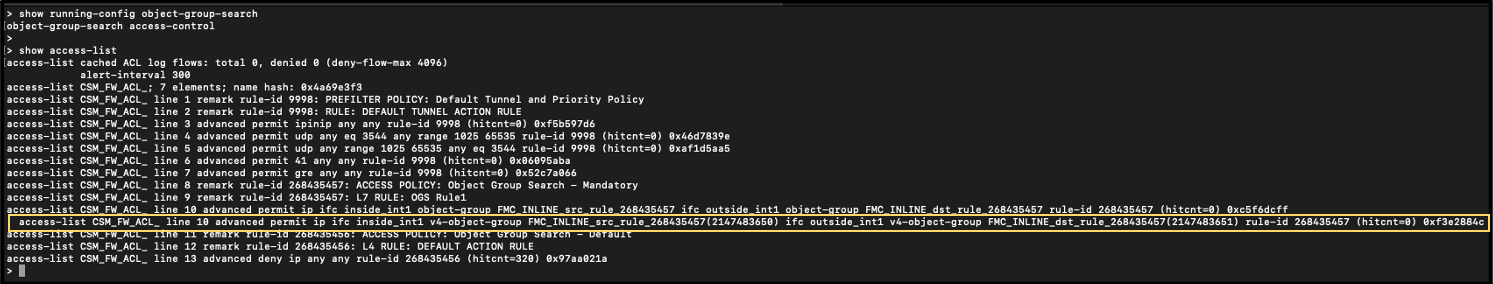
Object Group Search (6.6 and above)
Object Group Search is an ACL optimization feature that deploys one access-list instead of the multiplier of source and destination Access Control Elements on a per device basis.
Network object groups are configured as part of the source and destination when creating rules on the FMC. Upon deployment, network object groups used in the access control policies generate separate rules for each object group in the source and destination.
Note
The same logic applies to Object Group Search noted in the Interface Object Optimization section. The number of access lists is the multiplier of the number of objects in the source and destination.
Enabling Object Group Search reduces the memory requirements for Access Control Policies including network objects. However, Object Group Search may decrease rule lookup performance and increase CPU utilization. The CPU impact should be balanced against the reduced memory allocation for a specific Access Control Policy. In most cases, enabling Object Group Search provides an overall operational improvement.
Usage
Review the Access Control Rules below:
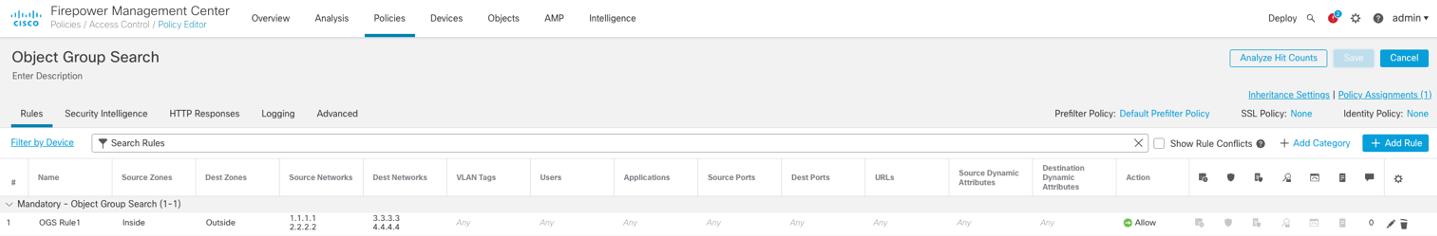
The Access Control Rule expands to four access-lists:
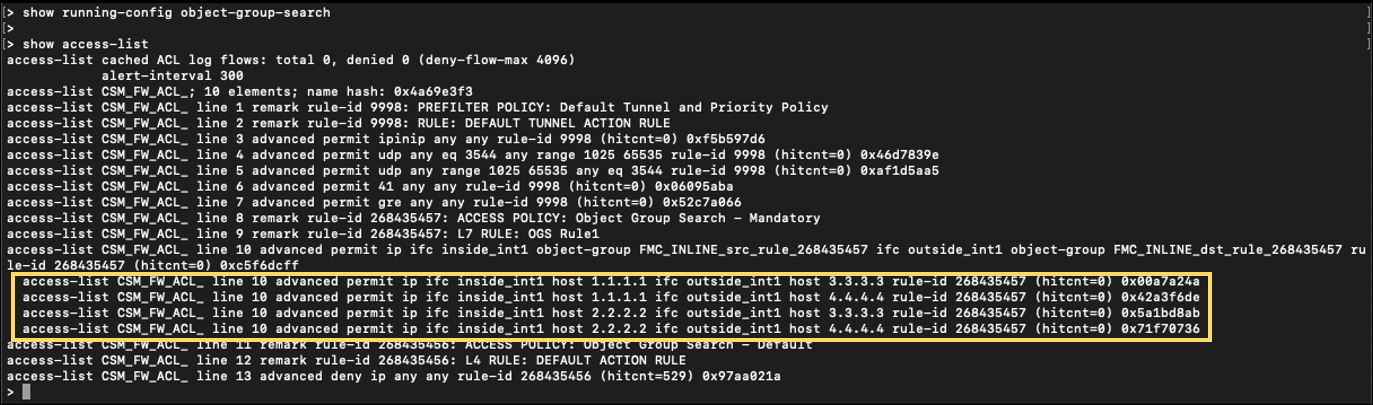
Note
The Object Group Search feature is enabled by default in software release 7.2. If the output displays without rules expanded, the device may be running release 7.2, or this feature is already is enabled.
Enable Object Group Search by navigating to FMC > Devices > Device Management.
- Edit the device by clicking the pencil icon and click on the Device tab.
- Click the pencil icon on the Advanced Settings section.
- Click the check box next to Object Group Search and click Save.
- Click Deploy > Deployment to deploy the changes.
Note
A warning appears that Object Group Search reduces memory requirements for Access Control Policies but might decrease rule lookup performance.
Upon enabling Object Group Search, the number of access-lists reduces to one:
Interface Object Optimization and Object Group Search are different features that can be enabled/disabled independently or together.
Additional Resources
Updated over 3 years ago
