Cisco Secure Dynamic Attribute Connector
Using Dynamic Attributes in Cisco Secure Firewall Policies
Introduction
The Cisco Secure Dynamic Attributes Connector (CSDAC) is an add-on feature of the Cisco Secure Firewall Management Center (FMC)that brings agility and intelligence into your security policy management.
Figure 1: Cisco Secure Dynamic Attribute Connector Benefits
CSDAC enables your firewall policy to adapt in real time to the changes in public and private cloud workloads and business-critical SaaS applications. The Firewall Management Center and CSDAC integration simplify management through firewall policy automation by keeping the rules up-to-date without tedious manual updates and policy deployment. With CSDAC, you can centrally manage workload attribute feeds obtained from multiple public and private cloud environments, enabling firewalls to adapt to changes instantaneously to help accelerate Cisco Secure Firewall integration with your complex and dynamic environment.
CSDAC significantly improves network security with automatic endpoint attribute and contextual awareness propagation simultaneously, preventing the build-up of outdated firewall rules over time.
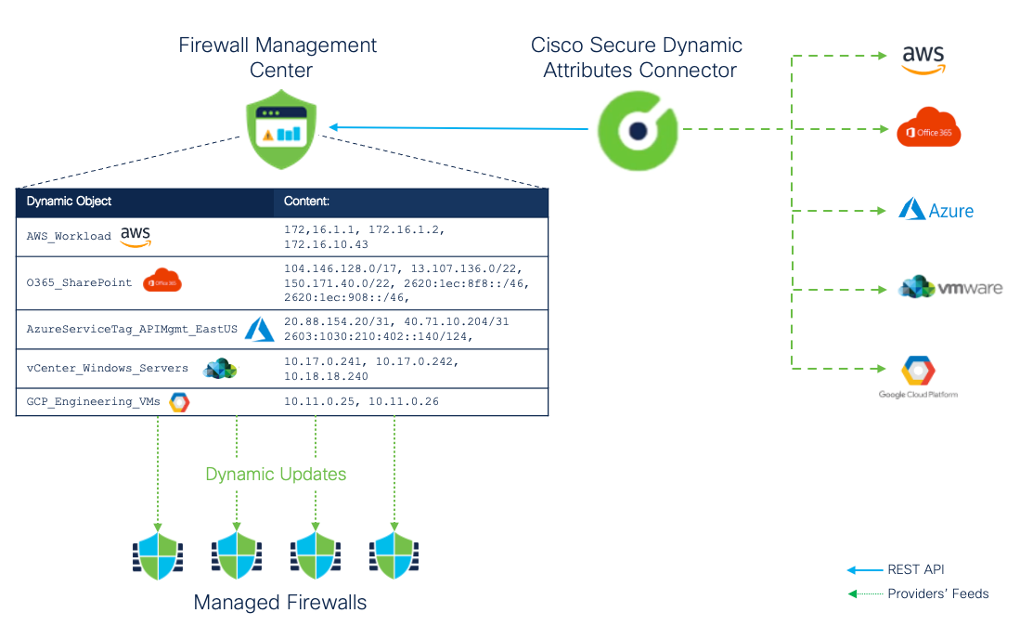
Figure 2: Cisco Secure Dynamic Attributes Connector
CSDAC in Action
CSDAC maps cloud VM IP addresses to Dynamic Objects, which are then used in Access Control Policy rules. Changes in the cloud detected by CSDAC are cascaded in real-time to the FMC, and in turn, to the managed firewalls without any administrator action. CSDAC makes firewall policy dynamic, more secure, and easier to manage.
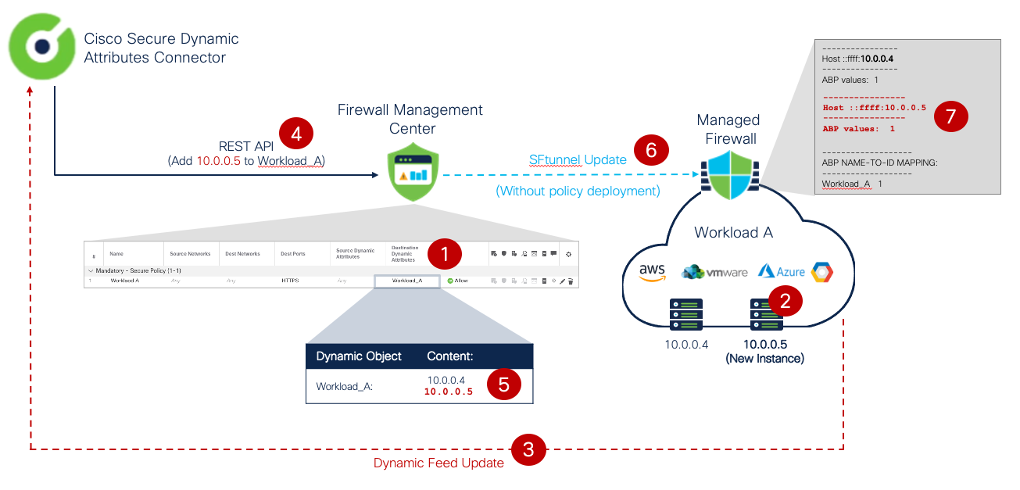
Figure 3: CSDAC Dynamic Object Update
- In Figure 3 above, the firewall protects a Workload and is configured with an Access Control Policy containing the dynamic object Workload_A representing cloud resources.
- CSDAC is configured to monitor changes to the workload constantly and detects when a new instance is spun up.
- CSDAC detects the workload change and evaluates the user-created attribute filters.
- Then CSDAC triggers a REST request to update the Workload_A dynamic attribute with the 10.0.0.5 IP address of the new server.
- The Firewall Management Center adds the new IP address to the dynamic object.
- Immediately after the Workload_A object change, the FMC pushes an update to all the managed firewalls using that object in deployed Access Control Policies. The dynamic object update happens automatically and does not require a policy deployment.
- The firewall updates the new IP address in Snort's identity memory and its policy to allow the new server access.
Architecture
Cisco Secure Dynamic Attributes Connector is a modular, containerized application comprised of three main components:
- Connectors – a connector is a software interface that interacts with a public or private cloud provider to retrieve up-to-date network information, categories, and tags. CSDAC translates information provided by the connectors to Dynamic Objects used in firewall access control policies on the FMC. Architecturally the connectors are software plug-in modules installed in CSDAC, which allows the straightforward addition of new connectors in future releases.
- Dynamic Attribute Filters – a set of conditions configured by an administrator, defining how cloud resources are mapped to Dynamic Objects. The filters are built with AND/OR boolean expressions matching attributes specific to the source Provider. For example, you can configure a Dynamic Object with VM IP addresses assigned with a particular tag in Azure or running in a specific VMWare port group.
- Adapters – represent a secure connection to an FMC configured with Dynamic Objects by CSDAC and periodically updated with changes detected via configured cloud Connectors.
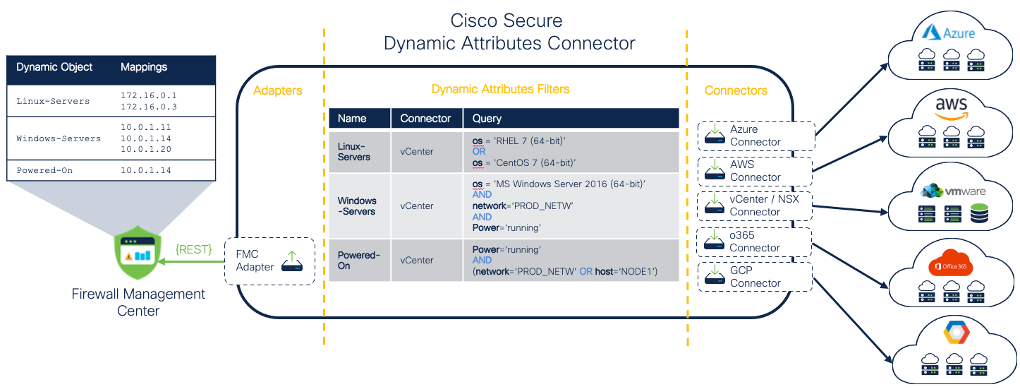
Figure 4: CSDAC Architecture
Dynamic objects are the cornerstone of the solution in the Firewall Management Center that provides a new approach to the access control policy building blocks and was initially introduced in the Secure Firewall 7.0 release. Dynamic Objects are configured and updated using the Firewall Management Center’s programmatic interface. When used in an Access Control Policy, the Dynamic Objects programs Snort’s Identity Memory in addition to PassiveID and SGT identities and are auto-updated in real-time without policy deployment.
Deployment Scenarios
CSDAC comes in two form factors:
- An on-premises application that runs on a Linux server
- A Cisco Defence Orchestrator cloud-delivered application
On-Prem CSDAC Deployment
The on-premises CSDAC application can be installed on the following Linux distributions:
- Ubuntu 18.04 or 20.04
- Red Hat Enterprise Linux (RHEL) 7 or 8
- CentOS Linux
The install and upgrade process is automated with Ansible Galaxy 2.9 or later and requires Python 3.6.x. The minimum requirements for the system are 4 CPUs, 8GB RAM, and 100 GB of available disk space.
Best Practice
Depending on your deployment scale and the number of the connectors consider following sizing recommendation for the CSDAC host system:
Max. Connectors
Avg. Number of Filters per Connector
Number of Workloads
Recommended System Setup 50
5
20 000
4 CPUs; 8GB RAM; 100 GB disk 125
5
50 000
8 CPUs; 16GB RAM; 100 GB disk
The on-premises CSDAC is typically deployed in a Data Center in close network proximity to the Firewall Management Center as illustrated in Figure 5. Depending on the providers you want to monitor, ensure the CSDAC has network connectivity to the programmatic interfaces on the Internet or locally in your Data Center. Use the on-premises CSDAC to provide dynamic objects to on-premises and cloud-delivered Firewall Management Centers.
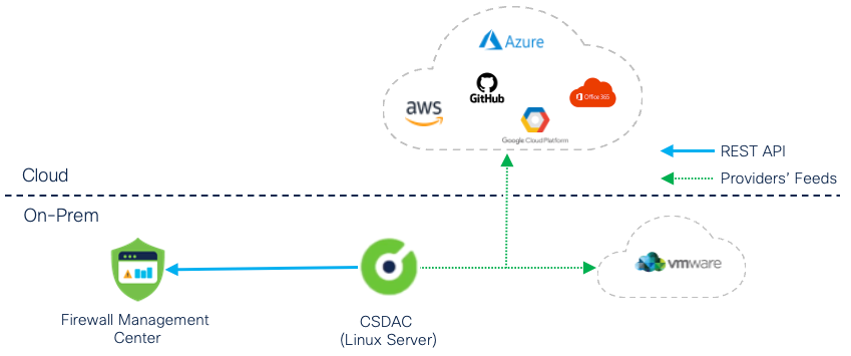
Figure 5: CSDAC On-Prem Deployment with On-Prem FMC
If you are integrating an on-premises CSDAC with a cloud-delivered FMC, ensure you allow outbound network access towards Cisco Defense Orchestrator on your firewalls (Figure 6). To find the your cloud-delivered Firewall Management Center's URL, open the CDO console and navigate to "Tools & Services > Firewall Management Center" and select the desired FMC instance.
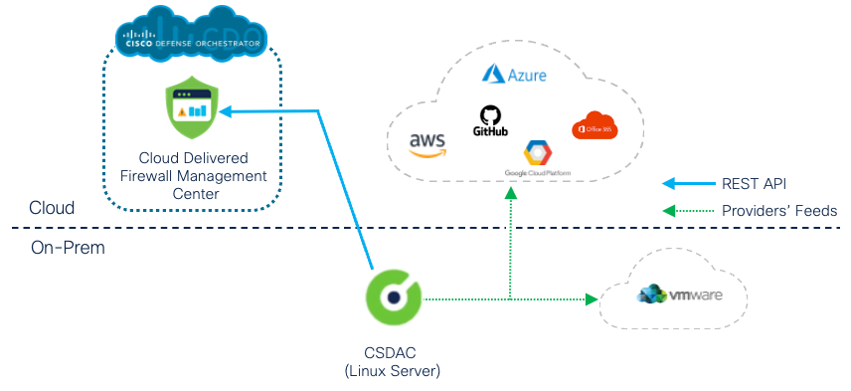
Figure 6: CSDAC On-Prem Deployment with Cloud-Delivered FMC
The CSDAC Ansible collection and detailed installation instructions are available on the Ansible Galaxy space and in the video below.
Cloud-Delivered CSDAC Deployment
The SaaS form factor provides all the benefits of dynamic attribute updates without having to deploy and maintain a Linux VM hosting the CSDAC application in your environment. The CSDAC application is available in Cisco Defense Orchestrator in the Tool & Services section.
Figure 7: Cloud-Delivered CSDAC Dashboard
The cloud-delivered CSDAC runs within Cisco Defence Orchestrator and can provide dynamic updates to both on-premises and cloud-delivered Firewall Management Center deployments. In the latter scenario, the communication between CSDAC and the cloud-delivered FMC is provided natively by the CDO's infrastructure as illustrated in Figure 8.
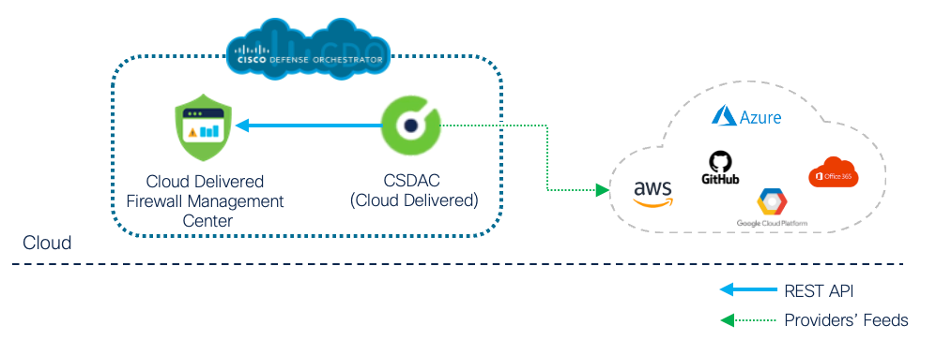
Figure 8: Cloud-Delivered CSDAC and Firewall Management Center
The communication between cloud-delivered CSDAC and the on-premises FMC, is established through a lightweight connector application, Secure Device Connector or SecureX as illustrated on Figure 9.
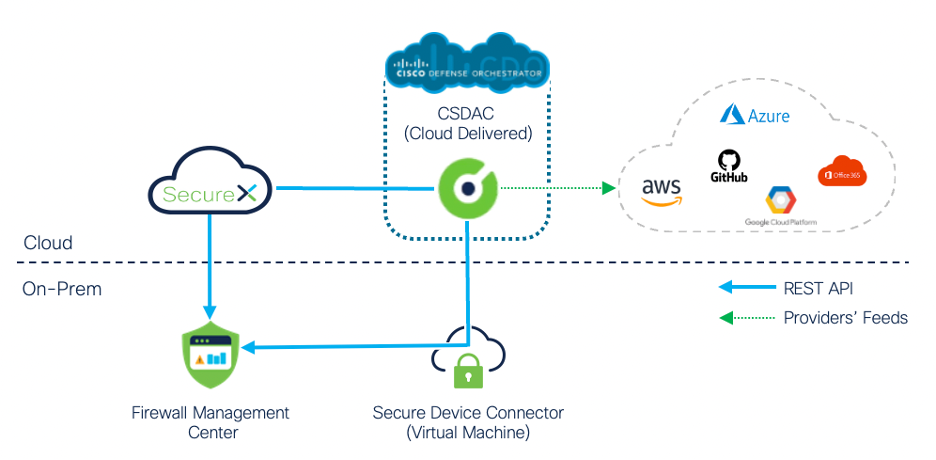
Figure 9: Cloud-Delivered CSDAC with On-Prem Firewall Management Center
In order to use the cloud-delivered CSDAC with an on-premises firewall deployment, you need to add your Firewall Management Center to the Cisco Defence Orchestrator's inventory. CDO supports two connection methods with on-premises Firewall Management Centers:
- SecureX based connection (SecureX on-boarding procedure)
- Secure Device Connector based connection (Credentials on-boarding procedure)
Figure 10 provides a screenshot of the initial step of the on-premises Firewall Management Center onboarding wizard in the Cisco Defense Orchestrator.
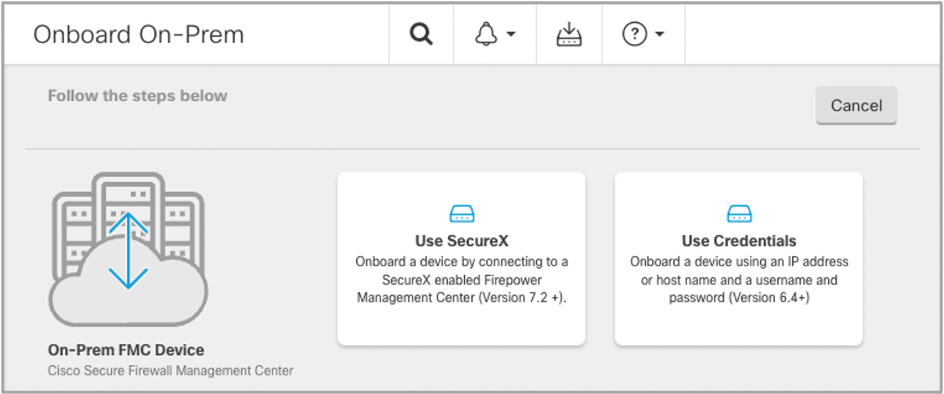
Figure 10: Adding On-Prem Firewall Management Center to CDO's Inventory
Note
Cloud-delivered CSDAC can support on-premises and cloud-delivered Firewall Management Center adapters at the same time.
The following video provides an overview of the cloud-delivered CSDAC along with a demo covering integration with both on-premises and cloud-delivered FMC.
Configuration
Connectors
The connectors are the modules that interface with the public and private cloud providers to retrieve information about workload resources over a secure connection. CSDAC supports the import of mappings from the following:
- Microsoft Azure user-defined tags (Azure Connector YouTube Demo)
- Microsoft Azure service-tags public feed (Azure Service Tags Connector YouTube Demo)
- Amazon Web Services (AWS) user-defined tags (AWS Integration YouTube Demo)
- Google Cloud Platform (GCP) labels and network tags (GCP Connector Setup YouTube Demo)
- Office 365 public feed (Office 365 Connector YouTube Demo)
- GitHub public feed (GitHub Connector Setup YouTube Demo)
- VMware categories and tags are managed by vCenter and NSX-T (VMWare Integration YouTube Demo)
The table below provides the connector individual release support matrix of the Cisco Secure Dynamic Attributes Connector.
| CSDAC Version/Platform | AWS | VMWare | Office365 | Azure | Azure Service Tags | GitHub | GCP |
|---|---|---|---|---|---|---|---|
| Version 1.1 (on-premises) | YES | YES | YES | YES | YES | NO | NO |
| Versions 2.0 (on-premises) | YES | YES | YES | YES | YES | YES | YES |
| Cloud-Delivered (CDO) | YES | NO* | YES | YES | YES | YES | YES |
* - in CDO deployments, you can use an on-premises CSDAC instance to provide VMWare sourced dynamic objects to your cloud-delivered Firewall Management Center as illustrated on **Figure 6**.
In Figure 11 below, you can see an example of a Google Cloud Platform Connector setup. The name uniquely identifies the connector instance and refers to the dynamic attribute filters configuration to specify the provider for individual Dynamic Objects.
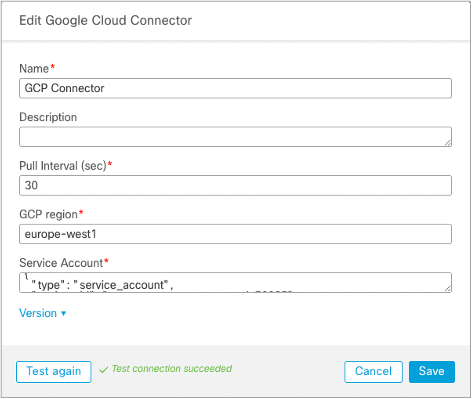
Figure 11: Google Cloud Platform Connector
The pull interval value determines the frequency at which the CSDAC reaches out to the provider for the latest list of resources. This timer directly influences how quickly your firewalls pick up changes to the Dynamic Objects used in enforcing policies. The lower the pull interval, the quicker the firewall policy gets updated.
Warning
Some providers impose limits on the number of API calls in a unit of time and may throttle CSDAC requests if the pull interval is set to a low value.
Best Practice
When configuring the pull interval, ensure you find the right balance between the desired dynamic object update rate and the rate of requests supported by your providers. The CSDAC generates warnings messages when a provider throttles the requests. In such instances, gradually increase the pull interval timer to an acceptable value.
The attributes required to configure a connector are specific to the provider. Depending on the connector you are setting up, you may need a set the region where your services are deployed, as well as the API access credentials or username/password. Once you configure the required fields, you can run a connectivity test to confirm your setup is complete, and the CSDAC can reach the provider.
The Cisco Secure Dynamic Attributes Connector Configuration Guide gives a helping hand with provider-specific application account setup. In the documentation, you will find a set of step-by-step procedures for each provider supported by the CSDAC. The table below provides a list of quick links for your convenience.
| Provider | Procedure for setting up an application account for CSDAC access |
|---|---|
| AWS | Create an AWS User with Minimal Permissions for the Cisco Secure Dynamic Attributes Connector |
| Azure | Create an Azure User with Minimal Permissions for the Cisco Secure Dynamic Attributes Connector |
| GCP | Create a Google Cloud User with Minimal Permissions for the Cisco Secure Dynamic Attributes Connector |
| VMWare | vCenter Connector—About User Permissions and Imported Data |
| Office365 | No credentials are required - CSDAC downloads IP ranges of Skype for Business, Sharepoint, Exchange and Common Services from a public Microsoft's API URL. |
| GitHub | No credentials are required - CSDAC downloads IP ranges of GitHub content, webhooks and Actions from a public GitHub's API URL. |
Once you set up a connector you can review the configuration details as well as the current status. The Connectors tab provides a list of all provider instances configured in your CSDAC.
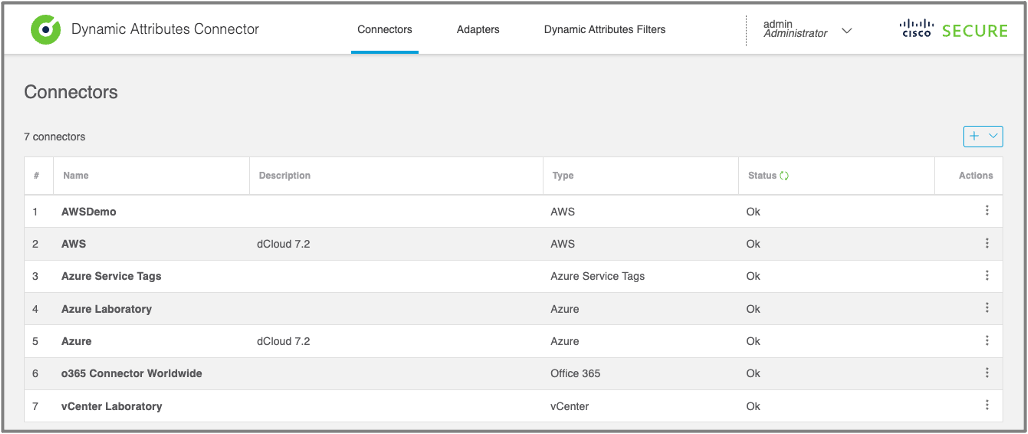
Figure 12: CSDAC Connectors Tab
Note
You can configure multiple connectors for each type AWS, Azure, GCP, and VMWare, should you have multiple public or private cloud instances of the same type.
Adapters
Adapters are secure connections to the Firewall Management Center that CSDAC uses to configure and update dynamic objects. When configuring the adapter on your on-premises CSDAC you need to provide the IP address, username, and password, as well as, the your FMC's trusted certificate chain.
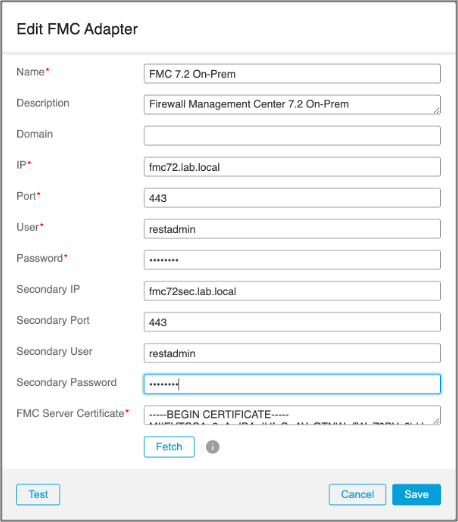
Figure 13: Configuring an On-Prem Firewall Management Center Adapter
️Warning
It is strongly recommended to create a dedicated user on the FMC for the CSDAC REST API access.
Starting from the on-premises CSDAC release 2.0, you can configure an adapter connecting to the cloud-delivered FMC. The adapter setup requires a base URL and the API token, which are available in your Cisco Defense Orchestrator tenant. The step-by-step procedure is available in the CSDAC Configuration Guide in the Get Your Base URL and API Token section.
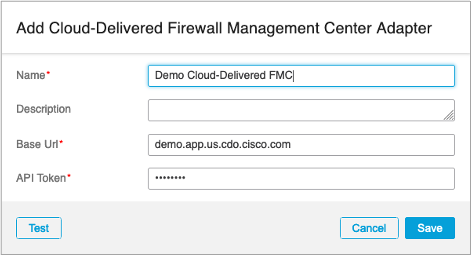
Figure 14: Configuring a Cloud-Delivered Firewall Management Center Adapter
In the cloud-delivered CSDAC, you simply select the on-premises FMC from your inventory or the cloud-delivered FMC. You don't have to specify access credentials as the connection is already secured by Cisco Defense Orchestrator management channel.
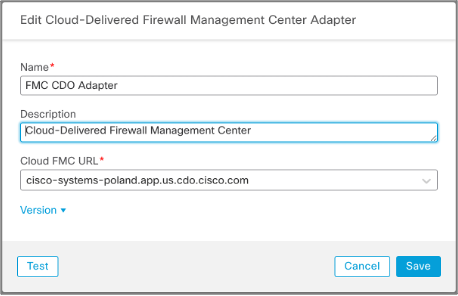
Figure 15: Configuring Cloud-Delivered Firewall Management Center Adapter
Dynamic Attributes Filters
The Dynamic Attribute Filters are conditions used to map public and private cloud resources to Dynamic Objects. Each filter contains:
- The Dynamic Object name to be programmed on the Firewall Management Center
- The source connector providing information about the workload
- A query string defining the matching criteria for VMs and instances which IP addresses will be dynamically added to the objects pushed to the firewalls
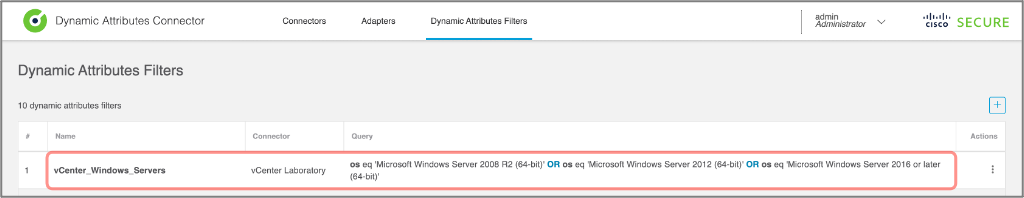
Figure 16: CSDAC Dynamic Attributes Filters Tab
CSDAC pulls the list of resources using configured connectors with provider-specific meta-data. The information is made available to the administrator within the Dynamic Attribute Filter configuration in the form of Key/Value pairs. The Keys are the attributes associated with a VM or an instance running in a cloud, such as user-defined tags in AWS/Azure/GCP, or network, power status, or VM name on vCenter.
In the sample condition depicted on Figure 17, the CSDAC provides a drop-down of available Keys that one can use for the vCenter connector.
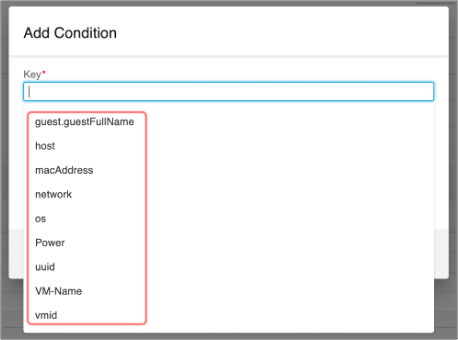
Figure 17: Selecting Keys in a Condition
After selecting a Key, CSDAC displays the available set of Values an administrator can use as the matching criteria. In Figure 18, after selecting "os" key, CSDAC provides the list of operating systems running in the VMware infrastructure.
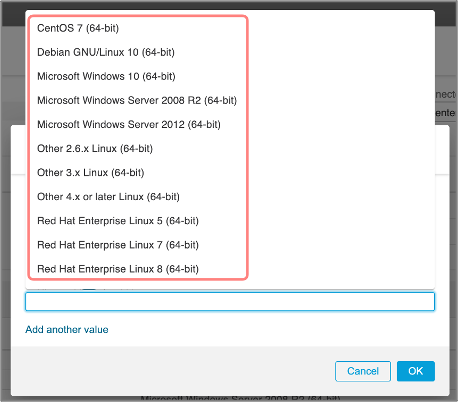
Figure 18: Selecting Values in a Condition
You can use Equals and Contains operands, as well as, select multiple values with ANY/ALL matching logic.
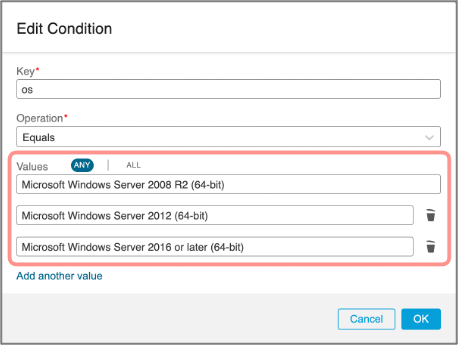
Figure 19: Adding Multiple Values to a Condition
CSDAC gives you the flexibility to configure a query with multiple conditions to match many Key/Value pairs at the same time.
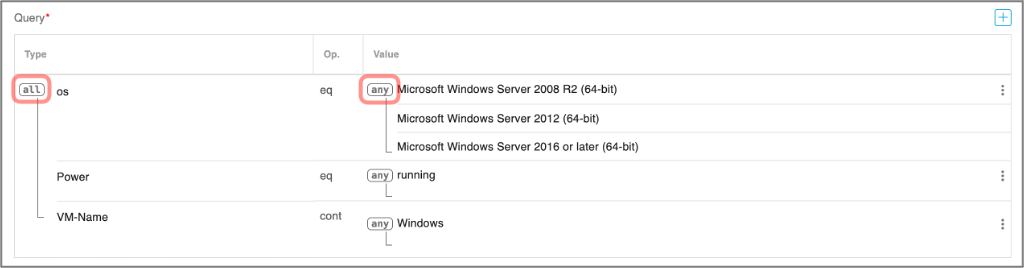
Figure 20: Adding Multiple Conditions to a Query
Once your query is complete you can observe the list of IP addresses in the preview that match the conditions.
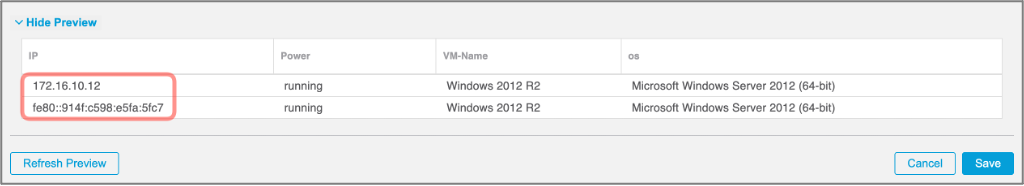
Figure 21: Dynamic Attribute Filter Preview
Note
You cannot configure dynamic attributes filters for GitHub, Office 365, or Azure Service Tags. For these public connectors, the CSDAC creates automatic filters, organizing IP prefixes into dynamic objects as per categories provided within the feeds.
Using CSDAC Provided Objects in the Firewall Rules
CSDAC polls the cloud providers periodically for a list of available VMs/instances and their attributes. When a change in a workload is detected, CSDAC sends an update to the FMC. You can review the list of IP addresses assigned to dynamic objects in the Firewall Managment Center in Objects > Object Management > External Attributes > Dynamic Object.
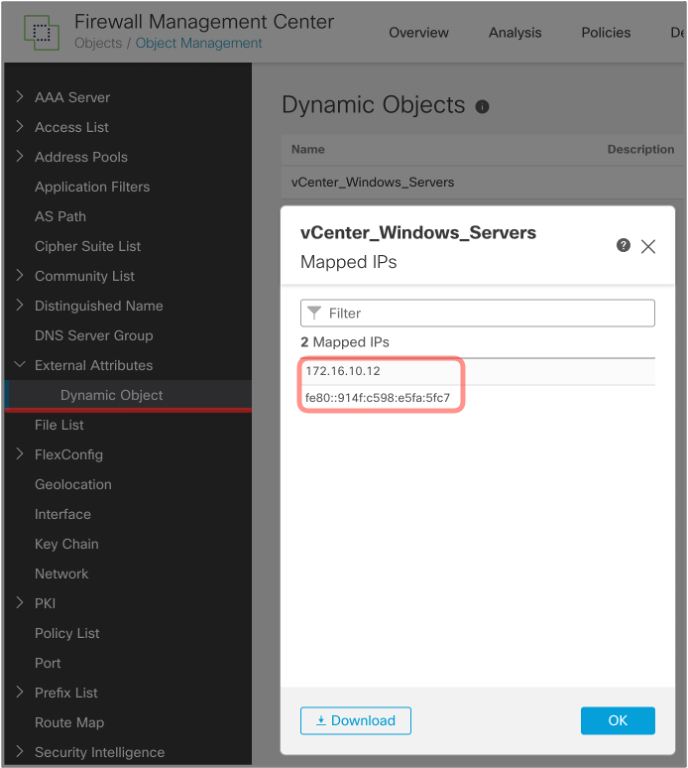
Figure 22: Viewing IP Addresses Mapped to a Dynamic Objects in Firewall Management Center
You can use Dynamic objects in the firewall rules in your Access Control Policy as both source and destination matching criteria.
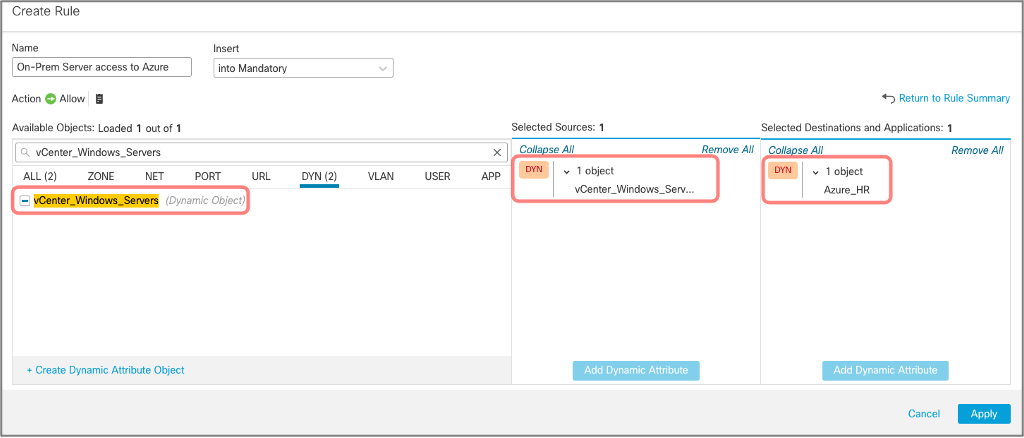
Figure 23: Using Dynamic Objects in an Access Control Policy
The Firewall Management Center distributes the change to the managed firewalls seamlessly, without deploying the policy or performing a Snort reload. This way, the firewall policy remains up-to-date, without any action from the administrator and with no interruption to traffic. The updates to dynamic objects propagate to the firewall in near real-time.
📚Additional Resources
Cisco Blogs:
Documentation and Configuration guides:
- Cisco Secure Dynamic Attributes Connector Configuration Guide 2.0
- Managing the Cisco Secure Dynamic Attributes Connector with the Cisco Defense Orchestrator
- Ansible CSDAC Collection
CSDAC videos on Cisco Secure Firewall YouTube channel:
- Cisco Secure Firewall 7.2 Release - Cloud Delivered Dynamic Attributes Connector
- Cisco Secure Firewall 7.1 Release - Dynamic Attributes Connector Update
- Cisco Secure Firewall 7.0 Release - Deployment of CSDAC
- Cisco Secure Firewall 7.0 Release - Dynamic Attributes Connector Integration with AWS
- Cisco Secure Dynamic Attributes Connector - VMware vCenter Integration
- Cisco Secure Firewall 7.0 Release: Identity - Dynamic Objects
Cisco Live! Security Sessions:
Updated over 3 years ago
