Elephant Flow Detection
Cisco Secure Firewall Elephant Flow Detection
Introduction
This document discusses the elephant flow detection and throttling features in release 7.2 of the Cisco Secure Firewall Threat Defense. An elephant flow is a long-lived connection and is generally quite large in the number of bytes transferred.
Elephant flows are important because they can potentially consume an inordinate amount of CPU resources. This can impact other competing flows for detection resources and cause issues such as increased latency or packet drops.
Elephant flow detection was introduced in release 7.1. Release 7.2 allows easier customization and the option to bypass or even throttle elephant flows. This capability replaces the Intelligent Application Bypass feature for Snort 3 devices running release 7.2 or later. Intelligent Application Bypass works by allowing users to define flow parameters to bypass Snort inspection. Elephant Flow Detection provides a similar function and adds the capability to throttle flows causing duress to Snort processes. Elephant Flow Detection is available for devices running Snort 3 on release 7.2 or greater.
In this document, the terms flow and connection are used interchangeably and mean the same thing – packets flowing between a source and destination host.
Configuration
Users can configure three elephant flow detection outcomes:
- Alerting - by adding a note to the Reason field in a connection event.
- Flow bypass* - this can be select for all flows or just flows matching selected application criteria.
- Flow throttling* - flows can be throttled by adjusting TCP window sizes to reduce the flow's CPU usage and prevent consequences such as high latency or packet drops.
Note
* Taking actions on an elephant flow is not supported on Firepower 2100 Series devices.
Once a flow exceeds the bytes and duration threshold, the system logs a connection event with Elephant Flow in the Reason field.
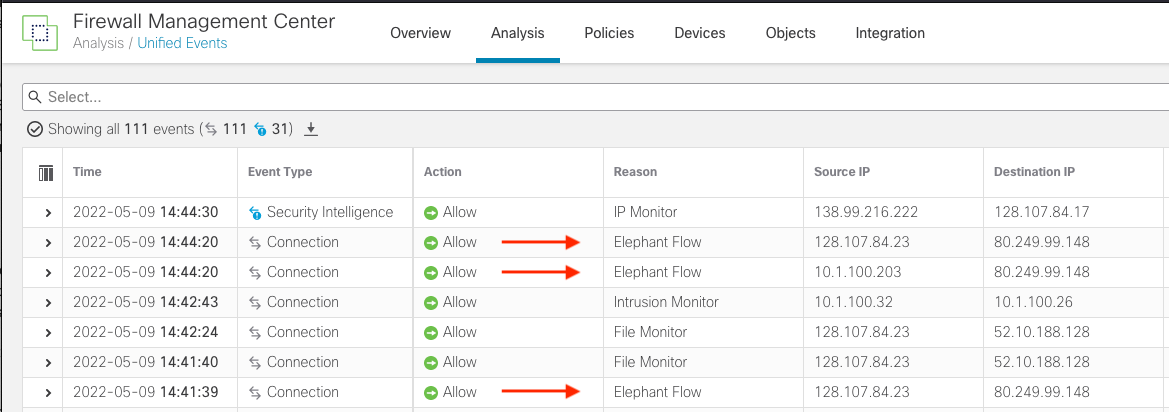
Unified Events View
Elephant flow detection is enabled by default. The system identifies any connection that transfers 1024 MB (1GB) and has a duration of at least 10 seconds. Connection events with "elephant flow" in the Reason column will be logged in mid-flow as soon as the threshold criteria is met.
Note
Enabling elephant flow detection alone will not generate additional connection events. Elephant flow detection will add the "Elephant Flow" notation to matching connections that are already being logged to the FMC. To log these events you must enable connection logging in your Access Control policy. You can do that for specific rules or add a Monitor rule, this will log all connections including elephant flows.
To view or configure additional settings, follow the steps below.
Step 1: Navigate to Policies -> Access Control and edit your Access Control policy.
Step 2: Click the Advanced tab and then click the pencil icon next to Elephant Flow Settings. The Elephant Flow configuration dialog will appear.
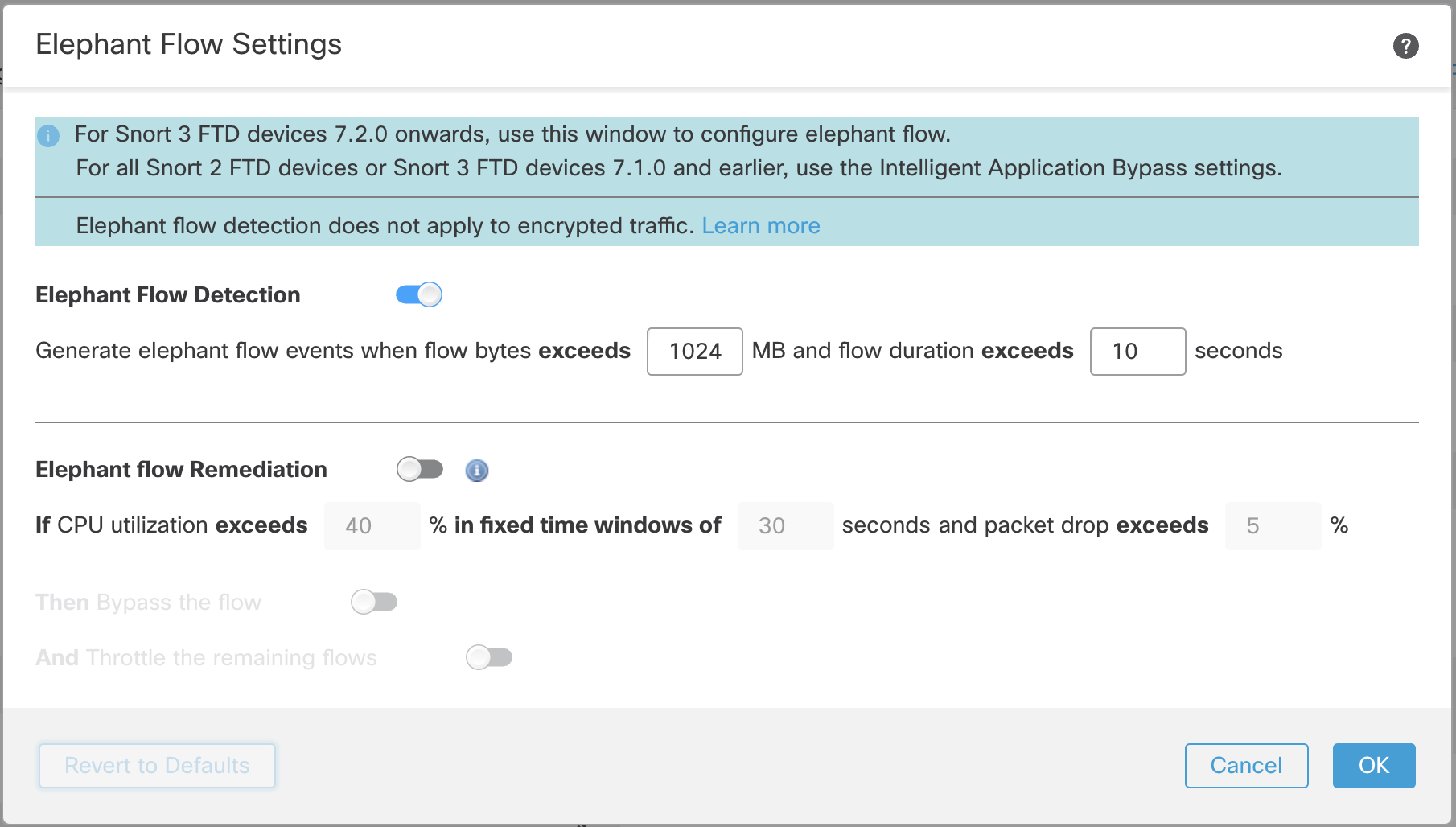
Elephant Flow Default Dialog
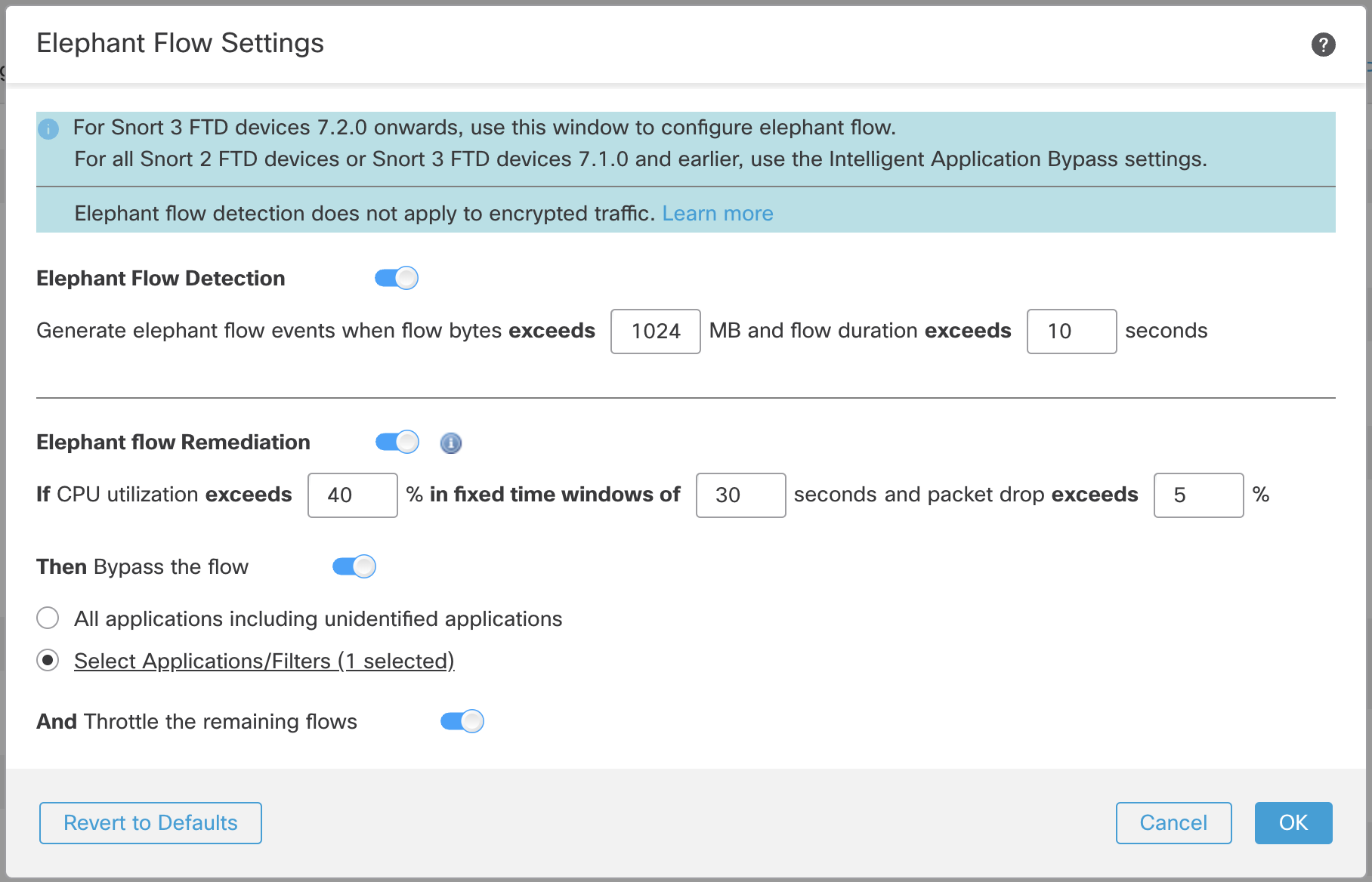
While the default setting enables detection, no default action is configured. The detection settings allow you to adjust the flow bytes and duration so you can identify the elephant flows on your system. Once you are satisfied that you have identified all the elephant flows, you can move on to taking action if desired by clicking the toggle next to Elephant flow Remediation.
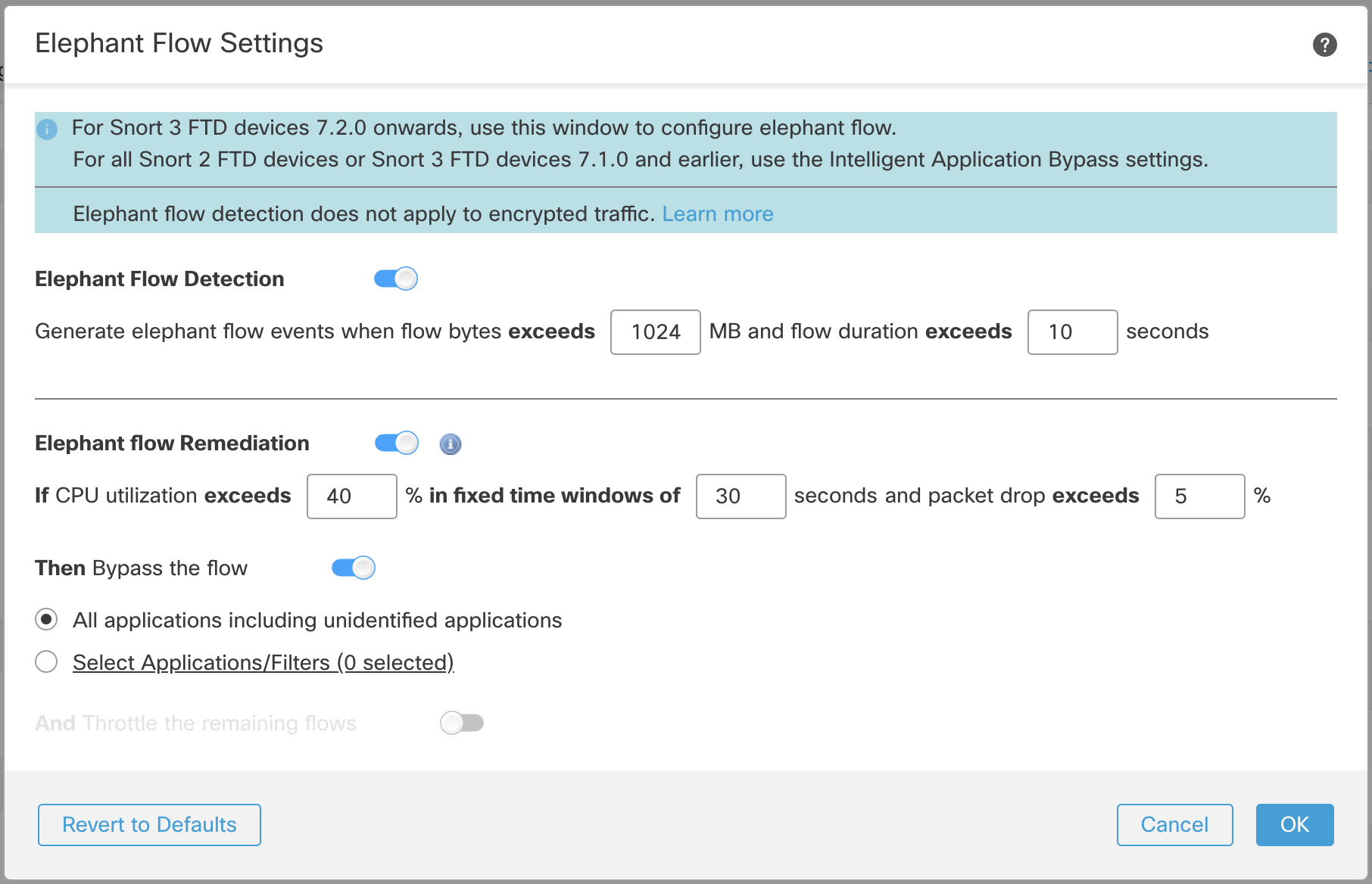
Elephant Flow Remediation Enabled
When an elephant flow is detected, you can choose to bypass or throttle the flow. Bypassing a flow means that the traffic is allowed to pass without Snort inspection. Throttling means the flow throughput is reduced. This is done in 10% increments until the CPU utilization is reduced below the configured threshold.
Note that bypassing or throttling takes place after identifying the elephant flow and meeting the additional CPU and time window parameters. Prior to this, the flow is processed by your intrusion policy - assuming you have configured this in an Allow rule. This means that elephant flows are not allowed to pass through the system completely uninspected. This is important to remember as the majority of attacks are detected very early in a connection.
To understand how flows are handled, see the flow diagram below.
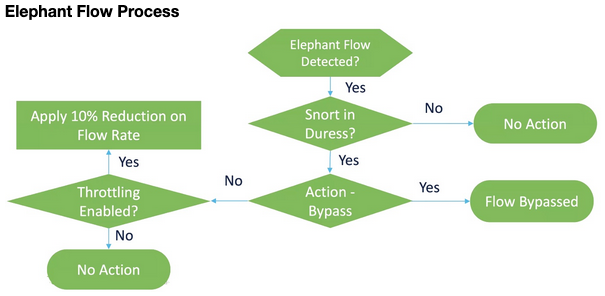
Elephant Flow Diagram
There are a couple of items worth highlighting in the flow diagram. First, note that no action will be taken unless a Snort duress condition is detected. This means Snort is having trouble processing all the flows/packets on a particular inspection thread. The system will not throttle or bypass a flow just because it’s large. Also, the actions of throttle and bypass are mutually exclusive. This means you can either bypass or throttle a flow but not both.
When you enable remediation you can then configure thresholds for Snort utilization and packet drop percentage. Note that for remediation to occur the device must exceed both of these thresholds. Once exceeding these thresholds, the system bypasses the flows that are causing Snort to be under duress. Of course, this means the flows are now passed without further Snort inspection.
If you do not want to bypass all elephant flows causing duress, you can go further by limiting the bypass option to specific applications. The idea is that you may have applications that are trusted and you want to prioritize connectivity for these without throttling performance. You would configure these applications to be bypassed but the remaining flows (causing duress) would be throttled. This ensures that the other non-trusted application flows still receive full Snort inspection although their bandwidth would be reduced.
To do this click the Select Applications/Filters radio button to select the applications that should be bypassed instead of being throttled. Upon clicking the radio button the application selection dialog will appear. In the example below we configured bypass for applications with low risk and high business relevance.
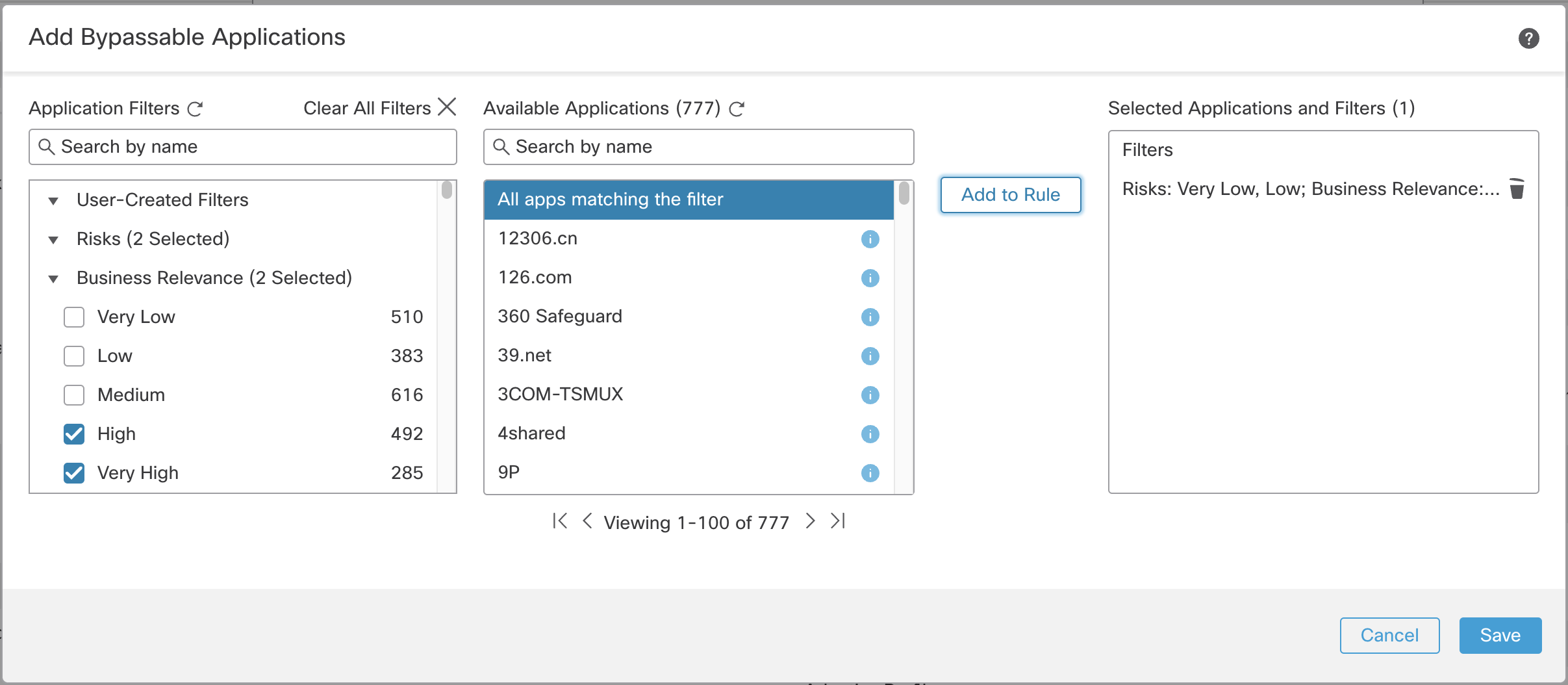
Application Selection Dialog
Once your application(s) are selected and you return to the main screen it will look something like the example below.
Elephant Flow with selected bypass
Once you have your Elephant Flow settings configured you should monitor your connection events to see if any flows are detected, bypassed or throttled. You will see this in the Reason field of your connection event. The three Reasons for Elephant Flow connections are:
- Elephant Flow
- Elephant Flow Throttled
- Elephant Flow Trusted
Remember, enabling Elephant Flow Detection alone will not cause connection events to be generated for elephant flows. If a connection event is already logged for another reason and the flow is also an elephant flow then the Reason field will contain this information. However, to ensure you are logging all elephant flows you must enable connection logging in the applicable Access Control rules.
Summary
The new Elephant Flow feature in release 7.2 gives users the ability to not only indentify elephant flows but to also take action by bypassing or throttling if desired. This provides an automated way to deal with large flows which may be impacting device performance as well as other flows which are not long running. Users can now choose to bypass or throttle flows based on selected applications to provide inspection of suspect traffic while bypassing more trusted traffic.
📚Additional Resources
Updated over 3 years ago
