Network Discovery Policy
Cisco Secure Firewall Network Discovery Policy Guidance
Introduction
This document provides network discovery policy configuration and deployment guidance. The Firewall Management Center (FMC) network discovery policy controls how the system collects asset data on an organization's network and which network segments and ports to monitor.
Network Discovery Policy
A discovery policy specifies the networks and ports that a Secure Firewall system passively monitors to generate discovery data based on the network traffic passing through the deployed firewalls. A discovery rule defines the hosts, applications, and non-authoritative users to monitor. Similarly, a discovery rule can exclude networks and zones from discovery.
Network Discovery Configuration
Step 1: Navigate to Policies > Network Discovery.
Step 2: Remove the default discovery rule (that includes 0.0.0.0/0 and ::/0 subnets) by clicking on the trash can on the right.
Note
We can't simply add host and user discovery to this default rule as it would result in host database entries for every IP address seen by the devices. This would likely result in using up the full licensed capacity for host storage on the FMC rather quickly. You should add a rule or rules specific to the hosts local to your network.
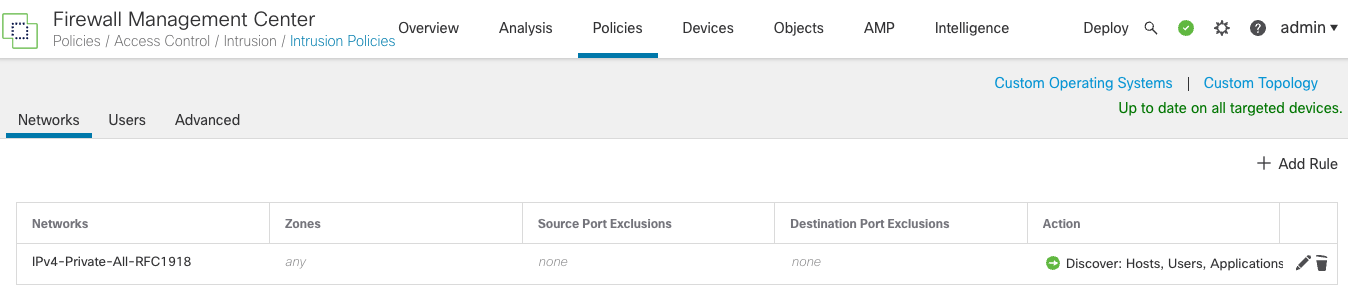
Figure 1: Discovery Rule
Step 3: Click Add Rule on the right side to add a discovery rule. The Add Rule window displays.
Step 4: Choose the predefined network objects or create new network objects that define your company's internal network precisely. (The screenshot below shows the available RFC-1918 IP addresses.) In a real-world deployment, this object should include only the internal networks that require profiling. The system IPv4-Private-All-RFC1918 network object may be suitable initially if the networks in use are unknown or for the discovery of rogue networks.
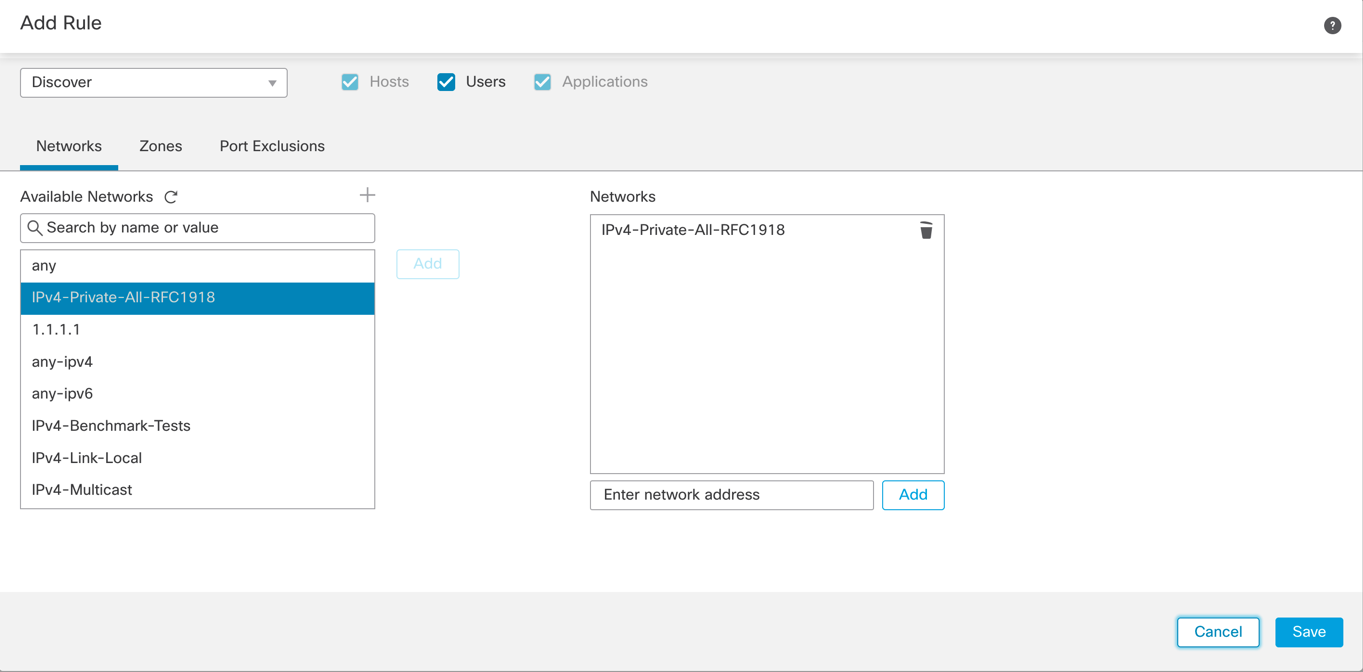
Figure 2: Discovery Rule Creation
Step 5: Choose an action from the drop-down menu at the top and then check one of the checkboxes. The following table describes possible actions, options, and functions.
| Action | Option | Function |
|---|---|---|
| Discover | Hosts | Adds hosts to the network map based on discovery events. (Optional, unless user discovery is enabled, then required.) |
| Discover | Applications | Adds applications to the network map based on application detectors. Note that the Secure Firewall system cannot discover hosts or users in a rule without also discovering applications. (Required) |
| Discover | Users | Adds users to the user's table and logs user activity based on traffic-based detection on the user protocols configured in the network discovery policy. (Optional) |
| Exclude | N/A | Excludes the specified network from monitoring. If the source or destination host for a connection is excluded from discovery, the connection is recorded, but discovery events are not created for excluded hosts. |
Table 1: Actions, Options, and Functions
Step 6: Possible hosts to consider for exclusion from monitoring include load balancers (or specific ports on load balancers) and NAT devices. These devices may create excessive and misleading events, which fill the FMC database. For example, a monitored NAT device might exhibit multiple updates of its operating system in a short period. However, excluding the NAT device from monitoring, the excessive and duplicate discovery events do not appear in the network map and no events are reported.
Step 7: Once the rule conditions are defined, click Save to save the discovery rule. The Discovery Policy window redisplays.
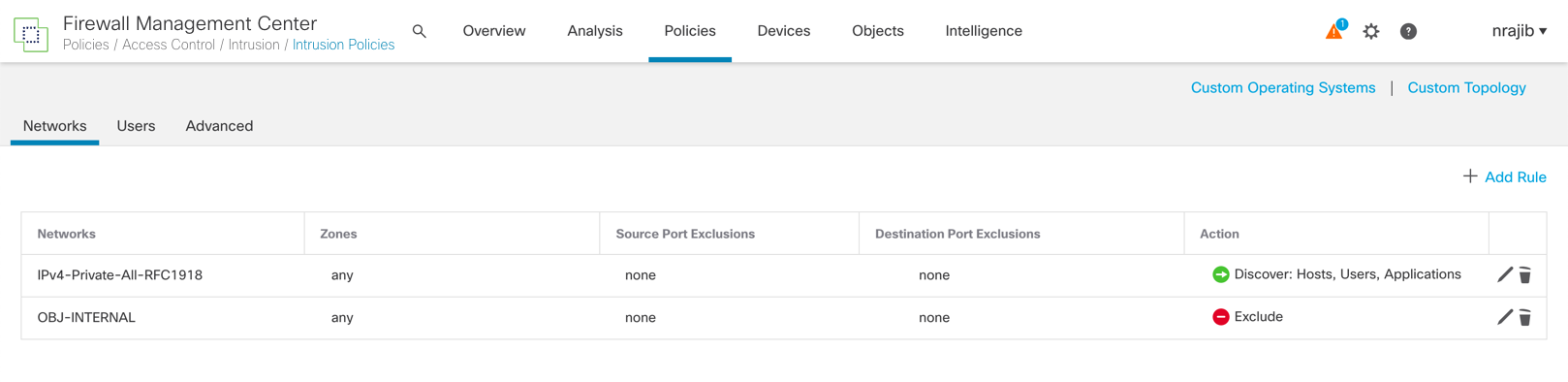
Figure 3: Discovery Rules with Discover and Exclude Action Examples
Step 8: From the Advanced tab, click the pencil icon to edit the General Settings. A pop-up window displays.
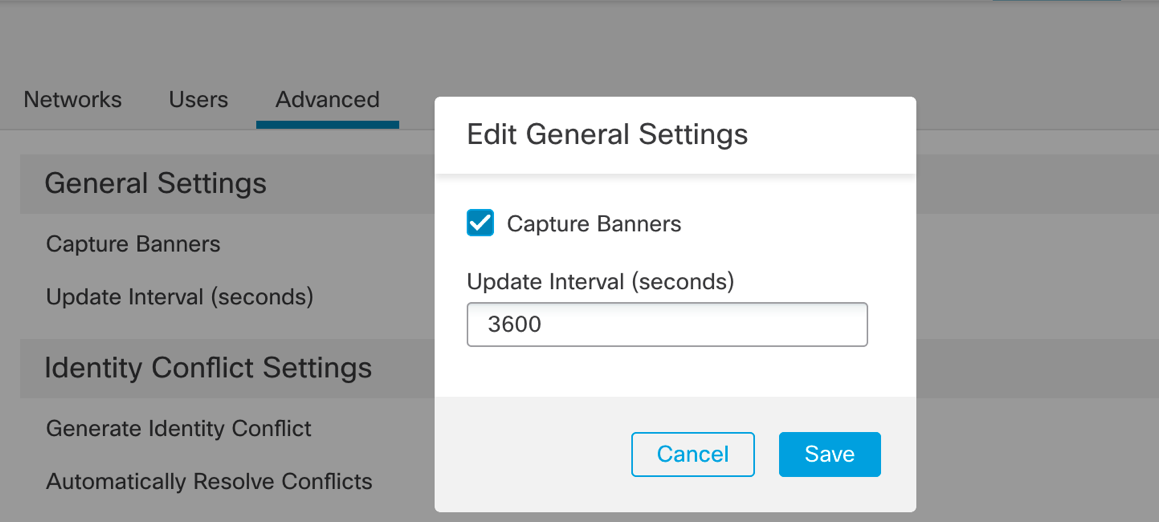
Figure 4: Enabling Capture Banners in the Advanced Settings
Step 9: Check the Capture Banner checkbox to store header information from network traffic that advertises server vendors and versions. This banner information can provide additional context to the information gathered during discovery.
Step 10: Deploy the discovery policy. Click Deploy, choose the desired FTD device(s), and then click the Deploy button.
Firewall Recommendations
The FMC starts building a network map as soon as a discovery policy is deployed and traffic is seen on managed devices with a discovery policy applied. After running a discovery policy for several days, the FMC creates a network map and host profiles with details about the operating systems, servers, and client applications running in an environment. The Firewall Recommendations feature allows an FMC to automatically use the discovery data to enable or disable intrusion rules to protect these assets.
Organizations can run Firewall Recommendations on an on-demand basis after introducing new hosts or services into the network. Firewall Recommendations allow the Secure Firewall system to automatically tune the intrusion policy for efficiency and to ensure the appropriate network protection. For example, if a network runs only the Windows operating system, intrusion rules that address vulnerabilities on a Linux or Mac OS don't need to be included. However, if Linux is introduced into the network, network discovery would update the host profiles and modify the Firewall Recommendations the next time it is run.
For guidance on Firewall Recommendations refer to the Intrusion Policy page.
Verification/Troubleshooting
Occasionally, the FMC may display health alerts for exceeding the discovery host/user limit. The FMC model determines the number of hosts and users a Secure Firewall system can monitor.
| Maximum network map size | FMC 1600 | FMC 2600 | FMC 4600 | FMCv | FMCv300 |
|---|---|---|---|---|---|
| Hosts | 50,000 | 150,000 | 600,000 | 50,000 | 150,000 |
| Users | 50,000 | 150,000 | 600,000 | 50,000 | 150,000 |
Table 2: Hosts and Users a System can Monitor
Here are two options for handling a situation where your FMC is hitting the host limit:
-
Upgrade the FMC to a higher model.
-
Fine tune your Network Discovery rule(s) network ranges. In our example above, we included the IPv4-Private-All-RFC1918 network range. If this range includes devices like IP phones or guest wireless networks, you can add additional rules to exclude these ranges. This will conserve host database entries for more relevant host entries.
Summary
The network discovery feature provides deeper visibility into a network environment, allowing the Secure Firewall administrator to take advantage of the Cisco Recommendations feature to enable an FMC to automatically optimize its intrusion policy or use it as a tuning reference. The combined network discovery and intrusion prevention functionalities save administrators time by automating policy optimization and reducing false positives alerts.
📚Additional Resources
To learn more about the network discovery policy on the Cisco Secure Firewall system, refer to the following publication:
Updated over 3 years ago
