Encrypted Visibility Engine
An overview of Cisco Secure Firewall's Encrypted Visibility Engine (EVE)
Introduction
Traffic inspection is one of the most important tools used by today’s firewall systems. However, encryption technologies like Transport Layer Security (TLS) present challenges to traditional deep packet inspection technologies. The inability to inspect packet payloads for encrypted traffic means key firewall capabilities are not available. Decryption technologies offer one solution to this issue. However, the process of decrypting traffic for inspection is resource-intensive. In addition, enabling decryption significantly reduces next-generation firewall throughput. There are also operational concerns, for example, certificate pinning makes decrypting some applications impossible. There may also be privacy or compliance issues for certain types of traffic, making decryption difficult or otherwise undesirable.
Cisco Secure Firewall Threat Defense offers several technologies to enhance encrypted traffic inspection without the need to implement full main-in-the-middle (MITM) decryption. The most recent of these is the Encrypted Visibility Engine (EVE).
About EVE
EVE is a new means of identifying client applications and processes utilizing TLS encryption. It enables visibility and allows administrators to take actions and enforce policy within their environments. EVE works by fingerprinting the Client Hello packet in the TLS handshake. By identifying specific application fingerprints in TLS session establishment, the system can identify the client process and take appropriate action (allow/block).
Currently, EVE can identify over 5,000 client processes. Secure Firewall, maps a number of these processes to Client Applications for use as criteria in Access Control rules. This gives the system the ability to identify and control these applications without enabling TLS decryption.
This capability also extends beyond just identifying Firefox or a TOR browser. By using fingerprints of known malicious processes, EVE technology can also be used to identify and stop malware. The malware identification feature is currently under development, and Cisco is constantly expanding the number of known fingerprints. As this capability matures, future releases will use EVE to identify and block encrypted malicious traffic without outbound decryption.
EVE brings another benefit, enhanced operating system identification. The system uses EVE to improve data accuracy in the Firewall Management Center’s host database built from passive host discovery. By leveraging EVE’s fingerprint technology, the system uses encrypted host communications to identify host operating systems better. This leads to better application and vulnerability data, thereby improving the accuracy of features such as Snort Recommendations.
How does it work?
EVE inspects the Client Hello portion of the TLS handshake to identify client processes. The Client Hello is the initial data packet sent to the server following the three-way handshake. As it turns out, the Client Hello gives a good indication of the client process on the host. This fingerprint, combined with other data such as destination IP address, provides the basis for EVE’s application identification.
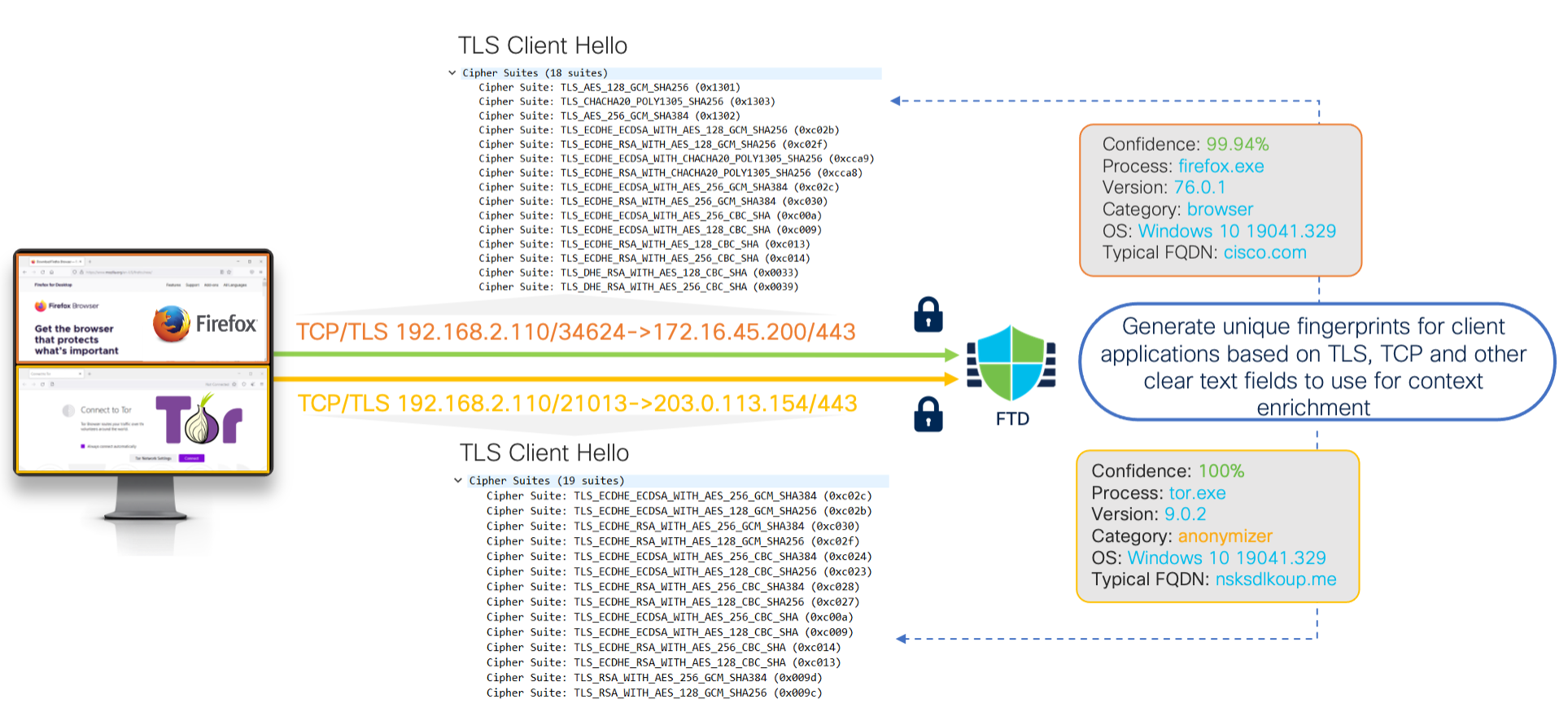
EVE Communications
Through machine learning (ML) technology, Cisco processes over one billion TLS fingerprints and over 10,000 malware samples daily to create and update EVE fingerprints. These updates are then delivered to customers via Vulnerability Database (VDB) packages.
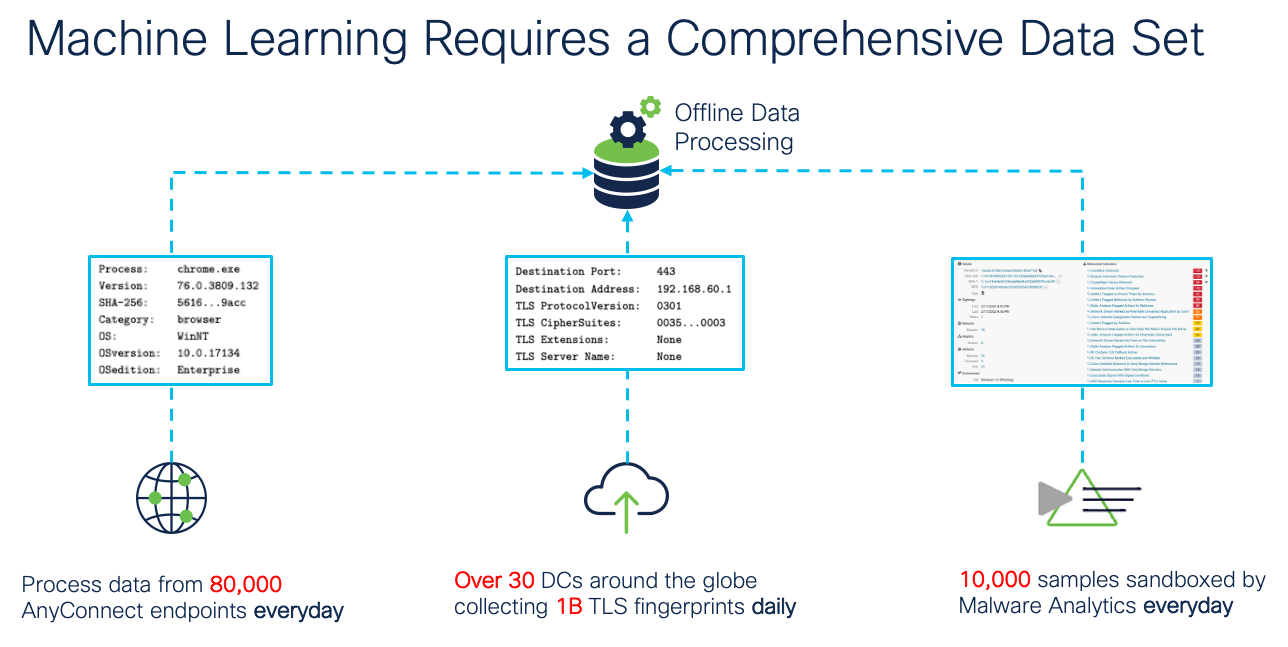
EVE Machine Learning
New in Release 7.4
Enhancements to EVE in release 7.4 include:
- Blocking Traffic based on EVE Threat Confidence Score
Overview
The Encrypted Visibility Engine (EVE) now provides means of leveraging the threat score to block malicious encrypted traffic. Administrators can adjust the threat score required for EVE to block potentially malicious traffic.
Release 7.4 introduces the capability to block traffic based on EVE Threat Confidence Score. This means that as EVE analyzes traffic, it assigns a score based on the probability that the traffic is malware. If the incoming traffic is deemed to be malicious, then based on the threat score, EVE can be configured to block the connection.
In the example below, EVE has identified the process _malware with a Encrypted Visibility Threat Confidence of Very High and a Threat Confidence Score of 100%. With the EVE settings configured to block malware, you will see an Action of Block and a Reason of Encrypted Visibility Block.
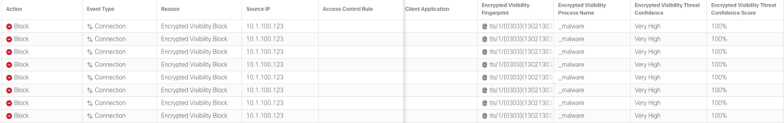
Encrypted Visibility Block Events
Configuring Block Thresholds
- Under the Advanced Settings of the Access Control Policy, click the pencil icon next to Encrypted Visibility Engine.
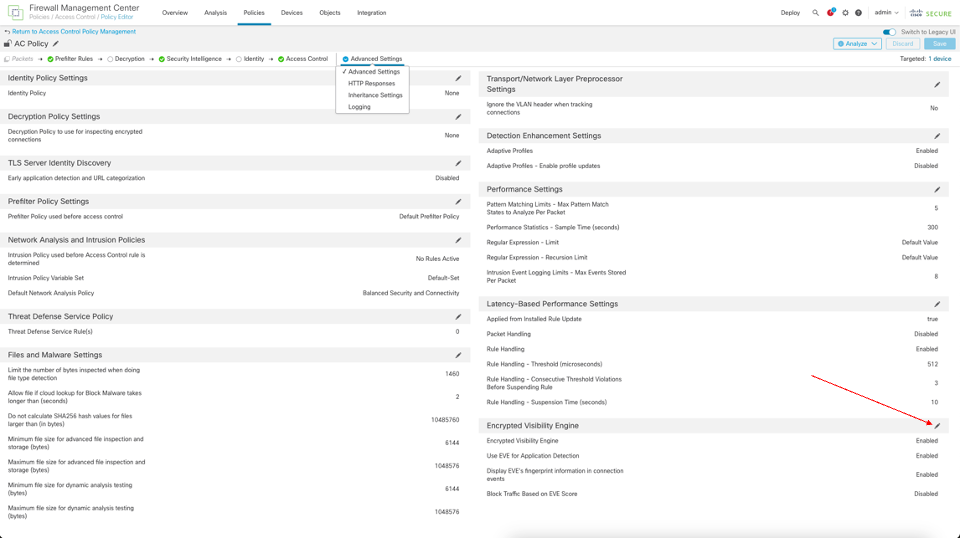
Advanced Settings
- Enable the toggle for Block Traffic Based on EVE Score
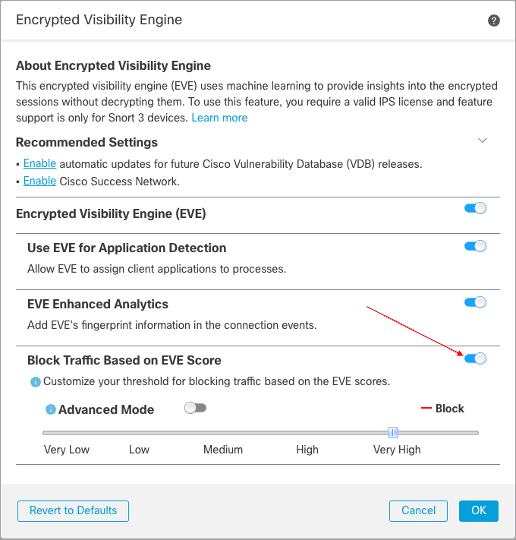
Enable Traffic Blocking Based on EVE Score
- You can use the slider to adjust the threshold for blocking based on EVE Threat Confidence. This ranges from Very Low to Very High and for this example we will adjust the slider to High.
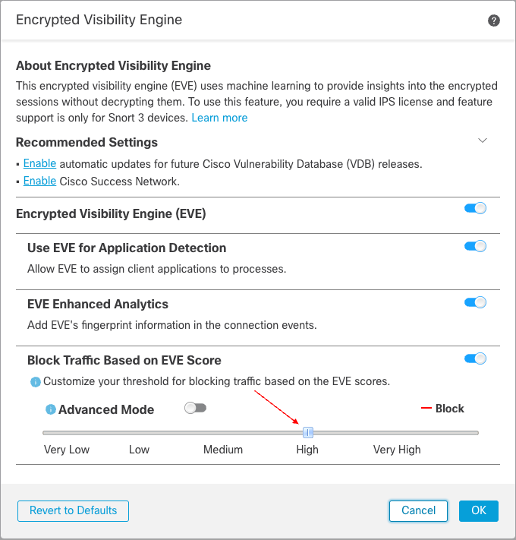
Adjust Blocking Threshold
(Optional) If you should need further granular control, enable the Advanced Mode toggle. Now, you have the ability to assign a specific EVE Threat Confidence Score for blocking traffic. For example if EVE assign a Threat Confidence Score of 80 or higher, the traffic will be blocked. When the Advanced mode toggle is enabled, the default value is 80.
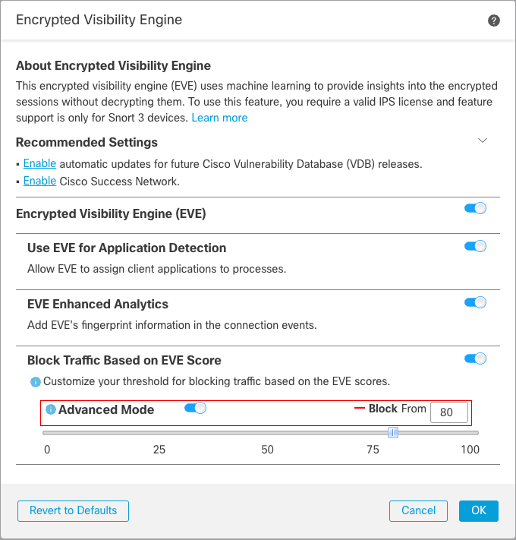
Adjust Blocking Threshold Using Advanced Mode
- Now that you have configured the thresholding settings, Save and Deploy your policy.
No other configuration is necessary. Once this feature has been enabled, EVE will block connections if the assigned Threat Confidence Score is above the configured threshold.
Using EVE
Step 1: Enable the toggle on the Access Control policy Advanced tab as shown below.
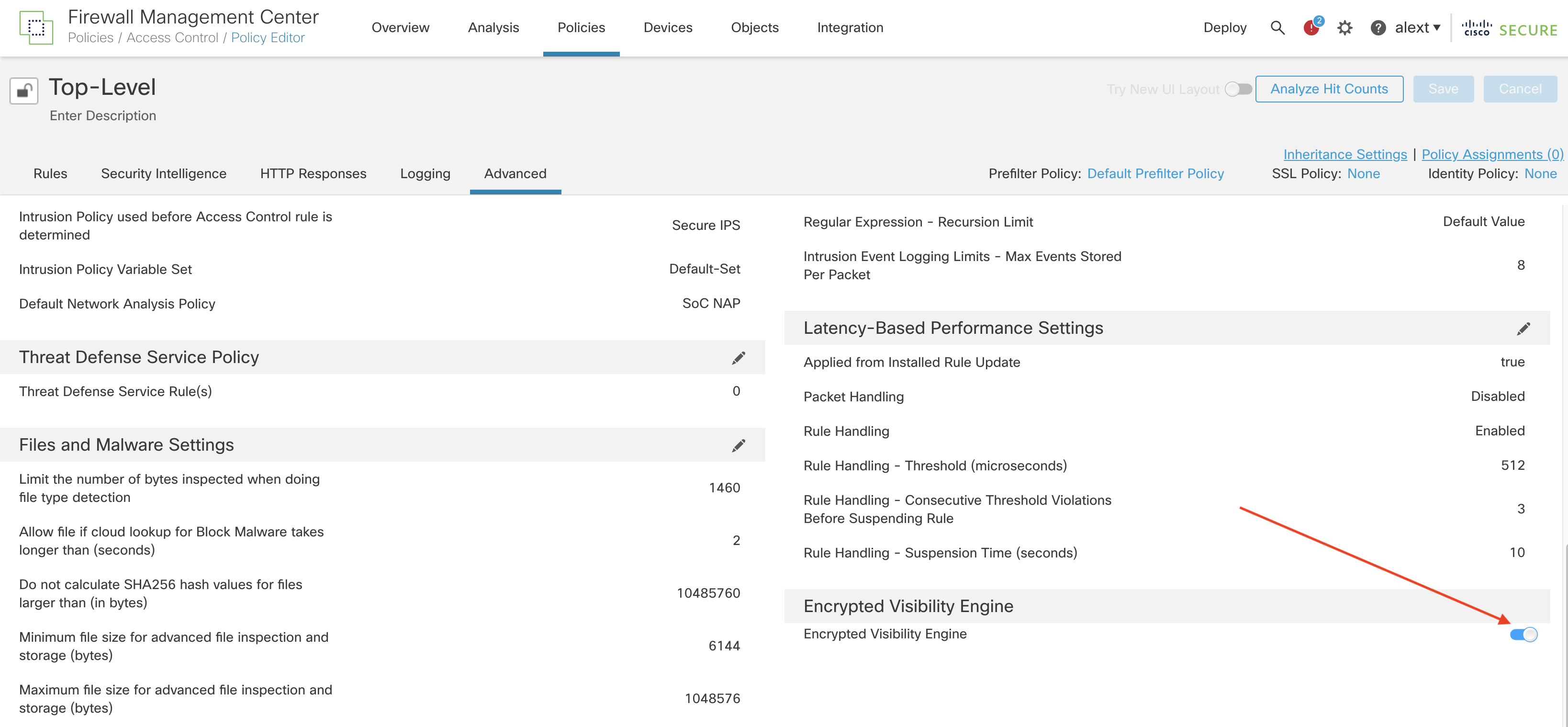
Step 2: Save and Deploy your policy.
That’s it! No other configuration is needed. Once you enable EVE, the system begins to identify client processes and applications.
View Events
After enabling EVE, you can view your connection events to see what EVE detects. An easy way to do this is via the Unified Events view (Analysis -> Unified Events) and adding some additional columns to the default view. To do this follow the steps below.
Step 1: Click the icon above the leftmost column on the screen to load the column selector.
Step 2: Check the boxes by Client Application, Encrypted Visibility Process Confidence Score and Encrypted Visibility Process Name. Then click Apply.
The added columns appear on the right side of the screen, you may need to scroll right to see them. If desired, you can grab them by clicking the column heading and dragging left or right to reorder. In the screenshot below, the Web Application column was moved to sit just to the left of Client Application.
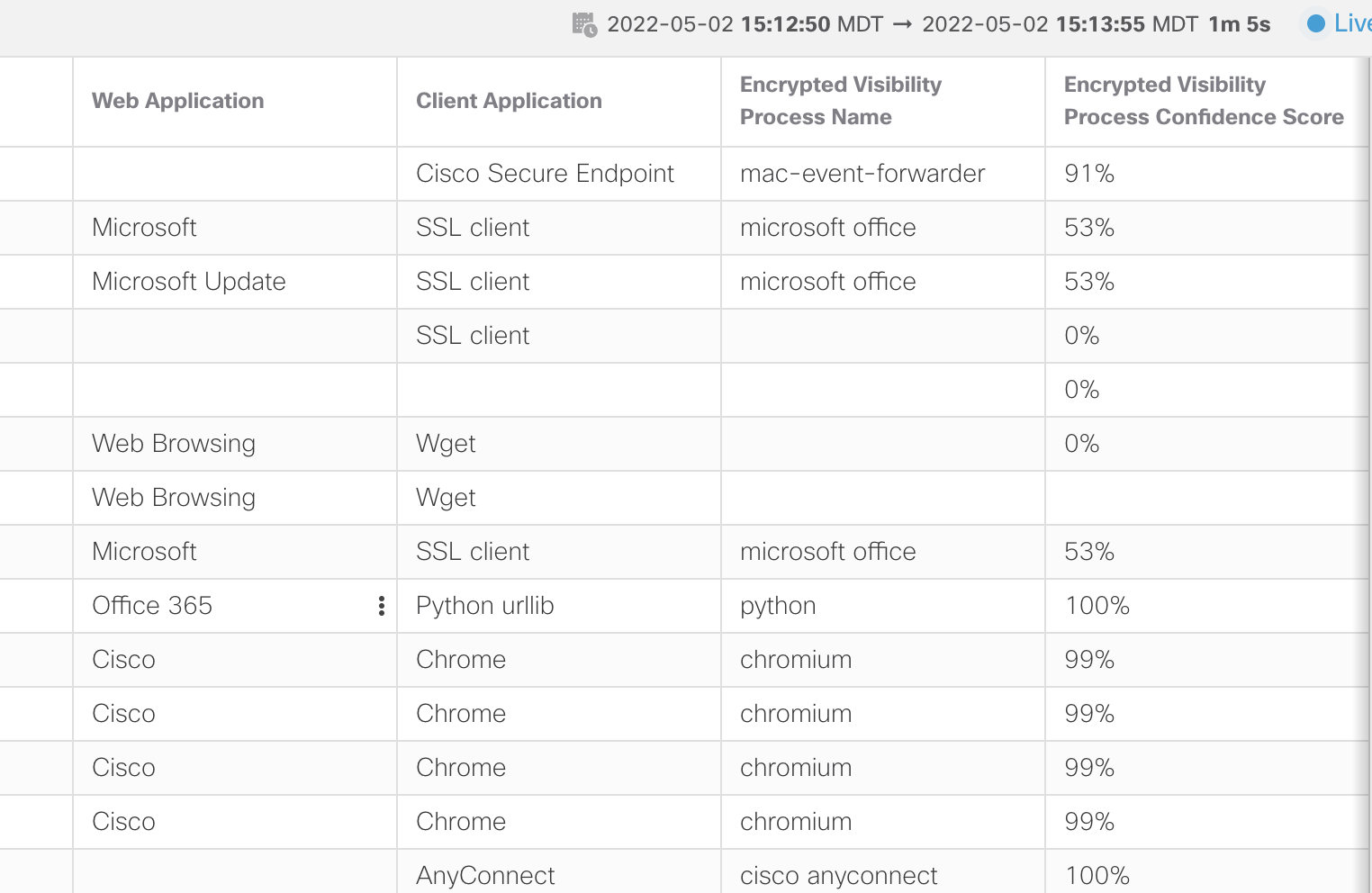
Unified Events VIew
Notice when the Encrypted Visibility Process Confidence Score is high the Client Application is updated with the EVE process. Although microsoft office was detected in the example above, the confidence score was not high enough to change the Client Application. However, for the high percentage scores, the Client Application column reflects the Encrypted Visibility Process Name.
Analyzing event data can help you understand what processes EVE is helpful in identifying. You can then use this data to help write Access Control rules to control your client applications.
EVE Dashboard
A new Dashboard tab has been added for EVE. After enabling EVE, you may want to let it collect data for a while. After that, you can follow the steps below to view EVE statistics.
Step 1: Navigate to Overview -> Dashboards.
Step 2: Click the switch dashboard link and select Application Statistics
Step 3: Click the Encrypted Visibility Engine tab.
Step 4: Select your time window to view the last hour, 6 hours, day, week, etc.
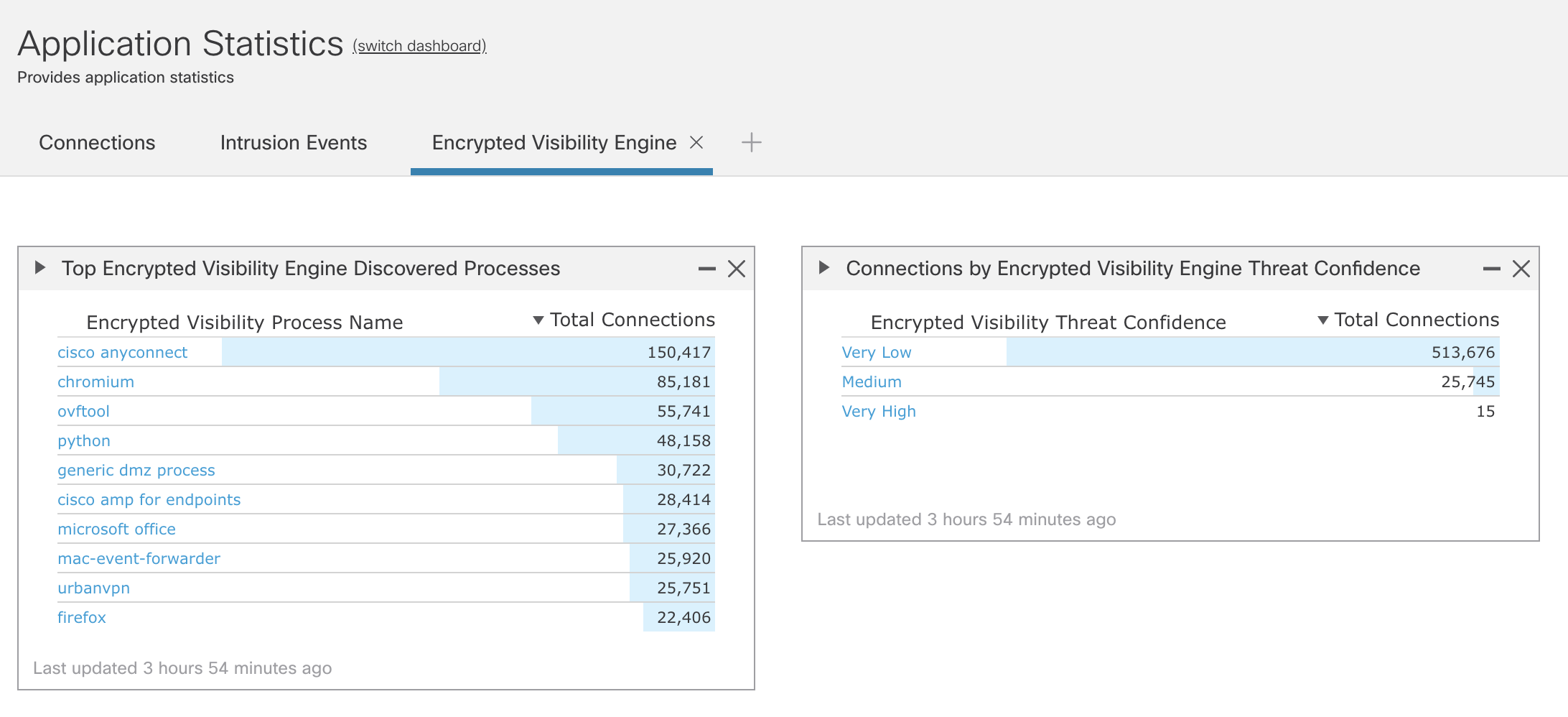
EVE Dashboard
EVE Applications
To see the current EVE client applications list.
Step 1: Navigate to your Access Control policy (Policies -> Access Control).
Step 2: Edit your policy, add a rule or edit an existing rule.
Step 3: In the rule, click the Applications tab.
Step 4: In the left section expand the the Tags section. Or just type “encrypted” into the Search by Filter Name field.
Step 5: Check the encrypted visibility engine tag to see the Applications.
In the example below, there are 236 client applications currently identifiable by EVE.
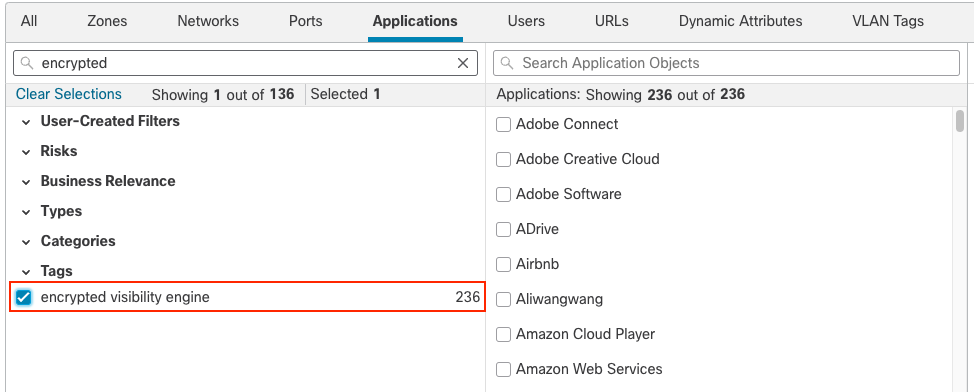
Note that while EVE can identify over 5,000 processes the number of applications currently mapped to these is lower. However, keep an eye on this list as it will grow as additional client applications are associated with EVE processes.
Summary
The Encrypted Visibility Engine is an exciting new feature that allows insight into encrypted communication processes without decryption and is available with the Secure Firewall Threat license. This feature provides an important capability in your threat detection toolbox and is an easy and risk-free way to provide additional encrypted traffic visibility and security.
Updated over 2 years ago
