Umbrella SIG Auto-Tunnel Configuration
Cisco Secure Firewall Umbrella Connector
Introduction
In Release 7.2, the tunnel configuration between Cisco Secure Firewall and Umbrella Secure Internet Gateway (SIG) required users to configure tunnels manually on the FMC and in the Umbrella User Interface (UI) to configure the SIG. And then, in the Secure Firewall Management Center (FMC), configure the Umbrella as an Extranet peer.
Starting in release 7.3, the Firewall Management Center (FMC) supports Auto-Tunnel configuration for Umbrella Secure Internet Gateway (SIG) integration, which enables a network device to forward all internet-bound traffic to Umbrella SIG for inspection and filtering via the SIG tunnel.
Additional improvements introduced include:
- A new simplified wizard-based user interface (UI) and Site-to-Site VPN named Secure Access Service Edge (SASE) to configure Umbrella tunnels.
- Pre-shared key auto-generation and population, virtual tunnel interfaces, and default IKE and IPsec policies to ensure minimal configuration.
- Ability to create and deploy network tunnels directly to Umbrella from the FMC, along with increased tunnel monitoring.
The Umbrella SIG Integration in Action
The FMC leverages the Umbrella Integration introduced in 7.2 (Umbrella DNS Connector) and invokes Umbrella APIs to configure network tunnels using the connection. The FMC fetches the list of Umbrella Datacenters and displays them in the UI for selection as a Hub in the SASE Topology. Then, pre-shared key-based authentication is used with an auto-generated manual PSK (several automated default configurations like IKE, IPsec policies, etc.).
Note
For the auto-tunnel configuration to work correctly, use the latest Umbrella SIG version, have an Umbrella integration with a configured management key on the FMC, and Route-Based VPN support with Local Tunnel ID on the Secure Firewall in place.
With the tunnel created, network devices use the SIG tunnel to pass all traffic through Umbrella for inspection.
Umbrella Auto-Tunnel Configuration
Prerequisites:
- To configure network tunnels on Umbrella, Cisco Umbrella SIG Essentials subscription or a free SIG trial is required.
- One Umbrella account per FMC (an HA pair uses one account)
- Export-Controlled enabled on the Secure Firewall Management Center (FMC)
- The FMC can reach management.api.umbrella.com
️Warning
This document does not cover the basics of the Umbrella SIG Policy configuration in the Umbrella Dashboard. You can read more about it here.
Umbrella SIG Integration in Secure Firewall Management Center
Step1: From the Global Search in the FMC, type Cloud Services and click on the Navigation result shown.
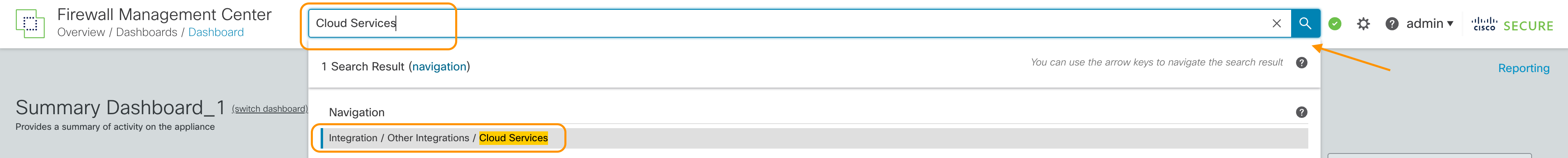
Cloud Services Navigation
Step 2: Scroll down to the Cisco Umbrella Connection widget, and enter the following details by going to your Cisco Umbrella instance to enable the integration.
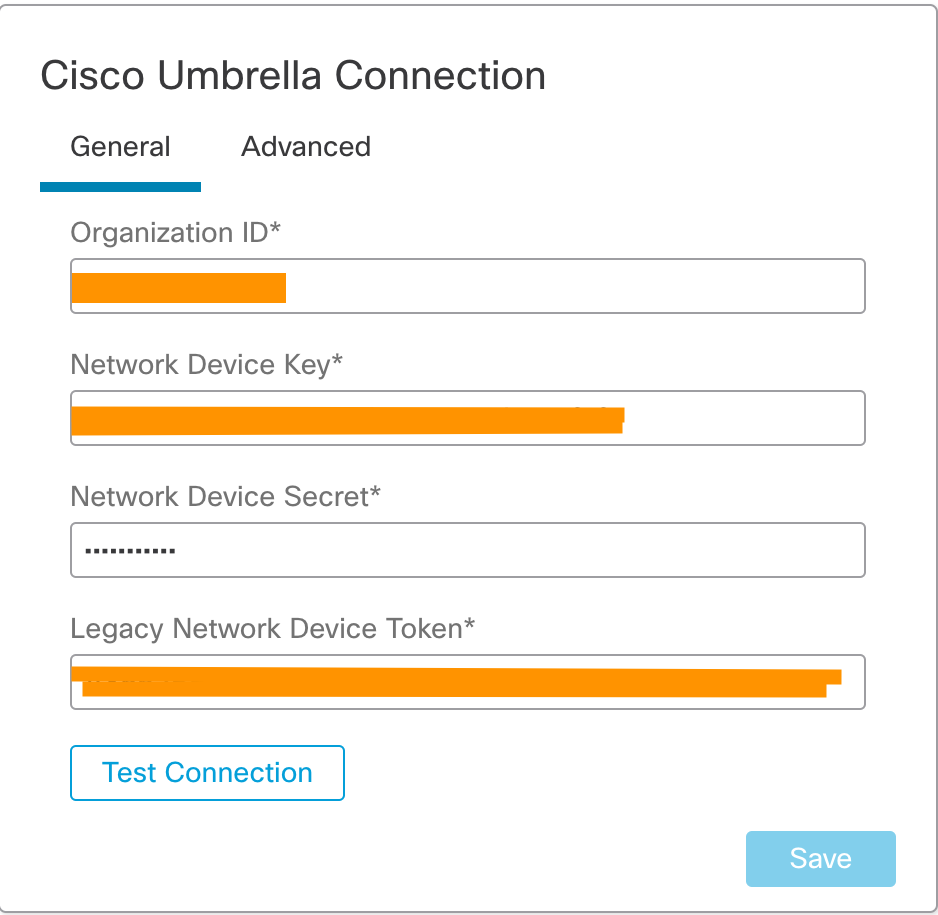
Cisco Umbrella Connection widget in Firewall Management Center
Cisco Umbrella Connection Mandatory Settings explained
Organization ID, Network Device Key, and Network Device Secret are used to identity the Umbrella account and fetch the associated Umbrella DNS policies.
The Legacy Network Device Token is used by the Secure Firewall to register with the Umbrella account and forward the DNS requests to the account.
If you have multiple Umbrella Organizations, ensure that you switch to the correct Organization.
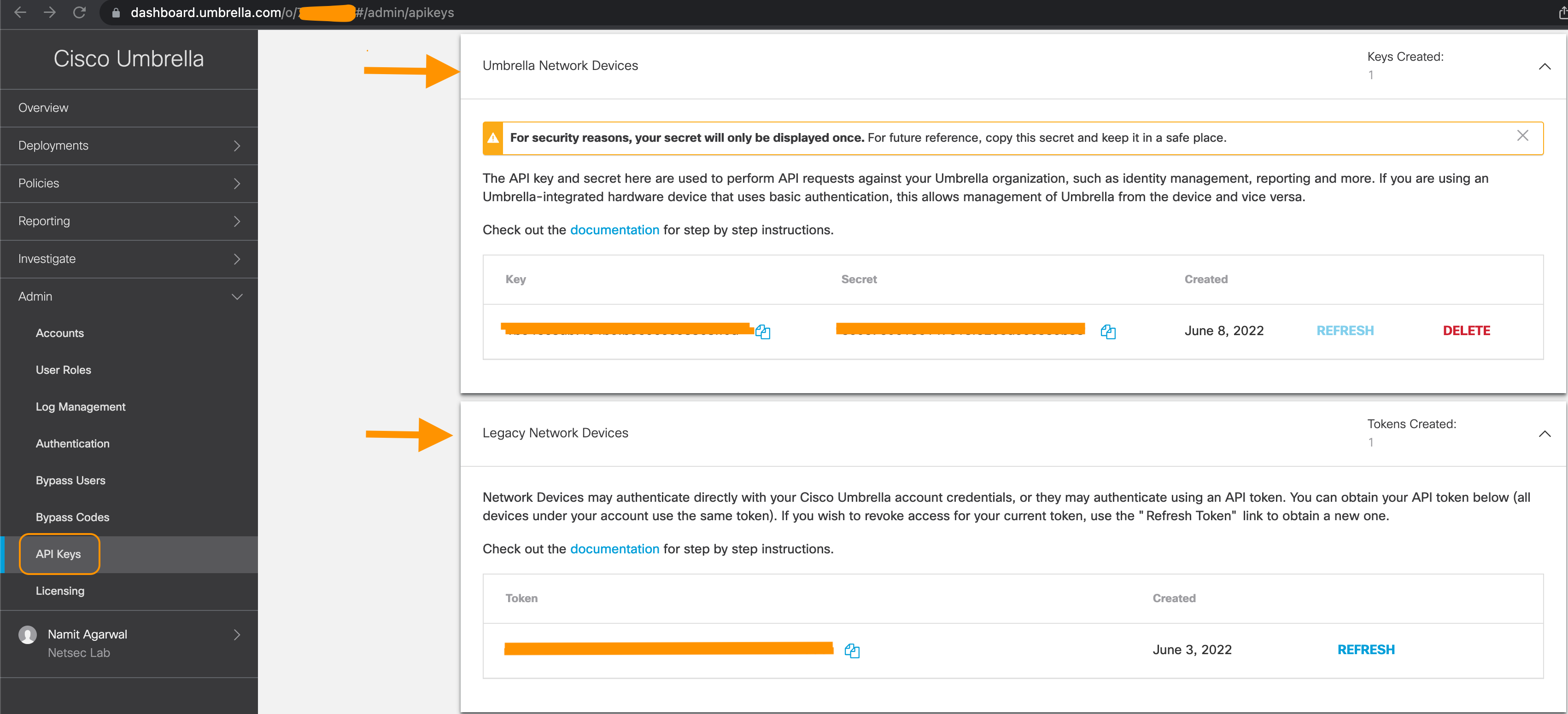
Step 3: Login to your Umbrella Dashboard and navigate to Admin > API Keys
Cisco Umbrella Admin - API Keys
https://dashboard.umbrella.com/o/[OrganizationID]/#/admin/apikeys
Step 4 Copy the number displayed in the URL and paste it under Organization ID in the Umbrella Connection Details within the FMC instance.
Step 5 Next, click on the Legacy Keys tile and select the Umbrella Network Devices
- If the Key and Secret are not available or known, click on Refresh to generate a Key and Secret pair
- Copy the Key and paste it under Network Device Key in the Umbrella Connection Details page on FMC
- Copy the Secret and paste it under Network Device Secret in the Umbrella Connection Details page on FMC
Step 6 Click on Legacy Network Devices
- If the Key is not available or known, click on Refresh to generate a Key
- Copy the Key and paste it under Legacy Network Device Token
The screenshot below shows an example:
Umbrella Dashboard with the Integration Details
Step 7: After entering all the details in the Firewall Management Center, click Test Connection. The connection test is initiated from the Firewall Management Center and should be successful, as shown below. If the test fails, please validate the Umbrella settings and ensure that the Firewall Management Center has internet connectivity. Click Save when the test succeeds.
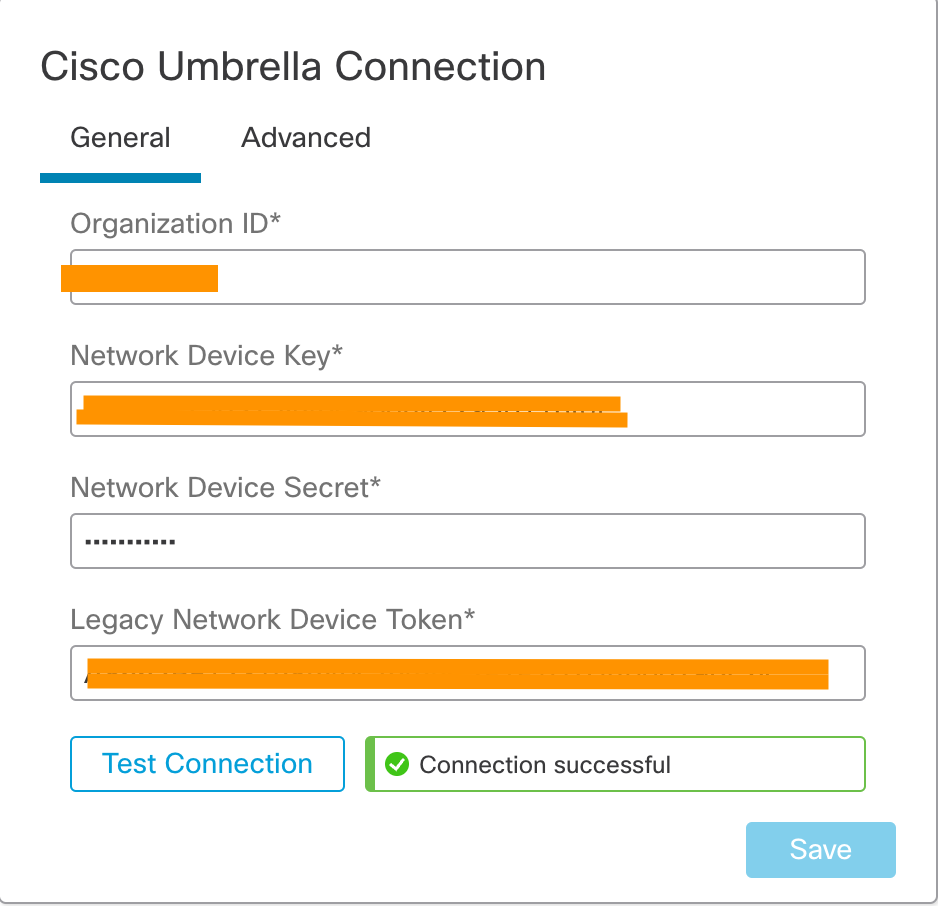
Successful Connection Test
Umbrella Auto-Tunnel Configuration
With the Umbrella Connection in place, the next step is to set up the auto-tunnel using the FMC SASE topology wizard.
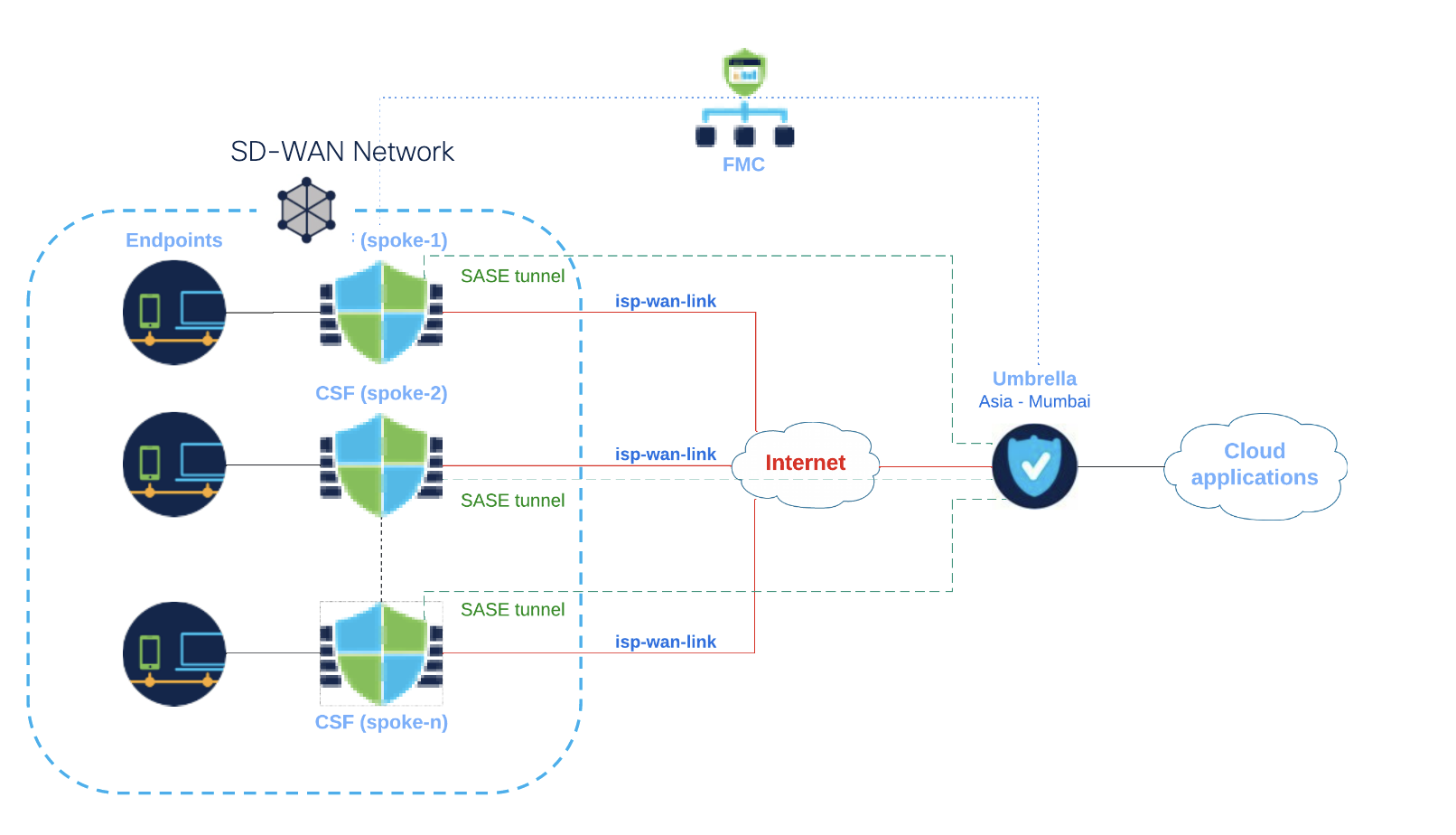
Example Deployment Use case
Step 1 Start in the Cisco Umbrella instance and grab the Umbrella Management Key and secret pair from Admin > API Keys > Legacy Keys.
Warning
If the Umbrella Management Keys are already present, you might need to refresh the keys to generate a new key and secret pair which could break any API integration using Umbrella Management Keys.
Umbrella Management Key
Step 2 Copy the key, then go to the FMC instance and select Integration > Other Integrations > click Advanced under the Cisco Umbrella Connection > then paste the management key & secret into the corresponding fields.
Note
If the secret key isn't visible, click refresh. Also, make sure to check for a successful connection by clicking "Test Connection" before saving.
Umbrella Integration Advanced Inputs
Step 3 Next, in the FMC, select Devices > VPN > and click Site to Site.
VPN Site to Site
Step 4 Click +SASE Topology in the top right to launch the create wizard.
+SASE Topology
Step 5 The Create SASE Topology window appears with the Pre-Shared Key pre-populated with an auto-generated value adhering to the PSK requirements on Umbrella (i.e., length of the key, the combination of alpha-numeric characters case and symbols etc.).
Note
The Pre-Shared Key is common for all the Secure Firewall spokes and Umbrella Data Center which are part of a SASE topology.
Step 6 Now add a Topology name and select the Umbrella Data Center. Here it is recommended to use the one closest to your location or as required by your company policy.
Create SASE Topology
Step 7 With everything in place, press the Add button to open the endpoint dialog box and perform the following:
- Select a device
- Pick a static VTI Interface or click on the '+' button to create a new static VTI
- If creating a new static VTI, the Add Virtual Tunnel Interface dialog box will open up with all values prepopulated. Review the values and Click OK to save and again to acknowledge the creation of the new Virtual Tunnel Interface.
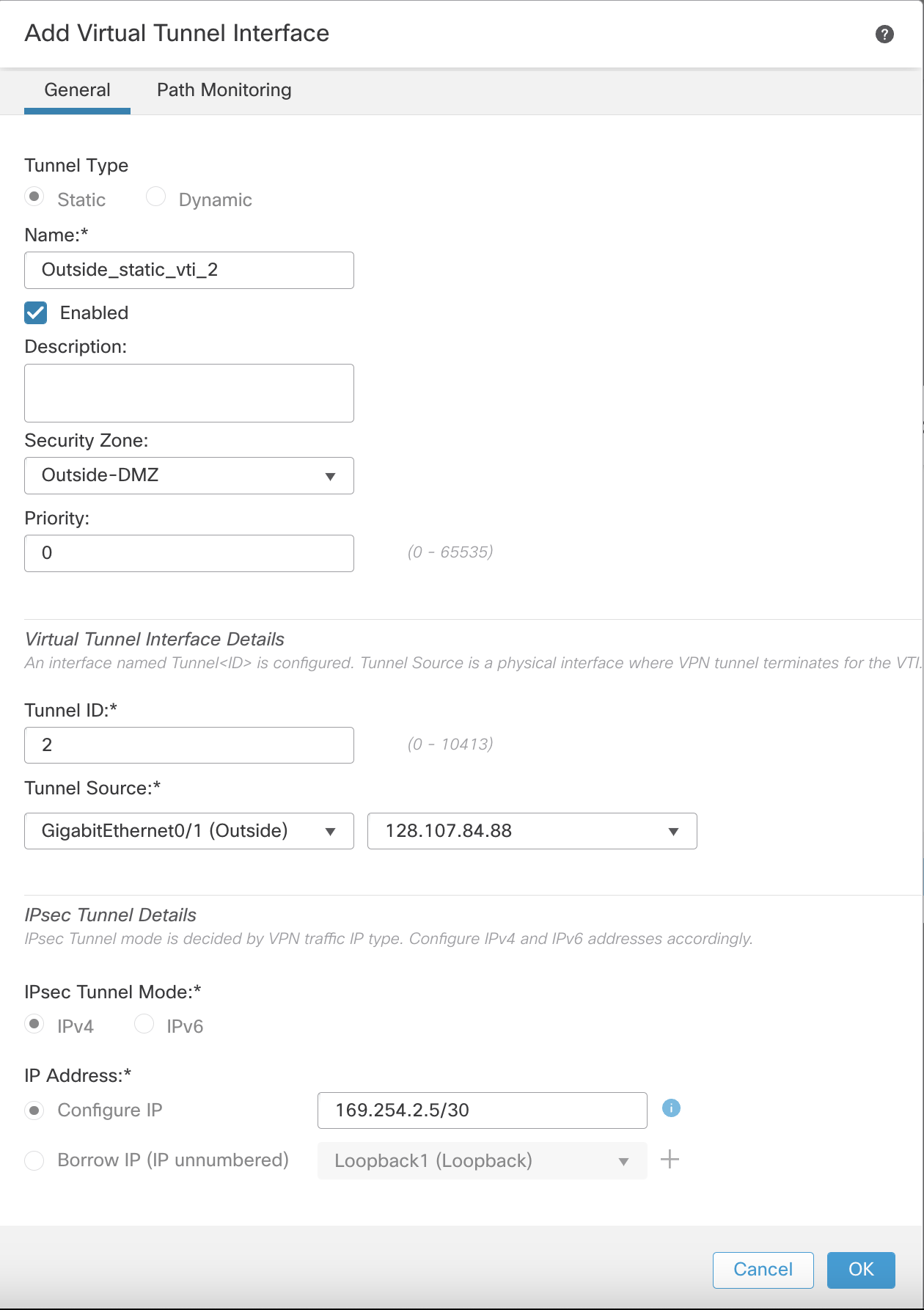
Add Virtual Tunnel Interface
Note
Creating VTIs on the fly is quick because the fields are auto-populated with values. Users only need to review and click "OK" to generate one.
- Enter the prefix for Local Tunnel ID. The complete tunnel ID (@-umbrella.com) will be generated on Umbrella once this prefix is configured and deployed on Umbrella by FMC. FMC will then retrieve and update the complete Tunnel ID and deploy it on FTD.
- Click Save
Adding an Endpoint
Step 8 Repeat Step 7 to add more Nodes. Once all the Nodes/devices have been added to the Topology, click Next to go to the summary page. Here, a summary of the topology created is shown with relevant information. If you are satisfied everything is correct, click Save.
SASE Topology Summary
Step 9 Upon clicking save, a pop-up window will show you the Tunnel Configuration Status and if it is successful.
Note
If interested in seeing the Deployment transcript, simply click the icon with the paper and magnifying glass under Transcript.
Tunnel Configuration Status
Congratulations on setting up the Umbrella Auto Tunnel!
Reviewing and Monitoring on FMC
- To see the tunnel status, go to Devices > Site To Site
- To view the updated tunnel ID, click the pencil icon
Tunnel Status and ID Review
- To view the Tunnel, go to Overview > Site To Site VPN
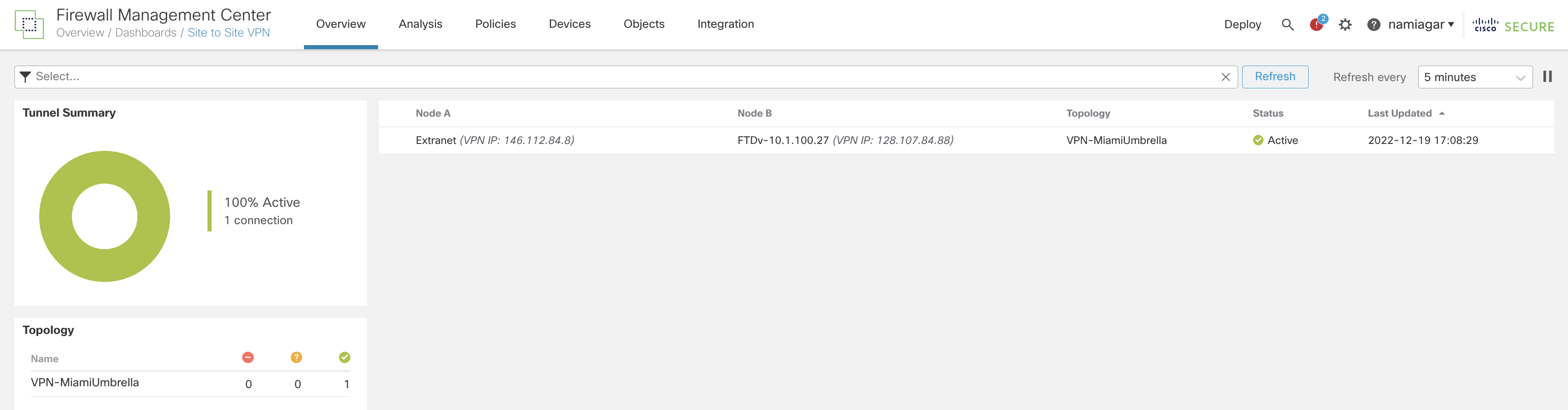
Tunnel Status Dashboard
Reviewing the Tunnel status and configuration on Umbrella Dashboard
Step 1 If not logged into the Umbrella dashboard, log in to the Umbrella dashboard and ensure you are in the correct organization account.
Step 2 On the overview page, you can see the Deployment Health. It shows the number of Active Network Tunnels
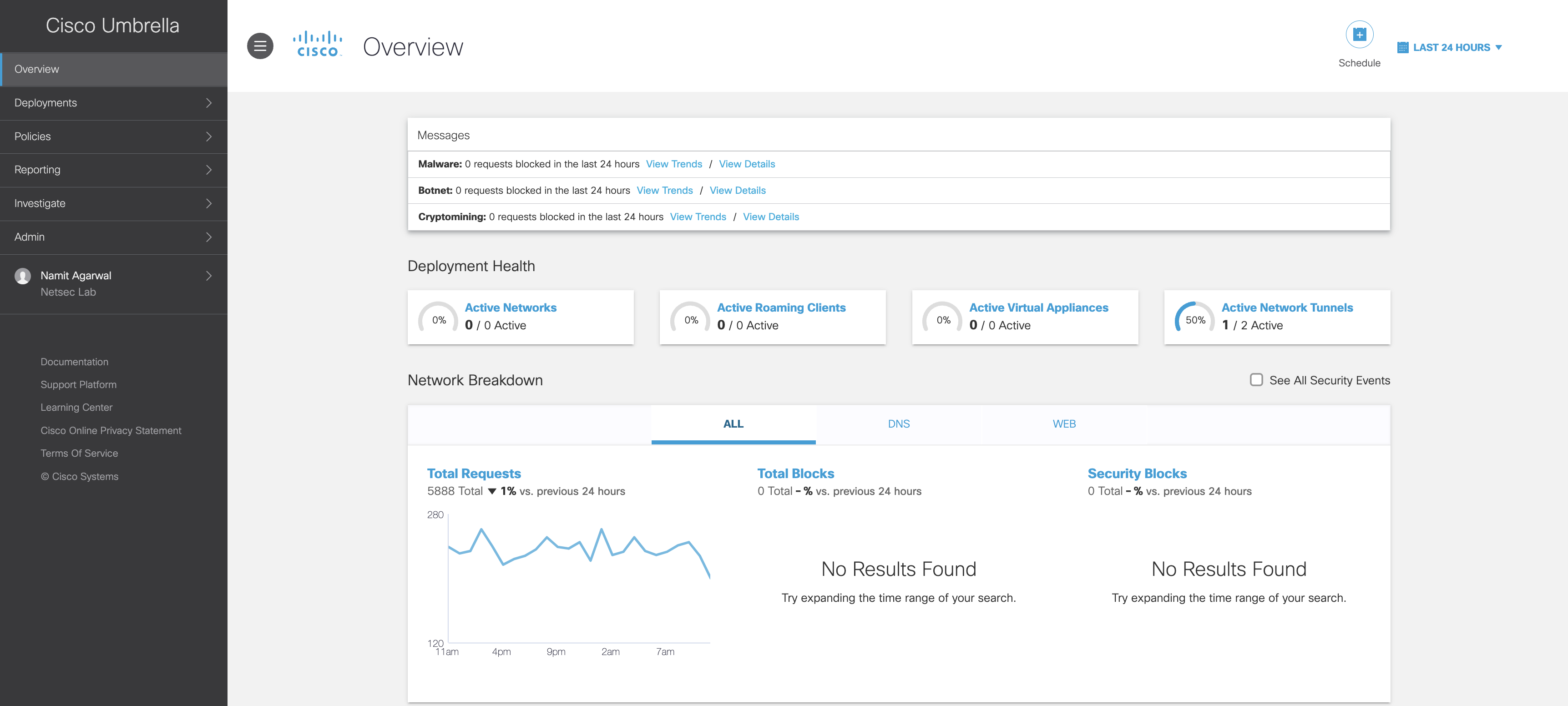
Umbrella Overview Page
Step 3 Click on Active Network Tunnels. It will take you to the Network Tunnels page. You will notice the Network Tunnel deployed on Umbrella and passing traffic.
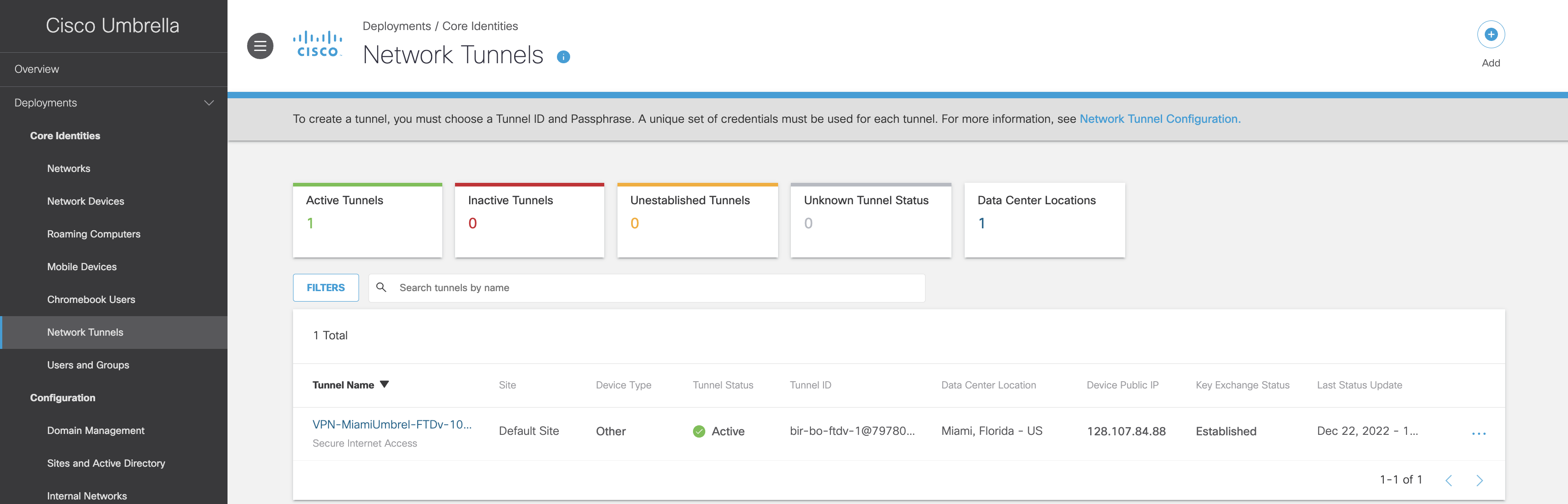
Umbrella Network Tunnels
Step 4 The FMC Umbrella Auto-Tunnel feature configures tunnels on the endpoint (Firewall) and the Umbrella Data Center. You can review further details of the tunnel by clicking on the Tunnel Name; they will match the tunnel summary on the FMC side.
Step 5 For more info about how Umbrella Network Tunnels work and how to apply cloud-delivered firewall and inspection policies, please review the Umbrella user guide.
Summary
Release 7.3 simplifies the configuration of Secure Internet Gateway (SIG) tunnels by automating the tunnel configuration on Umbrella and Edge Firewalls. The FMC also provides a central monitoring dashboard. The same tunnel configuration can be applied to multiple Firewalls enabling a scalable SASE deployment. The deployment supports multiple designs such as Dual Umbrella DC, Dual ISPs etc.
📚Additional Resources
Provide links to any additional resources:
Updated about 3 years ago
