Scenario 10 - Decryption Policy
In this section we will configure the Decryption policy. When it comes to decrypting TLS traffic, certificate management is one of the biggest challenges. For inbound decryption, we use the internal web server's secret key to decrypt traffic destined there.
For outbound decryption, the device will resign the TLS session with a certificate trusted by the browser. This trust is critical to the implementation of outbound decryption. Normally, there is already a Public Key Infrastructure (PKI) in the organization and all of the workstations have a common certificate authority (CA) that they trust. The FMC would then import the CA certificate and use it to resign the outbound communications. This trust is important to avoid browser errors and messages to the effect that the communication is not secure.
For our lab scenario we will use an internally generated CA to resign the outbound connections. This would not be acceptable in normal environment. However, our focus here is on the FMC policy - not how to build and maintain a PKI.
This scenario will focus on building a Decryption policy to decrypt outbound traffic.
Lab Tasks
These are the tasks in this scenario. If you are familiar with the Secure Firewall you may do these on your own, or for step-by-step instructions see below.
- Task 1 - Generate an internal CA on the FMC to be used to resign outbound decrypted traffic
- Task 2 - Create a new Decryption policy named Decrypt Outbound and add a rule to decrypt traffic from the Lab-Networks to the Internet using the generated CA certificate
- Task 3 - Create a rule to block the insecure SSL v3.0 and TLS v1.0 protocols
- Task 4 - Create do not decrypt rules for the following traffic:
- Financial traffic to known favorable sites
- Health care traffic to known favorable sites
- Applications that use pinned certificates
- Sites in the Cisco-Undecryptable-Sites object group
- spotify.com and plex.tv
Task 1 - Generate FMC Internal CA
- From the FMC2 UI navigate to Objects -> Object Management expand PKI and click Internal CAs in the left panel.
Click the Generate CA button to create a new internal CA.
Name the CA Cisco-dCloud and fill in the information similar to the figure below. Use whatever information you want, the content is not important to the lab.
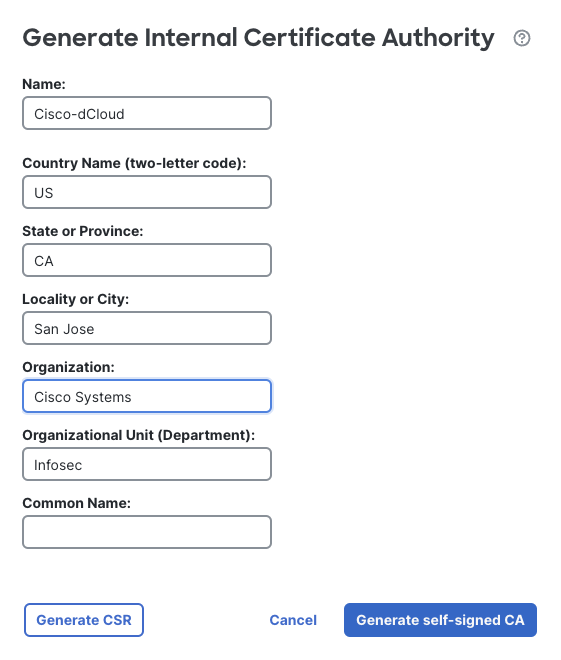
New Policy Dialog
When finished click Generate self-signed CA
Task 2 - Create Decryption Policy
- Navigate to Policies -> Decryption and click the Create Decryption Policy button.
In the policy information dialog name the policy Decrypt Outbound
Click the Internal CA drop-down and select the Cisco-dCloud CA
Click No networks/ports associated to limit the rule to outbound traffic only.
For Source Network select the Lab-Networks object
In the destination section select HTTPS for Port. Click Apply.
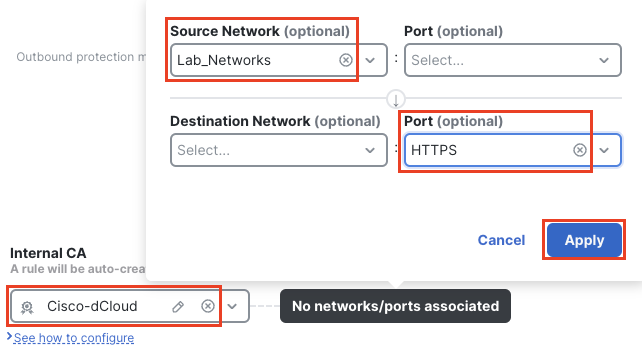
Associate Networks/Ports
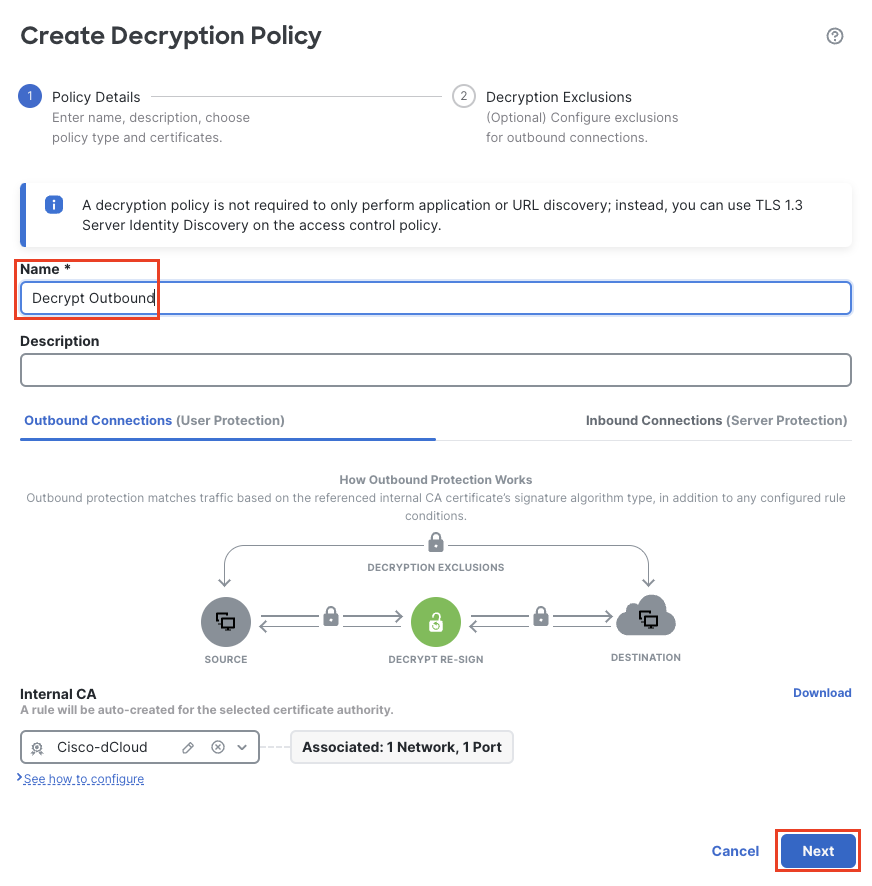
Decryption Policy Wizard
This will automatically create an outbound decryption rule in your policy.
Click the See how to configure link for information on how to download the certificate and distribute it to your users.
Click Next to go to the Decryption Exclusion page and click Create Policy to save the policy.
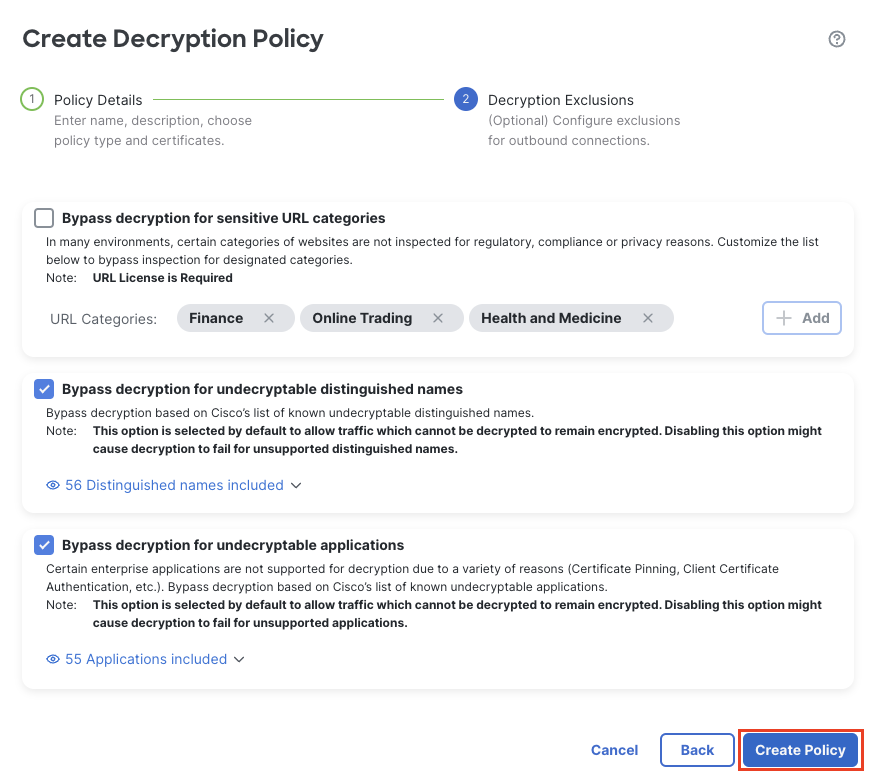
Click the pencil icon to the right to open the policy “Decrypt Outbound” for editing.
-
The automatically created rule will decrypt all traffic originating from the lab networks. However, it will decrypt traffic within the lab networks as well. We need to limit this rule to only decrypt traffic going to the Internet.
Click the pencil by the auto generated rule named Cisco-dCloudrule and make the following changes:
Name: Decrypt Outbound
Move: select into category and Root Rules
Zones: Add OutZone to Destination Zones
Logging: Check Log at End of Connection
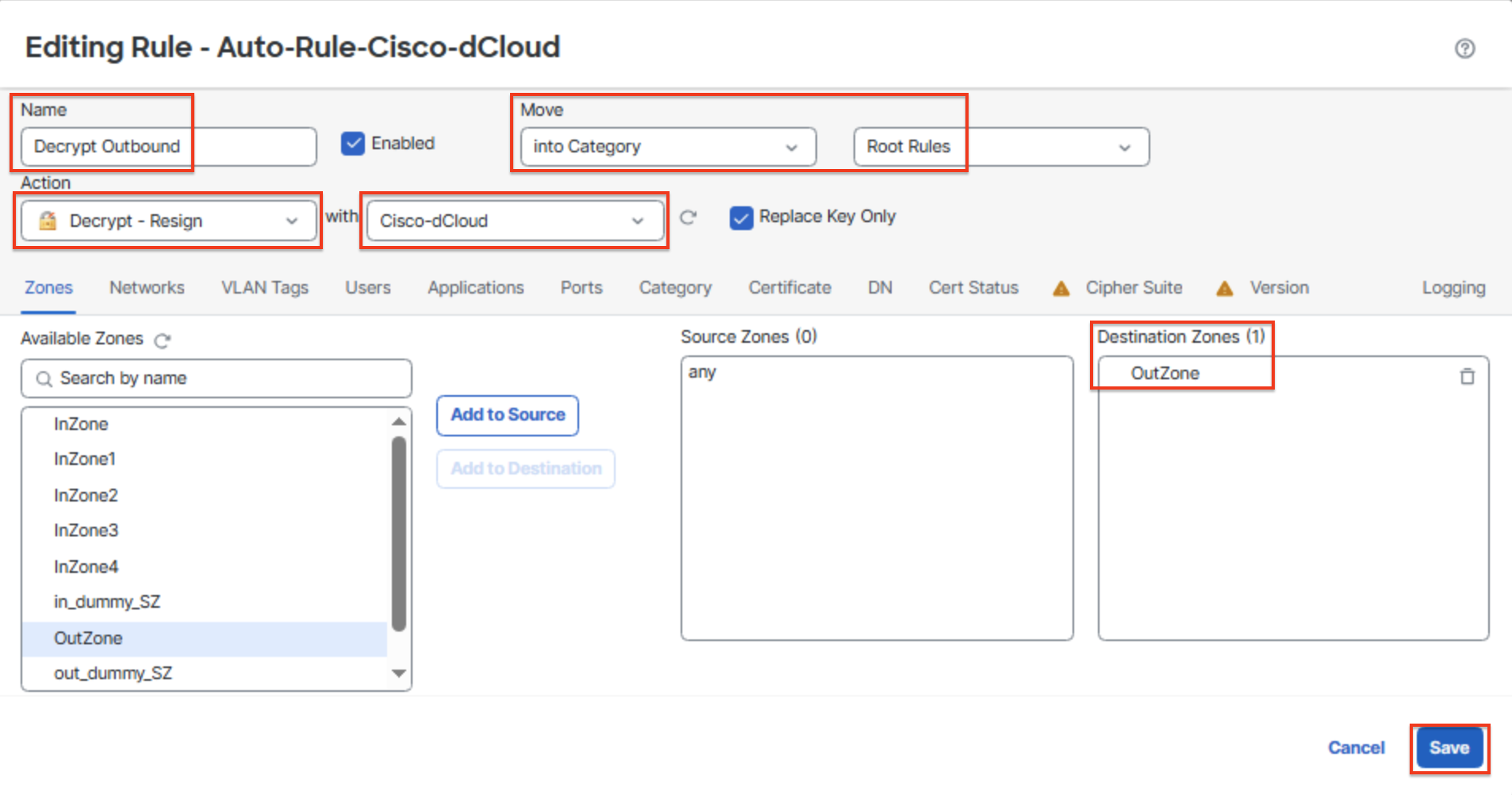
Decrypt Outbound Rule
Click save to save the rule.
Task 3 - Block Insecure SSL
- Now that we have our decryption rule, the deployed policy would decrypt all outbound traffic from the Lab-Networks. Now we will add some additional rules to deal with conditions where we might want to block or avoid decrypting traffic.
First, we will add a rule to block older insecure SSL/TLS versions.
Click + Add Rule
Name it Block Insecure Versions
Insert: select into category and Root Rules
Action: Block with reset
Click the Version tab
Check only the SSL v3.0 and TLS v1.0 boxes.
Click the Logging tab and check Log at End of Connection
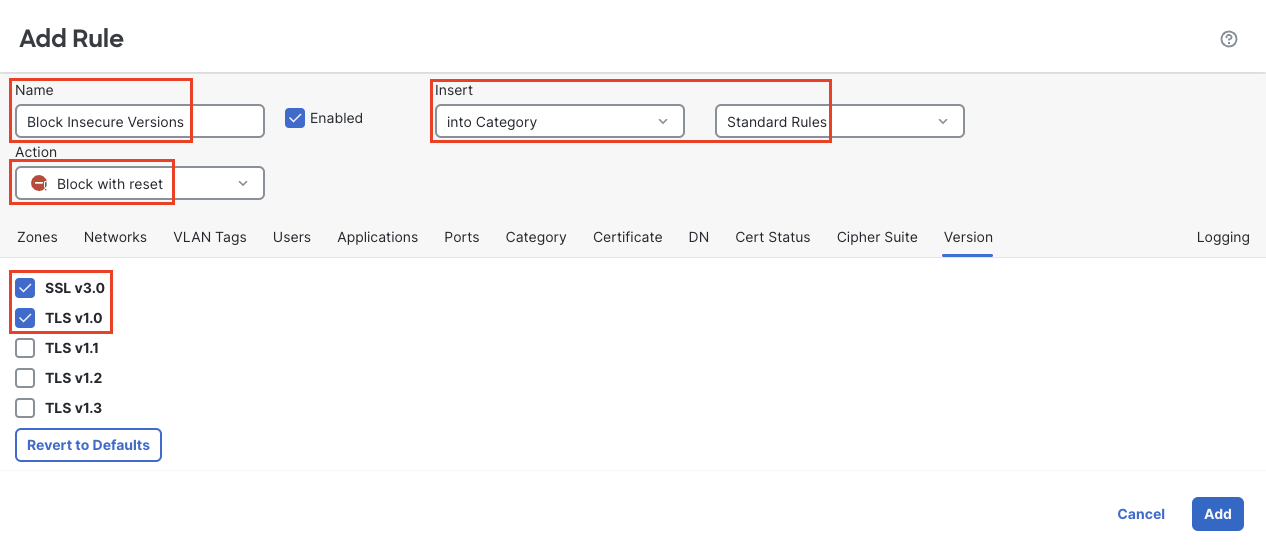
Block Insecure Versions
- Click Add to add the rule.
Note that we did not configure any source/destination conditions so this rule will block all insecure SSL/TLS traffic regardless of source or destination.
Task 4 - Decryption Exceptions
- The bulk of the rules within a Decryption policy will consist of decryption exceptions. Next we will add a rule to prevent decryption of sensitive traffic.
Create a Do not decrypt rule to match traffic to trusted banking and healthcare sites.
Name the rule DnD Banking and Health
Place it in the Standard Rules category below the first rule.
Source Network should be Lab-Networks
Destination zone is OutZone
Category: Finance Reputation: 4 - Favorable
Category: Health and Medicine Reputation: 4 - Favorable
Log at the end of the connection
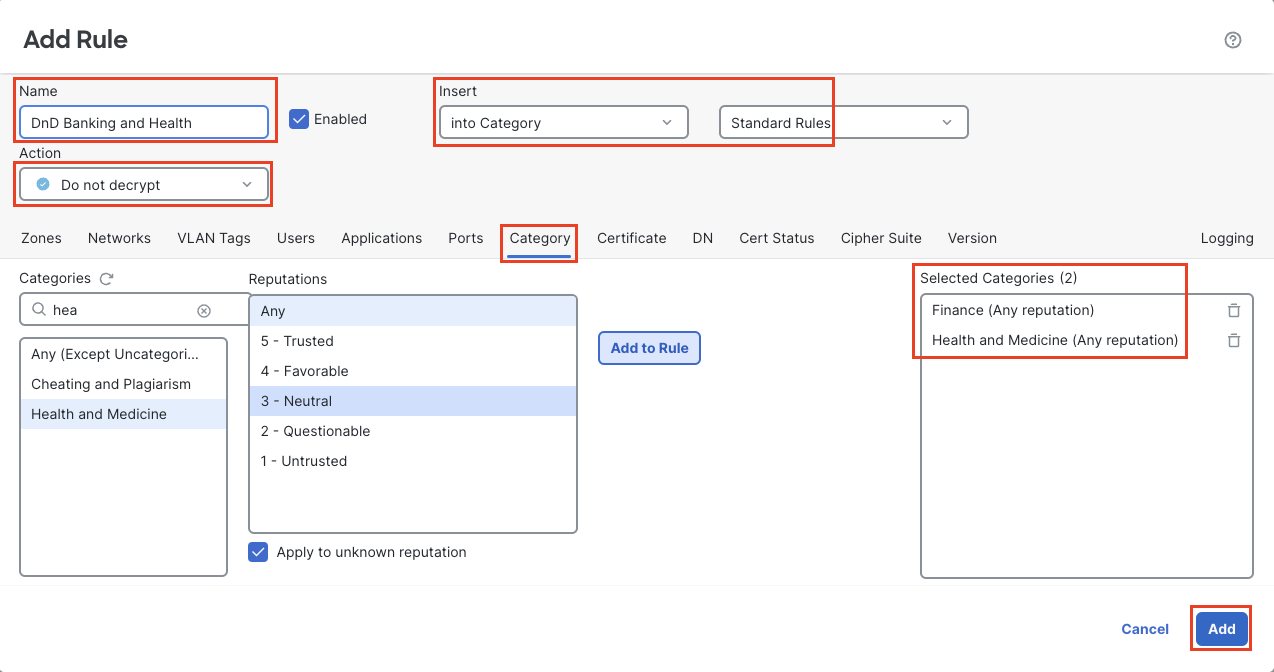
Do Not Decrypt Rule
- Another rule will provide a decryption exception for traffic from applications that are known to use a pinned certificate and are therefore undecryptable.
Create a Do not decrypt rule.
Name it DnD Undecryptable Apps
Place it in the Standard Rules category (the order isn't important as long as it comes before the Decrypt Outbound rule.)
Configure the Zones and Networks to match outbound traffic from the Lab-Networks
Click the Applications tab
Under Applications Filters in the search field type undecryptable
Check the box by undecryptable
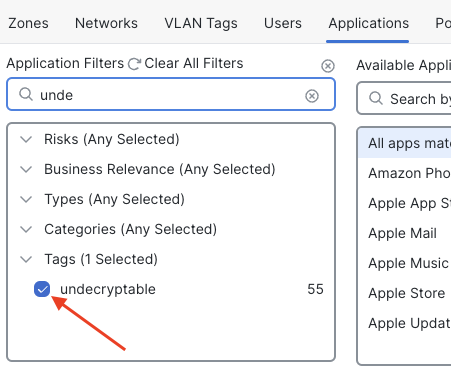
Pinned Certificate Apps
Add All apps matching the filter
Log at the end of the connection
- The last rule we will add will provide a decryption exception for connections using a specific Distinguished Name (DN) in the certificate. We will start with the included system object which has a number of known undecryptable sites, then add a couple of our own.
Create a Do not decrypt rule.
Name it DnD Specific DNs
Place it in the Standard Rules category (the order isn't important as long as it comes before the Decrypt Outbound rule.
Configure the Zones and Networks to match outbound traffic from the Lab-Networks
Click the DN tab
Locate the Cisco-Undecruptable-Sites object group in the Available DNs column and click Add to Subject.
Log at the end of the connection
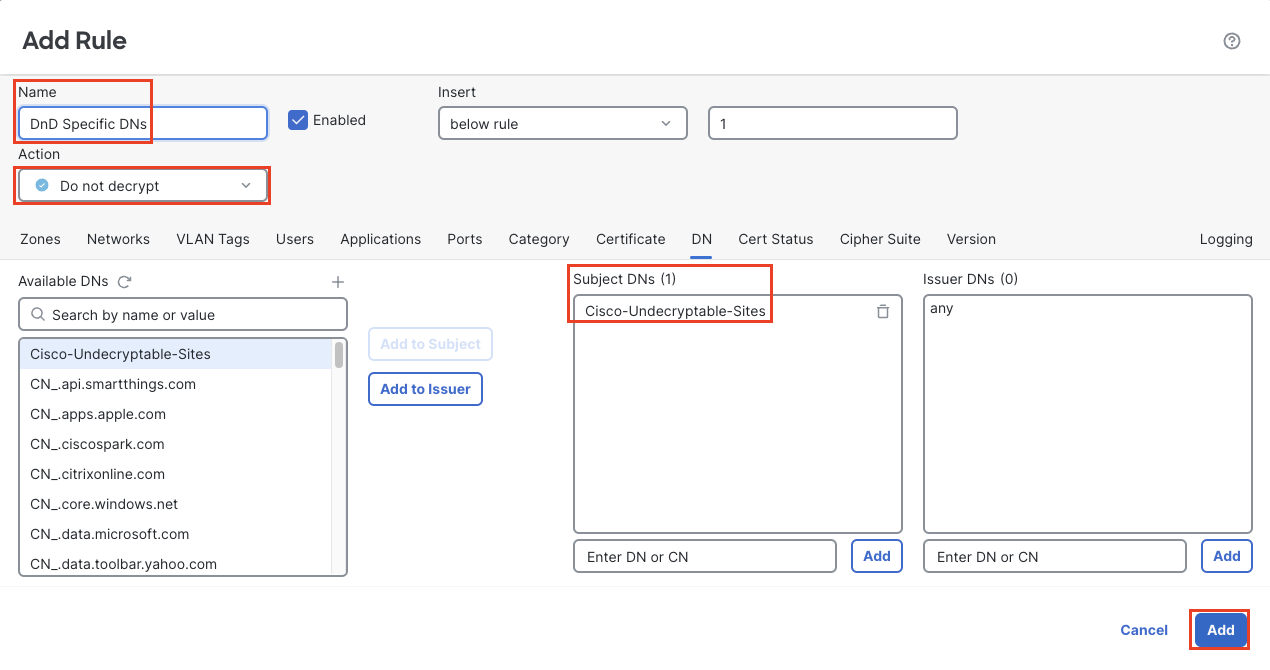
DnD Undecryptable Sites
There are two ways we can add custom DNs to this rule. One is to add an object and then use it in the rule. The other is to enter the DN directly into the rule. The first option is usually preferred in case the object needs to be used elsewhere as well. We will do one of each below.
Click the + at the top of the Available DNs column to add a new object.
Name the object Spotify.com
Under DN: enter spotify.com
Click Save
Scroll down the Available DNs list, locate the Spotify.com object and click Add to Subject to add it to the rule.
At the bottom of the Subject DNs list type plex.tv in the Enter DN or CN field.
Click the Add button to the right of the field.
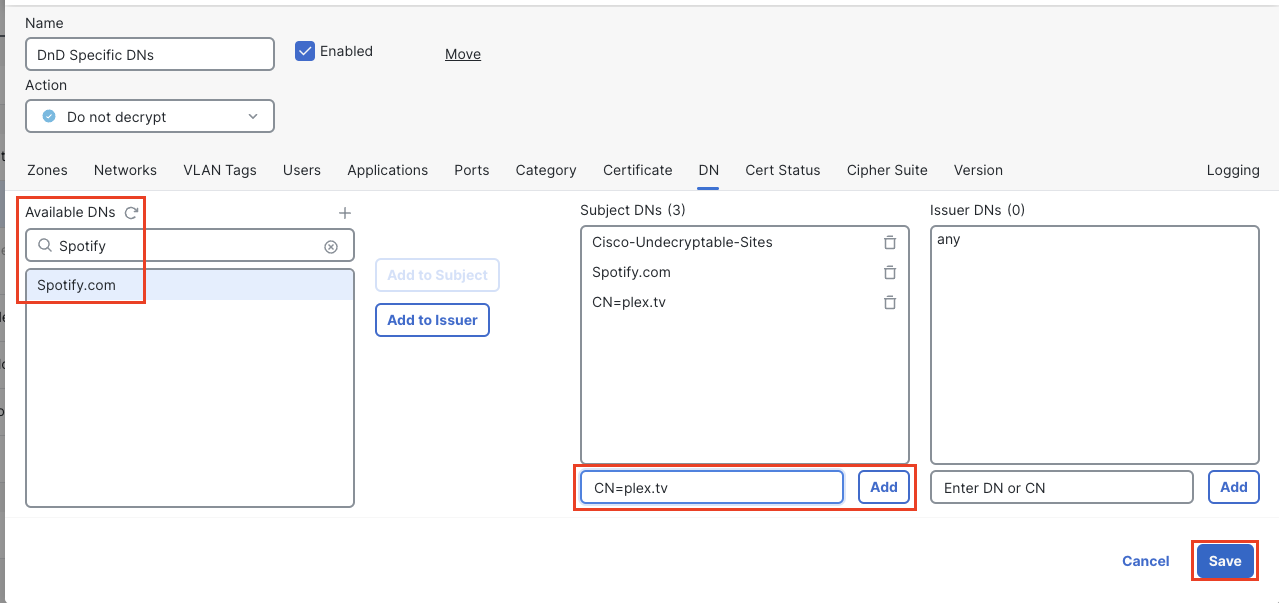
Final DnD Rule
Add the rule and Save your policy.
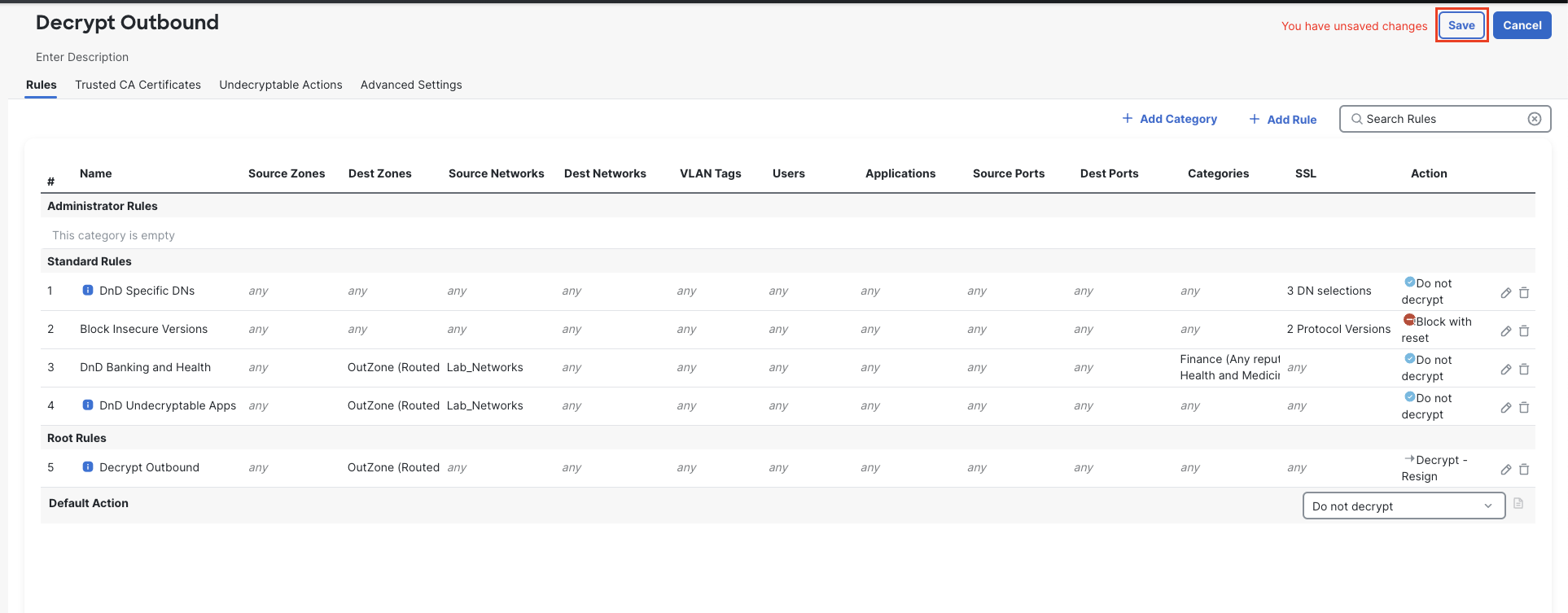
Decryption Policy
We have created a Decryption policy with a few standard exceptions for undecryptable sites. In an actual production deployment this would be just the start with other DnD exceptions added later as the policy is tested with actual traffic.
Tell us how we are doing
We are doing our best to ensure the scenarios in this lab guides are useful, clear and work as expected.
Please share your thoughts to help us improve or fix any problems you may run into..
Click here to provide your feedback or report an issue with this guide
Updated 10 months ago

