Policy Based Routing(PBR) with User Identity and Security Group Tags(SGT)
Introduction
Cisco Secure Firewall Release 7.4 introduces support for User Identity and Security Group Tags (SGTs) within Policy-based routing(PBR) policies.
This feature provides additional capabilities to steer traffic through Secure Firewall Threat Defense devices by leveraging user identity, AD group membership, or Security Group association(SGTs). These capabilities can coexist with current policy-based routing conditions. Additionally, this allows segregation of traffic based on user identities or SGTs for deployments where differentiated access is required for employees, guest users, and IOT devices.
This feature is supported with Secure Firewall Management Center (FMC) and Secure Firewall Threat Defense devices running release 7.4.
Background Information
Since 7.1, Secure Firewall Threat Defense devices support application aware Policy Based Routing which provides network administrators the ability to direct traffic to an interface based on the traditional 5-tuple attributes:
- Source Network
- Destination Network
- Source Port
- Destination Port
- Application
In order to simplify the deployment and provisioning of branch networks, release 7.4 introduces additional attributes that can be leveraged within Policy Based Routing such as
- User Identity
- AD Group membership
- Security Group Tags (SGT)
How PBR with User Identity and Security Group Tags(SGT) works
To ensure complete visibility into network traffic traversing through Secure Firewall and associate the traffic with user identity information, the Secure Firewall Management Center supports integration with authentication sources such as AD/LDAP and Cisco Identity Services Engine (ISE).
Once AD/LDAP servers are configured as Realms within FMC, they provide User Identity and Group association information which FMC passes on to FTD for leveraging the User and Group information in PBR policies.
️ Note
Along with PBR policies, the User Identity and Group information can also be leveraged in Access Control Policies for traffic inspection.
Additionally, once the pxGrid integration between ISE and FMC is successful, it provides additional user information such as user login events, Security Group Tags (SGT) assigned to the users, and the associated SGT to IP mappings.
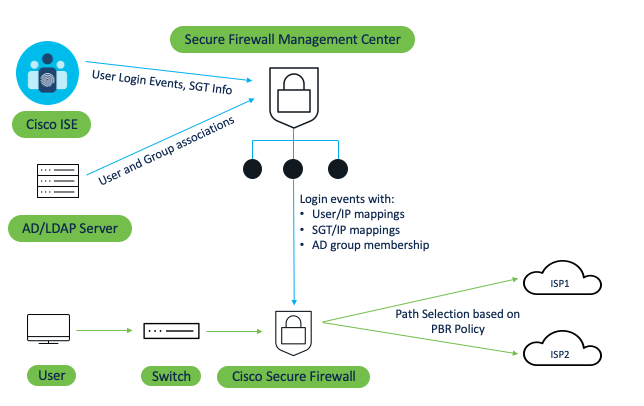
Figure 1. PBR Policy operations using User Identity and Security Group Tags(SGT)
As the FMC gets user identity, group membership, and security group tag information from various authentication sources, these attributes can be used as identifiers/conditions to select the traffic and route it appropriately using policy-based routing rules.
The complete workflow is as follows:
- Configuring PBR rules using user identity, group, or SGTs results in the deployment of a route map from FMC to FTD that references an extended access list with identity-based rules.
- For user identity, the user login events are supported using any methods such as VPN, Captive Portal, etc. which are pushed as event records to all the FTD devices.
- Once FTD has the route map with required identity-based rules and user event records, the routing decision is based on the traffic initiated by a particular user where the source address is mapped to either a user identity, AD group, or security group that is pushed to FTD when the user logs in.
In addition, FMC also allows the configuration of custom SGT objects for inline SGTs. This is useful in deployments where FMC is not integrated with ISE. Inline SGT is where the SGT is part of the packet itself and once the packet reaches FTD, it will read the associated SGTs and apply the policy-based rules based on the SGT information.
️ Note
- When ISE is configured on FMC, only the SGTs pushed from ISE can be used in the extended ACL for policy based routing. Inline SGTs cannot be used.
- The option to configure SGTs locally on FMC is removed if FMC is integrated with ISE.
- Similarly, if ISE is not configured on FMC, only Inline SGTs can be used in the extended ACL.
Configuration
Prerequisites:
- In order to configure User Identity within the Extended ACL used in PBR, AD/LDAP realm needs to be configured on FMC. Please follow the steps in this document to complete AD/LDAP realm configuration on FMC
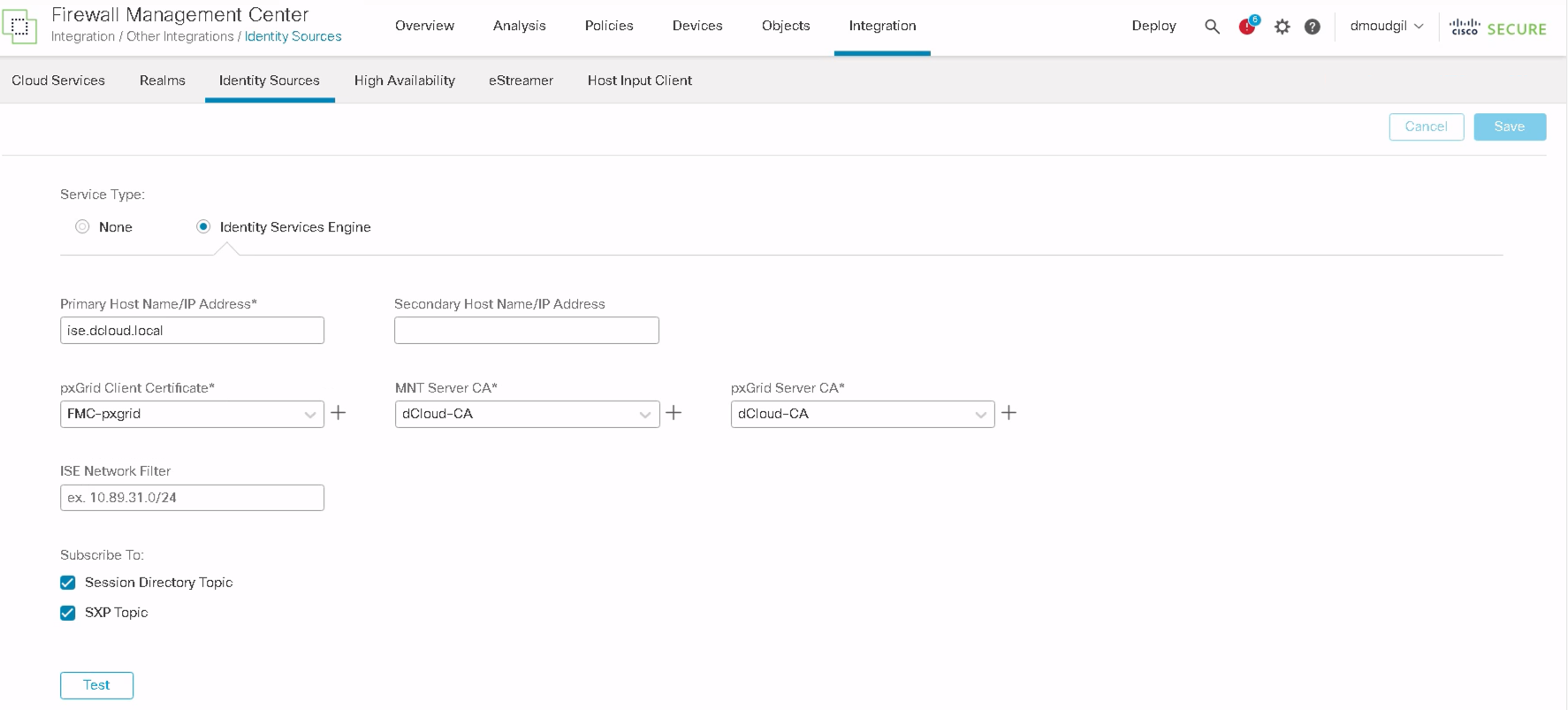
In order to configure Security Group Tags in PBR, either Cisco ISE integration with FMC is required or custom SGTs can be used. Please follow the steps in this document to complete ISE integration with FMC for pxGrid
If FMC is not integrated with ISE, then custom/inline SGTs can be used within PBR policies.
Step 1: Navigate to Integration > Other Integrations > Realms and ensure that AD/LDAP realm configuration is completed and successful as noted in point no. 1 in the prerequisites above.
Once the integration is completed, users and user groups are downloaded from the AD which can then be used in the extended ACL
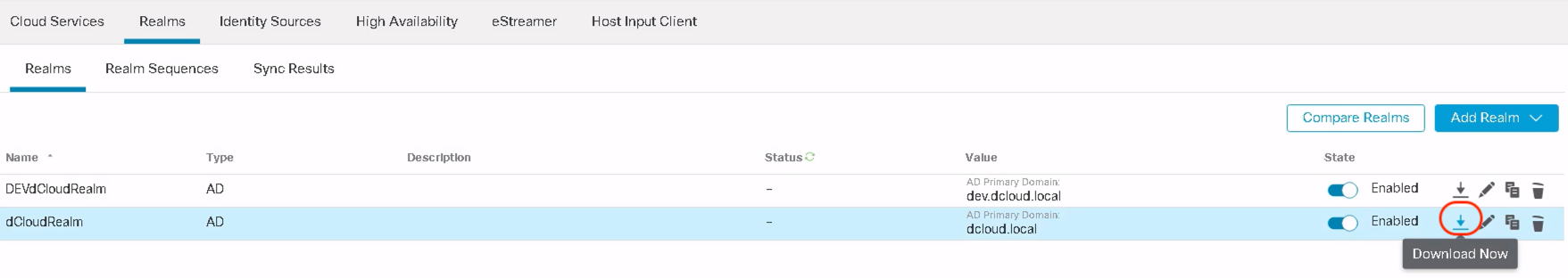
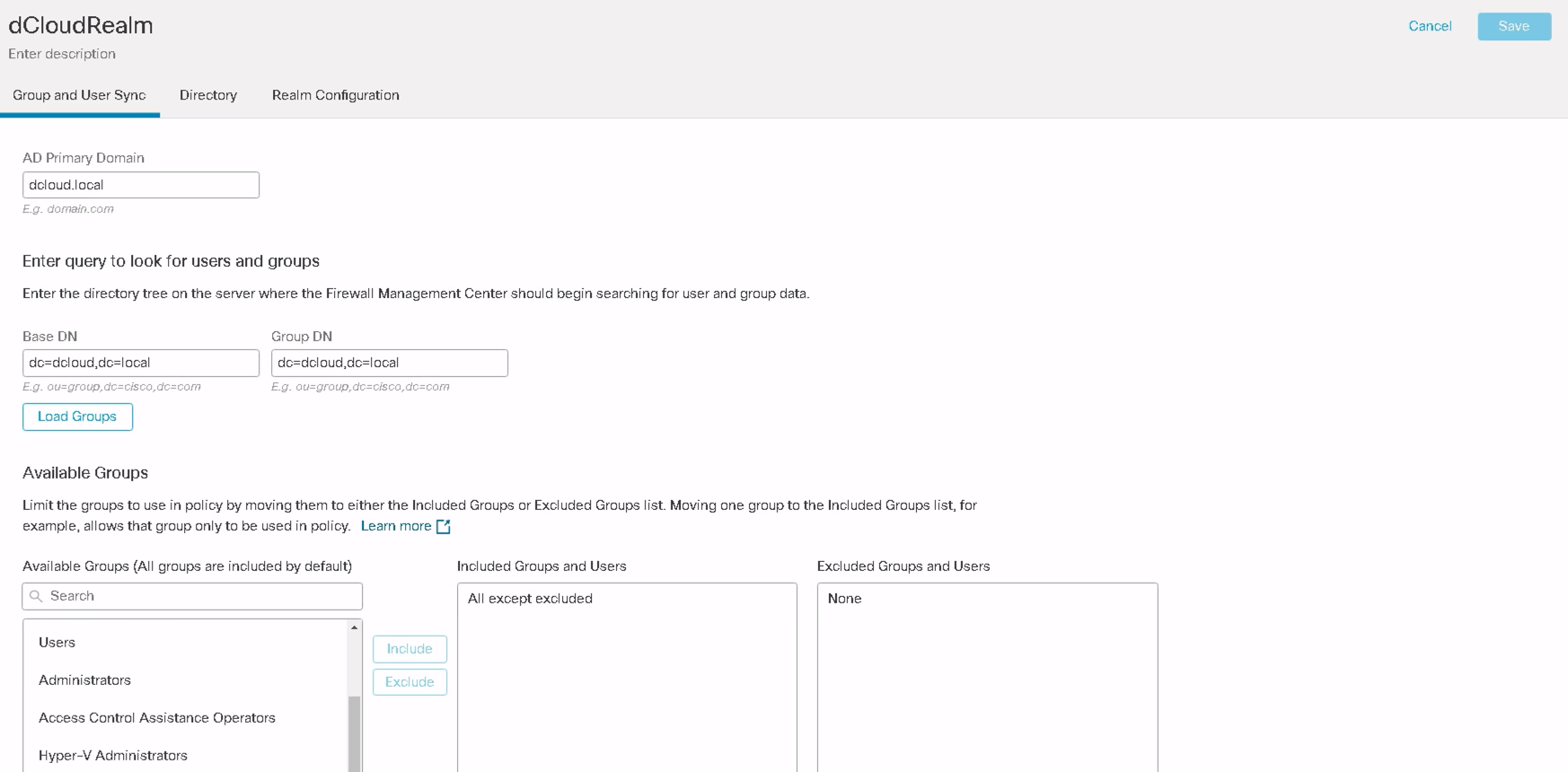
AD Realm configuration showing downloaded Users and User Groups
Step 2: Navigate to Objects > Object Management > Access List > Extended . Click Add Extended Access List and add the name of the ACL in the Name field. Click Add within the New Extended Access List object.
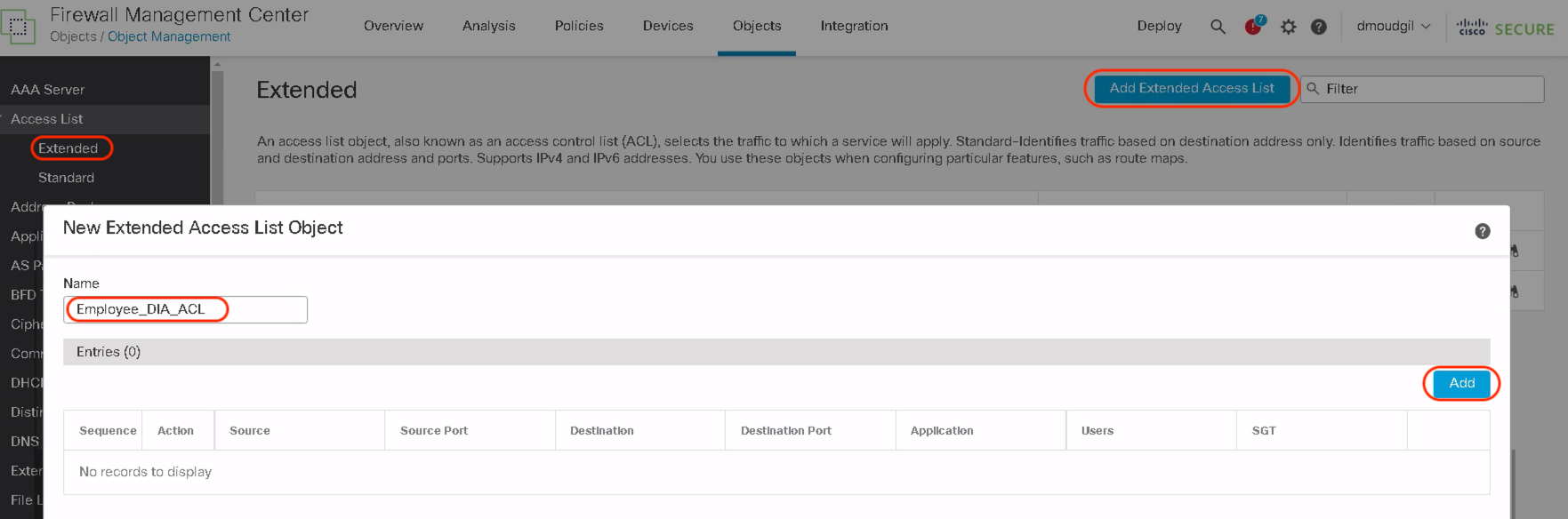
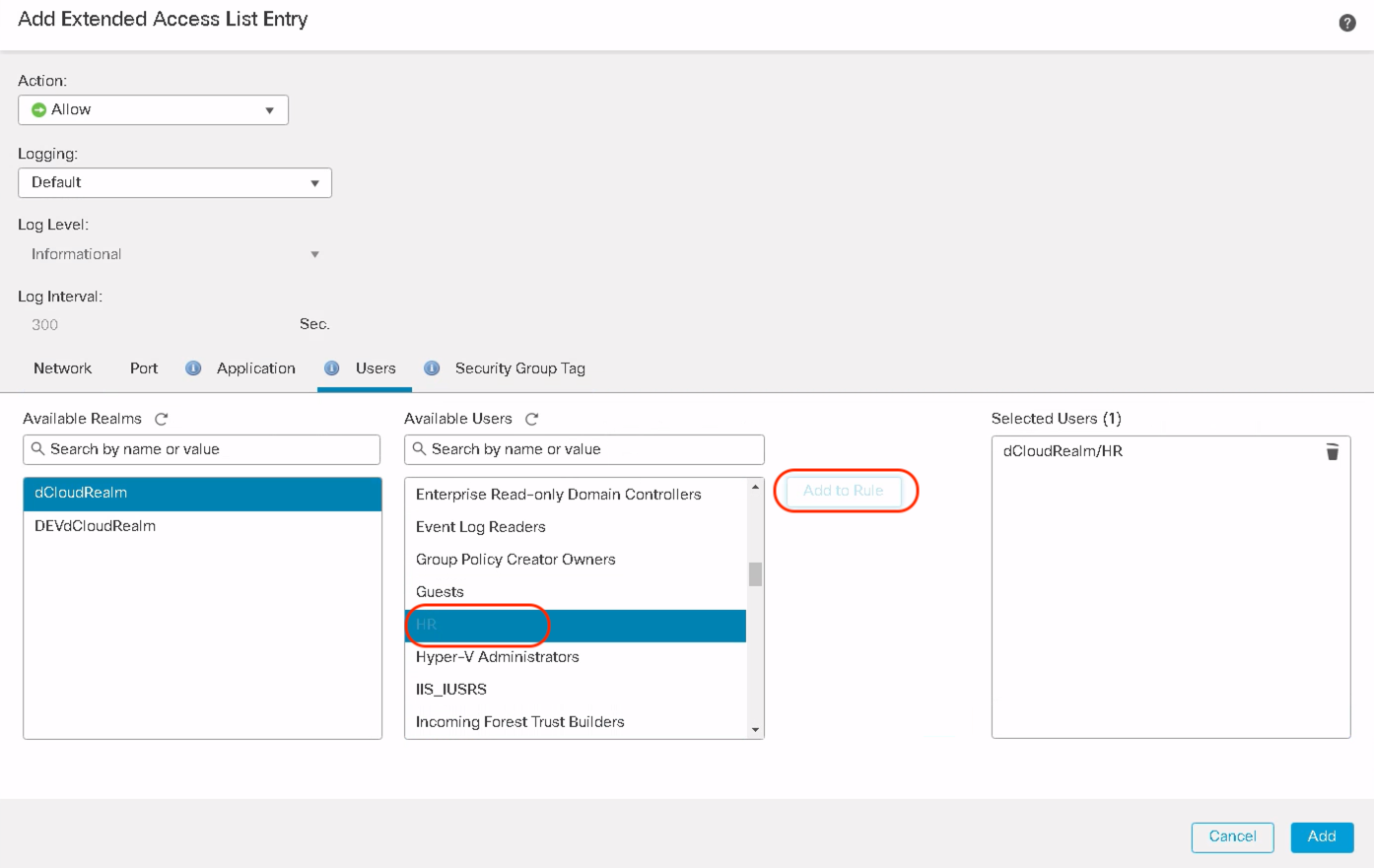
Step 3: The pop-up shows a new tab called Users. Click on Users and this shows all the configured realms under the Available Realms
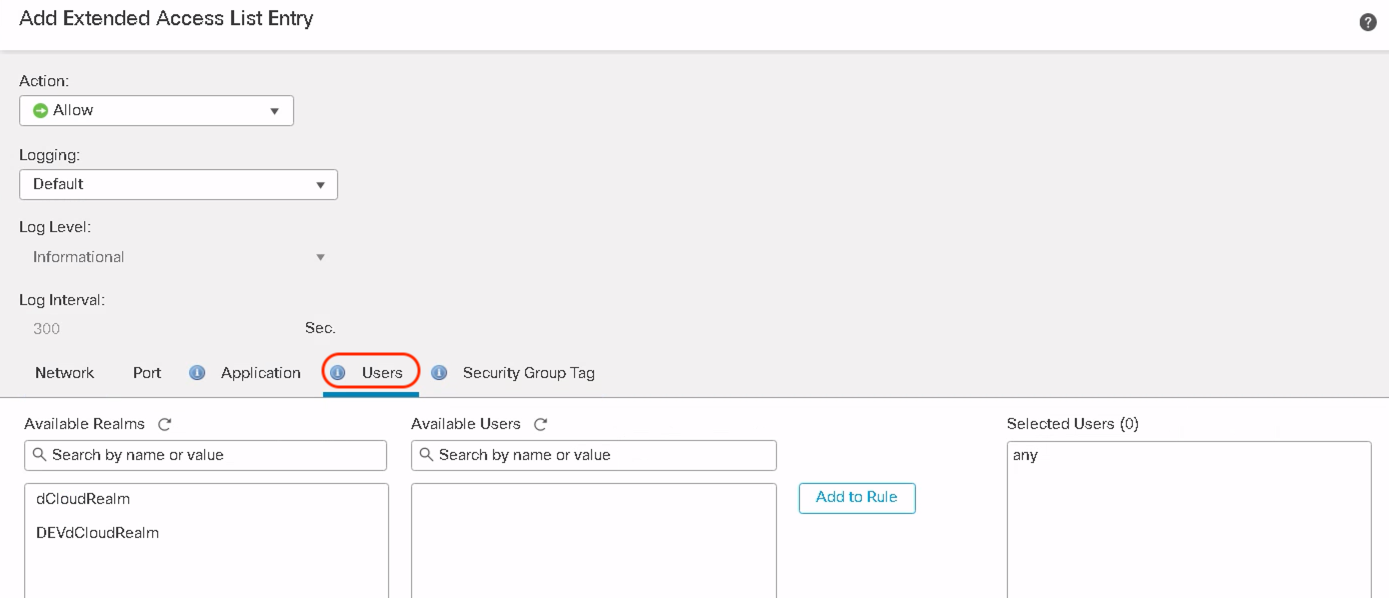
Click on the desired realms to see all the users and user groups downloaded from that specific AD/LDAP realm.
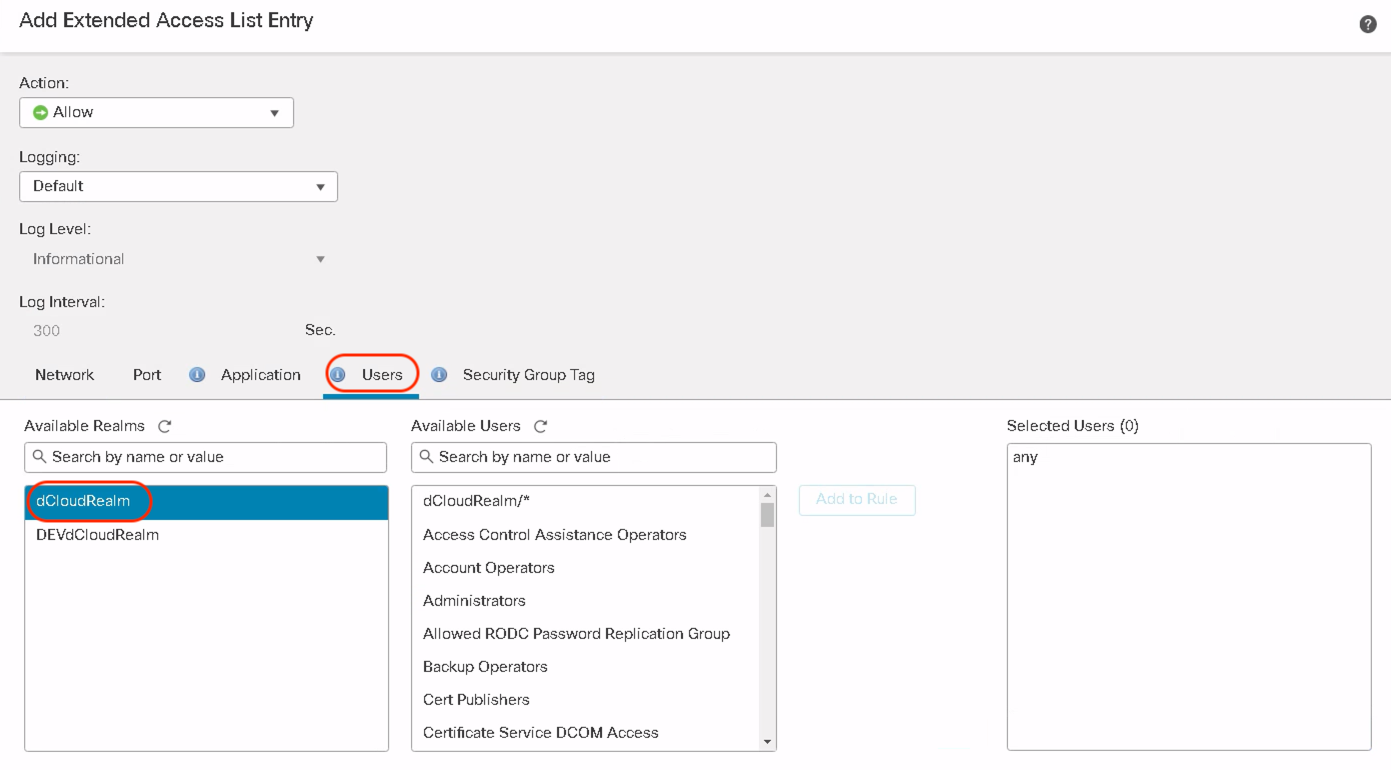
Select the users/user groups to match in the PBR policy. Click Add to Rule and click Add and Click Save.
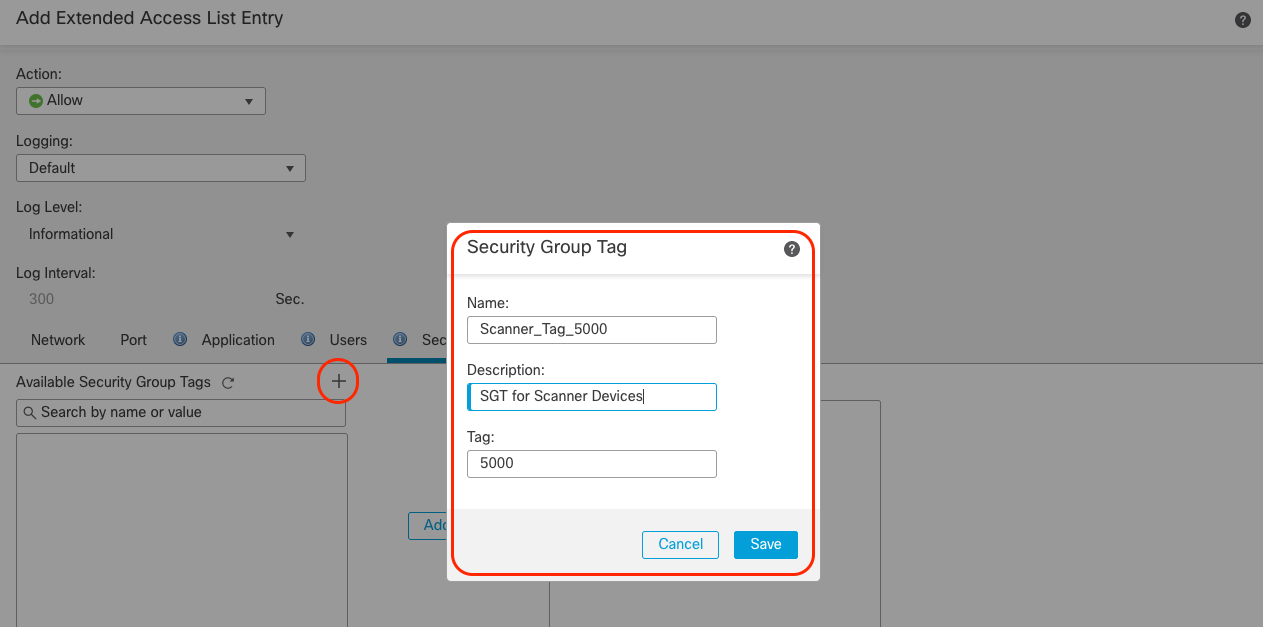
Step 4: To add PBR rules with Source SGT tags, Navigate to Integration > Other Integrations > Identity Sources > Identity Services Engine and ensure FMC is integrated with ISE as noted in point no. 2 in the prerequisites above OR inline SGT tags can be configured if FMC is not integrated with ISE.
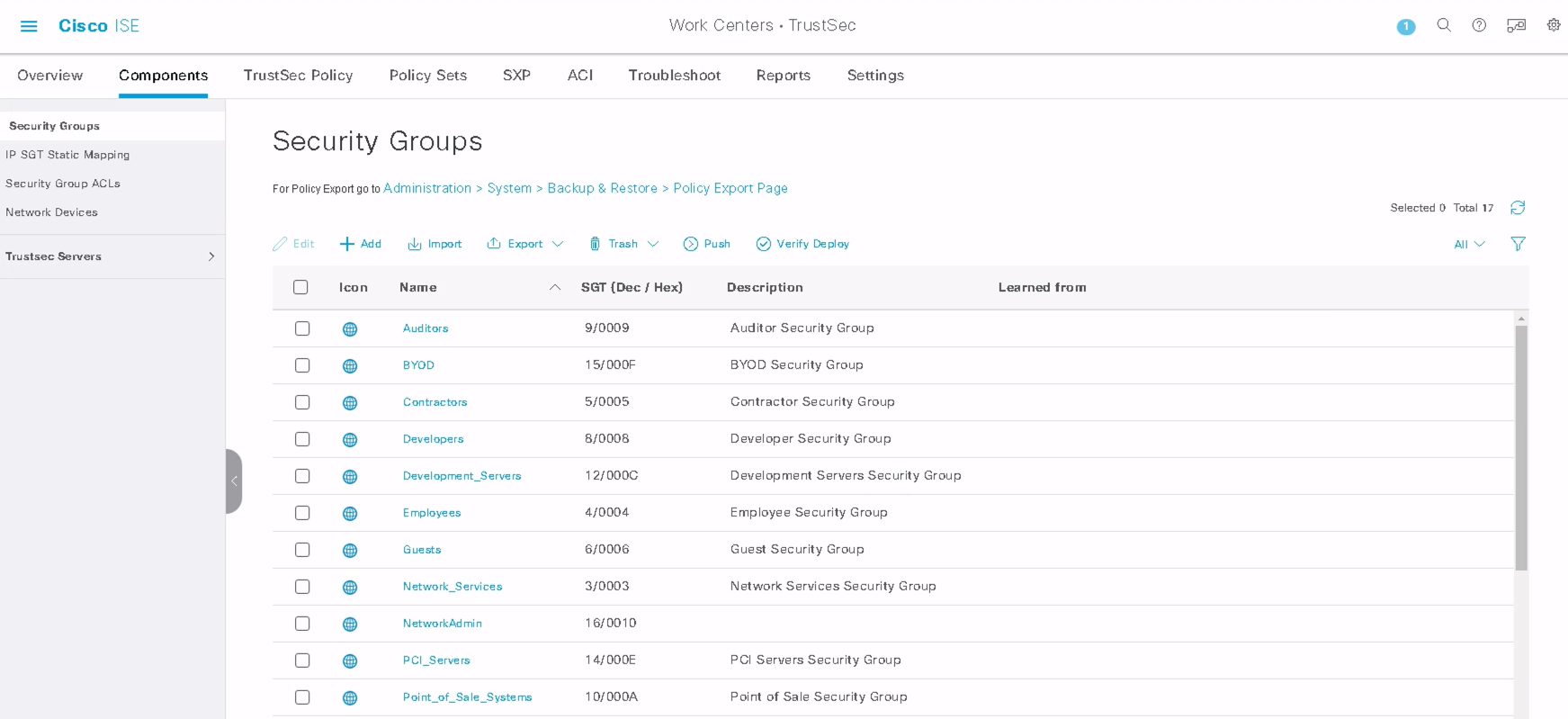
Step 5: Ensure that ISE is configured correctly with the required SGTs and is pushed to FMC to be used within PBR policies.
Step 6: Navigate to Objects > Object Management > Access List > Extended . Edit the extended ACL configured in Step 2.
Step 7: Click Edit on the existing extended Access List Entry.
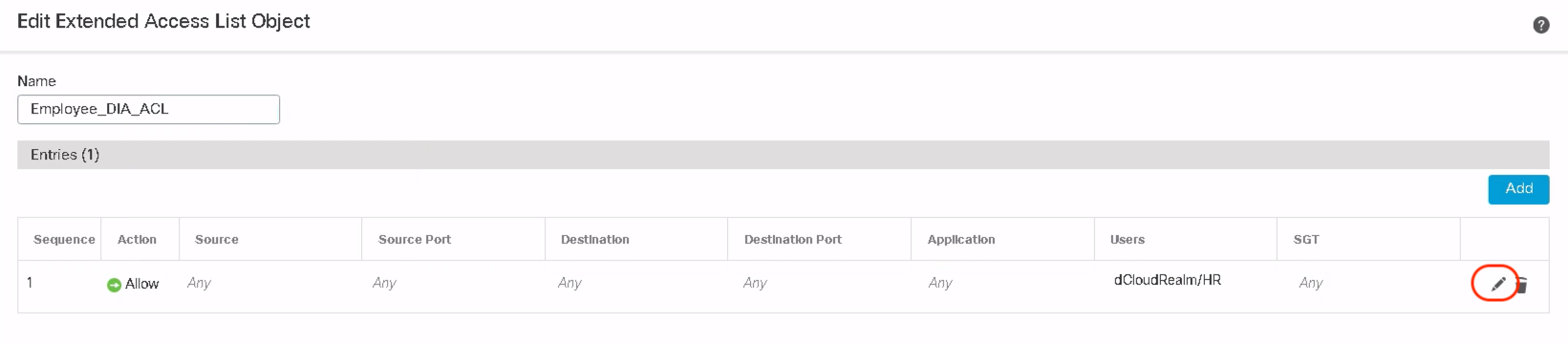
Notice adjacent to the Users tab, there is a new tab called Security Group Tag. Click on Security Group Tag and it lists all the available Security Group Tags pushed via ISE on FMC.
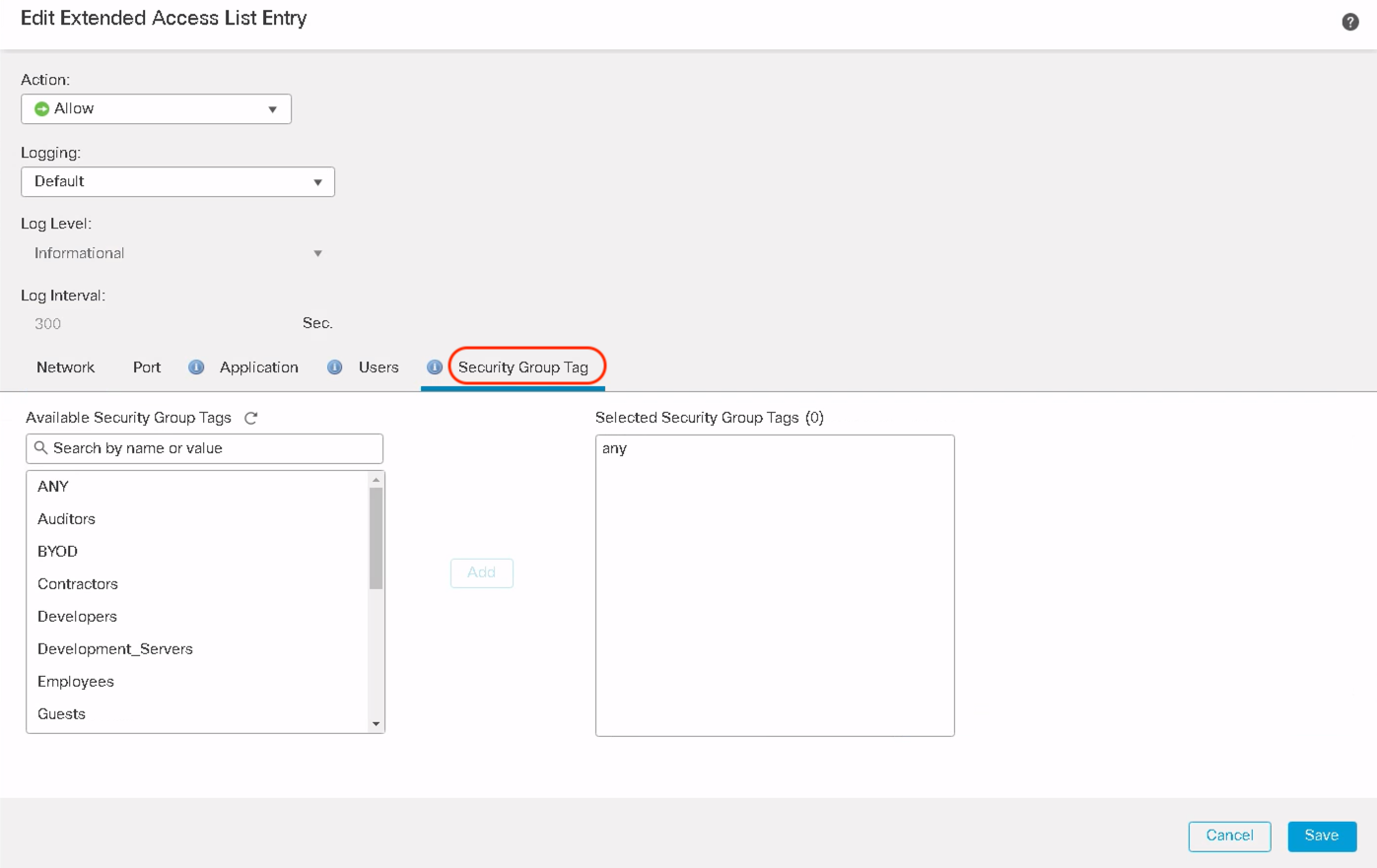
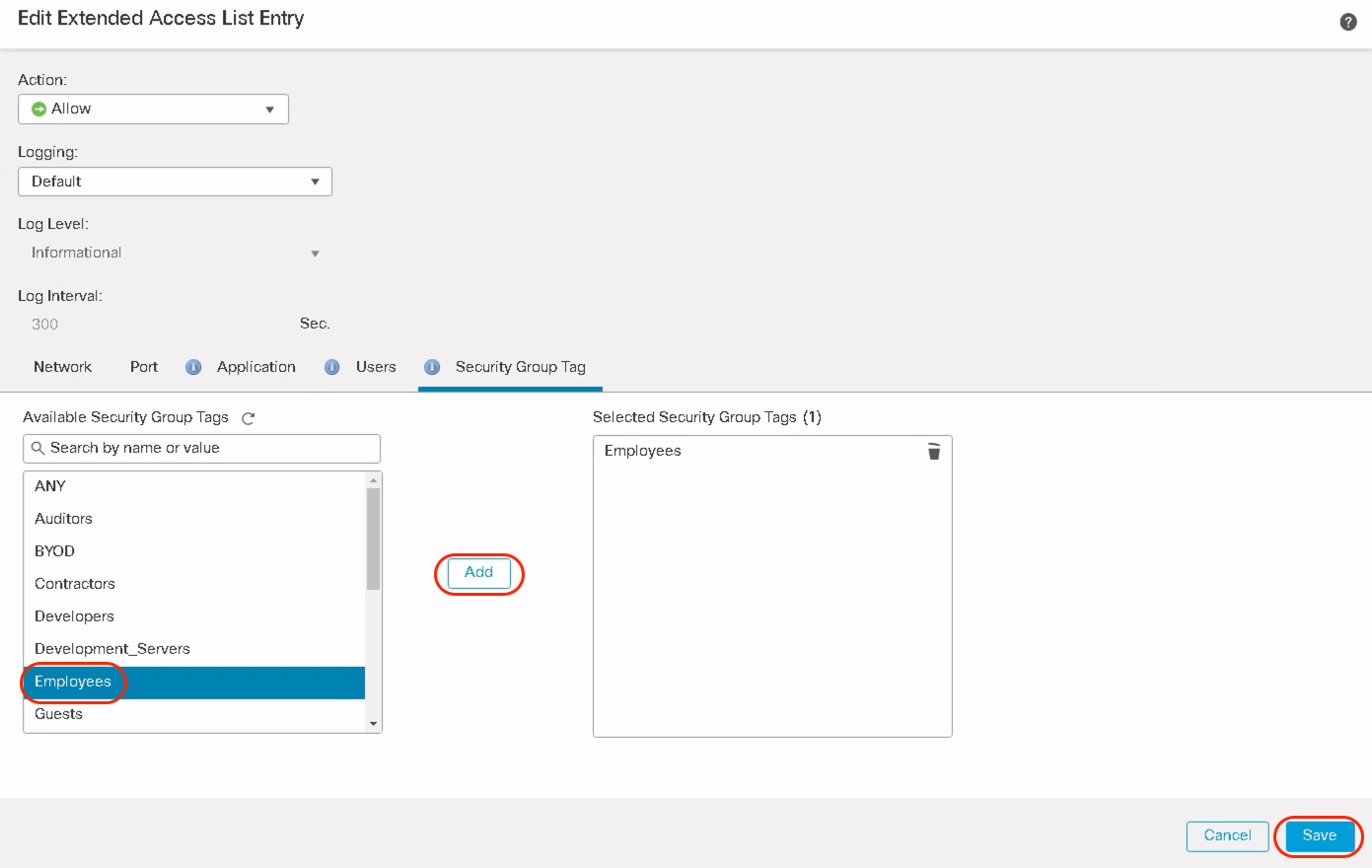
Select the desired Security Group Tag to match the PBR policy. Click Add and then click Save.
Note
Use Reload option to manually reload the list of users/ user groups or SGTs from ISE.
Only source SGTs are supported in PBR.
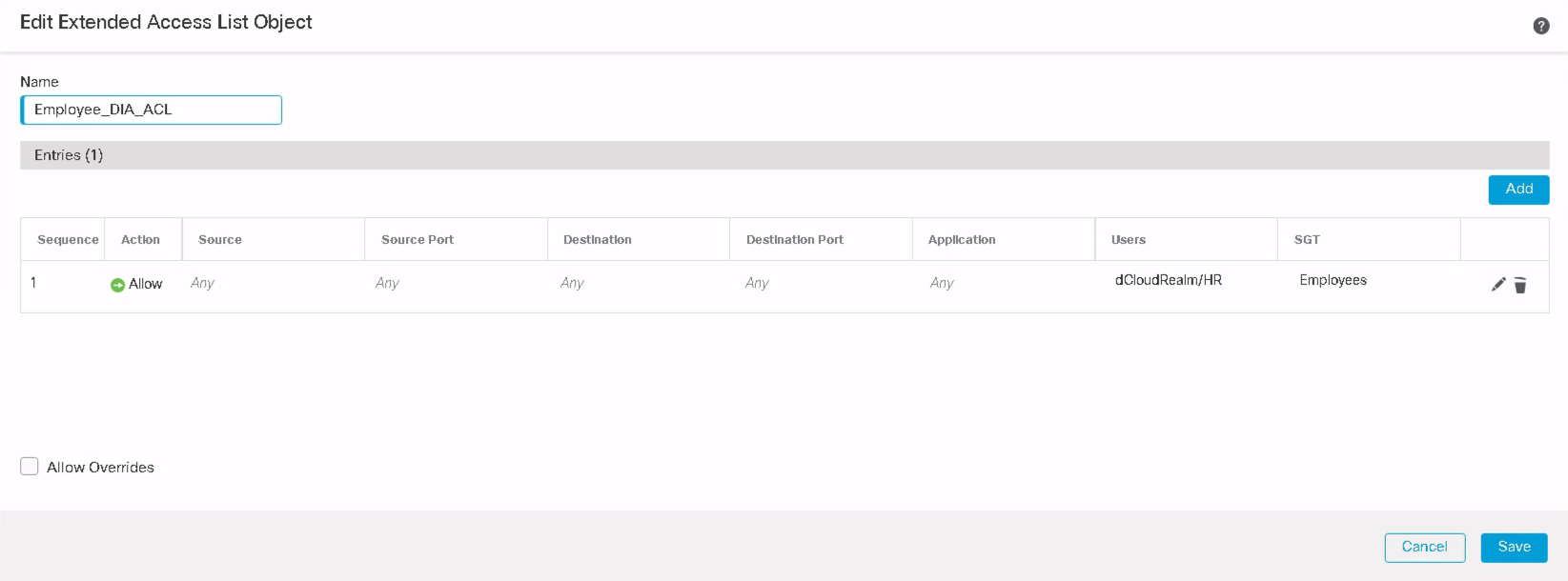
A sample extended ACL with user identity and SGT appears as shown below. Click Save to complete the extended ACL configuration.
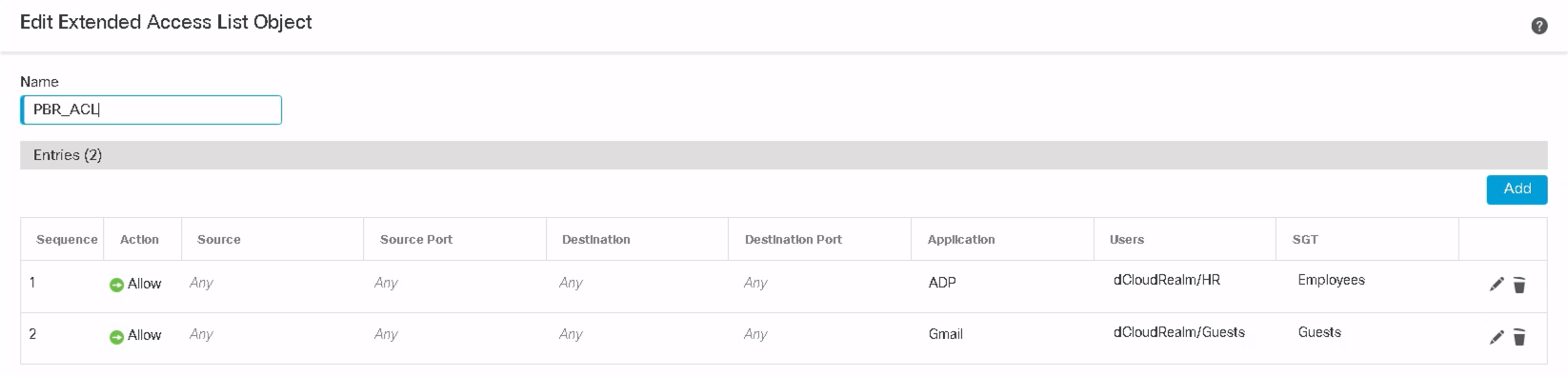
In a production environment, extended ACL objects can be configured to allow different users and groups with particular SGTs to traverse a particular transit path while trying to access their respective applications. In the below example, Users in the HR AD group with Employees SGT are allowed to access ADP applications via policy-based routing configuration.
Step 8: To use Custom SGT when FMC is not integrated with ISE, navigate to Objects > Object Management > External Attributes > Security Group Tag and click Add Security Group Tag. These user-defined objects can be used in Extended ACL for PBR policies.
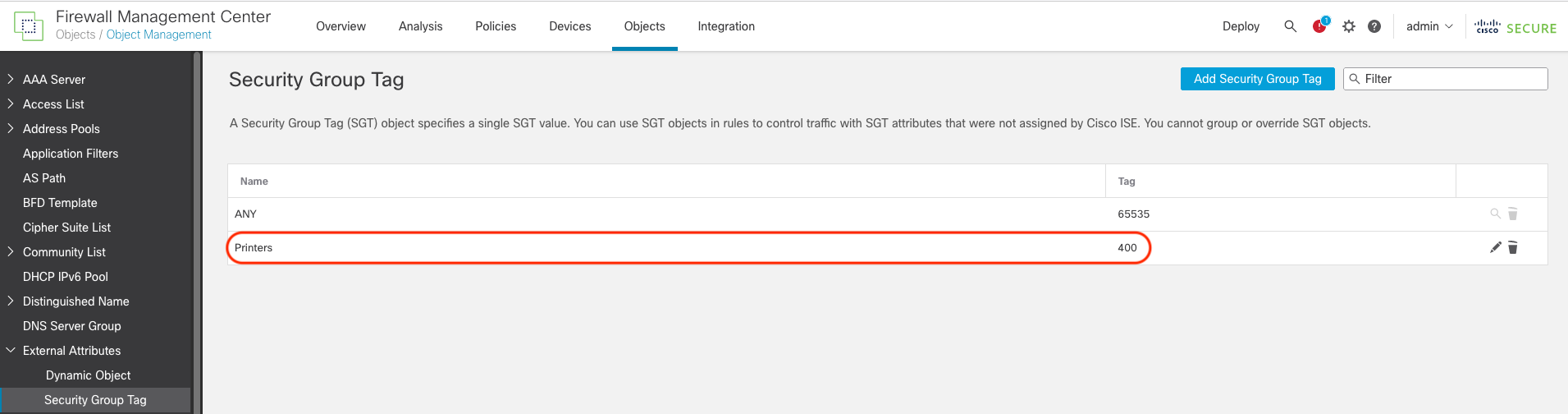
FMC also allows inline addition of these custom SGTs in extended ACL.
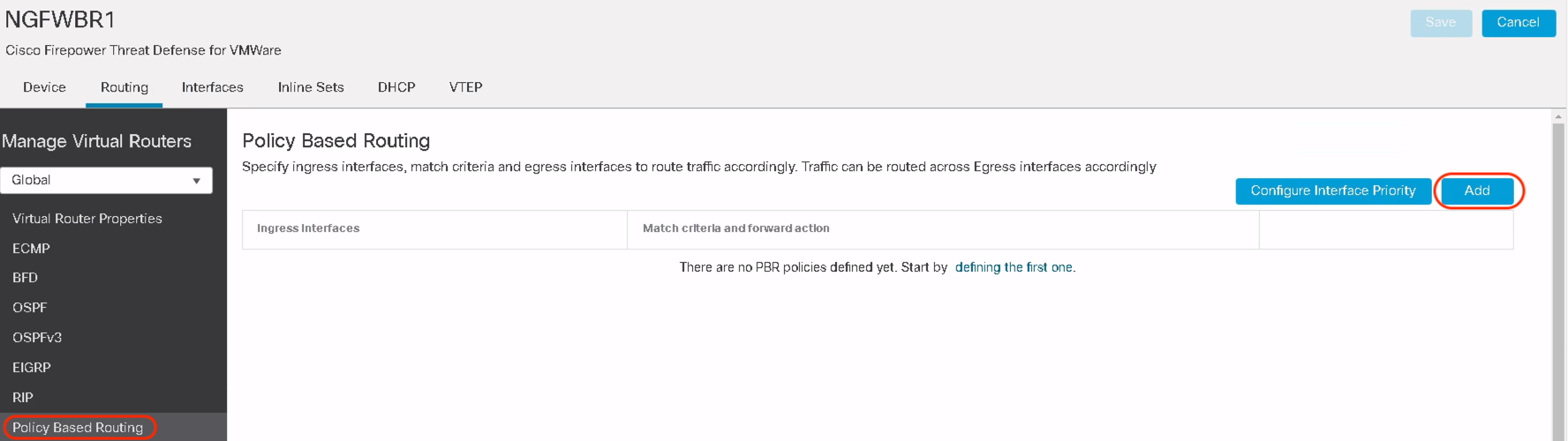
Step 9: Navigate to Device Management > Edit Device > Routing > Policy Based Routing and click Add to configure the PBR rule.
Step 10: Select the Ingress Interface and click Add.
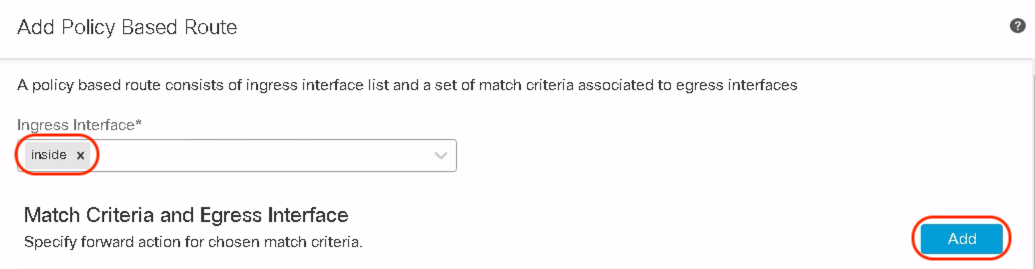
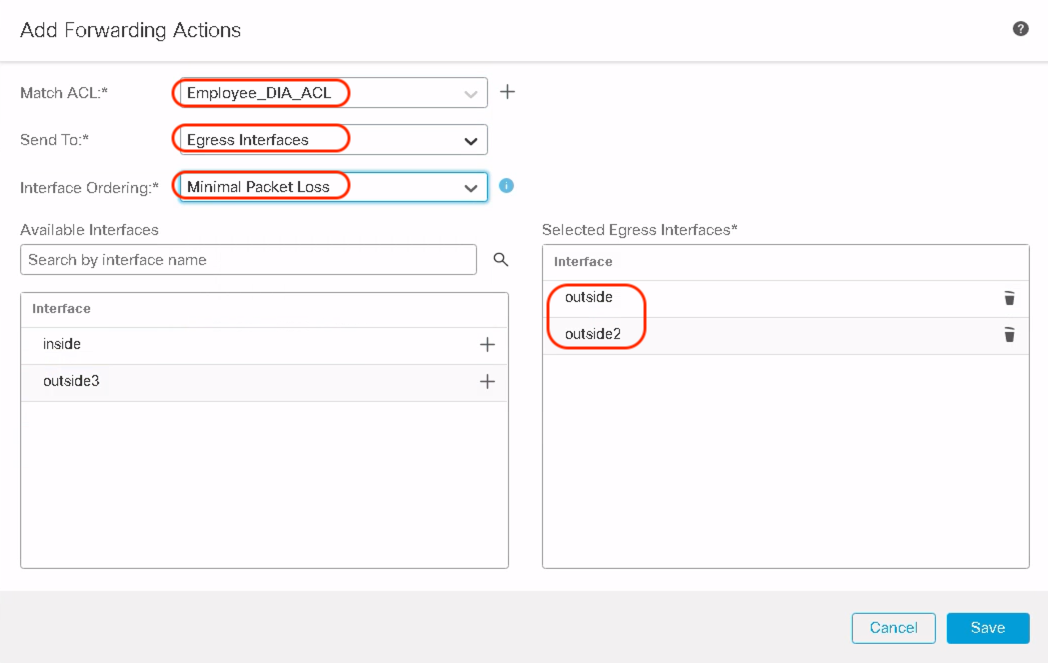
Within Match ACL, select the extended ACL defined in the previous steps to be used as the match criteria. Select the forwarding action to choose the egress interface based on different options e.g. order, priority, or path monitoring attributes e.g. minimal jitter, packet loss, RTT, or maximum MOS. Lastly, click Save.
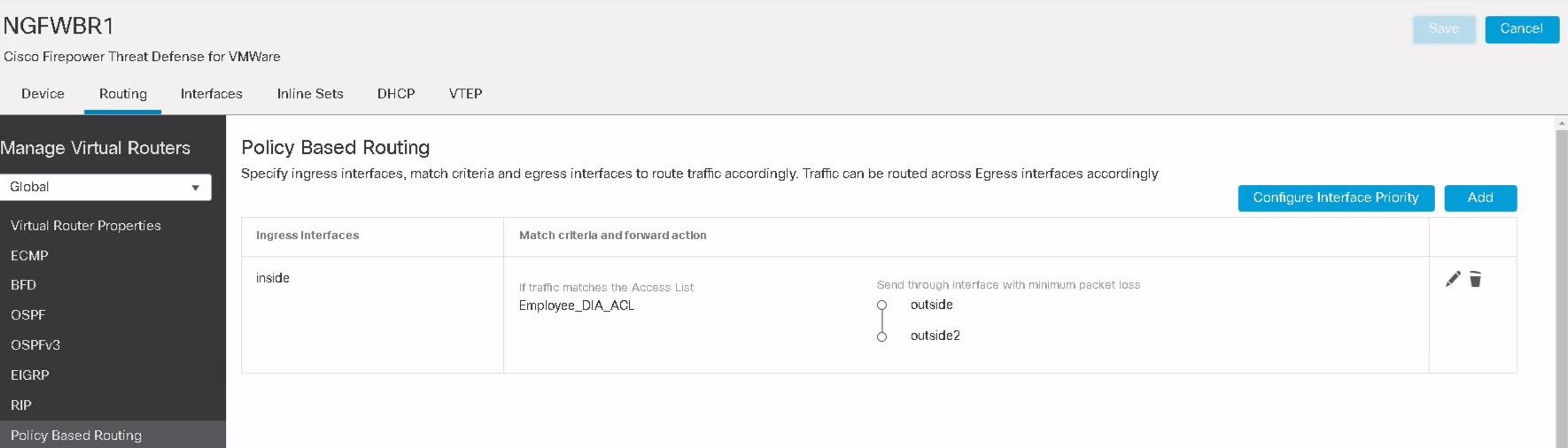
Step 11: Review the PBR rule created in the previous steps and Deploy the configuration to FTD.
️ Note
You can create additional PBR rules based on differentiated access for different users and applications. Traffic can be sent either through a direct ISP link, through a tunnel to Umbrella for cloud security, or directly to HQ or Hub site.
Verification
Here are some CLI commands you can use to verify the configuration is successfully deployed on FTD:
This command shows the deployed configuration for specified interfaces
show running-config interface
This command shows the route-map defined as part of FTD configuration deployment
show route-map
This command shows the access-list that includes identity-based rules
show access-list
This command shows the deployed configuration for specified interfaces
show object-group
Troubleshooting
All the show commands and debug commands that were used for policy-based routing in the previous releases are still applicable. For more details, please check the following link:
https://secure.cisco.com/secure-firewall/docs/policy-based-routing-with-path-monitoring
In addition, additional debug commands are added:
debug user-identity ftd-id
This command displays the relevant output as identity information is read from FMC
debug user-identity all
This command shows additional information as the identity information is processed
For troubleshooting AD/LDAP realm and ISE-FMC integration, please refer to the following docs:
- https://www.cisco.com/c/en/us/td/docs/security/secure-firewall/management-center/device-config/740/management-center-device-config-74/identity-realms.html#reference_9F6035406C884E24949A7EDAE8B868A9
- https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/200319-Troubleshoot-ISE-and-FirePOWER-Integrati.html
- https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine-32/220856-configure-and-troubleshoot-ise-3-2-with.html#toc-hId--674561381
Limitations
- User Identity support in PBR is limited only to users from AD/LDAP realm
- Local Realm Users, Special/Discovered Identities, and Azure AD users are not supported
- Wildcard User groups are not supported
- This feature is not supported in a clustered configuration
- Only the Source Security Group Tag is supported
Summary
In release 7.4, PBR provides enhanced support for user identity, user groups, and SGTs to route the user and application traffic. This helps Secure Firewall administrators with increased granularity in terms of how traffic is steered through Secure Firewall devices to provide the optimum path and result in a better user experience.
📚Additional Resources
To learn more about the PBR policies using User Identity and SGT, please refer to the following guide:
Updated over 2 years ago