Hardware Innovations in 7.6
Cisco Firewall Platform Innovations in Release 7.6
Introduction
The Cisco Secure Firewall 7.6 Release introduces key new hardware capabilities for the current lineup of Cisco Firewalls. This document describes the following:
- 2-Port 400 Gigabit Network Module for Secure Firewall 4200
- Individual Interface Mode Support for Clustering on Secure Firewall 3100 & 4200 Series
- Crypto Acceleration for DTLS on Secure Firewall 3100 & 4200 Series
- USB Port Control
2-Port 400-Gigabit Network Module for Secure Firewall 4200 Series
The Cisco Secure Firewall 4200 series supports various network modules to enhance its functionality and adapt to different network environments. These modules provide additional interfaces and capabilities, allowing for greater flexibility and scalability.
The Secure Firewall 4200 has two network module slots named NM-2 and NM-3, located left and right of the onboard interfaces of the front panel. Network modules are optional, removable interface modules that provide either additional ports or different interface types. Consult the Hardware Installation Guide for the location of these network modules on the front-panel of the Secure Firewall 4200 chassis.
The 7.6 Release adds a new 2-Port, 400G Network Module for Secure Firewall 4200. This new form-factor requires the following minimum support:
| Orderable PID | Description | Minimum FMC Version | Minimum FTD Version | Minimum ASA Version | Supported Platform |
|---|---|---|---|---|---|
| FPR4K-XNM-2X400G | 2-port 40/100/200/400G QSFP/QSFP28/QSFP56/QSFP-DD | 7.6.0 | 7.6.0 | 9.22.1 | Secure Firewall 4200 Series |
Note
Configuration for these network modules in the FMC Web Interface and ASA CLI is identical to that of previous releases.
The 2-port 400G network module is designed for 400-Gigabit operation, and also supports 200-Gigabit, 100-Gigabit, and 40-Gigabit full-duplex operation per port. The QSFP ports are numbered left to right - Ethernet 2/1 or Ethernet 3/1 through Ethernet 2/2 or Ethernet 3/2.
Below, is a breakdown of the front-panel of the 2-port 400G network module:
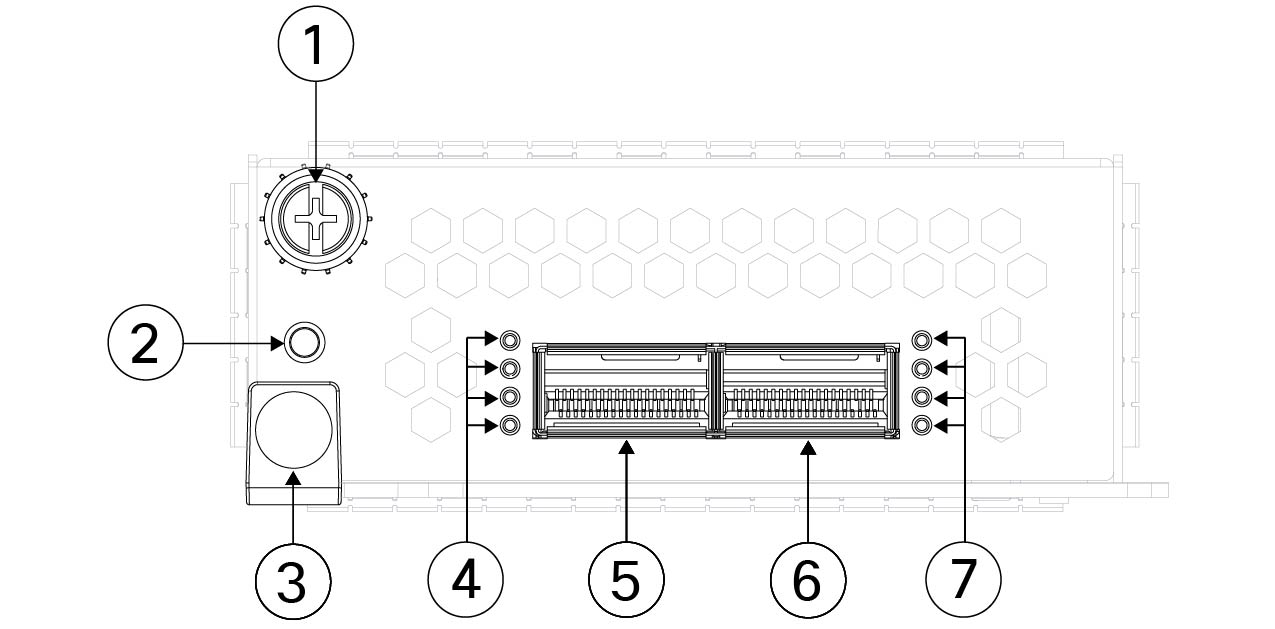
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
|---|---|---|---|---|---|---|
| Captive Screw | Power LED | Ejector Handle | Network activity LEDs | Ethernet 2/1 or Ethernet 3/1 | Ethernet 2/2 or Ethernet 3/2 | Network activity LEDs |
Network modules enable customization of the Cisco Secure Firewall 4200 series, further optimizing for specific network environments. By selecting the appropriate modules, organizations can ensure that their firewall solution meets performance, connectivity, and security requirements.
Individual Interface Mode Support for Clustering on Secure Firewall 3100 & 4200 Series
In terms of clustering in Secure Firewall, individual interfaces play a pivotal role in ensuring high-availability, load balancing, and seamless failover. The clustering capability, has been around for some time and allows for multiple physical firewall devices to operate as a single logical device.
Individual interfaces are normal routed interfaces, each with their own local IP address. Alternatively, clustering configuration can use groups of one or more interfaces in an EtherChannel, which is called Spanned Mode. Below is a comparison between Individual Mode interfaces and Spanned Etherchannels in terms of clustering deployments:
| Feature | Spanned EtherChannels | Individual Mode Interfaces |
|---|---|---|
| OSI Layer used for Traffic | Layer 2 | Layer 3 |
| Bandwidth | Higher aggregate bandwidth | Limited to the capacity of individual interfaces |
| Redundancy | High, with failover capabilities | Depends on the configuration of each interface |
| Management | Simplified, single logical interface | More complex, multiple interfaces to manage |
| Load Balancing | Yes, across aggregated links | No, each interface operates independently |
| Traffic Isolation | Less granular, all traffic types share the same logical interface | High, each traffic type can have a dedicated interface |
In prior releases, only Spanned Mode was supported when configuring a cluster from Firewall Management Center (FMC). The Secure Firewall 7.6 Release introduces the Individual Interface Mode for clustering of Secure Firewall 3100 and 4200 Series firewalls for improved topology handling when a change occurs.
Configuration Workflow
Individual mode clustering allows each cluster member to have its own dedicated data interface IP address and dynamic routing adjacencies. In the Add Cluster Wizard, administrators now have the option to choose between Individual mode and Spanned mode. Login to the FMC and navigate to Devices > Device Management to get started.
-
Click Add > Cluster
-
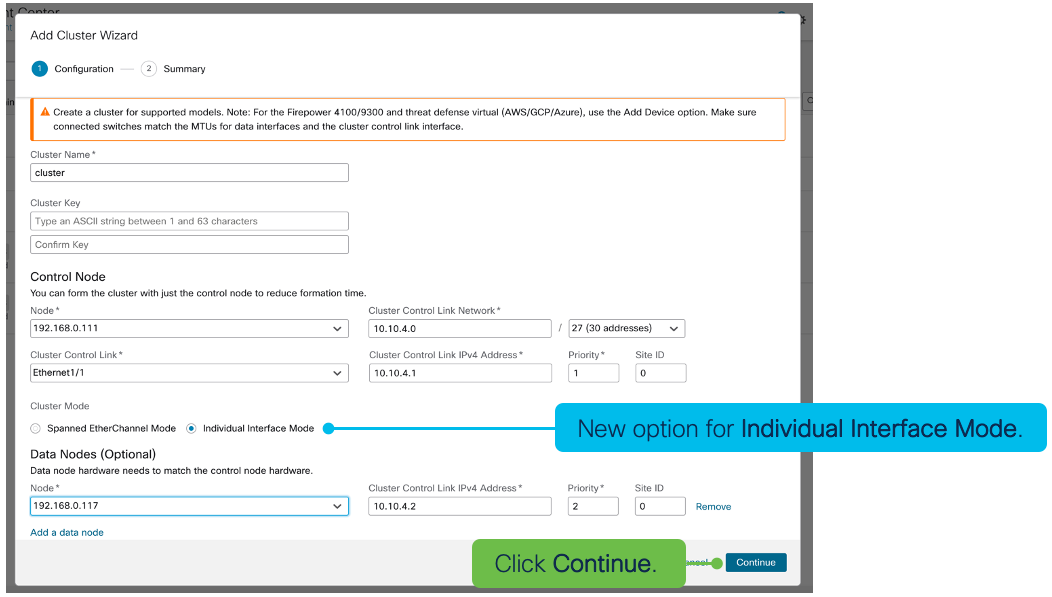
In the Add Cluster Wizard there is a new option for Individual Interface Mode. Check the radio icon and add the necessary configuration details applicable to the environment.
-
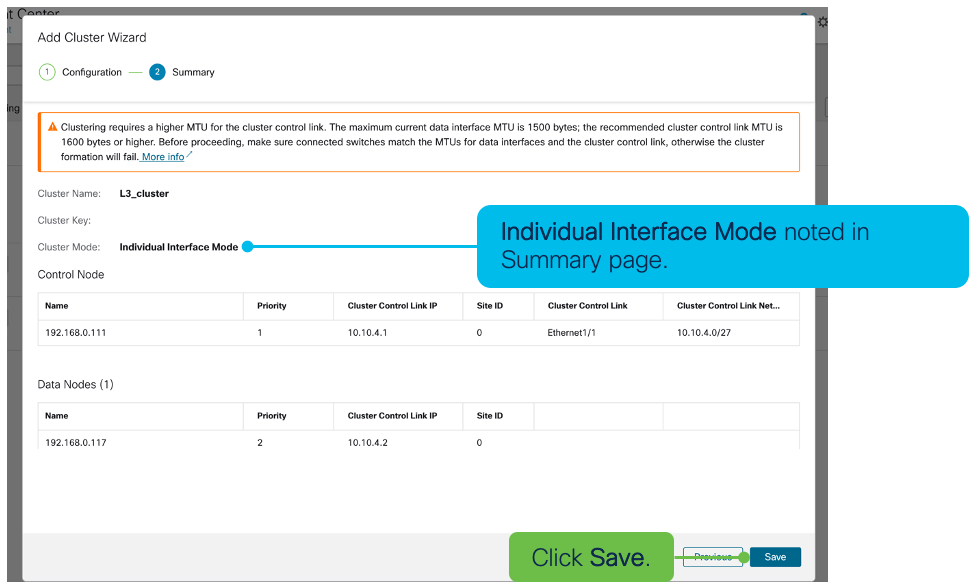
In the Summary, note the Cluster Mode is set to Individual Interface Mode. Click Save.
-
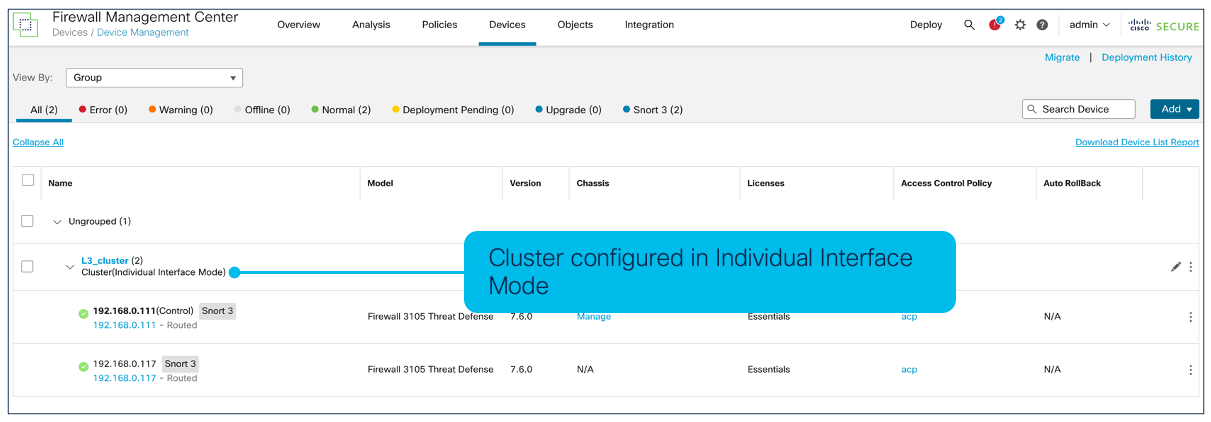
Back in the Device Management page, in the cluster description will be a note that it is configured in Individual Interface Mode.
When clustering firewalls, the choice between using spanned EtherChannels and individual mode interfaces can impact the performance, redundancy, and management of the network. With the addition of Individual Interface support the network's performance can be more equipped for topology changes, granular control, and simplicity in the network.
Crypto Acceleration for DTLS on Secure Firewall 3100 & 4200 Series
The Secure Firewall 7.6 release enables the Crypto Acceleration for DTLS feature on Secure Firewall 3100 and 4200 Series firewalls. This feature refers to the capability of offloading DTLS processing from the main CPU to the dedicated Field-Programmable Gate Array (FPGA) with the intent to significantly improve performance and efficiency of the firewall.
What is DTLS Offload and How Does it Work?
Datagram Transport Layer Security (DTLS) is a protocol designed to provide security for datagram-based applications, similar to how TLS secures stream-based applications. DTLS is common in scenarios where low latency is critical, like VPNs.
DTLS offload refers to the process of transferring the processing of DTLS encryption and decryption from the main CPU to dedicated hardware, the FPGA. This is useful in high-performance network environments where there is a large volume of encrypted traffic.
How it works is by leveraging the FPGA, which is better-optimized for cryptographic operations inside the firewall. When DTLS traffic arrives at the firewall, it is redirected to the FPGA for encryption and decryption. This frees up the main CPU so that it can focus on separate tasks like routing, policy enforcement, deep-packet inspection, etc. By leveraging DTLS Offload, administrators can take advantage of increased throughput, lower latency, CPU efficiency, and increased scalability.
- Increased Throughput: By offloading DTLS processing to the FPGA, the Secure Firewall supports higher volumes of encrypted traffic, making it an ideal choice for large enterprises and service providers.
- Lower Latency: Hardware-based traffic processing is typically faster and more efficient than software-based processing, hence lowering latency for encrypted traffic. This is particularly useful in VPNs, VoIP, and video conferencing.
- CPU Efficiency: By allowing the dedicated hardware to process DTLS traffic, this leads to an overall improvement in the performance and responsiveness of the Secure Firewall.
- Scalability: Offloading DTLS to the FPGA allows increased amounts of traffic to be processed without additional hardware. This is a cost-effective solution in growing network environments.
By accelerating DTLS connections on the Cisco Secure Firewall 3100 and 4200 series, it enhances the firewall's ability to manage encrypted traffic, achieve higher throughput, lower latency, and increase overall performance. The ability to offload DTLS from the main CPU not only improves performance, but also ensures that the firewall can scale to meet the evolving demands of the network.
USB Port Control
Cisco Secure Firewall platforms are equipped with a front-facing USB port serving various purposes for tasks like initial setup, firmware upgrades, backups, etc. While USB ports may provide convenient functionality, they also pose potential security risks if not managed properly.
The Cisco Secure Firewall 7.6 release provides a configurable option to disable the front-facing USB port for the following platforms:
- Firepower 1010 Series
- Firepower 1100 Series
- Secure Firewall 3100 Series
- Secure Firewall 4200 Series
Note
This feature can only be configured via the following methods for Secure Firewall 7.6 and ASA 9.22.1:
- FTD CLI
- FXOS CLI - Multi-Instance Deployments Only
- ASA CLI
- ASDM
Noted below is the front-panel USB port on Firepower 1010 and 1100 Series, Secure Firewall 3100 Series, and Secure Firewall 4200 Series:
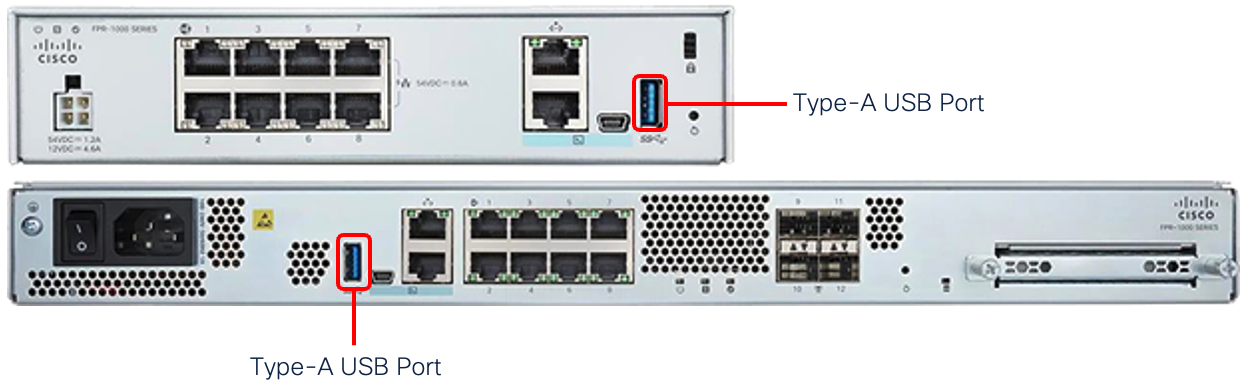
Figure 1: Firepower 1010 & Firepower 1100 Front-Panel USB Port

Figure 2: Secure Firewall 3100 Front-Panel USB Port
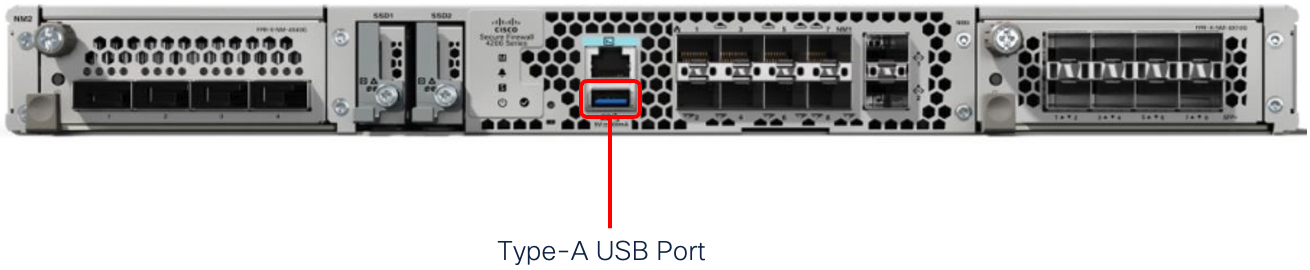
Figure 3: Secure Firewall 4200 Front-Panel USB Port
Below is the minimum software and hardware platforms supported with this feature:
| Minimum FTD | Minimum FXOS - Multi-Instance Deployments Only | Minimum ASA | Supported Platforms |
|---|---|---|---|
| 7.6.0 | 2.16.1 | 9.22.1 | Firepower 1010 Firepower 1100 Secure Firewall 3100 Secure Firewall 4200 |
Configuration Workflow
USB Port Control first requires a set of commands on either the FTD, ASA, or FXOS CLI depending on deployment type. Login to your device and enter the commands required applicable to the environment.
Note
For all deployment types (eg. FTD, Multi-instance, ASA, or ASDM) a reboot will be required to push the changes to the device.
FTD CLI Commands
Login to the FTD CLI and enter the following commands:
> System support usb show
USB Port Info
---------------
Admin State: [enabled | disabled]
Oper State: [enabled | disabled]
>
> system support usb configure disable
USB Port Admin State set to 'disabled’.
Please reboot the system to apply any control state changes
>
> reboot
This command will reboot the system. Continue?
Please enter 'YES' or 'NO': YES
FXOS CLI Commands - Multi-Instance Deployments Only
firepower-4245 /fabric-interconnect # show usb-port Usb Port:
Equipment Admin State Oper State
---------------- ----------- ----------
A Enabled Enabled
firepower-4245 /fabric-interconnect # disable usb-port
Note: USB enablement or disablement changes are effected only after FXOS reboot. Confirm change? (yes/no) [yes]:yes
firepower-4245 /fabric-interconnect* # commit
Note: USB enablement or disablement changes are effected only after FXOS reboot. Confirm change? (yes/no) [yes]:yes
firepower-4245 /fabric-interconnect # connect local-mgmt
firepower-4245(local-mgmt)# reboot
Before rebooting, please take a configuration backup.
Do you still want to reboot? (yes/no):yes
firepower-4245# scope fabric-interconnect
firepower /fabric-interconnect # show usb-port
Usb Port:
Equipment Admin State Oper State
---------------- ----------- ----------
A Disabled Disabled
ASA CLI Commands
ciscoasa(config)# show usb-port
USB Port info
---------------
Admin State: enabled
Oper State: enabled
ciscoasa(config)#
ciscoasa(config)# usb-port disable
Requesting USB disable. This may take 30 seconds to complete.
Please execute 'write memory' and reboot the system to apply any operational state changes.
ciscoasa(config)#
ciscoasa(config)# show usb-port
USB Port info
---------------
Admin State: disabled
Oper State: enabled
ciscoasa(config)# reload
System config has been modified. Save? [Y]es/[N]o: y
Cryptochecksum: 386a10ea 9909f7c8 e3110e6c 5e6c2d1f
11500 bytes copied in 0.500 secs
Proceed with reload? [confirm]
ciscoasa(config)# show usb-port
USB Port info
---------------
Admin State: disabled
Oper State: disabled
ASDM
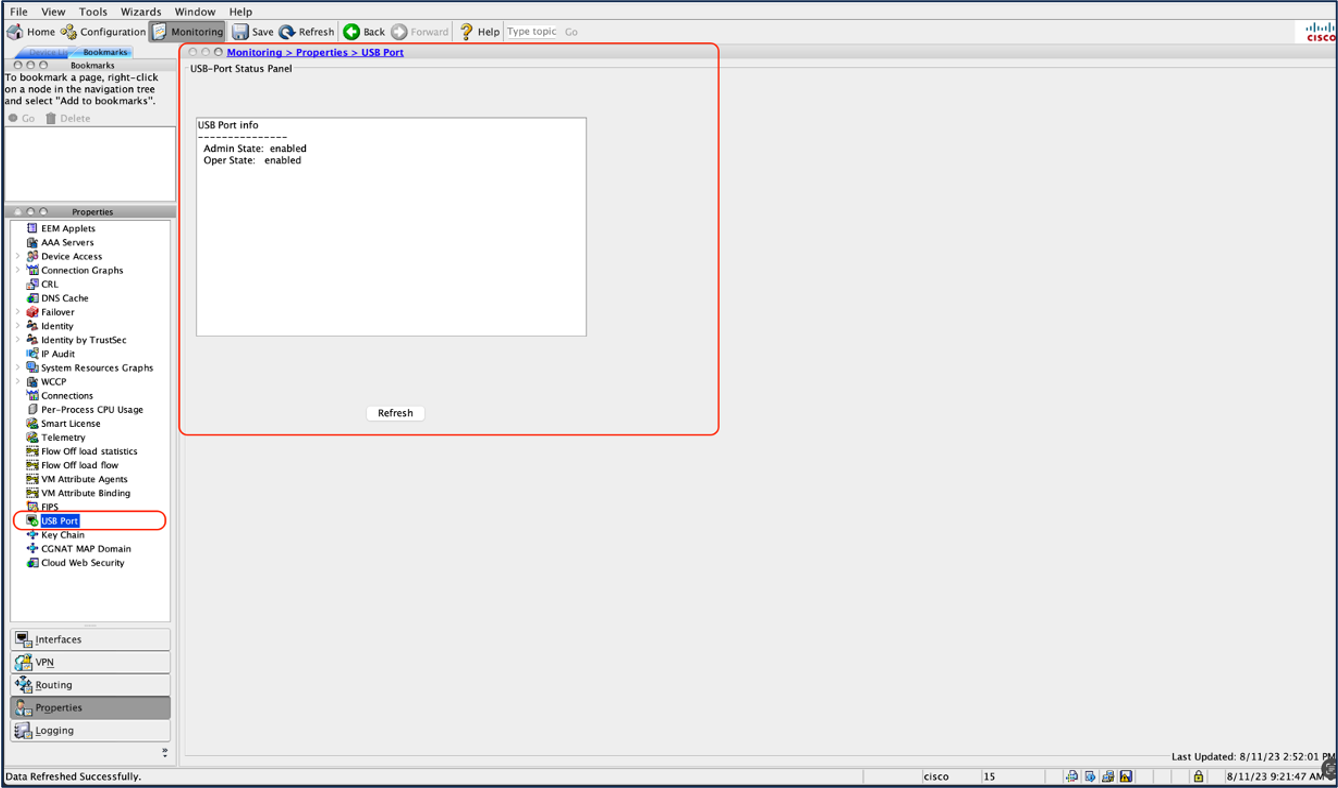
- Login to the ASDM interface and navigate to Monitoring > Properties > USB Port to check the current status of the USB port:
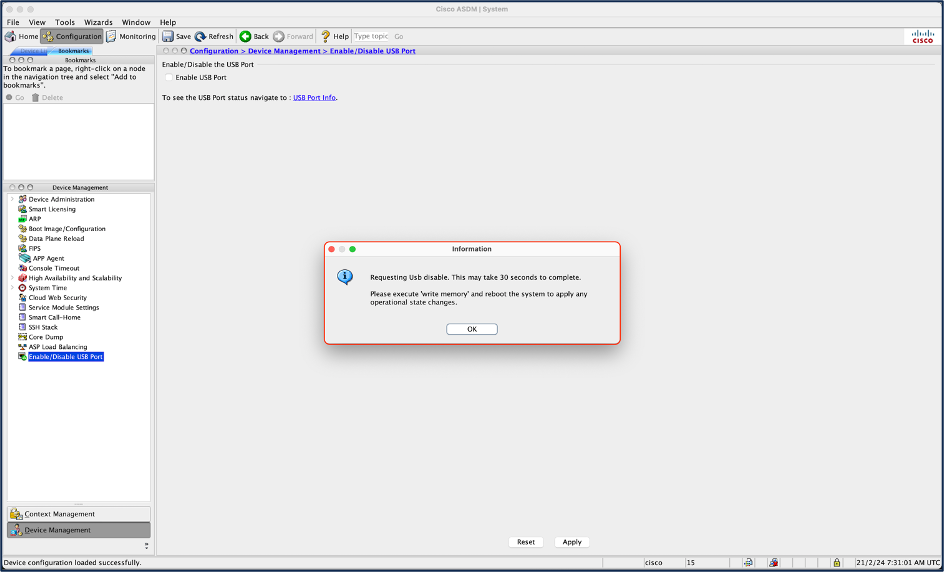
- Then navigate to Configuration > Device Management > Enable/Disable USB Port. Uncheck the box next to Enable USB Port:
- Apply changes by clicking Apply and then Send:
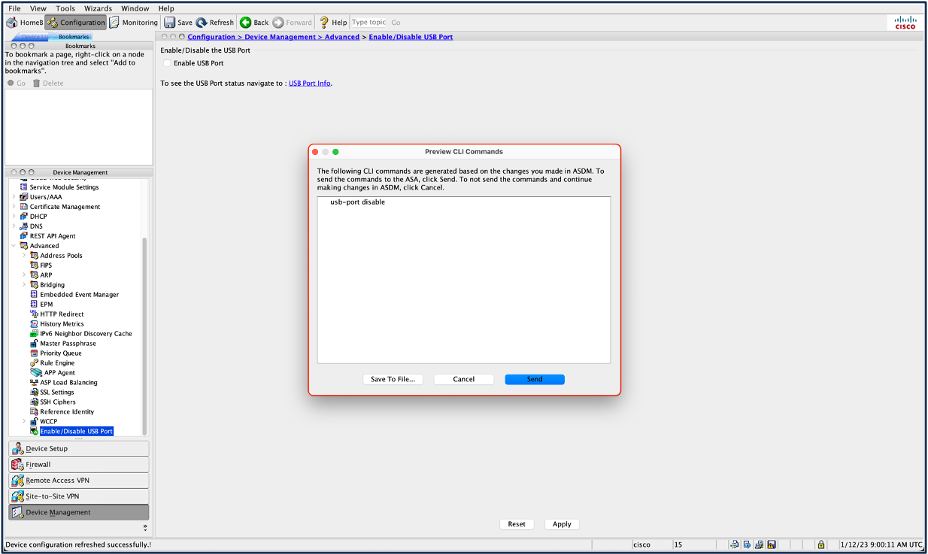
- Click Save. Now to push the changes, reboot the device using the Tools drop-down in top of the ASDM window.
Summary
The Cisco Secure Firewall hardware lineup offers a wide range of advanced features aimed at enhancing security, performances, and scalability in the enterprise network. USB Port Control provides administrators with the ability to manage and restrict USB port usage, hence mitigating physical security risks with unauthorized access and transfer of data. The 2-Port 400 Gigabit Network Module for Secure Firewall 4200 series evolves high-speed connectivity, making the module ideal for high-performance, large-scale deployments. Individual Interface Mode support allows for greater flexibility and scalability by bringing this feature to the Threat Defense software. Lastly, Crypto Acceleration for DTLS enhances processing for those connections, providing greater throughput, lower latency, and enhanced performance for encrypted traffic.
📚Additional Resources
Updated 8 months ago
