Deploy Threat Defense Virtual in an Existing VPC on AWS
Introduction
This document describes the procedure of deploying Cisco Secure Firewall Threat Defense Virtual and other network components on AWS using a terraform script. This procedure creates all the required resources inside an existing VPC on your AWS account. If you want to deploy the Threat Defense Virtual on AWS in a new VPC, see Deploy Threat Defense Virtual in a New VPC on AWS.
End-to-End Process
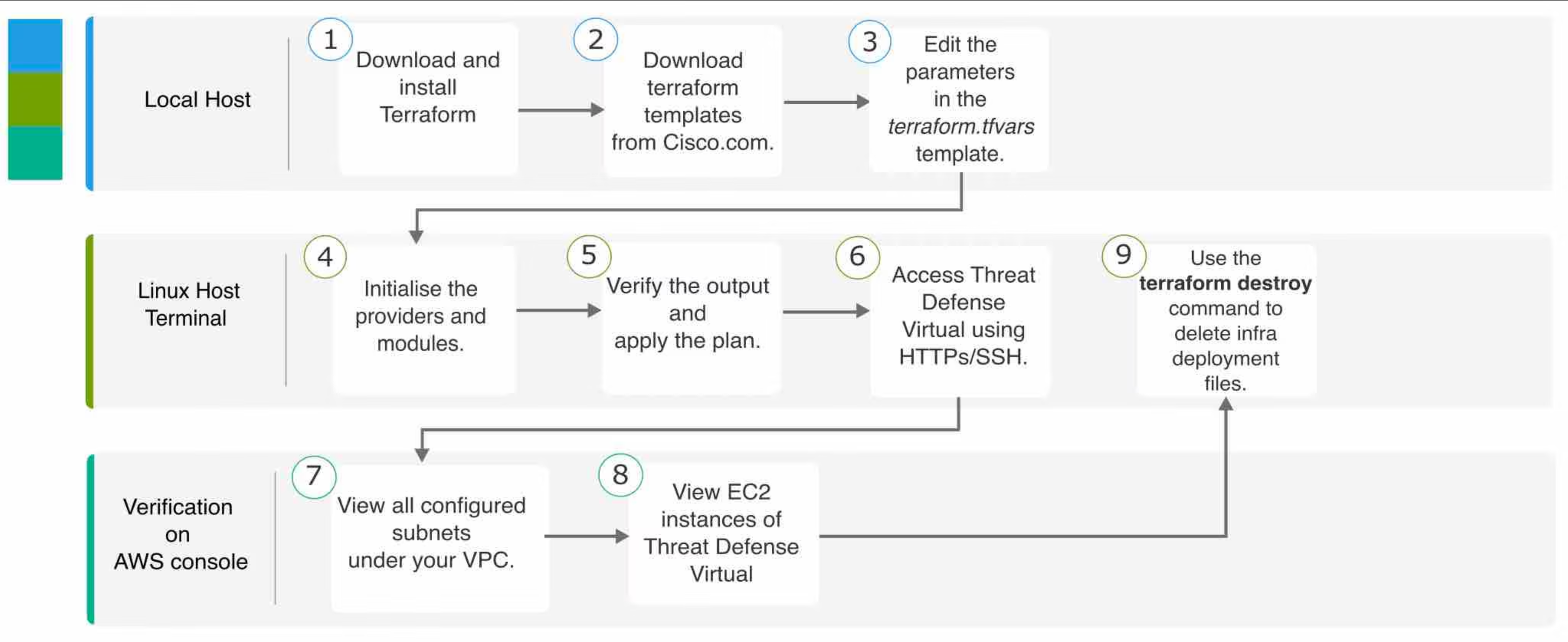
The following flowchart illustrates the workflow for deploying Threat Defense Virtual in an existing VPC on AWS.
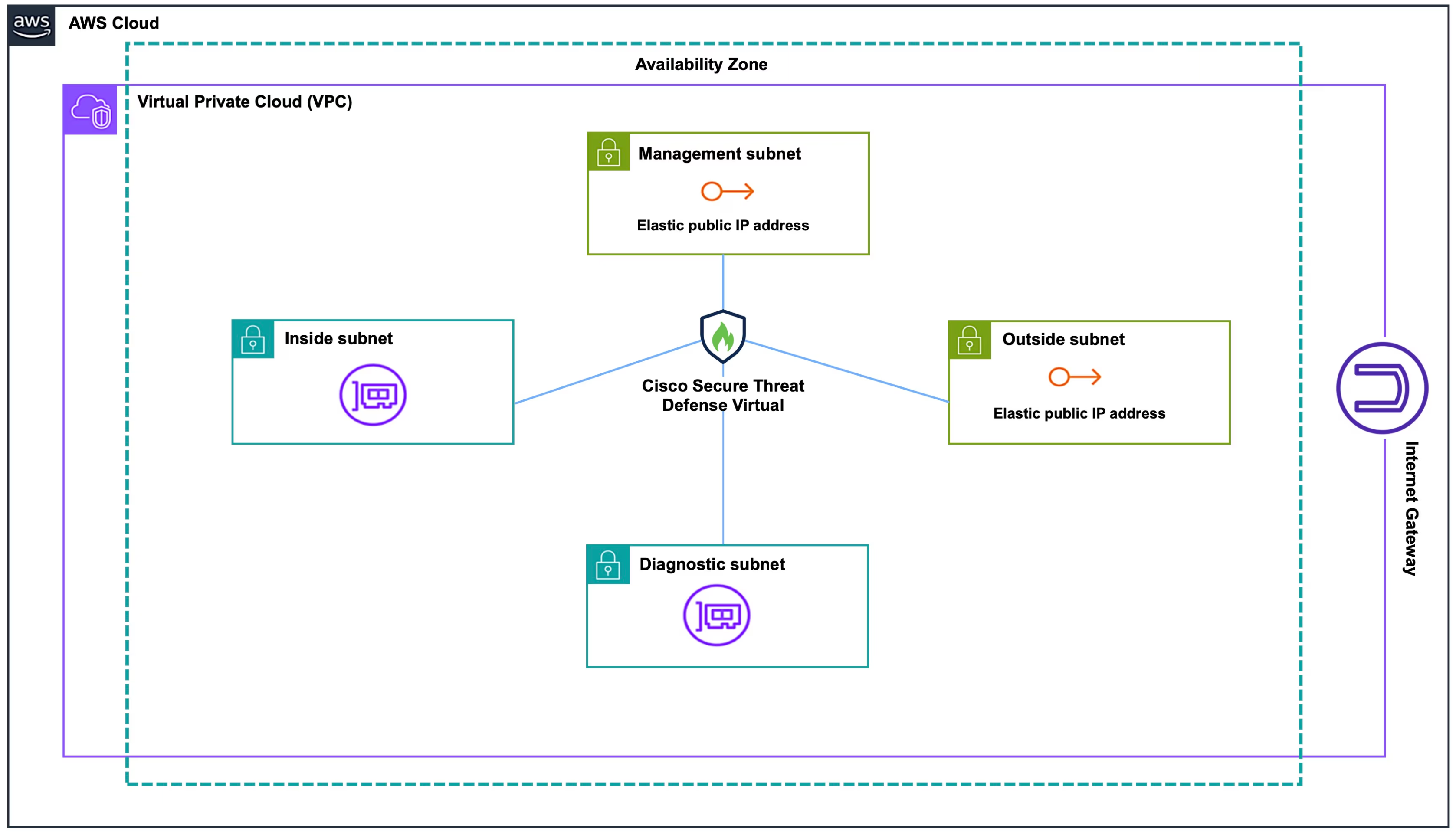
Sample Topology
The following network topology is deployed on AWS.
Prerequisites
- Download and install Terraform on your local machine. For more information, see Install Terraform.
- An AWS account with proper permissions for creating VPCs and EC2 instances. For more information, see Amazon VPC policy examples.
Procedure
Perform the following steps to deploy the required infrastructure in a VPC that already exists in your AWS account.
Procedure
- Download the terraform scripts from here.
- Extract the zip file and open the folder.
- Open the terraform.tfvars file by using a code editor or "vim" and provide inputs.
- Add your aws_access_key , aws_secret_key and region in the space provided between double quotes. For example, region = “us-east-1” . For information on how to fetch access keys and secret access key for your account, see Managing access keys for IAM users.
- Optionally, add a password for admin in the admin_password field. By default, the password is Admin123.
- If required, change the version of the Threat Defense Virtual in the "FTD_version" field.
- Provide the name of the VPC and the CIDR block in the vpc_name and vpc_cidr fields.
- If your VPC does not have an internet gateway attached to it, set the create_igw field to true. Otherwise, set it to false.
- Enter the appropriate subnet CIDR blocks for the four different subnets - mgmt_subnet, outside_subnet, inside_subnet , and diag_subnet.
NOTE:
Ensure that you only add subnet CIDRs that are not already present in the VPC to avoid any potential conflicts.
- Enter the private IP addresses corresponding to the respective subnet’s CIDR blocks in the ftd01_mgmt_ip, ftd01_outside_ip, ftd01_inside_ip and ftd01_diag_ip fields.
- Initialize the providers and modules by using the following command: terraform init
- Submit the terraform plan by using the following command: terraform plan --out filename
- Verify the output of the plan in the terminal and then apply the plan by using the following command: terraform apply filename
- The terraform output displays the IP address of the management interface and the command to SSH into the firewall. Use these to access the Threat Defense Virtual over HTTPs/SSH.
- Open the AWS console after the deployment is complete. Go to your provided region and validate the final configuration.
- Go to Service > VPC to view all the configured subnets under your VPC.
- Go to Service > EC2 to view the EC2 instance of Threat Defense Virtual with the name - Cisco Threat Defense Virtual.
NOTE:
Do not delete the .terraform folder and terraform.tfstate files as they are required for the clean-up process.
Clean-Up
We recommend that you delete the infrastructure deployment once it's not needed to prevent unnecessary billing on your AWS account.
To delete the infrastructure deployment that was created by terraform, enter the terraform destroycommand from the same directory in which you entered the terraform apply command.
terraform destroy
- Type "yes" to delete the infrastructure deployment.
NOTE:
The terraform destroy command does not delete anything that was manually configured on your AWS account.
- After entering the command, verify that all the resources are deleted from your AWS account.
Success!
You have now completed, "Deploy Threat Defense Virtual in an Existing VPC on AWS."
Updated almost 2 years ago
Check out our Secure Firewall Github page: https://github.com/CiscoDevNet/secure-firewall
Or our YouTube channel: https://www.youtube.com/cisco-netsec
