Security Content Tagging
Introduction
In release 7.3, MITRE Tactics, Techniques, and Procedures (TTPs) were added to Intrusion events and in release 7.4, the MITRE TTPs were added to select Malware events.
Given that the MITRE ATT&CK framework has become the standard language for security operations, it is crucial to represent it effectively in our Event Viewer. In release 7.6, Unified Event Viewer has been enhanced with a single pane view for MITRE ATT&CK techniques, progression graph, and other contextual enrichment.
Encrypted Visibility Engine (EVE) and Talos enrichment service enrich events with MITRE tags in a uniform standard. Hence, we now have MITRE contextual enrichment in EVE events and in Security-Related connection events.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework is an extensive knowledge base and methodology that provides insights into the tactics, techniques, and procedures used by threat actors aiming to harm systems. ATT&CK is compiled into matrices that each represent operating systems or a particular platform. Each stage of an attack, known as "tactics," is mapped to the specific methods used to achieve those stages, known as "techniques."
Each technique in the ATT&CK framework is accompanied by information about the technique, associated procedures, probable defenses and detections, and real-world examples.
The MITRE ATT&CK framework also incorporates Groups to refer to threat groups, activity groups, or threat actors based on the set of tactics and techniques they employ. By using Groups, the MITRE ATT&CK framework helps categorize and document behavior. For example, FIN4, Metador, and Rocke are examples of MITRE Groups and their TTPs are mapped and described within the appropriate MITRE ATT&CK matrix.
MITRE Enrichment
Below are the enhancements done in the Unified Event Viewer concerning MITRE:
- Columns MITRE and Other Enrichment are added with an expanded view detailing MITRE tactics, techniques, and progression graphs.
- Enhanced user-defined search using MITRE ATT&CK identifiers i.e., tactics and technique names.
View Events
To view MITRE and Other enrichment follow the below steps:
- Login to the FMC and go to Analysis > Unified Events .
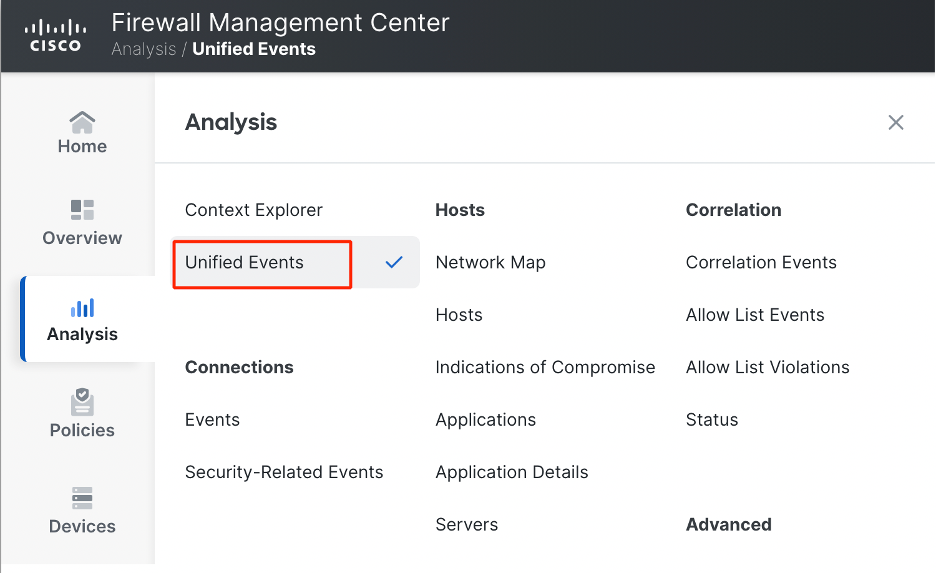
Navigate to Unified Events
- Click the icon above the rightmost column to load the column selection menu.
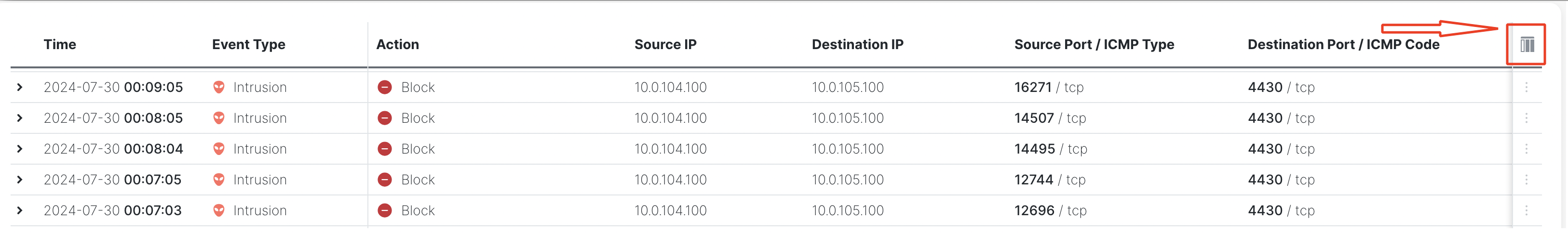
Column selection menu
- In the Filter columns bar, type in 'mitre.' Check the box next to MITRE ATT&CK.
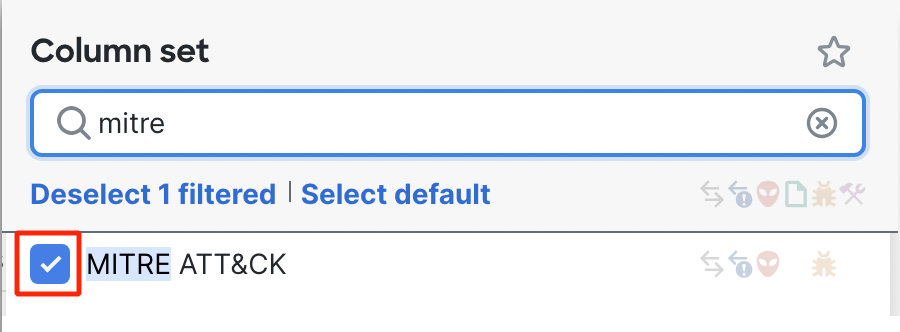
- Type 'other.' Check the box next to Other Enrichment and then click Apply to add the column to the Unified Event Viewer.
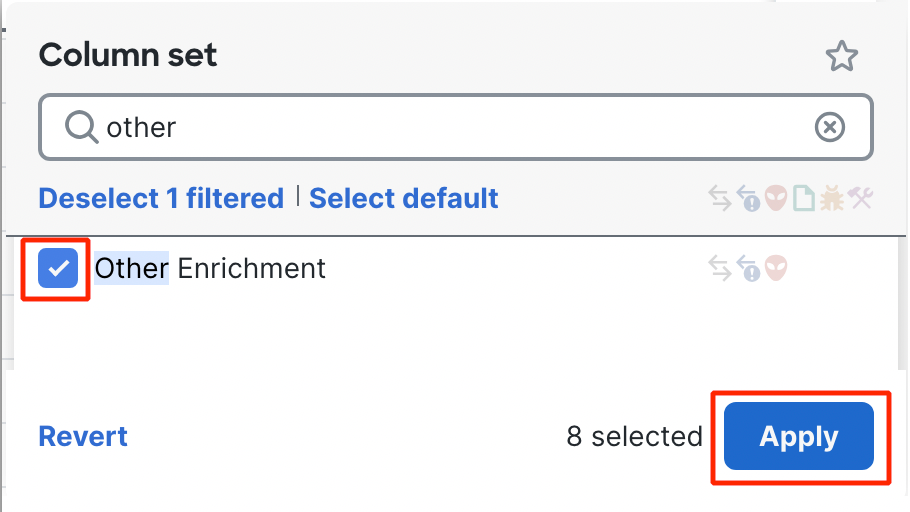
- The additional columns are added to the right side of the screen, if it is not in the immediate view you may need to scroll to the right.
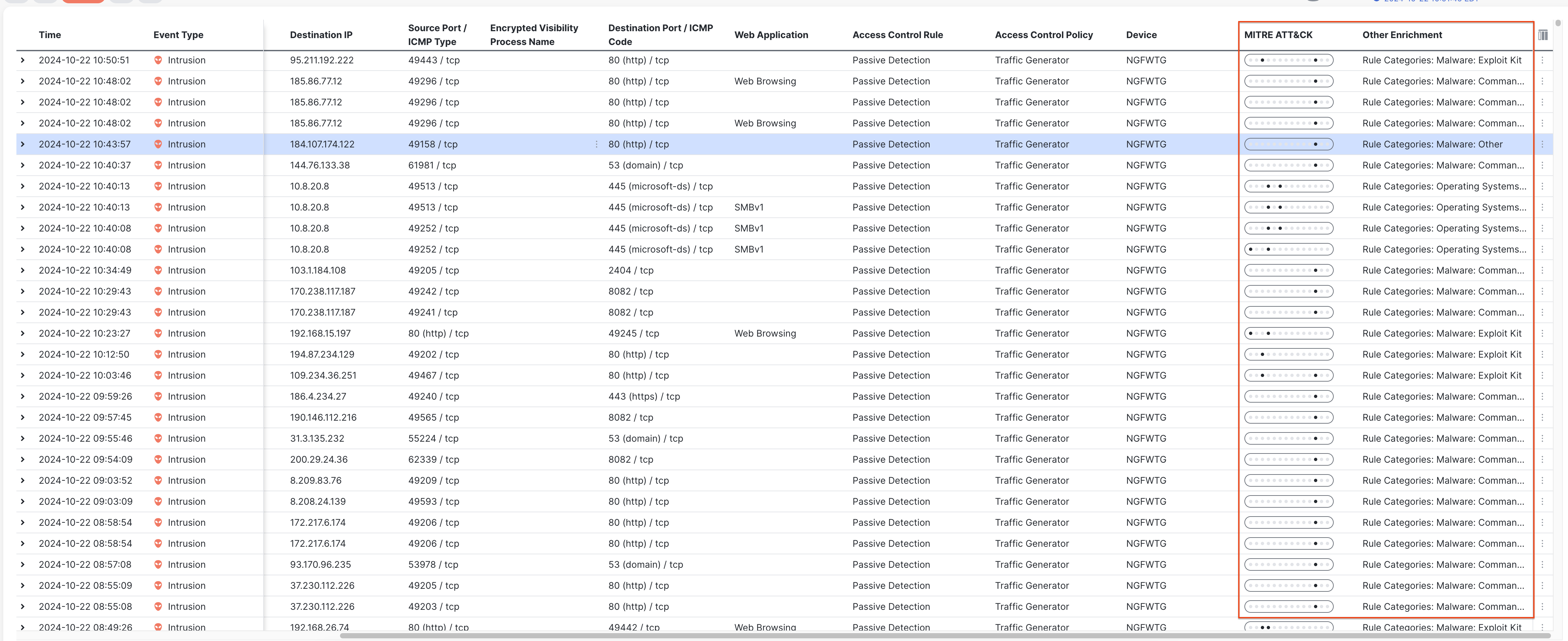
The progression graph under the MITRE ATT&CK column helps in visualizing the progress of the attack in the MITRE ATT&CK framework. Hovering your mouse over the progression graph shows all the tactics, highlighting the tactic corresponding to the attack. In the below example, Reconnaissance is the highlighted tactic.
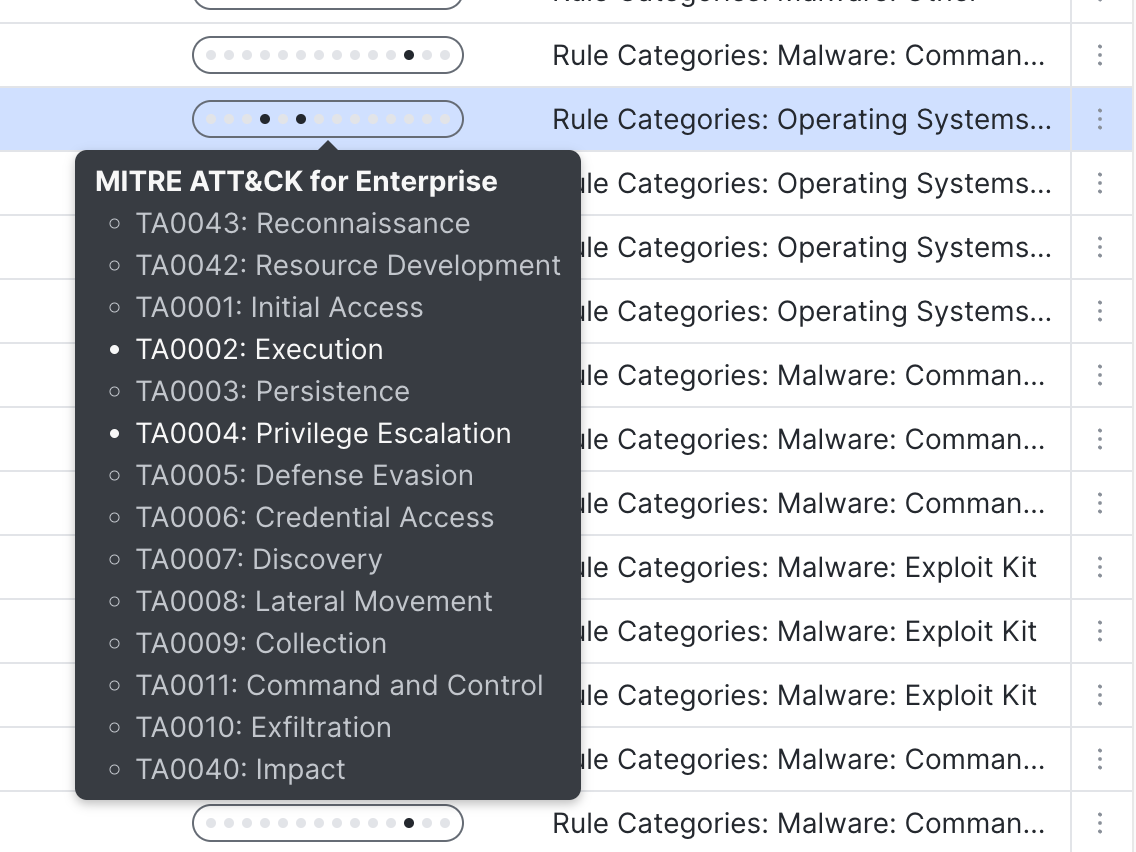
MITRE ATT&CK Tactics
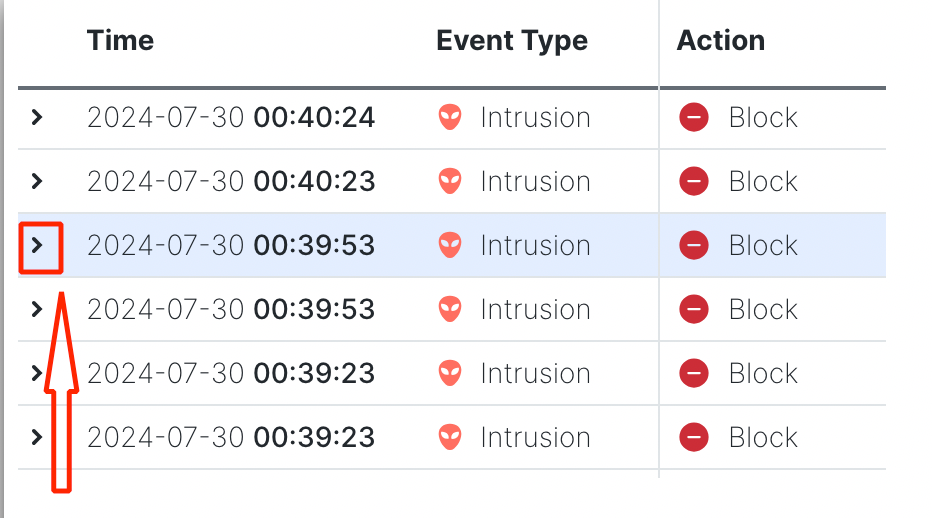
- Click on the angle bracket > on the left-hand side of an event to view the details of that event.
- Expand the Enrichments section to view the details of MITRE ATT&CK and Other Enrichment.
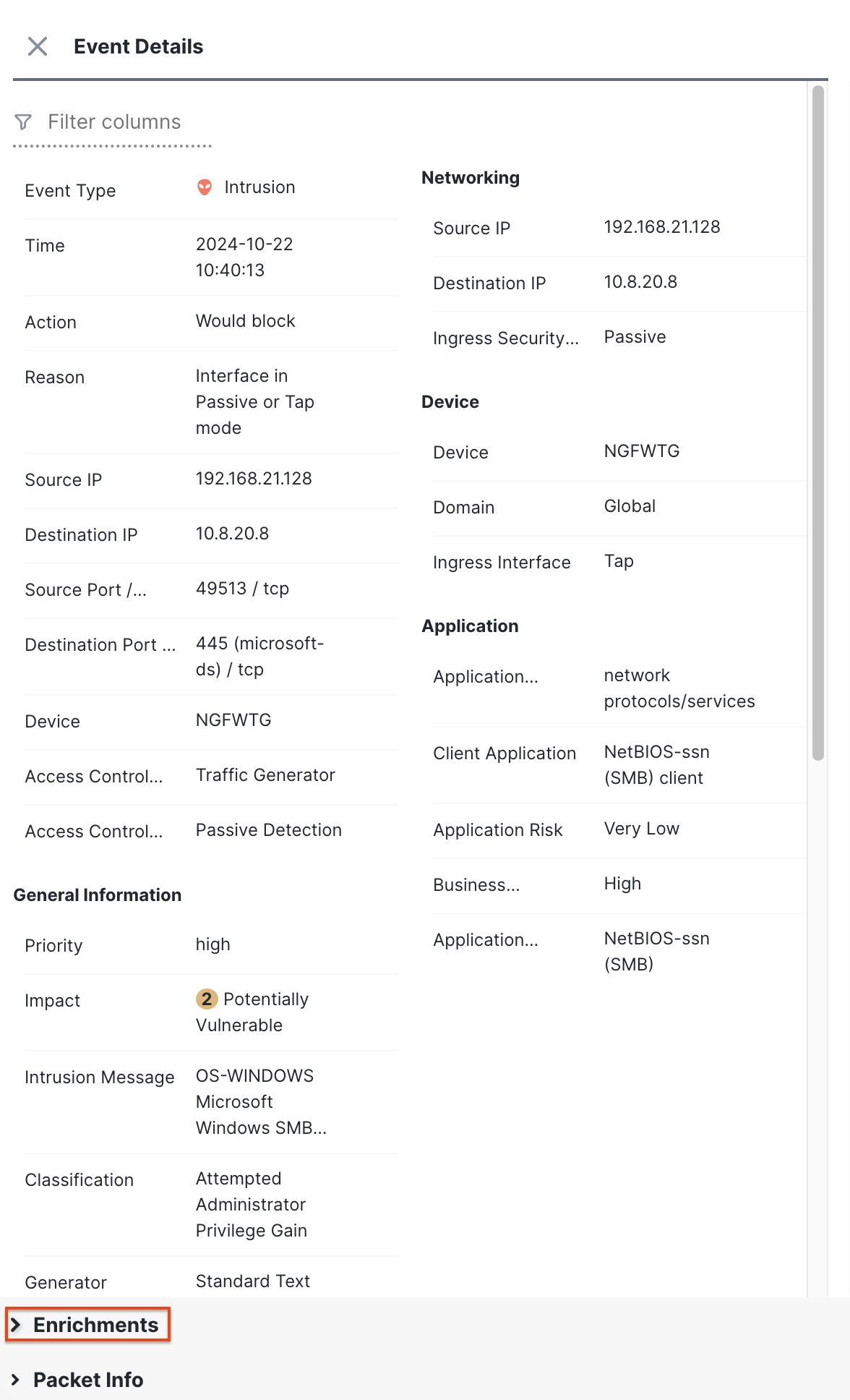
Event Details
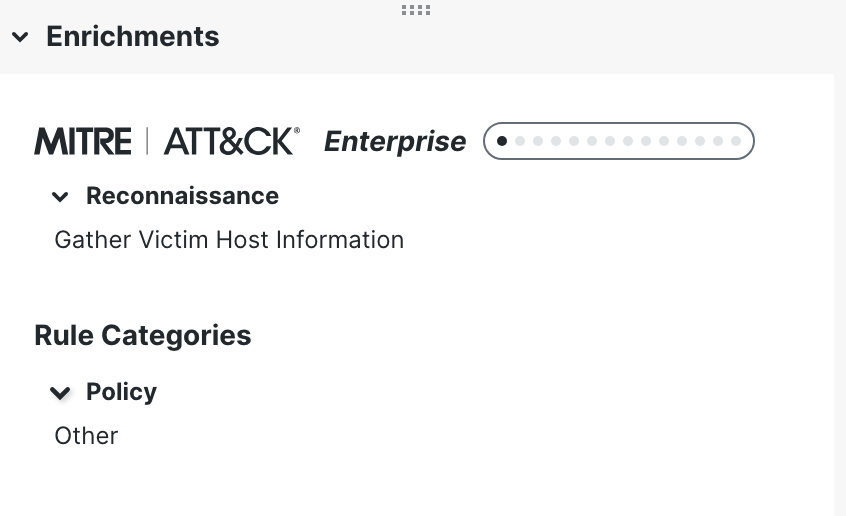
Enrichments
- For Encrypted Visibility Engine and Security-Related connection events, the Enrichments section also has a hyperlink to the MITRE ATT&CK official webpage for the corresponding tactic and technique. Click on Details to navigate to the webpage for further details on the attack.
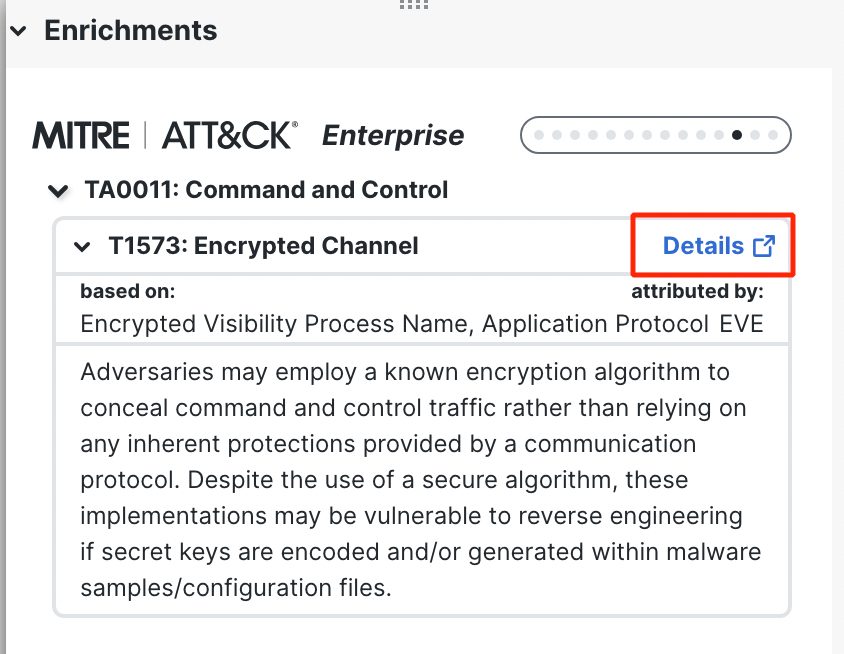
MITRE ATT&CK hyperlink
The attributed by field displays the source from where the MITRE tags were learned. In the below example, it is from EVE.
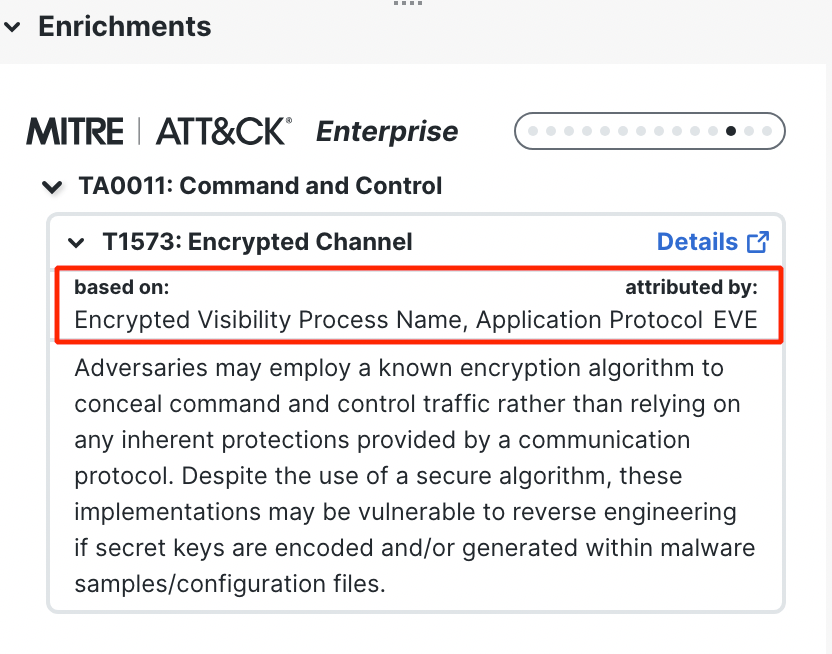
If the MITRE tags were sourced from Talos enrichment service, the attributed by field would be populated with talos.
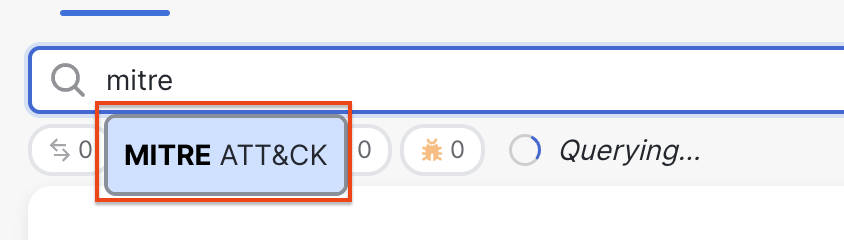
- The events can be filtered based on the tactic or technique under MITRE ATT&CK. Click on the search bar at the top of the Unified Event Viewer, type in 'mitre' and select MITRE ATT&CK.
- Type the tactic or technique you want to filter the events by, in the field space against MITRE ATT&CK. Click on Apply. In the below example, the events are filtered by the tactic Initial Access.
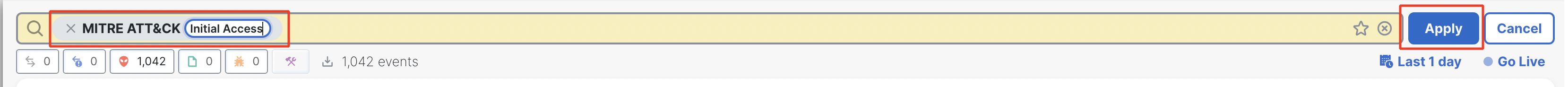
Filtering by tactic name
All the events belonging to the tactic Initial Access get displayed as shown.
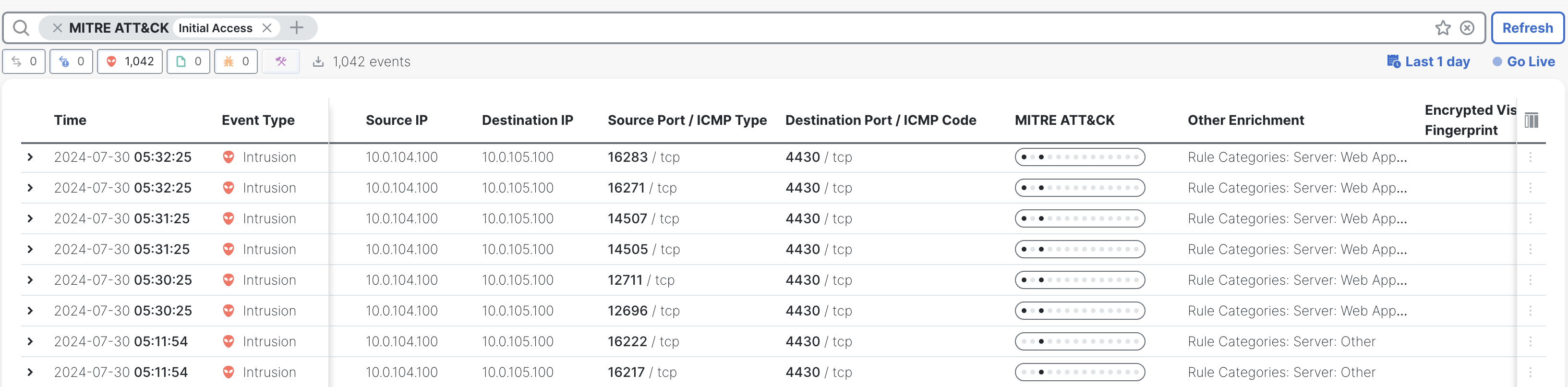
Events filtered by tactic name
Summary
Using MITRE tactics and techniques can enhance your cybersecurity efforts by providing a structured approach to threat detection, response, and analysis. With MITRE information in Intrusion, Malware, EVE, and Security-Related connection events, along with its enrichment with more relevant details, cyber threats can now be handled more effectively.
Updated 8 months ago
