QUIC Decryption
Introduction
QUIC, formalized as the transport protocol for HTTP/3, is a modern and efficient way for web servers and clients to exchange information over the internet, using the lightweight UDP protocol. It supports faster connection setup, better performance, and improved privacy and security. Today QUIC is supported by over 8% of websites on the internet, including many of the world's most popular sites. While this is a great benefit to users, it brings challenges for visibility and security within enterprise networks.
Cisco Secure Firewall has long supported QUIC in various ways--with AppIDs to detect and block QUIC, and as of version 7.2, support for native QUIC Application and URL visibility (thanks to the Encrypted Visibility Engine). Cisco Secure Firewall 7.6 now brings experimental support for QUIC traffic decryption. By decrypting QUIC traffic, the protocol is now on equal footing with TCP-based HTTPS, and administrators can decrypt traffic based on traditional criteria instead of worrying about the specific version of HTTPS in use.
Please note: QUIC Decryption in 7.6 is an experimental feature. Please test extensively before enabling outside of a lab environment.
Prerequisites and Recommendations
- Both the Firewall Management Center (FMC) and managed Firewall Threat Defense (FTD) devices must be running version 7.6.0 or later.
- QUIC Decryption is enabled as part of an existing Decryption Policy. (For guidance on creating a new policy, see Decryption Policy.)
- Managed FTDs must be using the Snort 3 engine.
- QUIC decryption is not currently supported for FTDs configured in a High-Availability Pair or Cluster.
- No special licensing is required for Decryption Policy or the QUIC decryption feature. However, to enable decryption based upon website category, a URL license is required. When performing decryption, it is generally recommended to apply intrusion and malware protections to the decrypted traffic, which requires the Threat and Malware licenses (respectively).
Enabling QUIC Decryption
-
In the FMC, navigate to Policies > Decryption and open the desired Decryption Policy.
-
Navigate to the Advanced Settings tab and flip the switch to enable QUIC Decryption.
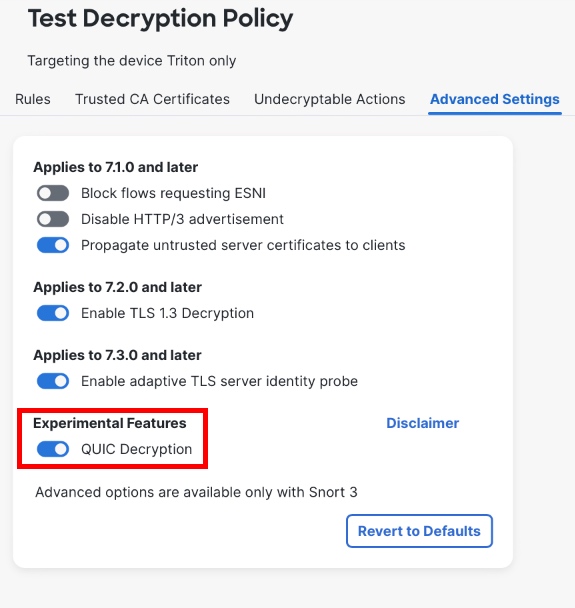
-
Ensure that your Decryption Policy rules are configured as desired, making sure (for instance) that they do not limit decryption to TLS only ports (such as TCP port 443). If needed, add rules to ensure QUIC traffic is targeted for decryption.
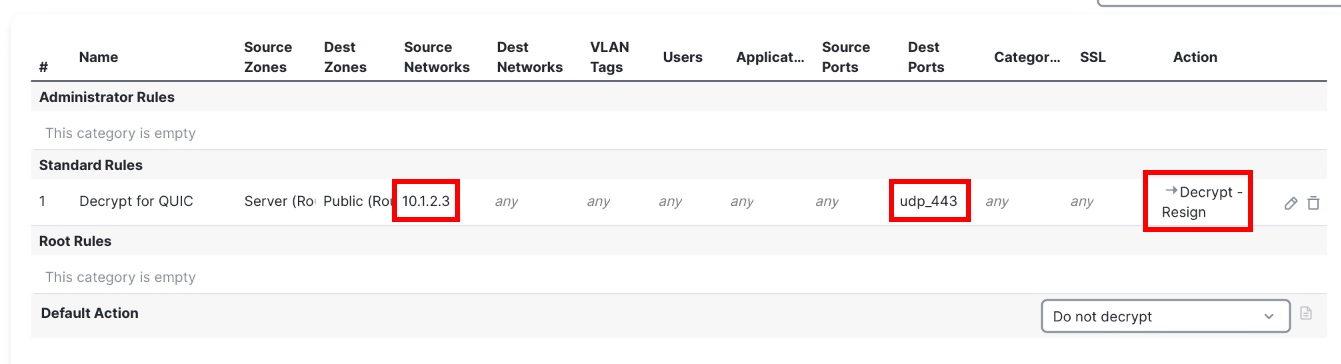
Example rule for illustration purposes only.
Please ensure that Access Control rules also allow QUIC traffic through the FTD device.
Testing QUIC Decryption
To validate that QUIC decryption is working, it is simplest to test directly in a web browser such as Firefox. Navigate to a website that is known to run over QUIC, such as the QUIC test site hosted by NGINX (quic.nginx.org). This example site will visually confirm whether the site has loaded over QUIC:
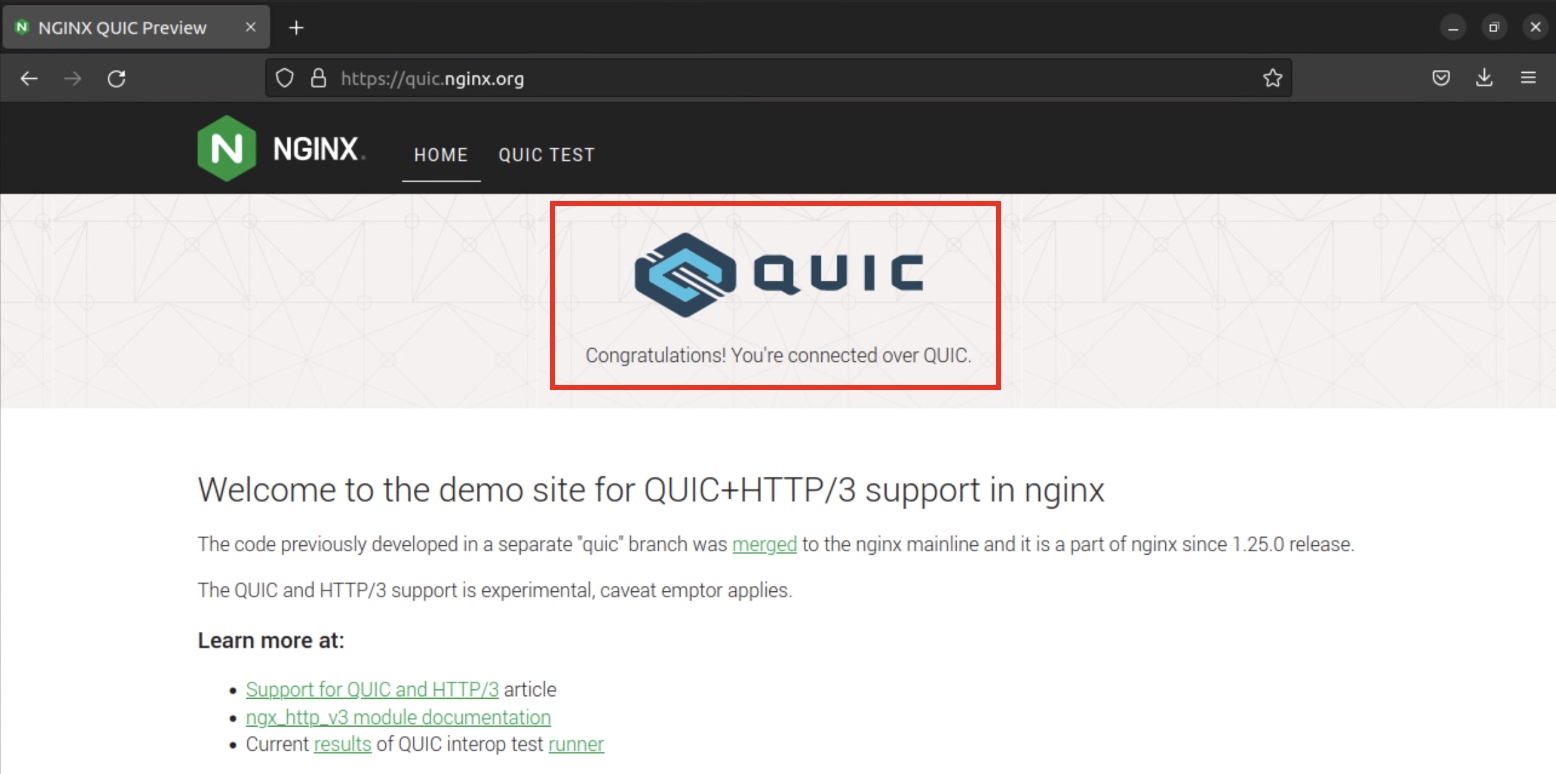
QUIC Test Site prominently displays whether or not QUIC is used.
Confirm that the firewall decrypted this connection by checking the certificate details. In most browsers this can be done by clicking on the Lock icon in the URL bar. In our example, the certificate issuer displayed is Cisco, confirming our FTD's re-signing certificate was used to decrypt the session. (Yours will show the name of your own enterprise certificate issuer.)
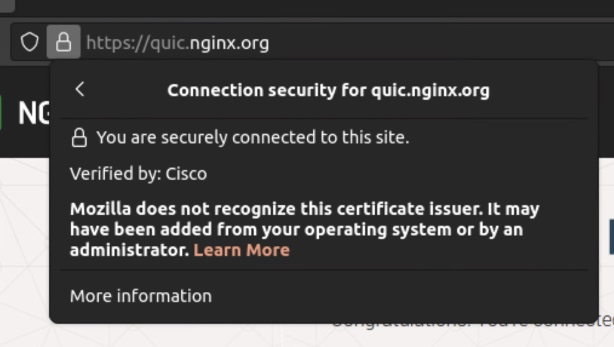
Verifying certificate issuer in Firefox.
While other sites don't generally present a badge to indicate the use of QUIC right on their page, it's possible to confirm the same details on any web request in the browser by leveraging the Web Developer tools. (In Firefox, this is opened with CTRL-SHIFT-I on Windows, or CMD-OPT-I on Mac.) Under the Network tab, it is confirmed that the requests loading over HTTP/3 were issued by our enterprise re-signing certificate.
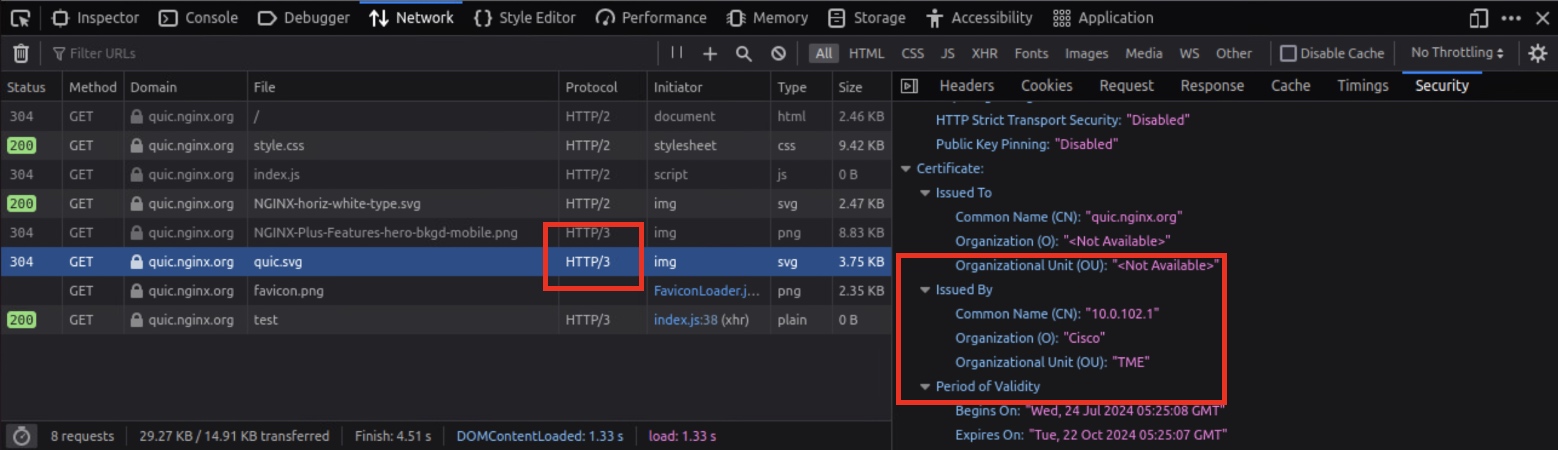
Confirming certificate issuer and protocol within Web Inspector panel.
Verifying QUIC Decryption in FMC
It is also possible to validate QUIC decryption by viewing logs in FMC. Ensure that the applicable Access Control Rules and Decryption Rules are set to log connections. Navigate to Analysis > Unified Events and apply a search filter to find the QUIC traffic (such as by applying a filter of 443 / udp to Destination Port). For traffic which is decrypted, the SSL Actual Action will display as Decrypt (Resign) or (for inbound connections) Decrypt-Known Key.
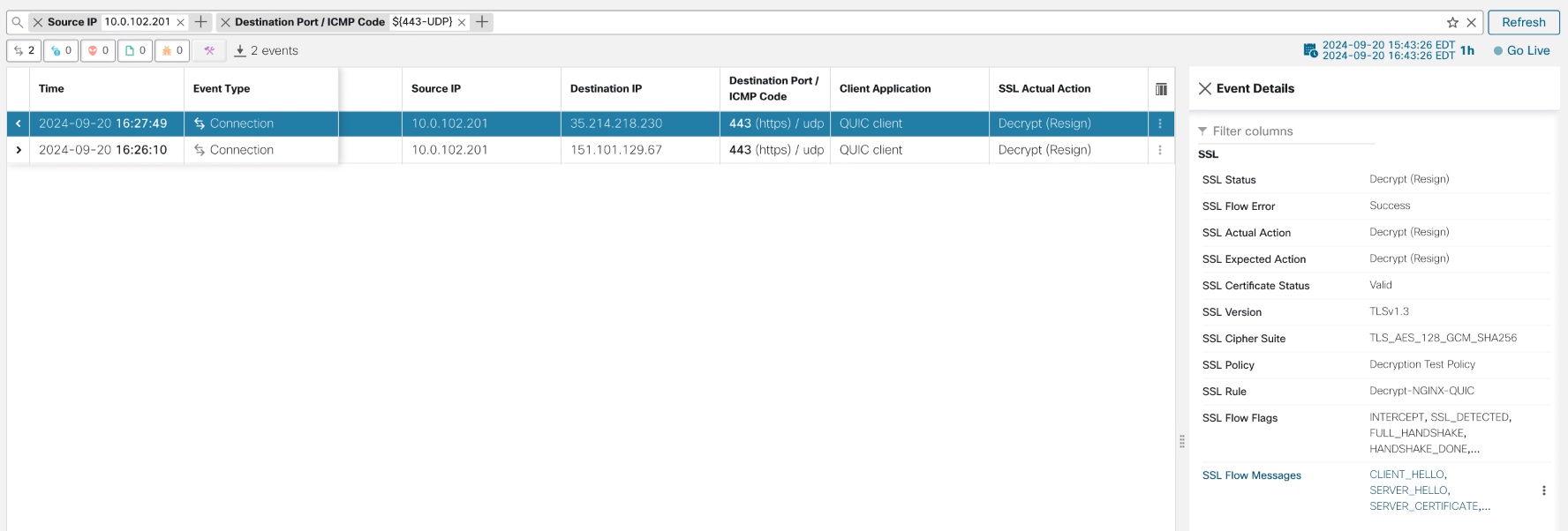
Updated 8 months ago
