Simplified Do Not Decrypt Configuration
Introduction
Creating a new decryption policy can often be a time-consuming and challenging process. To avoid network traffic disruptions and to comply with regulatory and privacy requirements, the decryption policies need to be revised frequently to bypass decryption for certain types of traffic.
Decryption Policy Wizard, introduced in release 7.3, eases the configuration for inbound and outbound TLS connections. With enhancements to this wizard in release 7.6, Do Not Decrypt rules are automatically added to outbound connections for the specified traffic.
The Do Not Decrypt Rules
The Do Not Decrypt options available in the New Decryption Policy wizard are as below:
- Bypass decryption for sensitive URL categories
- Bypass decryption for undecryptable distinguished names
- Bypass decryption for undecryptable applications
These options are available for outbound and inbound-outbound connections only. For inbound connections, they are greyed out at the wizard. However, you can enable them if needed after the policy is created.
Bypass Decryption for Sensitive URL Categories
This option is disabled by default for outbound and inbound-outbound connections. Sensitive URL categories indicate the URLs that are inspected in certain environments due to regulatory, compliance, or privacy reasons. It includes the below URL categories for bypass by default:
i. Finance
ii. Online Trading
iii. Health and Medicine
However, the above URL categories can be removed and other URL categories can be added to the list as required. This section requires a URL filtering license since it is based on URL category data.
Bypass Decryption for Undecryptable Distinguished Names
This option is enabled by default for outbound connections and inbound-outbound connections. It allows traffic that falls under Cisco's list of known undecryptable distinguished names to remain encrypted. Attempting to decrypt such traffic can cause decryption to fail. Updates to this list are provided in Secure Firewall releases. This list can only be viewed and cannot be changed by the user.
Bypass Decryption for Undecryptable Applications
This option is enabled by default for outbound connections and inbound-outbound connections. It allows traffic that falls under Cisco's list of known undecryptable applications to remain encrypted. Attempting to decrypt such traffic can cause decryption to fail due to Certificate Pinning, Client Certificate Authentication, etc. Updates to this list are provided in VDB releases. This list can only be viewed and cannot be changed by the user.
Configuration for Outbound Connection
- Navigate to Policies > Decryption. Click on Create Decryption Policy.
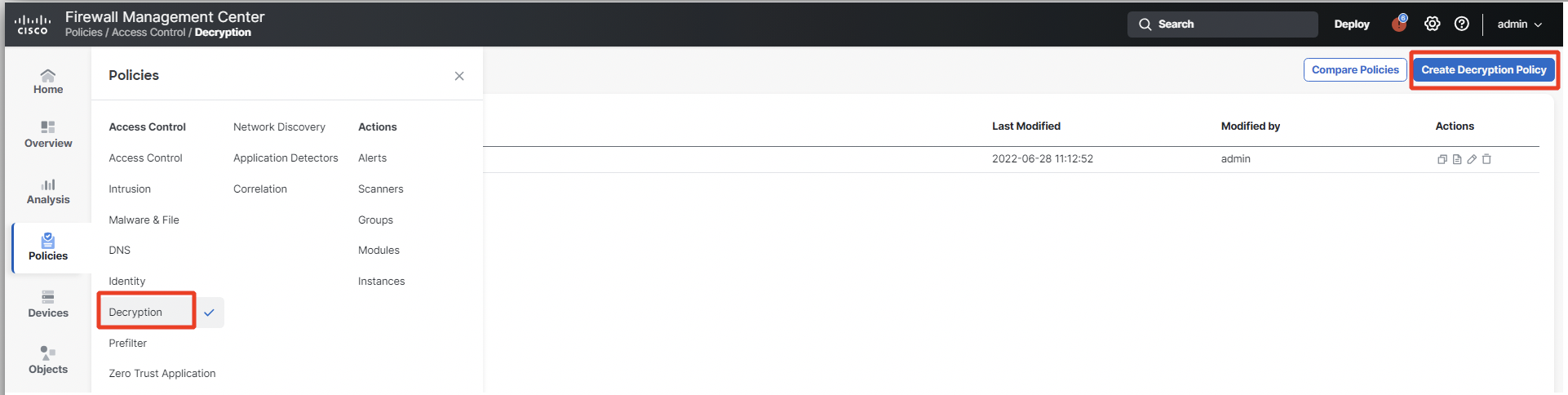
Decryption Policy
As per the note displayed in the wizard, if the requirement is to only perform application or URL discovery, TLS 1.3 Server Identity Discovery option can be used under Access Control Policy Advanced settings. This is a sidecar connection that opens TLS 1.2 connection to TLS 1.3 server and hence can identify the application or URL being accessed.
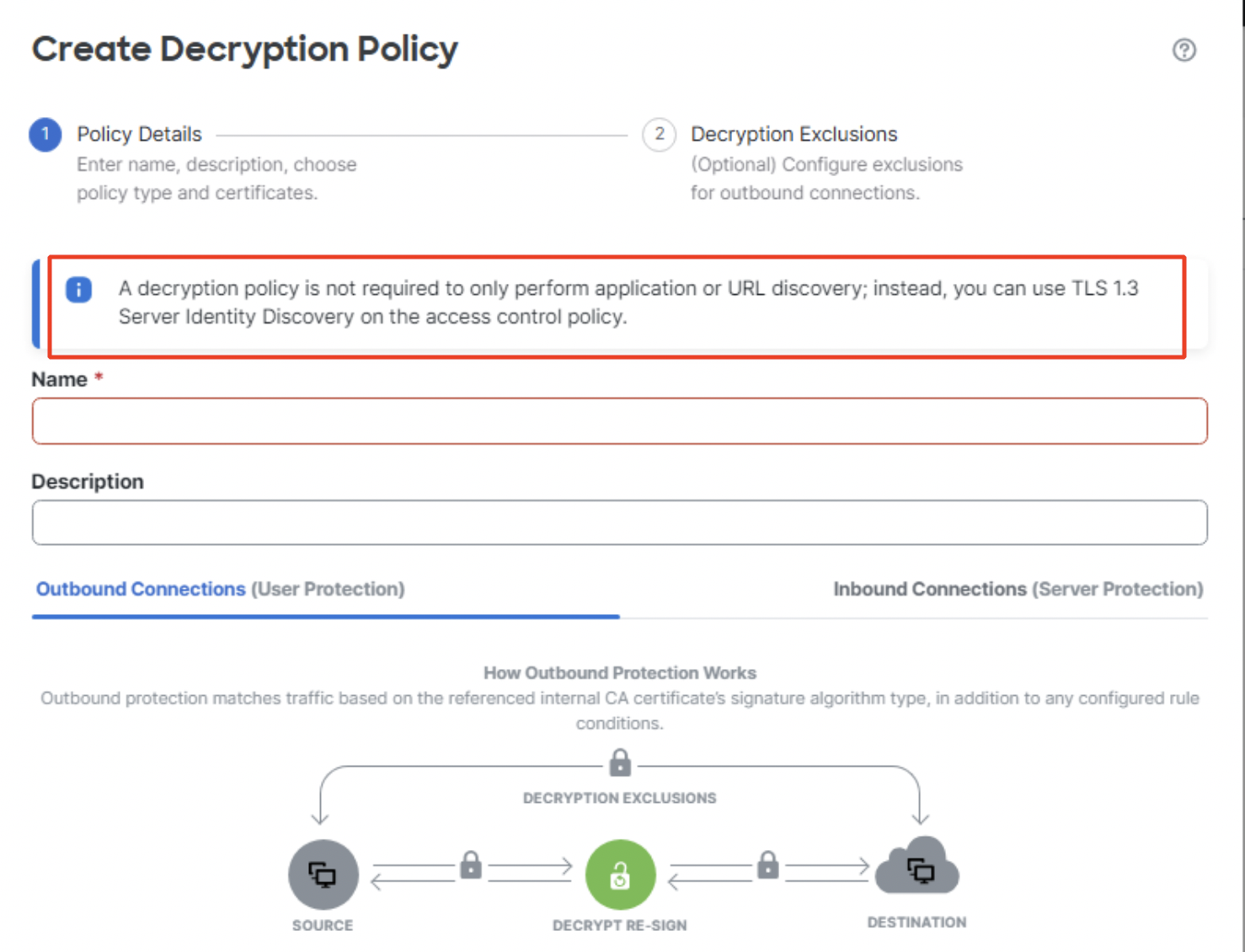
Decryption Policy Note
- Enter the Name and Description of the Decryption Policy. Select the Certificate Authority certificate to be used for outbound connection under Internal CA. You can also create a new Internal CA by clicking on + Create New.
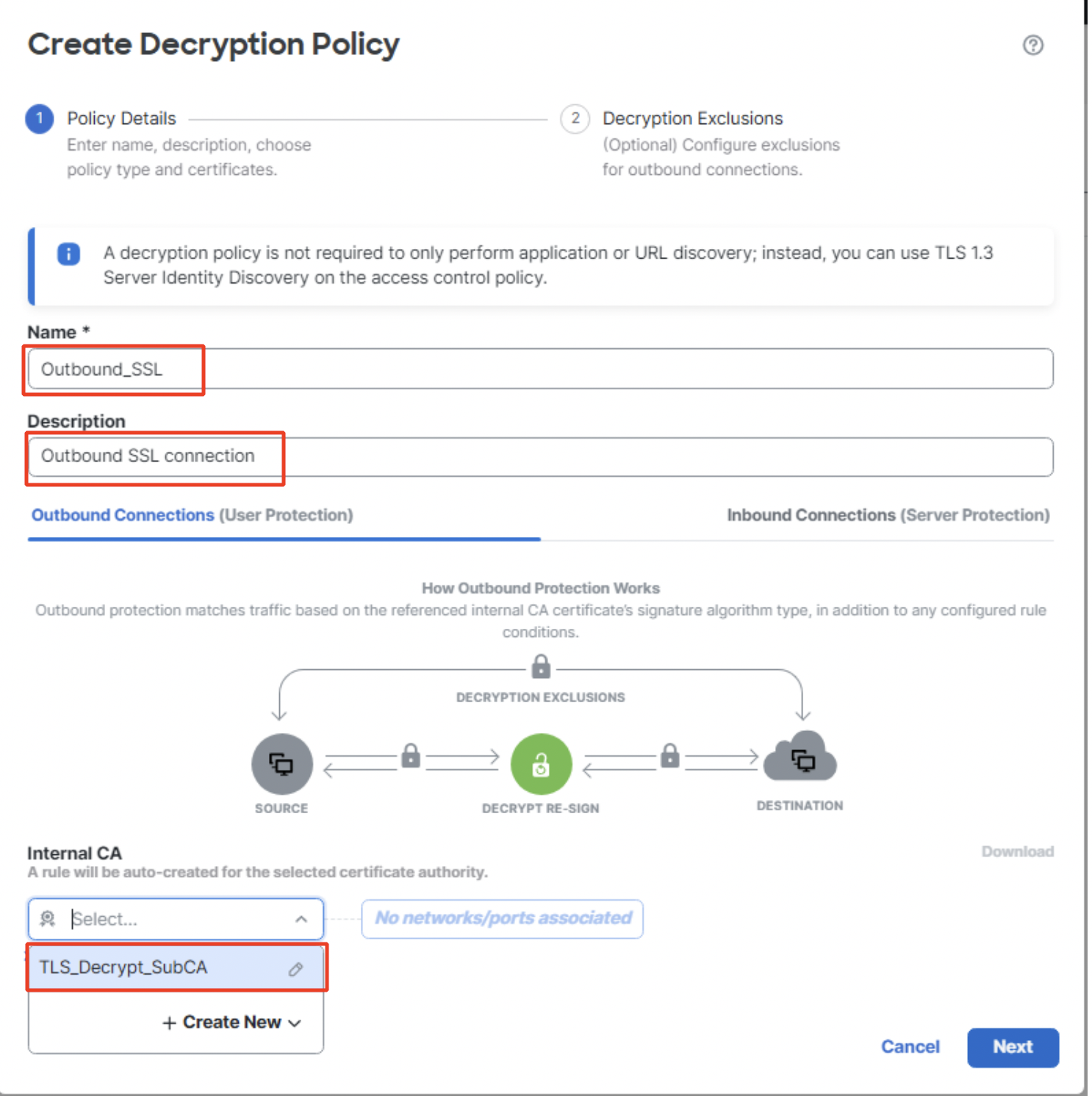
Create Decryption Policy for outbound connection
- Once you hover your mouse over No networks/ports associated, it changes to Click to assign networks and ports. Click on it to add source and/or destination networks as well as source and/or destination ports. Click on Apply.
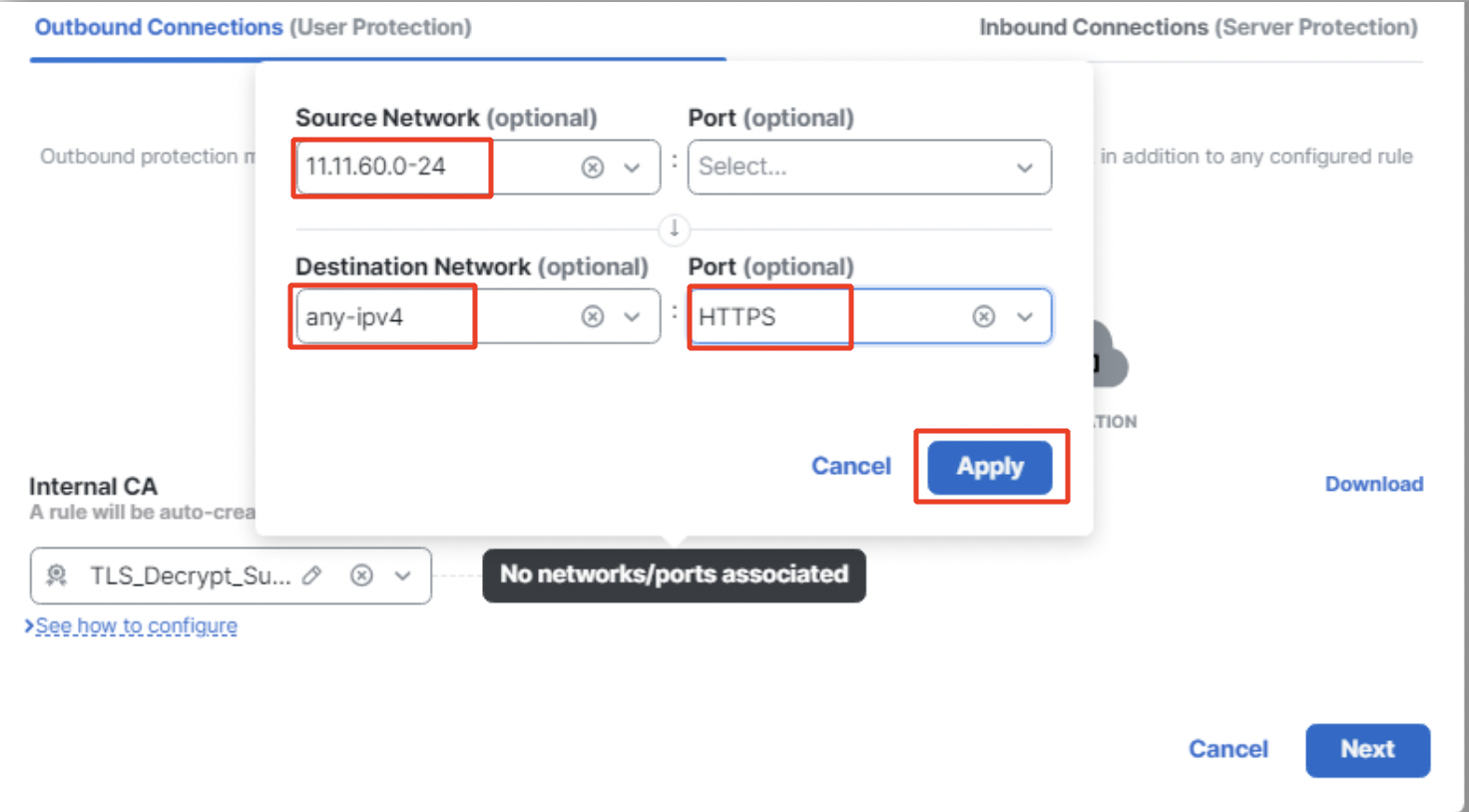
Network and Port configuration
The added networks and ports are shown below. Click on Next to continue to Decryption Exclusions.
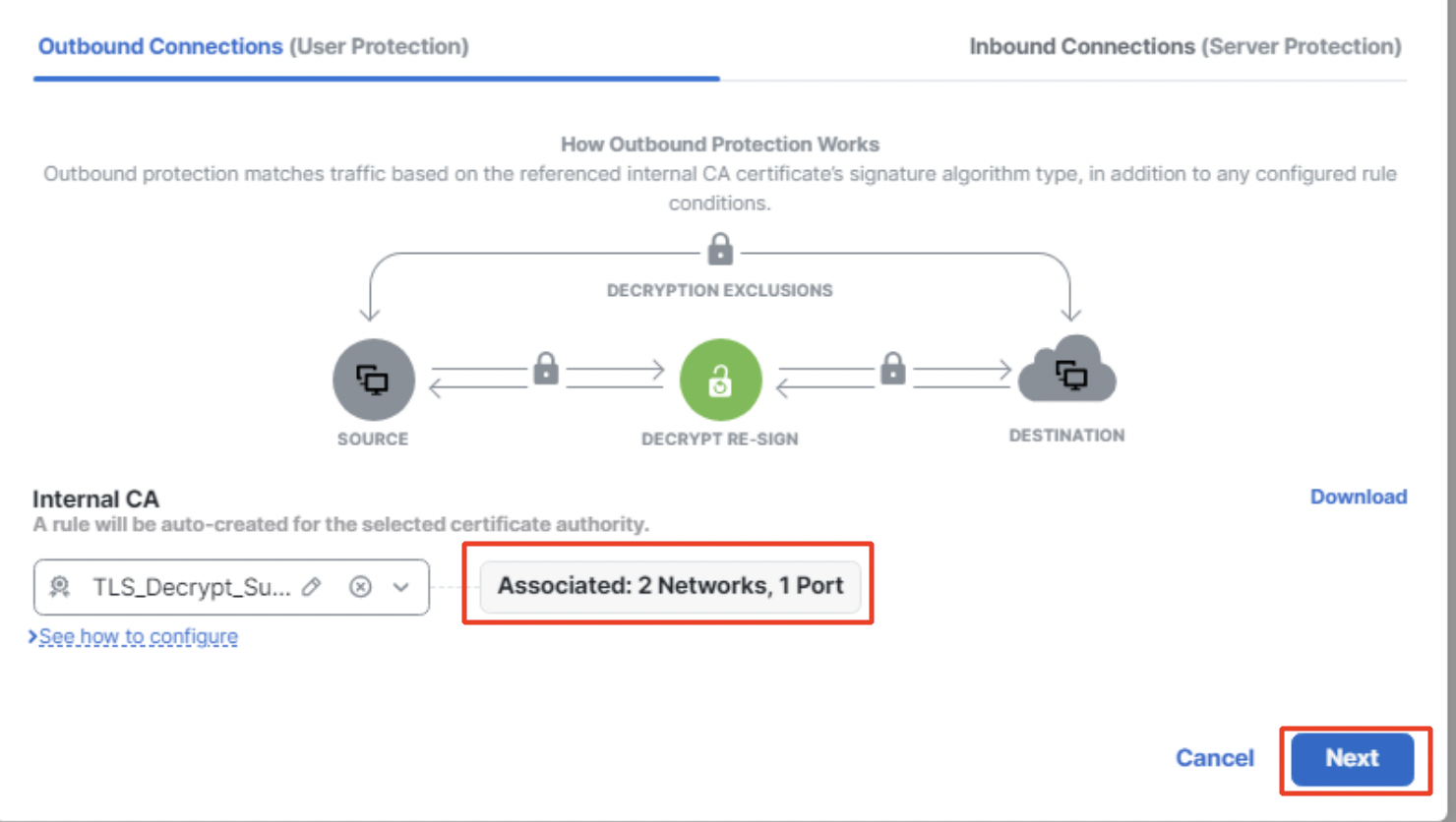
Create Decryption Policy
- The status of the three Do Not Decrypt rules is as below:
i. Bypass decryption for sensitive URL categories - disabled by default
ii. Bypass decryption for undecryptable distinguished names - enabled by default
iii. Bypass decryption for undecryptable applications - enabled by default
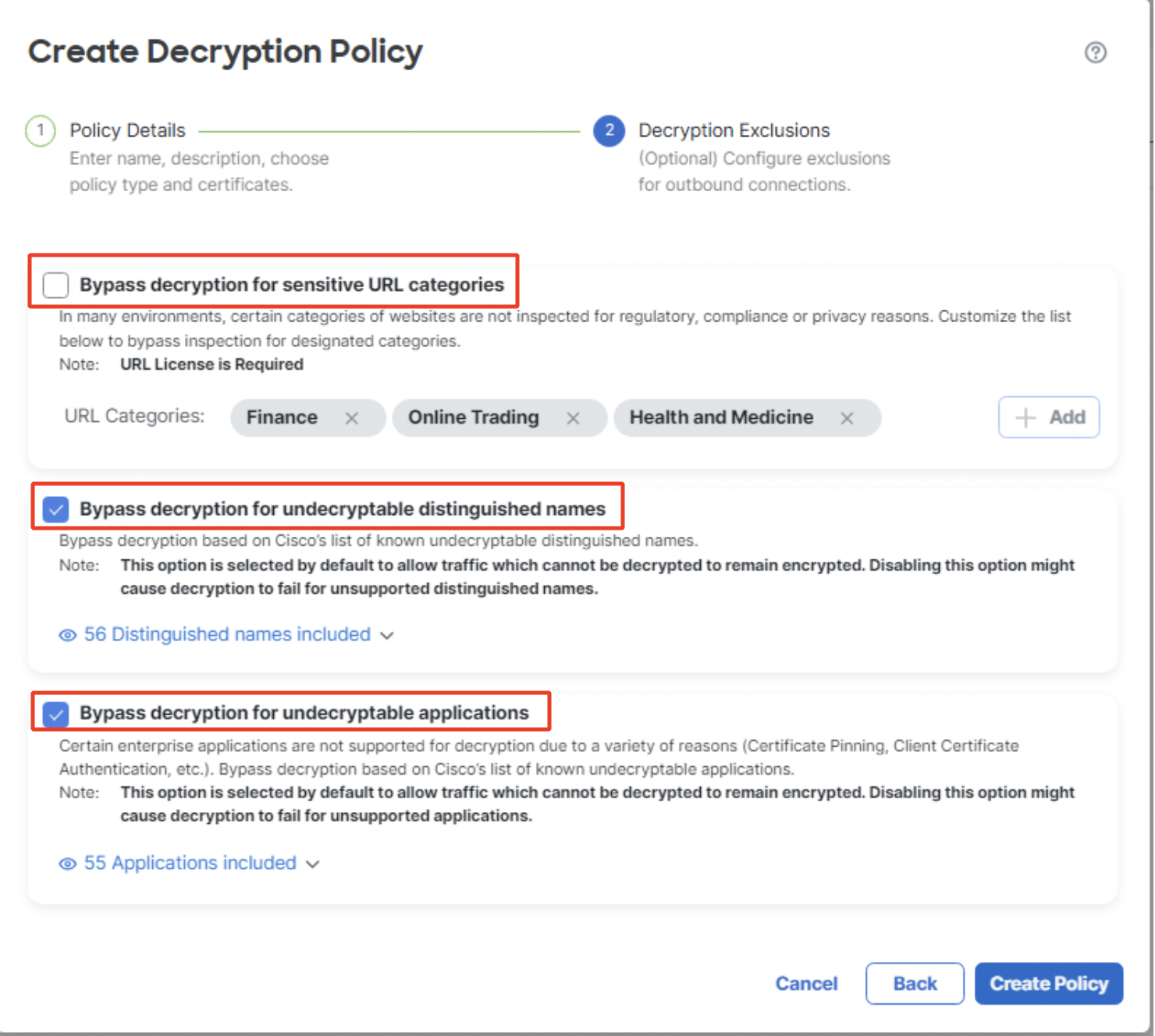
Decryption Exclusions for outbound connection
- Click on the check box against Bypass decryption for sensitive URL categories to enable it. Click on + Add to customize the default URL Categories list. URL categories can be added/removed as per requirement.
In the below example, Cryptocurrency has been added to the URL Categories list.
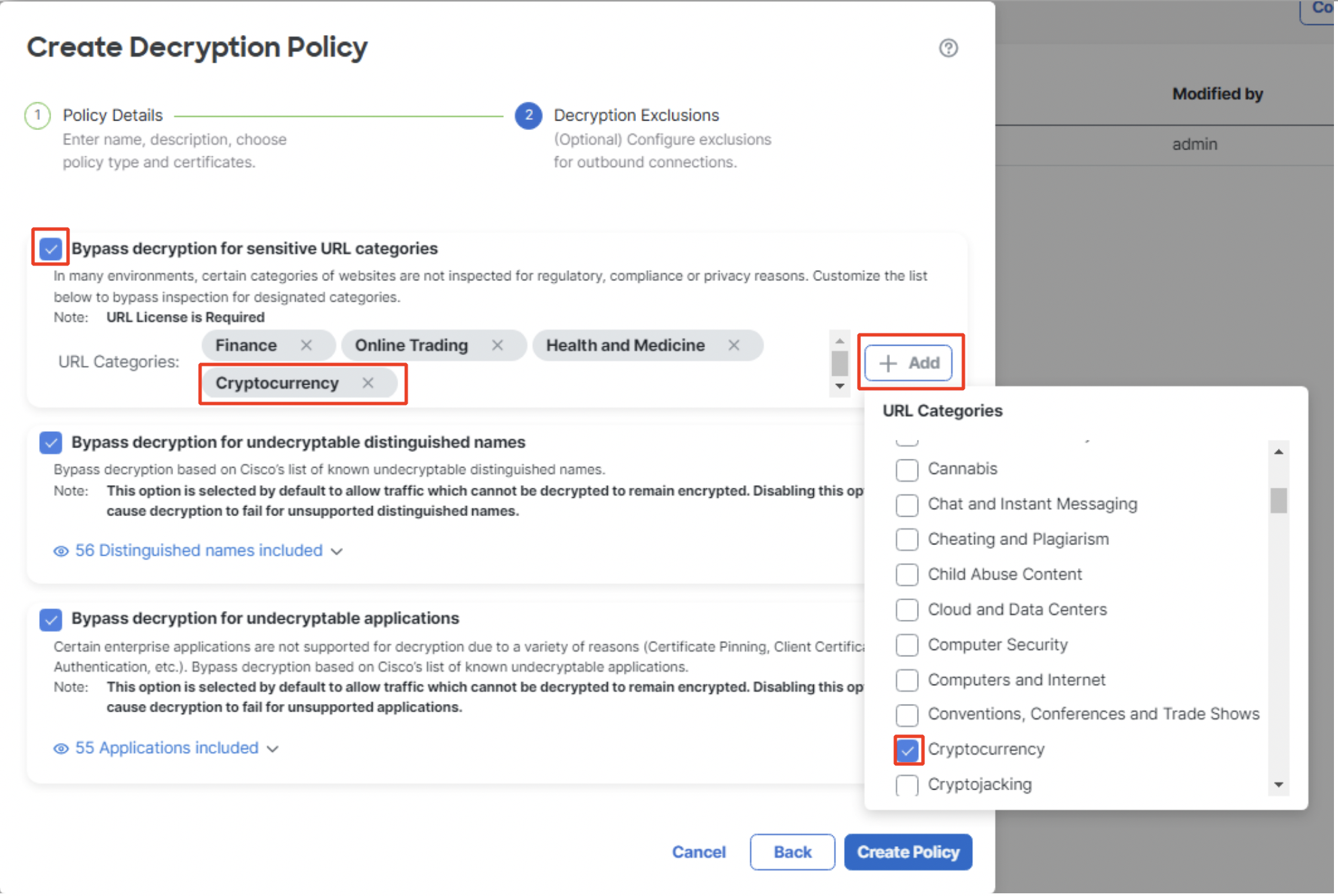
Customizing sensitive URL categories for bypass
- Click on Distinguished names included under Bypass decryption for undecryptable distinguished names to view Cisco's list of undecryptable distinguished names.
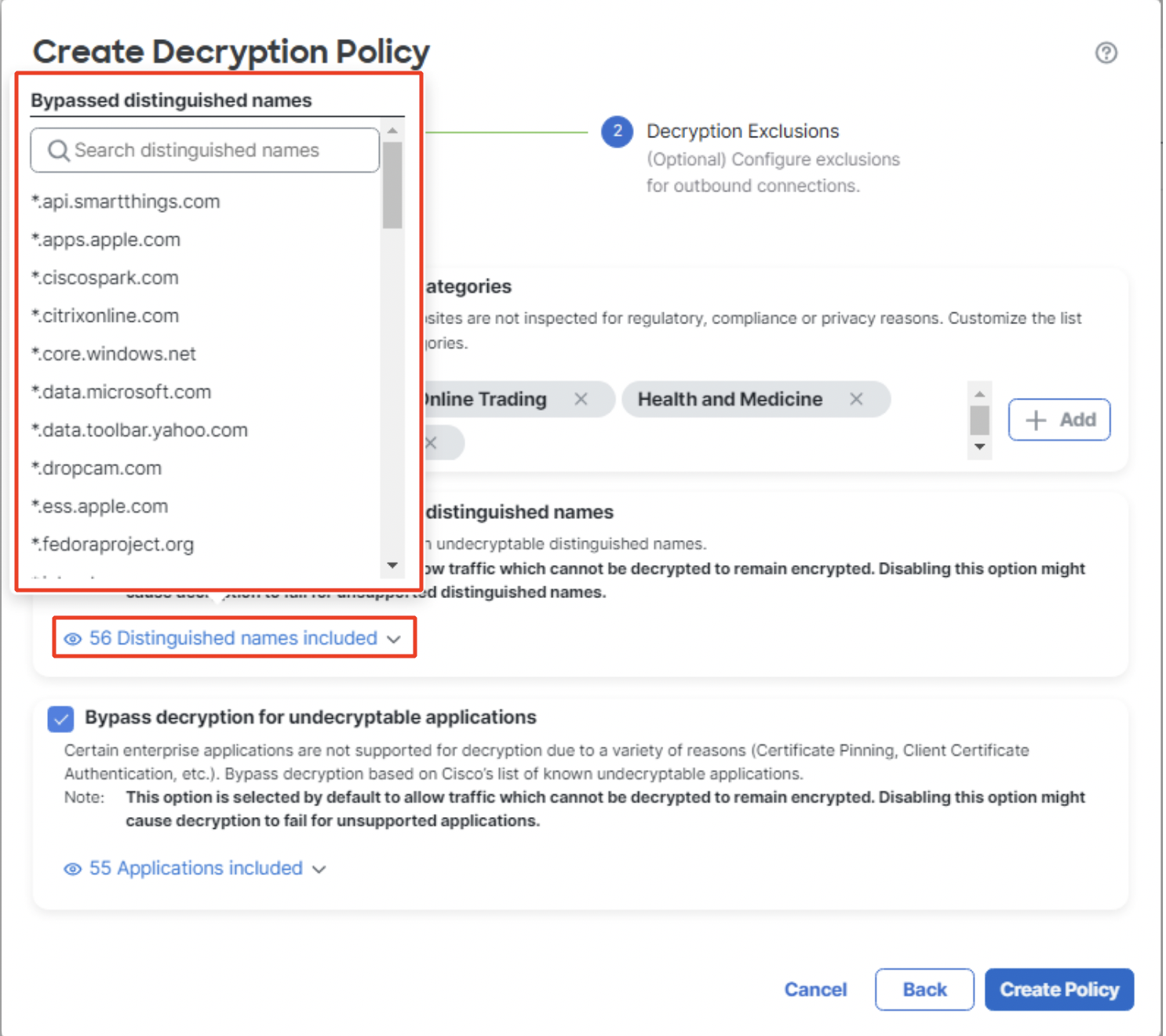
Bypassed distinguished names list
- Click on Applications included under Bypass decryption for undecryptable applications to view Cisco's list of undecryptable applications. Click on Create Policy.
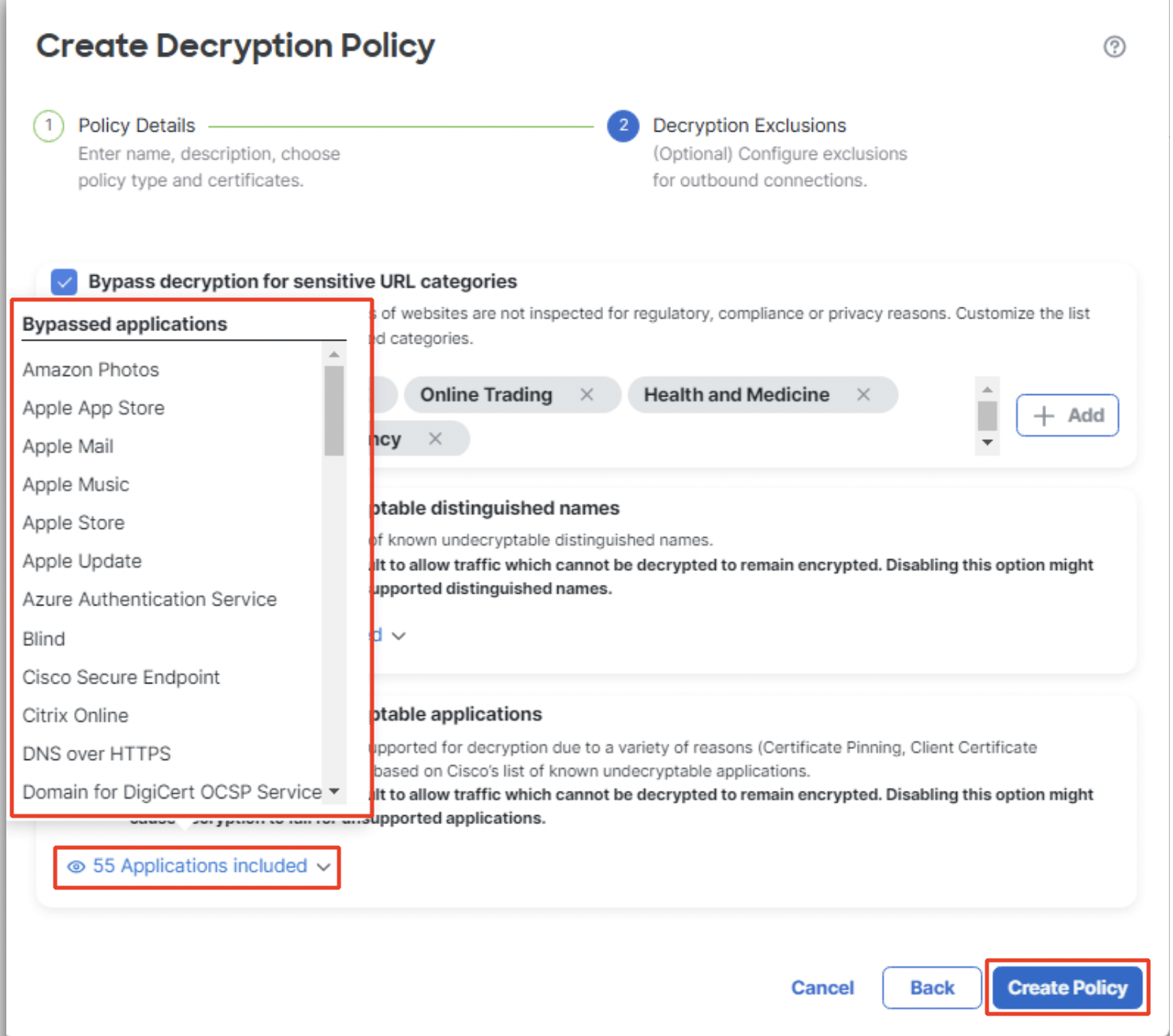
Bypassed applications list
- Four Do Not Decrypt Rules are added automatically in the following order:
i. Undecryptable Distinguished Names
ii. Sensitive URL categories
iii. Undecryptable Applications
iv. Decrypt-Resign
Note that all the automatically created rules are with the prefix Auto-Rule- and Decrypt-Resign rules are always added to the bottom of the other Do Not Decrypt rules.
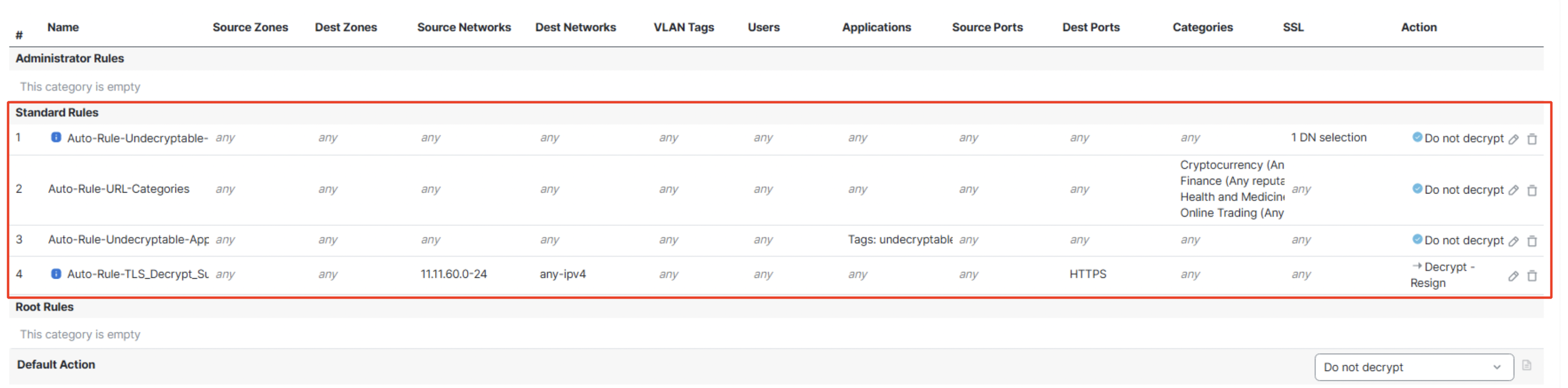
Auto-Rules created for outbound connection
Existing rules can be edited and new rules can be added to the Decryption Policy at this stage.
- This Decryption Policy can then be applied to an Access Control Policy by navigating to Policies > Access Control. Click on the Edit icon of the Access Control Policy to be configured. Click on Decryption and then on the drop-down to select the Decryption policy created.
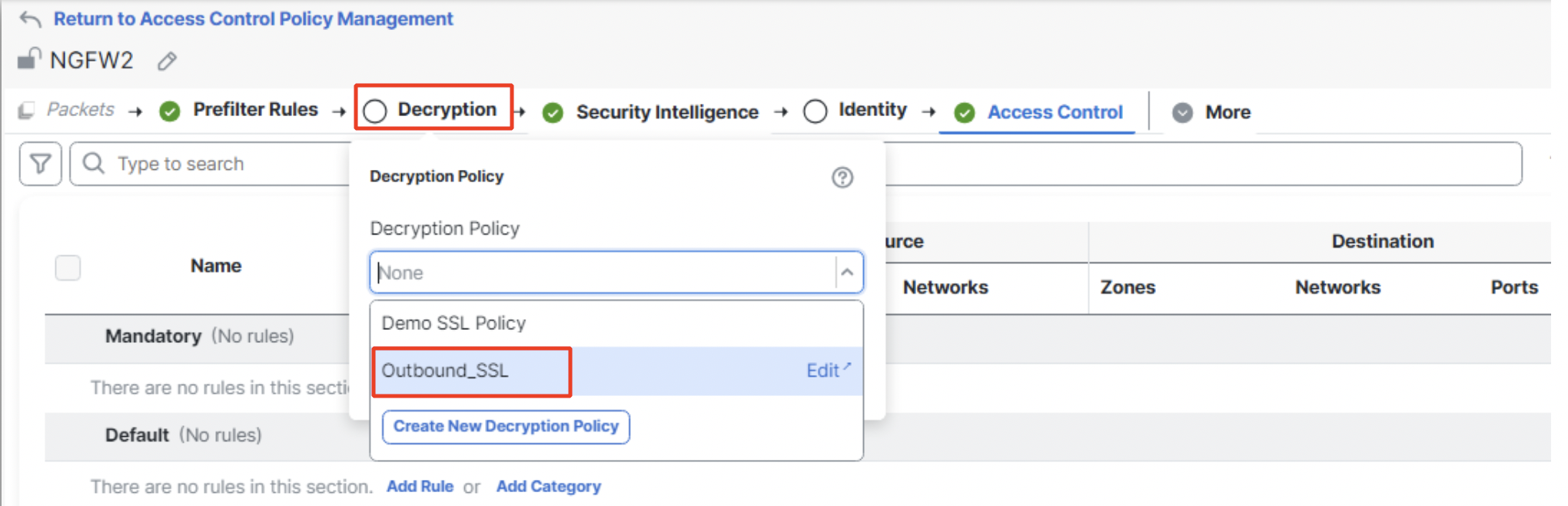
Mapping Decryption Policy to Access Control Policy
Click on Save to save the changes to the Access Control Policy and click on Deploy to deploy the changes to the firewall.
Configuration for Inbound Connection
- Navigate to Policies > Decryption. Click on Create Decryption Policy.
- Type in the Name and Description of the policy. Click on Inbound Connections (Server Protection).
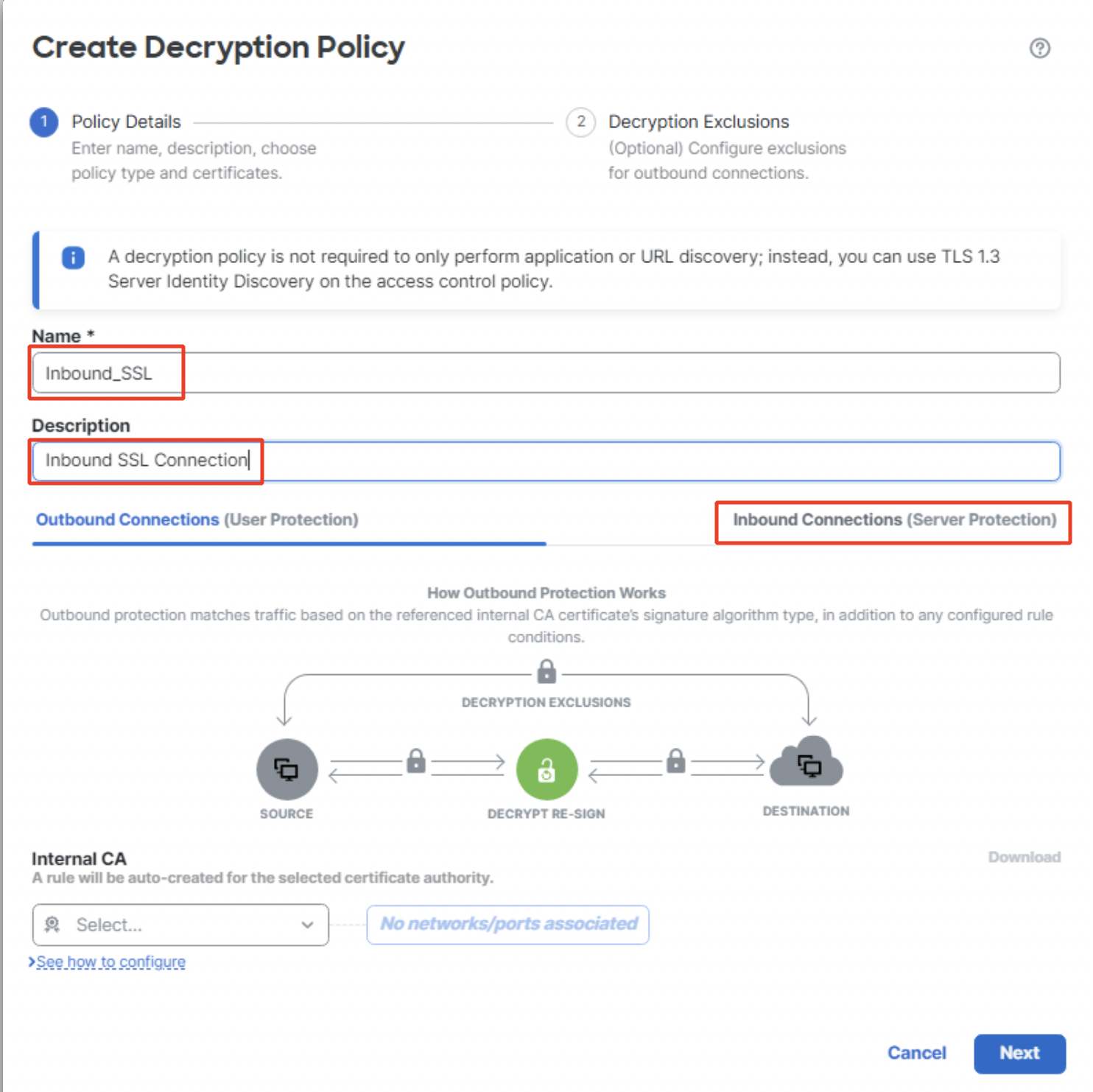
Create Decryption Policy for inbound connection
- Click on the + sign under Internal Certificates to add the Server certificate. Click on OK. New Internal Certificates can be uploaded by clicking on Upload.
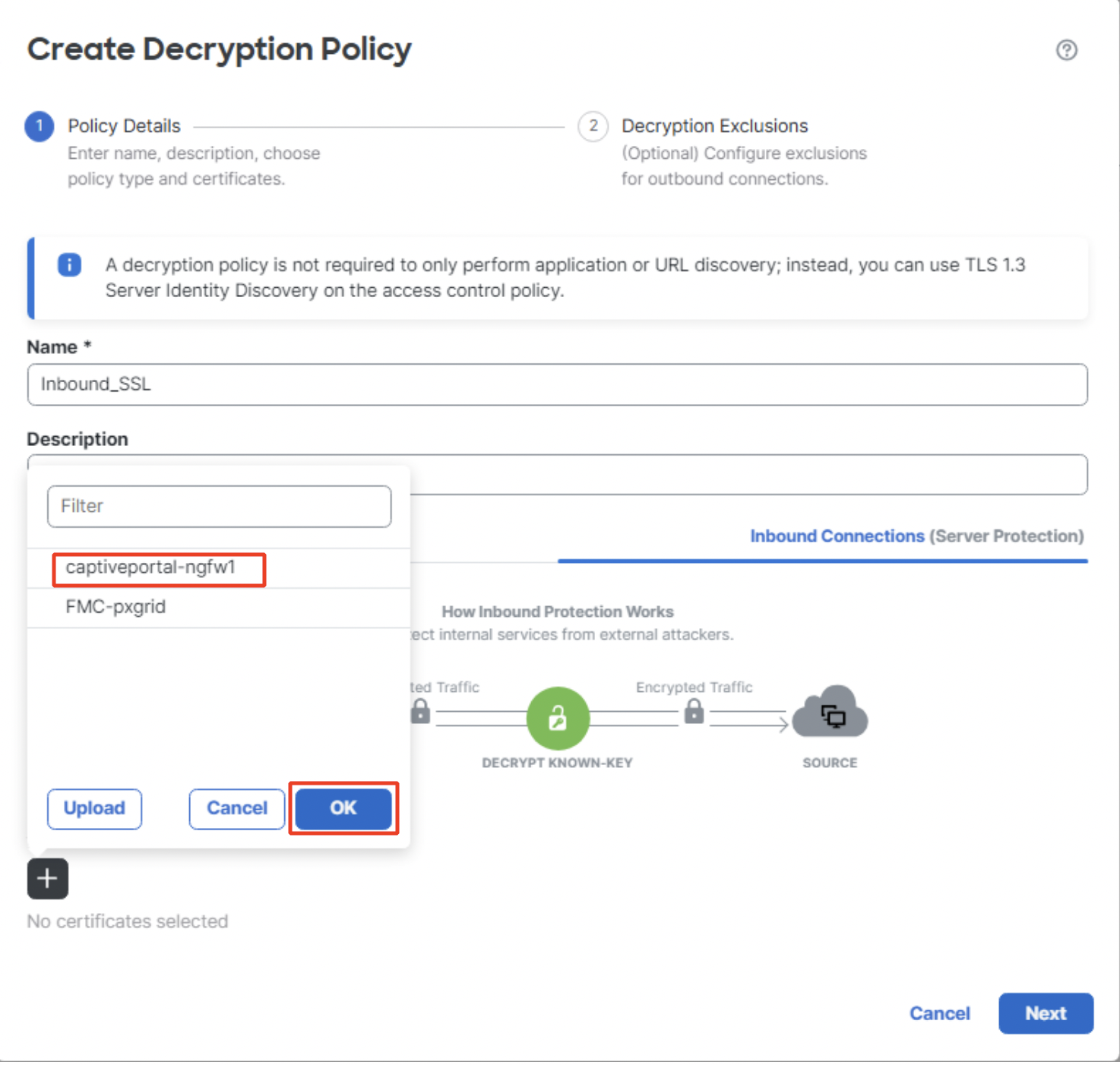
Adding Internal certificate
- Click on No networks/ports associated to add source and destination networks and ports. Click on + to add additional internal certificates. Click on Next.
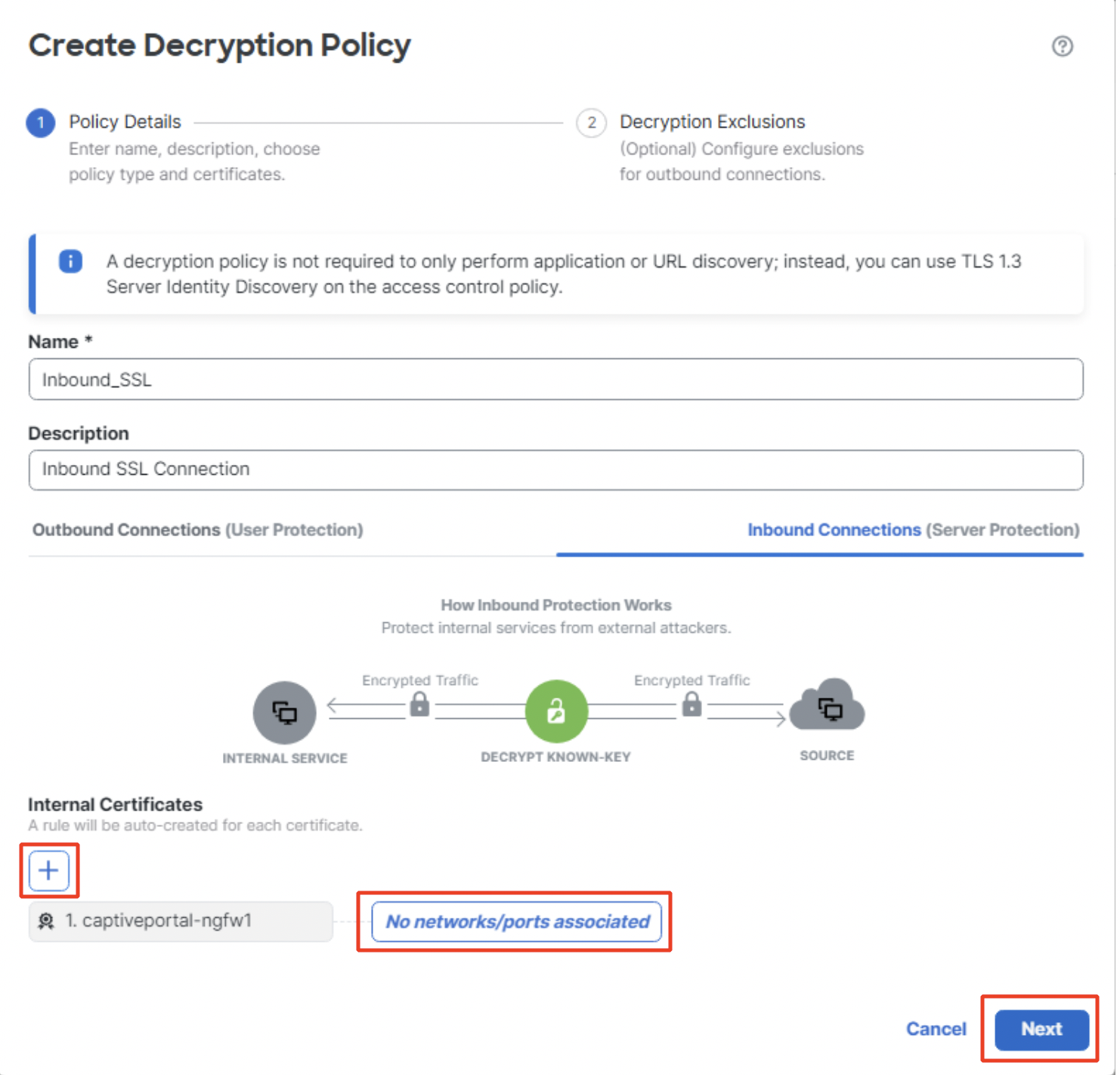
Adding networks/ports and additional Internal Certificates
- All the Do Not Decrypt options are greyed out since the decryption policy is inbound-only. Click on Create Policy to proceed.
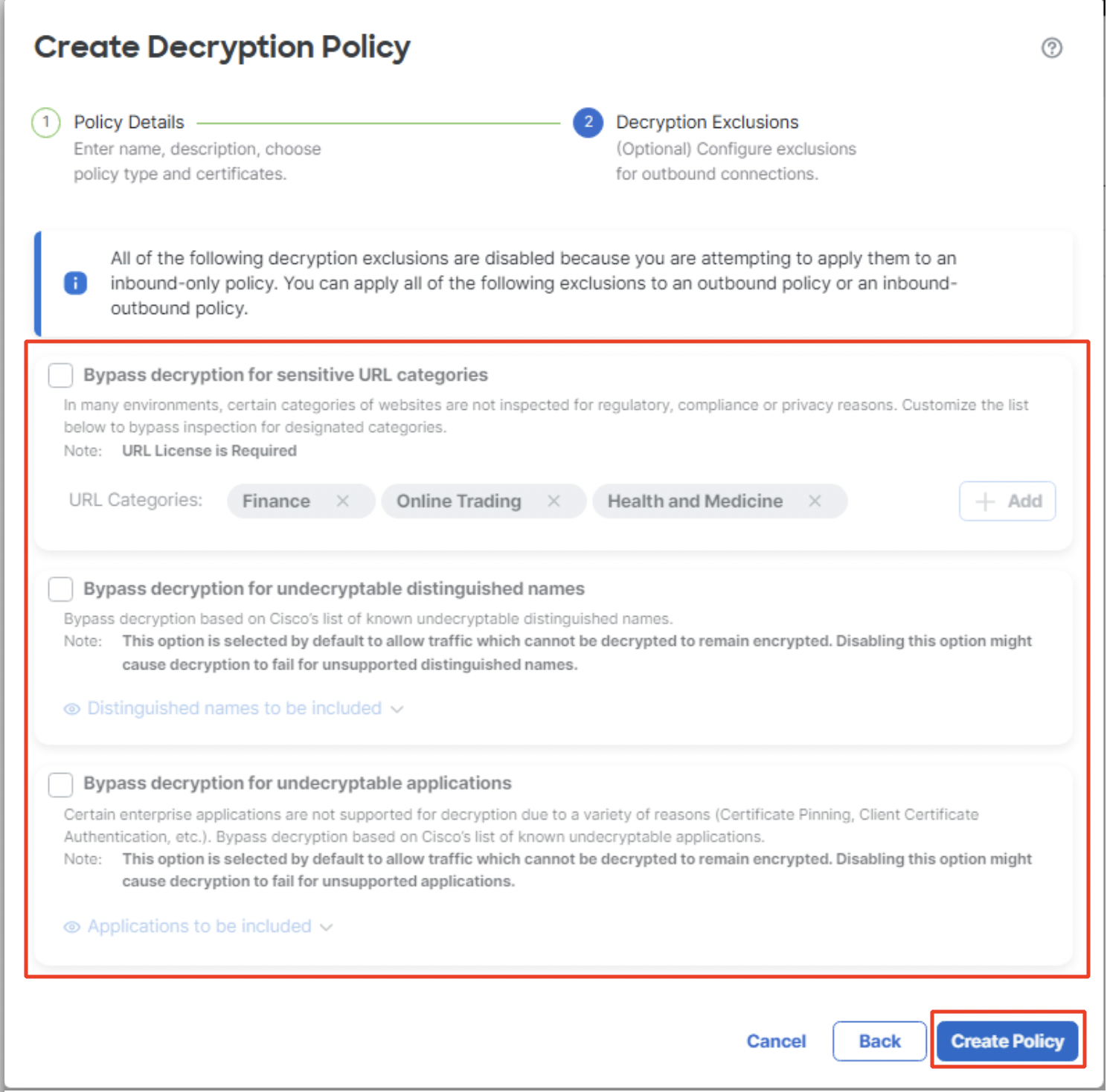
Decryption Exclusions for inbound connection
- All the rules get added to the decryption policy with the Do Not Decrypt rules in disabled state. Note that the Decrypt-Known Key rule gets added before the Do Not Decrypt rules. The disabled rules can be enabled if required by clicking on the edit icon of the rule and then clicking on Enable.
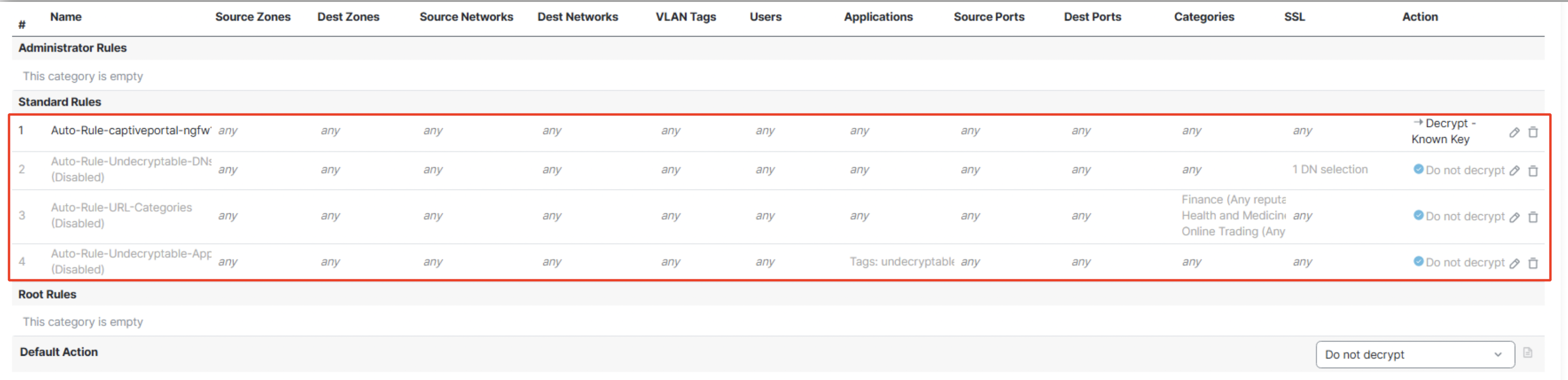
Auto-Rules for inbound connection
Summary
With the new Decryption Policy wizard, outbound connections can easily be configured with decryption exclusions to bypass decryption for sensitive URL categories and undecryptable traffic with Cisco-provided lists.
Updated 8 months ago
