Cloud-delivered Firewall Management Center
Introduction to Cisco's latest offering for managing Cisco Secure Firewall.
Introduction
The cloud-delivered Firewall Management Center(cdFMC) brings the management capabilities of the Firewall Management Center (FMC) within Cisco Defense Orchestrator (CDO). Adoption is made easier with a minimal learning curve, as we have retained the FMC's policy management workflows and user experience. Also, the built-in migration wizard enables easy migration from privately managed FMCs (Hardware appliance, private or public cloud) to the cloud-delivered FMC.
Cloud-delivered FMC is available through Cisco Defense Orchestrator, a SaaS-delivered offering, so Cisco manages the upkeep of the service, eliminating the OpEx associated with maintaining a virtual or hardware management appliance.
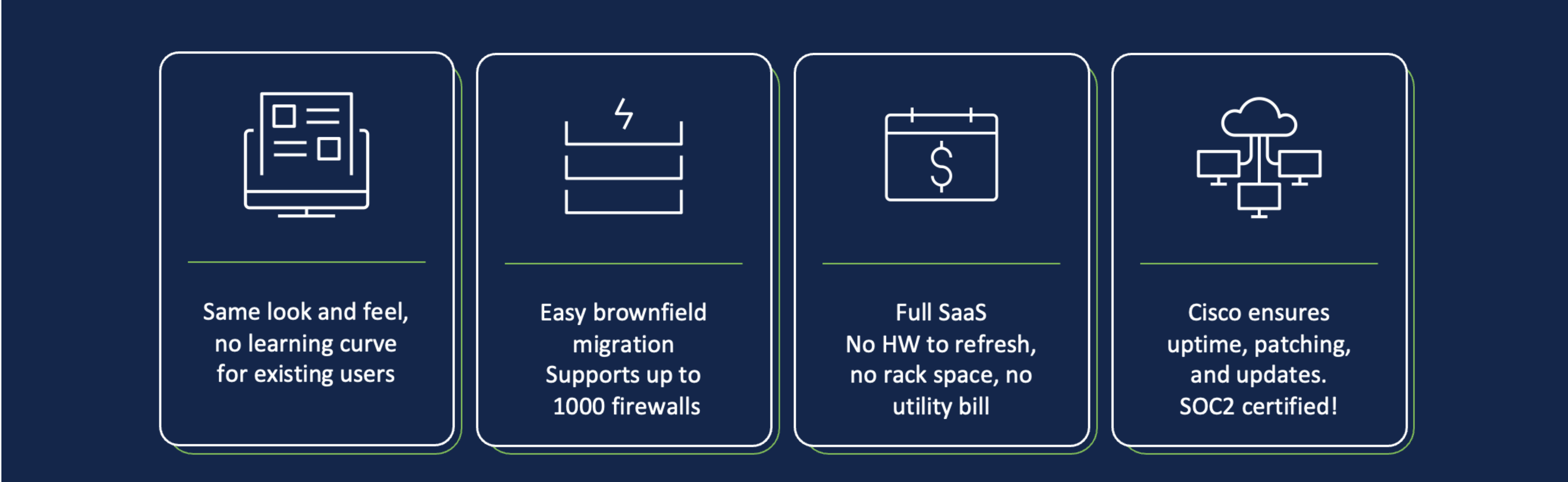
Benefits of cloud-delivered Firewall Management Center
Like its privately managed counterpart, the cloud-delivered FMC can manage all Secure Firewall (Hardware, Private Cloud, Public Cloud, Container, as-a-Service) form factors.
Key Benefits
Familiar User Experience
The cloud-delivered FMC reuses most of the policy configuration components to minimize the learning curve and provide the same user experience for customers looking to adopt this solution. The examples below show the familiar Device Health Monitoring dashboard, where you can find the overall health statistics of your deployment, and the Policy Editor from the cdFMC.
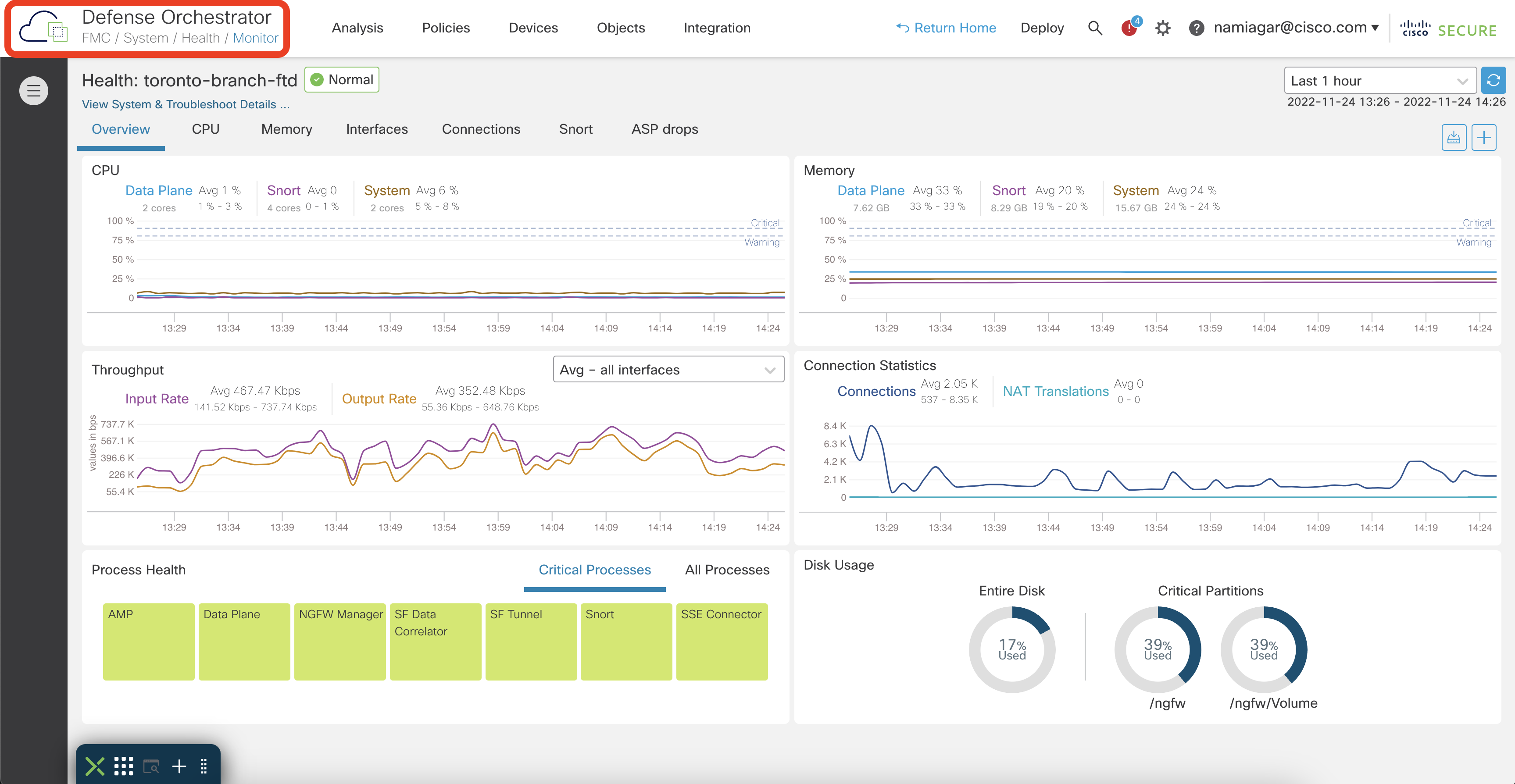
Device Health Monitoring Dashboard in cdFMC
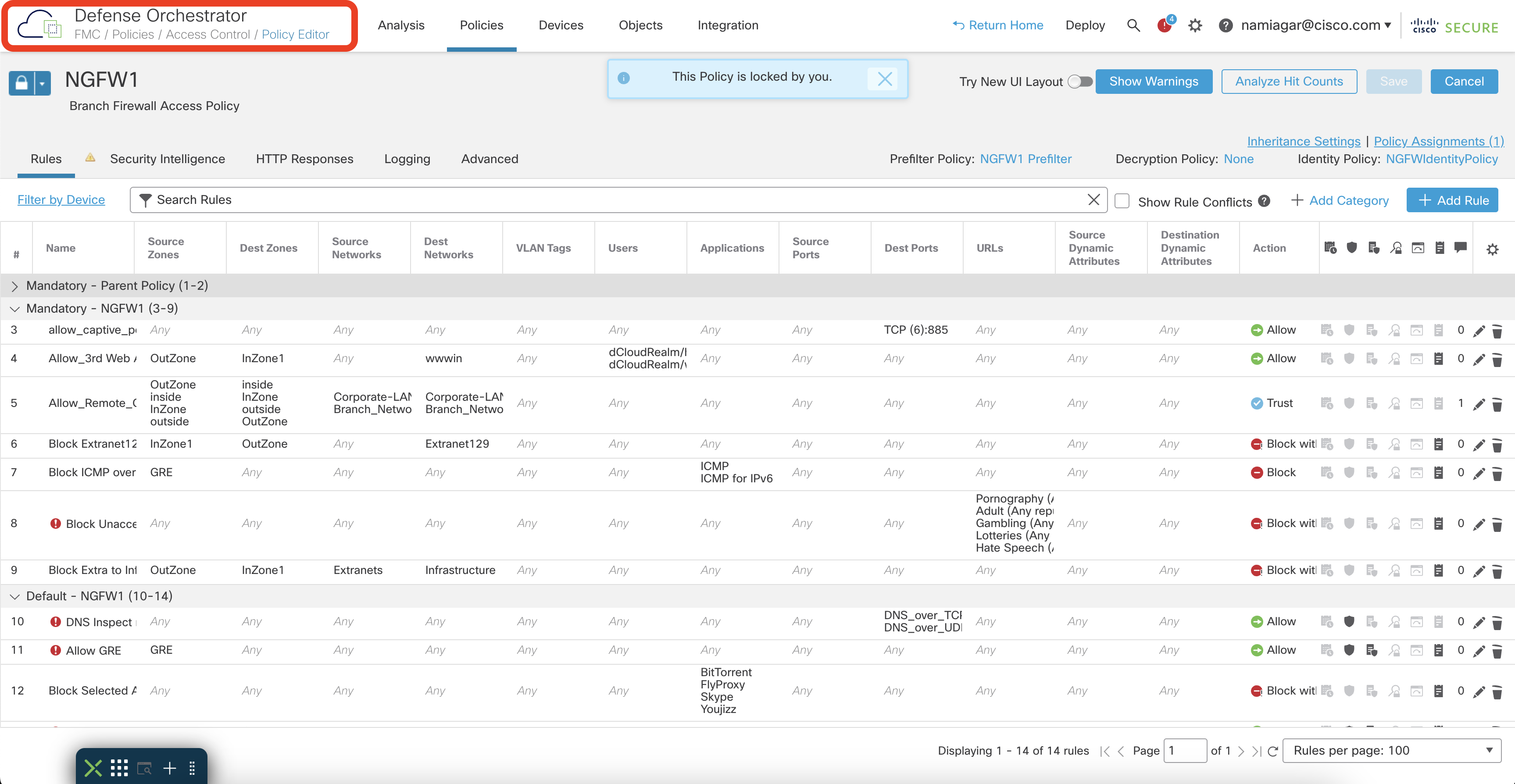
Access Policy Editor in cdFMC
Easy Onboarding and Migration Experience
The Device Onboarding and Migration workflows are driven through the Cisco Defense Orchestrator Home Page. A quick launch widget allows users to launch routine tasks with a single click.
Quick Launch Widget on Cisco Defense Orchestrator (CDO) Home Page
The cloud-delivered FMC supports two onboarding methods:
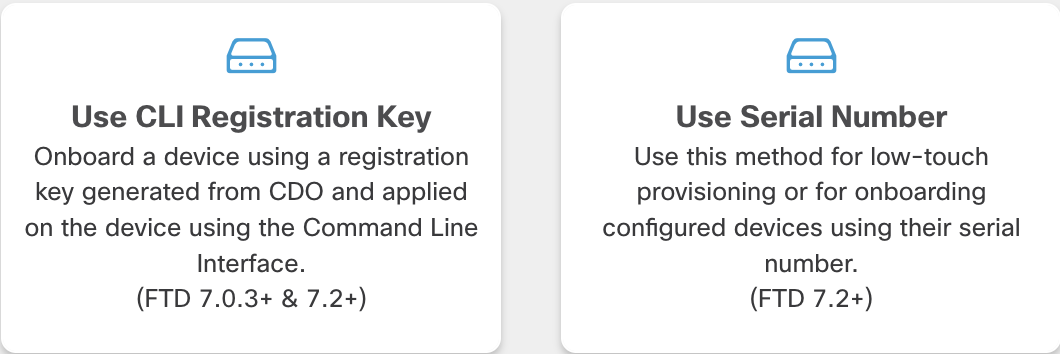
Onboarding Methods
Registration Key-Based Onboarding
The administrator generates a registration key from the Device Onboarding Wizard, which is then entered into the firewall using the CLI (similar to the FMC onboarding workflow).
Low Touch Provisioning
The administrator claims the Firewall by entering the firewall S/N into the Onboarding Wizard. Upon powering up and connecting to the Internet, the Firewall is automatically onboarded. This provides a low-effort onboarding experience, which is especially useful for provisioning remote branches.
Migration from Privately Managed FMC
The migration tool facilitates cloud adoption further and provides a simple process to move the management of an existing Firewall deployment to the cloud. You can enable one-click SecureX integration on the Smart Licensed FMC. The tool pulls the list of eligible firewalls and allows the migration of one or more firewalls, along with all the associated configurations. More details are covered on the Migration Page.
Migration from Other Firewalls
The Secure Firewall Migration Tool supports migration from ASA and 3rd party firewalls to Cisco Secure Firewall. Recently expanded to support migrations to cloud-delivered FMC as well. Now, the migration tool can migrate the firewall configuration to all deployments of the Firewall Management Center (on-premises, virtual, or cloud-delivered).
Simpler Branch Management
The introduction of the cloud-delivered FMC and recent firewall features makes branch provisioning very simple, enabling some key use cases around branch connectivity.
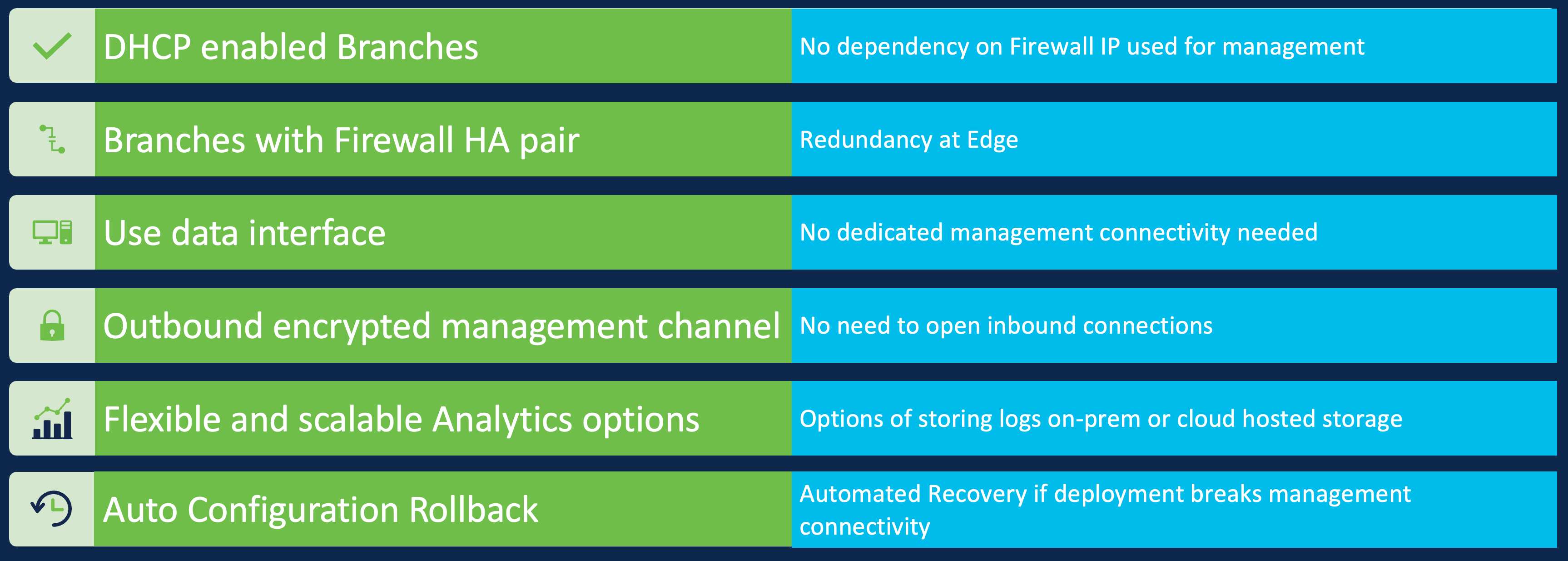
Easy Branch Management
Higher Scale of operations
The cloud-delivered FMC can manage up to 1000 firewalls per tenant, which is more than the current FMC appliances can support. Also, to make the FMC components cloud compatible, we have added a lot of optimizations behind the scenes, allowing for a faster and lighter experience.
With cloud-hosted logging, you can achieve retention times of years along with a higher event rate. Cloud-hosted logging supports a maximum rate of 100,000 events per second with flexible logging packages depending on consumption requirements. The administrator can view their logging quota usage and request more storage if required.
Because Cisco Defense Orchestrator is multi-tenant, the cloud-delivered FMC supports multi-tenancy where each tenant is completely isolated from the other, allowing for MSP deployments.
Easy Maintenance and Recovery
As mentioned early on, Cisco is responsible for ensuring uptime, updates and cloud-delivered FMC maintenance. Daily configuration snapshots are backed up. The operations team keeps two weeks' worth of the latest snapshots, allowing for a quick recovery if necessary using any of these snapshots. This allows for faster recovery and the maximum data loss of up to 24 hours.
Support Multi-Cloud Scalable Adoption
The cloud-delivered FMC offers flexible deployment options depending on the use case requirements. For example, customers can manage the firewall from the cloud but retain the events with the sensitive information on-premises, or cloud-savvy customers can move the eventing and logging to the cloud with the unified event viewer in the cloud, offering both real-time and historical views.
- Complete Cloud Adoption - configuration management, log storage and analytics are cloud-delivered. It can be further enhanced by behavioural analysis from Secure Cloud Analytics (formerly known as Stealthwatch Cloud). It can also send behavioural analysis alerts to an external SIEM.
- Logging to an on-premises FMC - configuration management is cloud-delivered, but the log storage and analytics are available through an on-premises FMC. It can be further enhanced by integrating with Cisco Secure Analytics and Logging on-premises, which provides additional behavioural analysis powered by Secure Network Analytics (formerly known as Stealthwatch Enterprise) or used to forward the logs to an external SIEM using eStreamer.
- External SIEM - You have the flexibility of logging into an external SIEM using any of the above options or directly sending syslogs from the Firewall.
Note
Using the on-premises FMC for logging and analytics only requires running version 7.2 or later.
The Cisco Secure Firewall inherently supports granularity when choosing one or any of the above combinations for logging by providing the flexibility of choosing event types and their destination.
E.g., Connection Events can be streamed to the cloud, but the IPS and File and Malware events can be retained on-premises.
Dynamic Attributes Connector
Secure Firewall supports Dynamic Policies, allowing policy modification in near real-time, without any administrative action. 3rd Party and Cisco Secure products like ISE, APIC, Secure Workload, and SecureX can integrate with the FMC and push policy updates in near real-time.
This is extremely critical for applications and workloads deployed in dynamic cloud environments. Cisco Secure Dynamic Attributes Connector aggregates attributes from the private, public cloud, and 3rd party feeds like O365 and uses them to update policies using the FMC APIs. It was introduced as a custom docker package, which could be installed on a dedicated VM. However, we have also made it available as a built-in component within CDO, eliminating the need to install and maintain a separate VM.
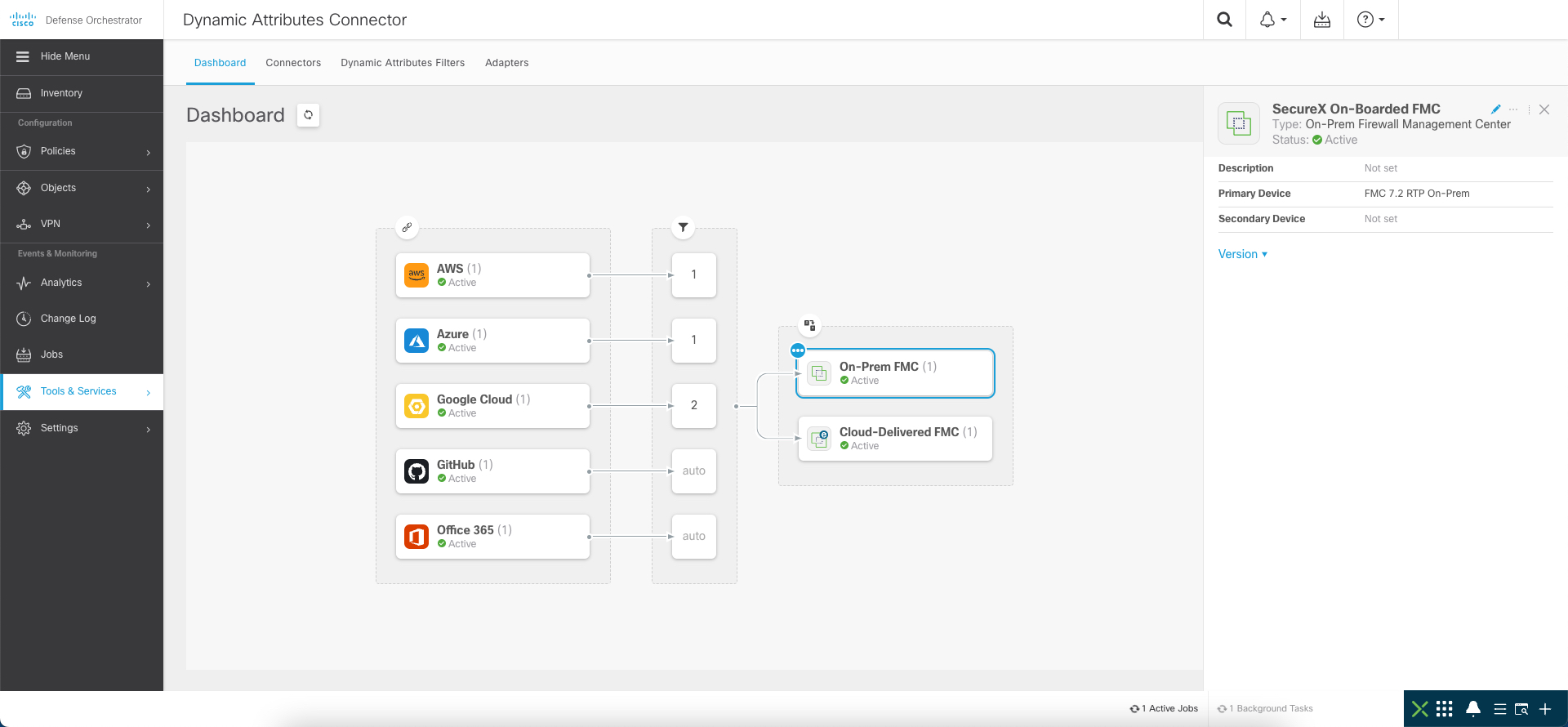
Cisco Secure Dynamic Attributes Connector in CDO
More details about the Cisco Secure Dynamic Attributes Connector are covered in depth here.
Licensing and Ordering Info
The cloud-delivered FMC is part of the Cisco Defense Orchestrator and follows the CDO licensing model. The licensing has multiple options, depending on the features and deployment use case.
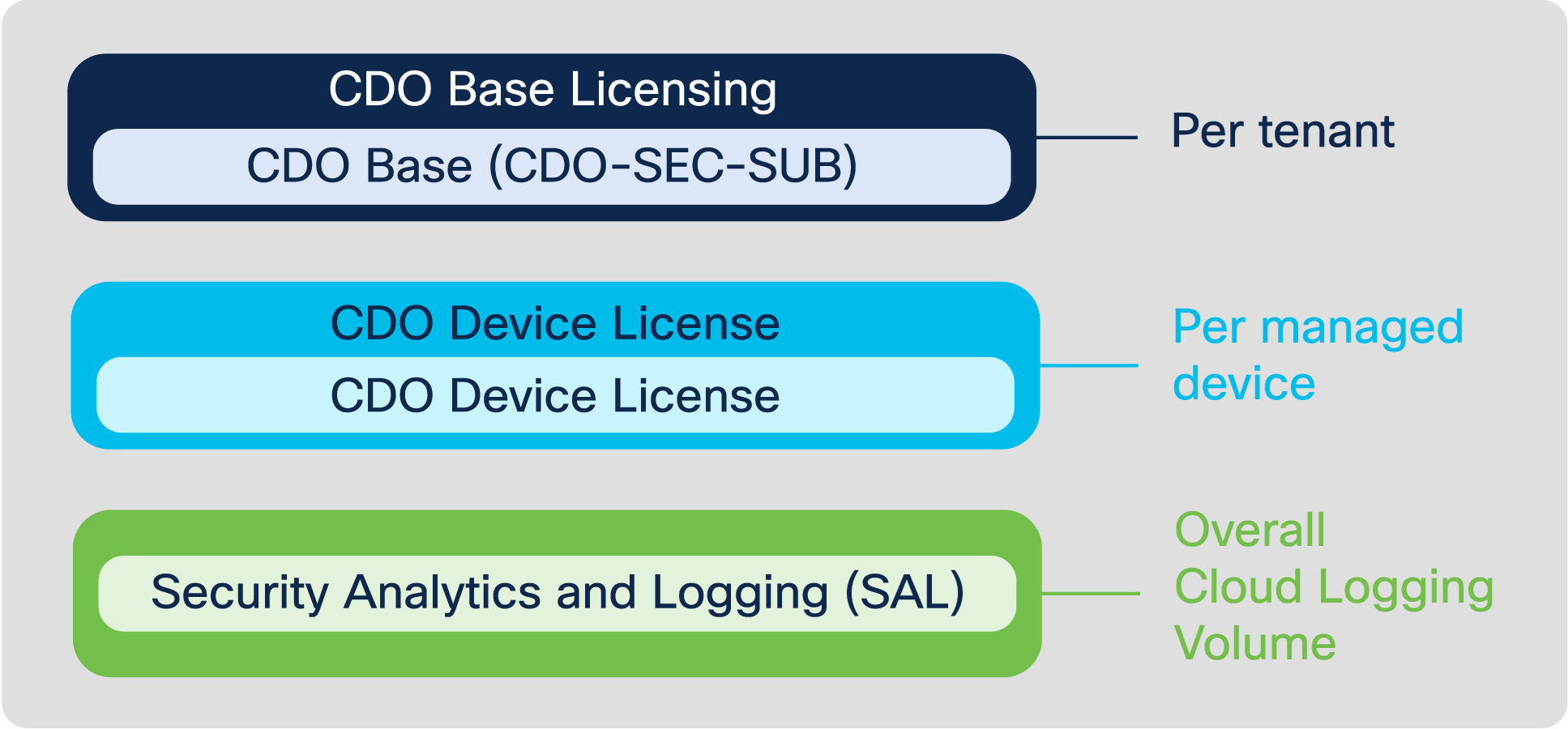
- CDO Base Licensing (CDO-SEC-SUB) - is tied to CDO tenancy, one SKU count per CDO tenant. E.g. For the use of two CDO tenants, combine two SKU counts.
- CDO Device License - is tied to the number of devices managed by CDO. The SKU is tied to the Firewall platform and not the software running on it. e.g. The SKU for managing a Firepower 1010 appliance is L-FPR1010-P. It does not depend on whether it is running ASA or FTD.
- Security Analytics and Logging (Optional)- enables cloud logging and is charged based on the volume of logs stored in the cloud. It also has add-on tiers where apart from storing and viewing the logs, additional behavioural analytics can be applied using the Secure Cloud Analytics integration. More ordering info about cloud logging is available here.
The above licenses are not tied to Cisco Smart Licensing.
- Firewall Feature Licenses (Optional)- are the familiar Threat, Malware and Control feature licenses on the Secure Firewall. More info is available in the Licensing Section of the Configuration Guide.
More buying information is available in the Ordering Guide.
Reference Docs
- cloud-delivered FMC Configuration Guide
- Firewall Migration Tool
- Cisco Defense Orchestrator Docs
- What's New in cloud-delivered FMC
Demo Resources
- Always-On Demo in dCloud (Cisco Internal and Partner access)
- Secure Firewall Youtube Channel
Updated almost 3 years ago
