MITRE Information in Malware Events
Overview of MITRE ATT&CK Framework on Cisco Secure Firewall
Introduction
This document describes the use of the MITRE ATT&CK Framework on Cisco Secure Firewall.
In release 7.3, MITRE Tactics, Techniques, and Procedures (TTPs) were added to Intrusion events in order to act on traffic based on the MITRE ATT&CK Framework. This enables administrators to view and handle traffic with more granularity by having the ability to group rules by vulnerability type, target system, or threat category.
Starting in release 7.4, the same MITRE TTPs can be leveraged for select Malware events.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) Framework is an extensive knowledge base and methodology that provides insights into the tactics, techniques, and procedures (TTPs) distributed by threat actors aiming to harm systems. ATT&CK is compiled into matrices that each represent operating systems or a particular platform. Each stage of an attack, known as "tactics", is mapped to the specific methods used to achieve those stages, known as "techniques".
Each technique in the ATT&CK framework is accompanied with information about the technique, associated procedures, probable defenses and detections, and real-world examples.
The MITRE ATT&CK framework also incorporates Groups to refer to threat groups, activity groups, or threat actors based on the set of tactics and techniques they employ. By using Groups, the MITRE ATT&CK Framework helps categorize and document behaviors. For example, FIN4, Metador, and Rocke are examples of MITRE Groups and their TTPs are mapped and described within the appropriate MITRE ATT&CK matrix.
Adding MITRE TTPs to Malware Events
Note
You must first configure a Malware & File Policy. See Malware and File Policy for additional information on configuration.
- Login to the FMC. Navigate to Policies > Access Control > Malware & File.
- In this example, the Block Malware policy is already configured and associated with an access control policy. Click the Pencil icon to bring up the policy editor page.
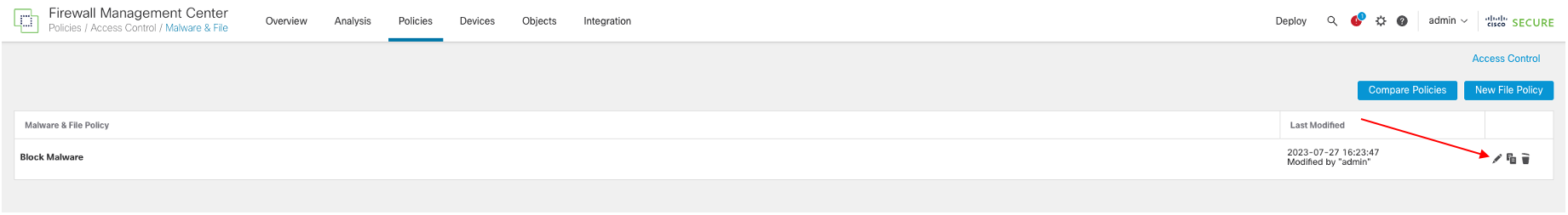
- In the policy editor page, click Add Rule.
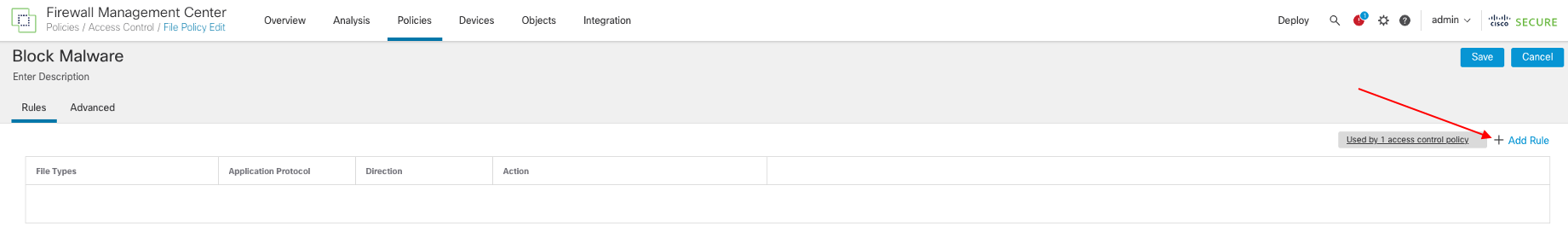
- In the Add Rule window, specify Action as Block Malware and enable the check box next to Local Malware Analysis.
Note
Local Malware Analysis must be enabled in order for MITRE TTPs to be populated for Malware events.
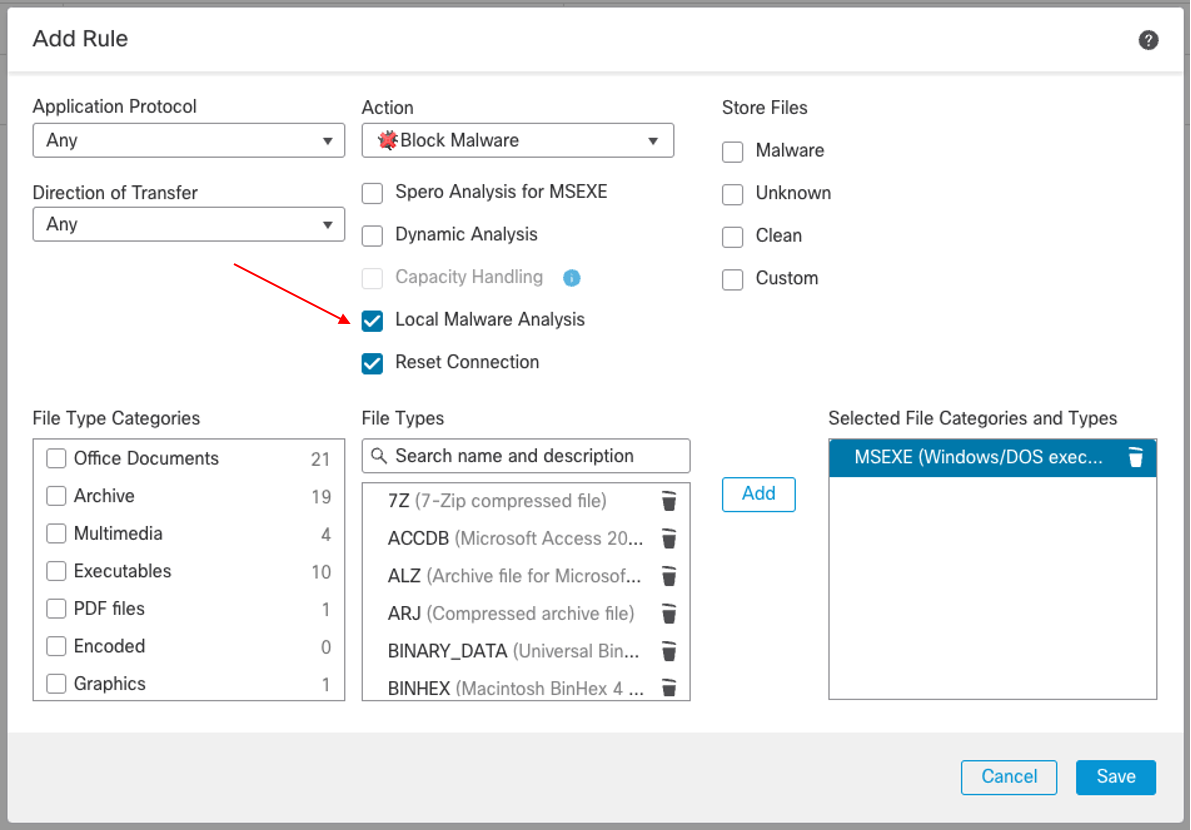
- Click Save in the Add Rule window.
- Save and Deploy your policy.
View Events
After configuring a Malware & File Policy, you can view your connection events that are identified as Malware with the associated MITRE TTP. Utilize the Unified Events Viewer (Analysis > Unified Events), and add an additional column to the default view. Use the steps below:
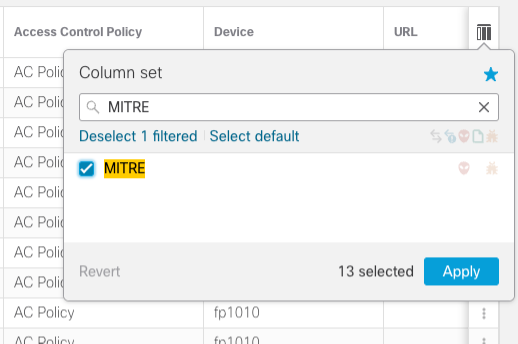
- Click the icon above the rightmost column to load the column selection menu.
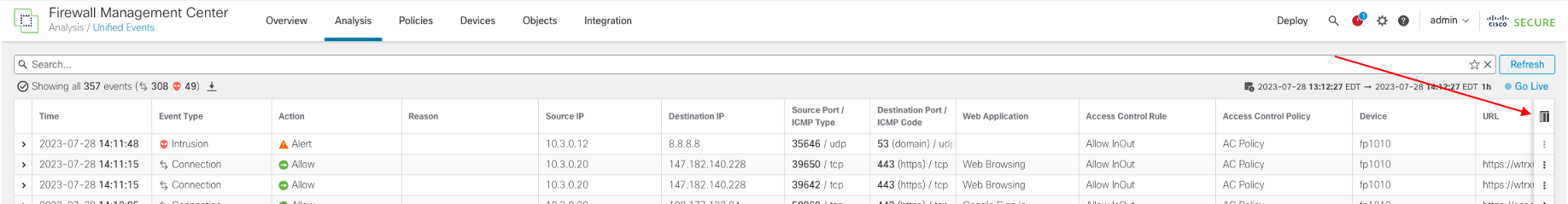
- In the Filter columns bar, type MITRE. Check the box next to MITRE and then click Apply to add the column to the Unified Event Viewer.
- The additional column is added to the right side of the screen, if it is not in the immediate view you may need to scroll to the right. In the example below, the MITRE column is sitting at the rightmost side of the screen.
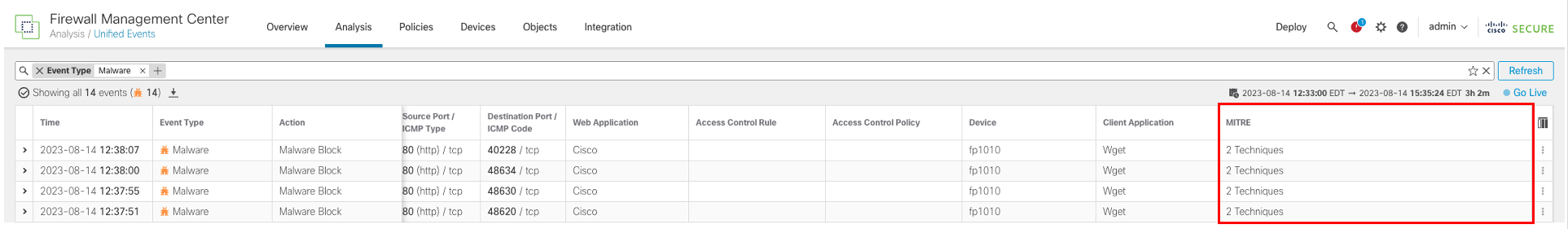
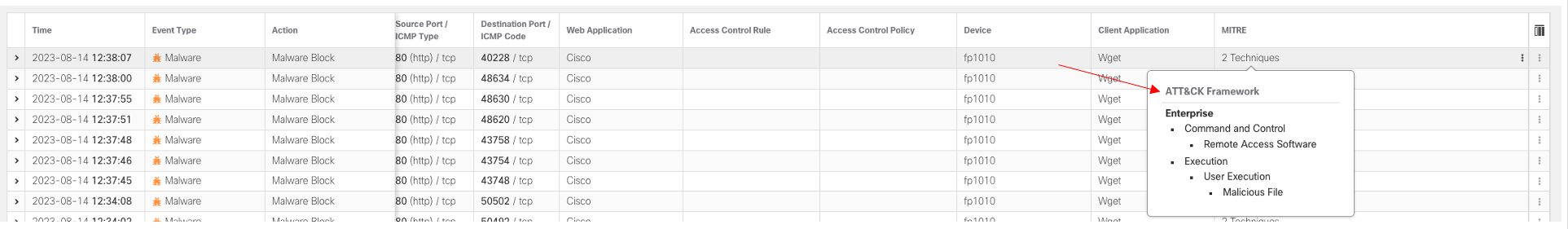
Some malware events will be associated with more than one TTP. Notice when there is a Malware event, the MITRE column is updated with the Technique(s) associated with the event. When multiple TTPs are assigned, clicking 2 Techniques will show a pop-up window noting the TTP in the ATT&CK Framework:
It is important to note that that for malware detected in network traffic, dispositions can change. Wherein, a file that was previously thought to be clean is now identified as malware or vice-versa. This is known as a retrospective malware event. When searching for these events it is a best practice to not search only on source and/or destination IP address. To see all associated events, use the Event Type with Malware as the search criteria and then to further narrow the results other search parameters can be used like MITRE, inclusion/exclusion filters, etc. In the example below, both the source and destination IP address columns are not populated and also in the Event Details, the Malware Event Type is indicated as retrospective:
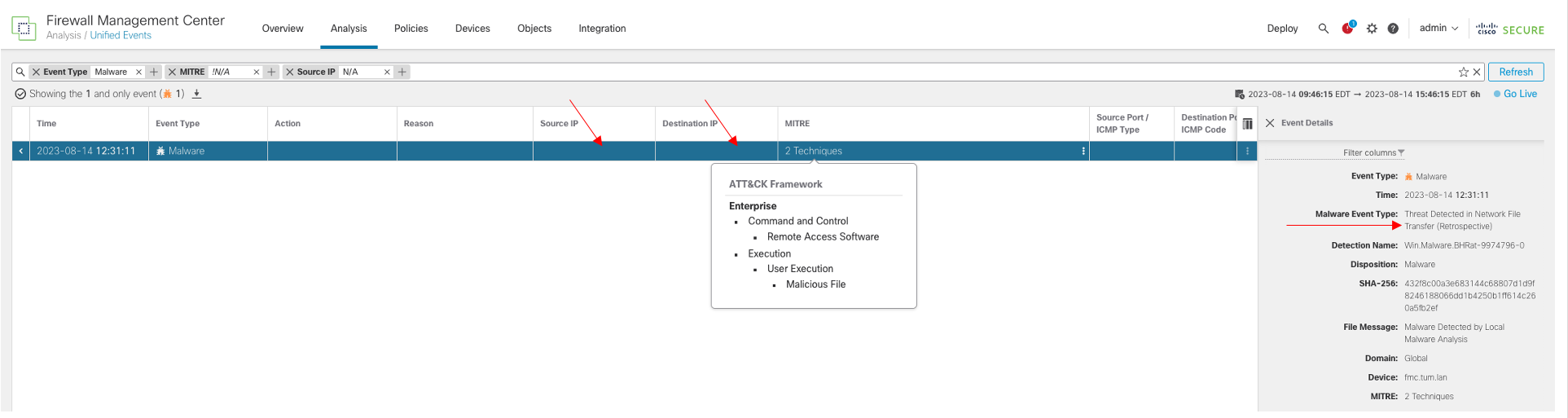
Retrospective Malware Event Example
Summary
This document provided an overview on how MITRE Tactics, Techniques, and Procedures (TTPs) are leveraged to provide context on select malware events. MITRE TTPs add additional context to those malicious traffic and present an additional layer to the Threat Detection capabilities in the Cisco Secure Firewall.
📚Additional Resources
Updated over 2 years ago
