Policy Analyzer and Optimizer
Policy Analyzer and Optimizer is a new feature that provides suggestions to improve the security and performance of managed firewalls. It does this by analyzing Access Control Policies to detect common design anomalies, including Duplicate Rules, Overlapping Objects, Expired Rules, and Mergeable Rules. It also provides an easy place for performing Policy Analysis of hit counts. As a cloud-delivered component of Cisco Secure Firewall Management Center, Policy Analyzer and Optimizer's capabilities will continue to expand, providing even greater value for customers.
Prerequisites and Limitations
- Supported on Firewall Management Center 7.2 or later. Firewall Management Center 7.6 or later is recommended, as it enables integrated cross-launch to Policy Analyzer and Optimizer from Firewall Management Center.
- Firewall Management Center must be integrated with Cisco Security Cloud. (For versions prior to 7.6, the Firewall Management Center interface will refer to this as SecureX integration.)
- Any Firewall Threat Defense device which is managed by a supported Firewall Management Center can have its corresponding Access Control Policy analyzed by Policy Analyzer and Optimizer.
Enable the Feature
To enable Policy Analyzer and Optimizer on Firewall Management Center 7.6, navigate to Integration > Cisco Security Cloud and check the box for Enable Policy Analyzer and Optimizer. Click Save to apply.
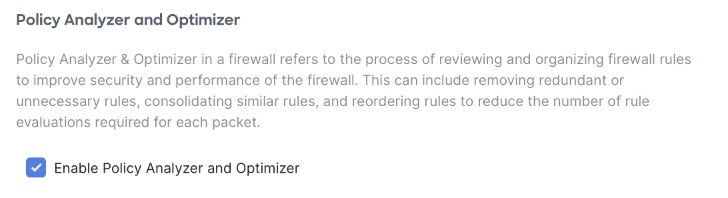
Ensure that Policy Analyzer and Optimizer is enabled by checking the state of the checkbox above. This feature is enabled by default when Management Center is connected to Cisco Security Cloud (or SecureX for version 7.2 through 7.4).
Accessing Policy Analyzer and Optimizer
As a cloud-delivered feature, Policy Analyzer and Optimizer lives within Security Cloud Control. The feature can be accessed either directly from within Security Cloud Control, or via a cross-launch from Firewall Management Center.
Accessing from Security Cloud Control
-
From within Security Cloud Control, navigate to Insights > Policy Analyzer and Optimizer.
-
If you have multiple Firewall Management Centers, select the desired one from the Showing policy for drop-down menu.
-
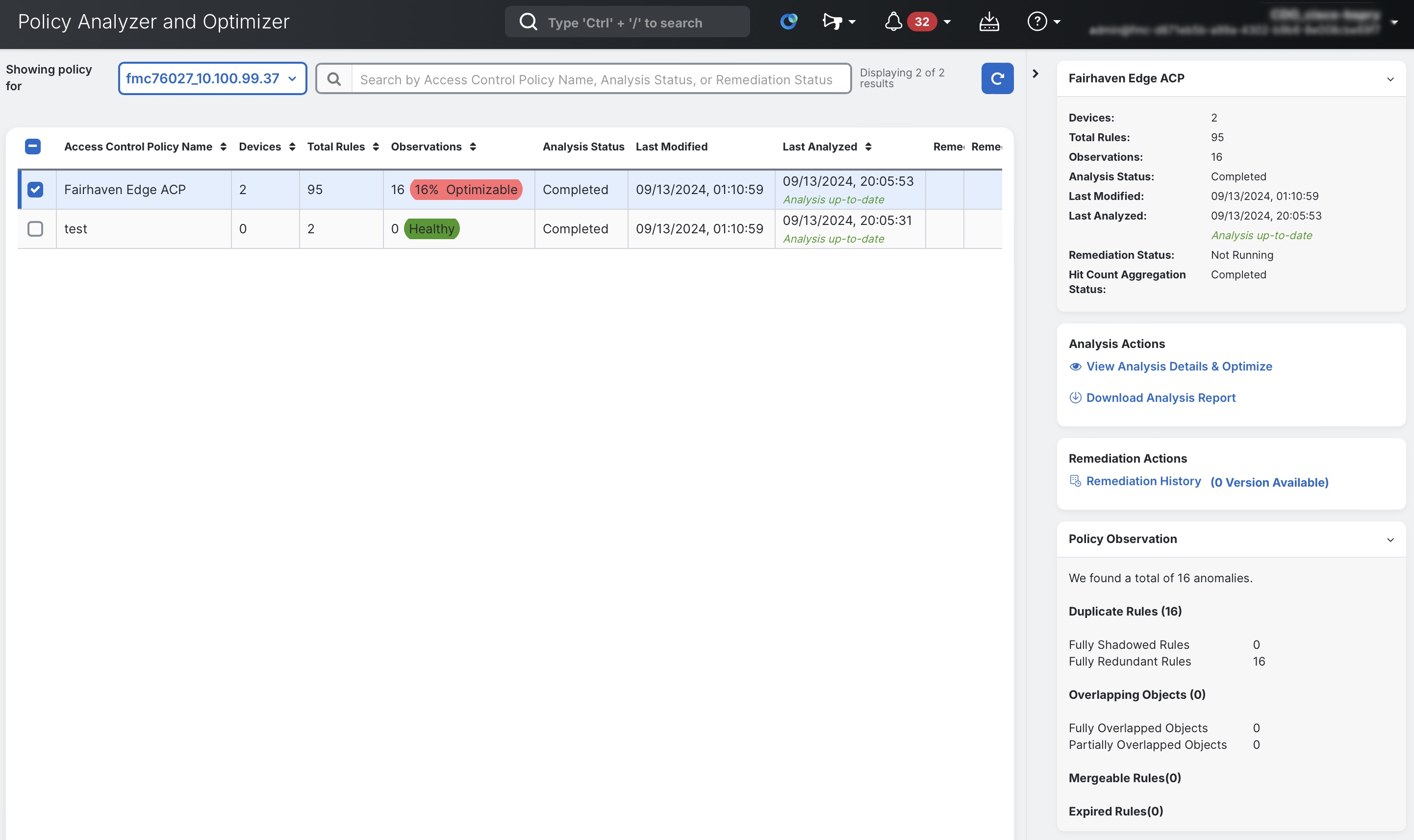
A list will display all Access Control Policies on the selected Firewall Management Center. Each policy in the list displays its total rule count and some details about the policy analysis. When selecting an Access Control Policy, a right sidebar appears displaying some additional details about the Policy Observations.
-
To enter the full analysis view for the selected policy, in the right sidebar click View Analysis Details & Optimize.
Accessing from Firewall Management Center
On Firewall Management Center version 7.6, you can also cross-launch directly into Policy Analyzer and Optimizer.
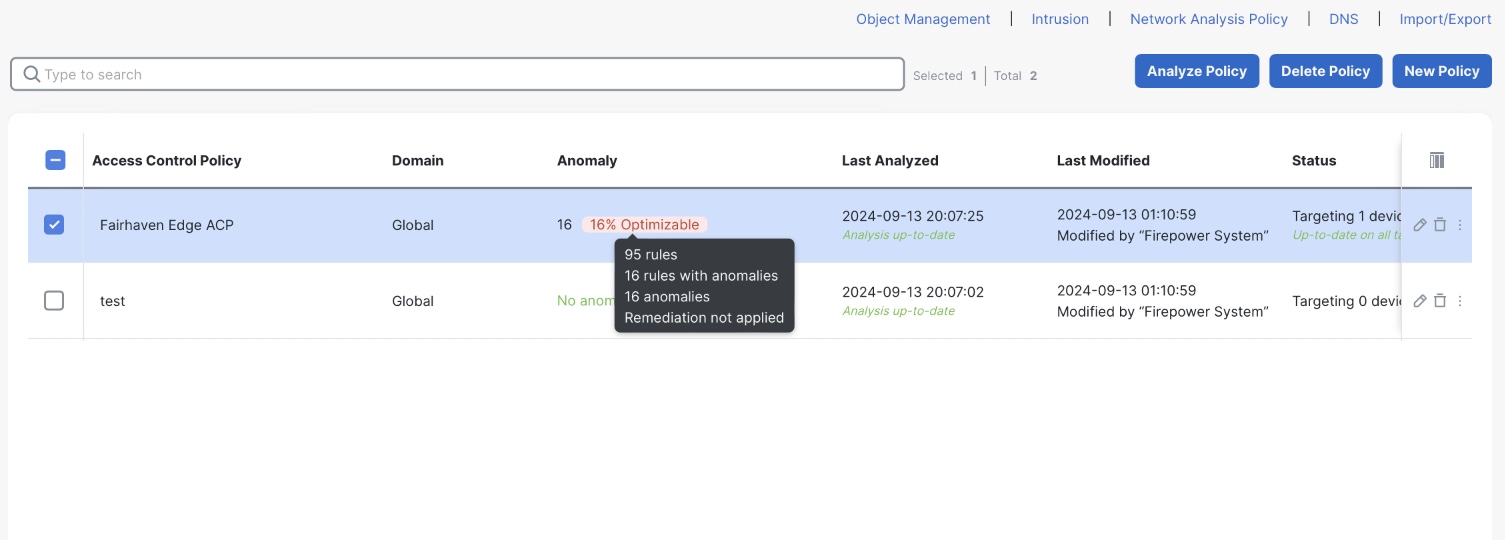
- From Firewall Management Center, navigate to Policies > Access Control. This screen displays a listing of all Access Control Policies on the Management Center. For each policy, there are additional details displayed about Anomalies found within the policy, the date last analyzed, etc. Hovering over the Anomaly column displays additional details about anomalies found.
-
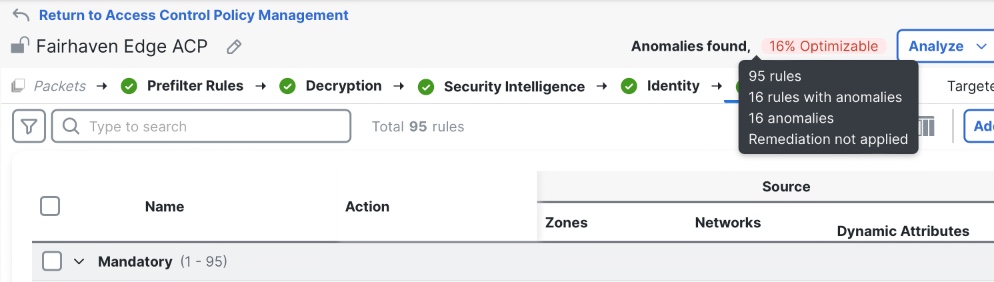
Click on the policy name of a desired policy, or click the pencil icon to enter the policy editor. From within the policy editor the same Anomaly details can be seen.
-
To cross-launch into Policy Analyzer and Optimizer, click on the Anomaly field from either the Access Control Policy list page, or from the individual Access Control Policy editor screen. (In the screenshots above, this is the field that appears as 16% Optimizable.
Using Policy Analyzer and Optimizer
The first tab within Policy Analyzer and Optimizer's policy-level analysis is a Summary tab, highlighting how many rules match each of the highlighted anomaly types. There are also charts making it easy to see overall ruleset health. Scrolling down further, a Hit Count summary is shown, highlighting potentially dead rules, as well as top-hit rules.
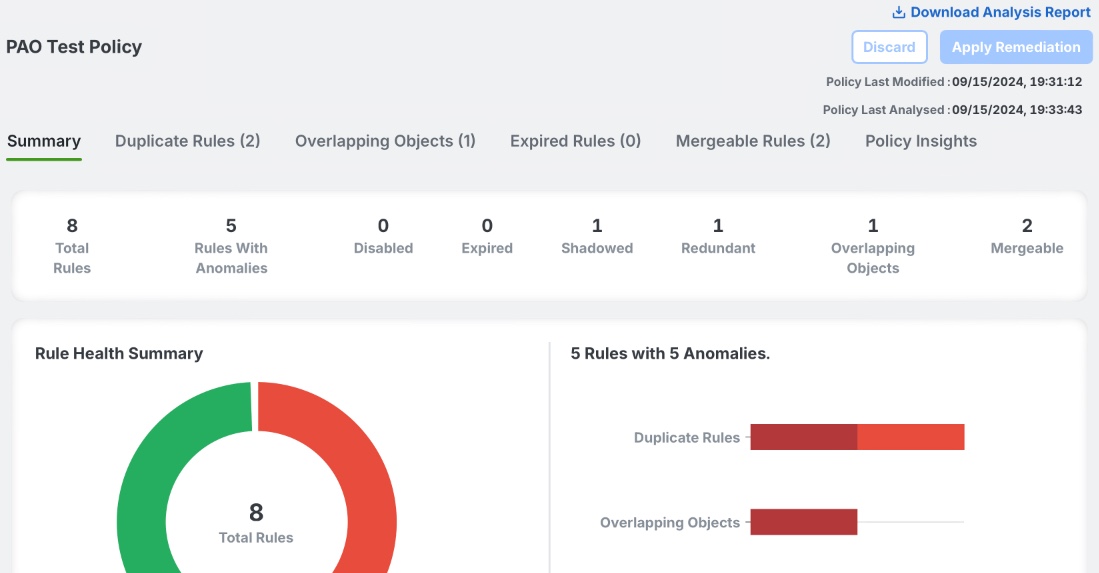
Summary view
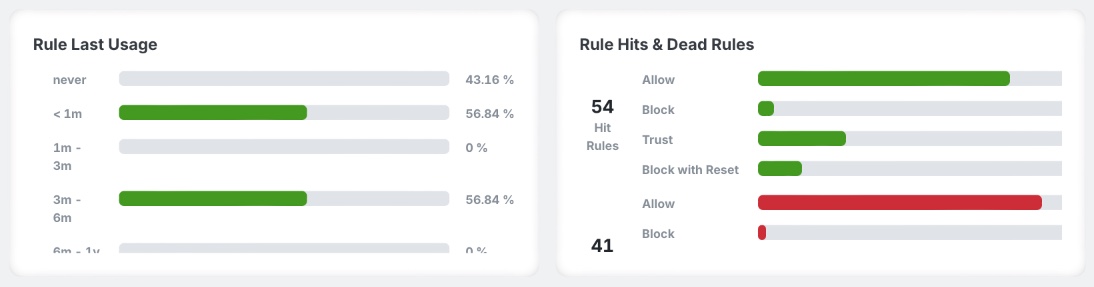
Summary view, showing Hit Counts
Duplicate Rules
The Duplicate Rules tab highlights rules which duplicate the functionality of another rule in policy, such that they are not needed for proper traffic evaluation. There are two different types of duplicate rules highlighted by Policy Analyzer and Optimizer: a Fully Shadowed Rule is one which will never evaluate within policy because the traffic will always match the criteria of a higher rule in the policy. A Fully Redundant Rule is one whose criteria is a subset of another rule below in the policy. It is generally possible to remove either type of duplicate rule with no change in firewall traffic evaluation. Removing duplicate rules also improves performance as the effective policy running in firewall memory is reduced in size.
Below are examples of Fully Shadowed and Fully Redundant rules, as highlighted by Policy Analyzer and Optimizer.
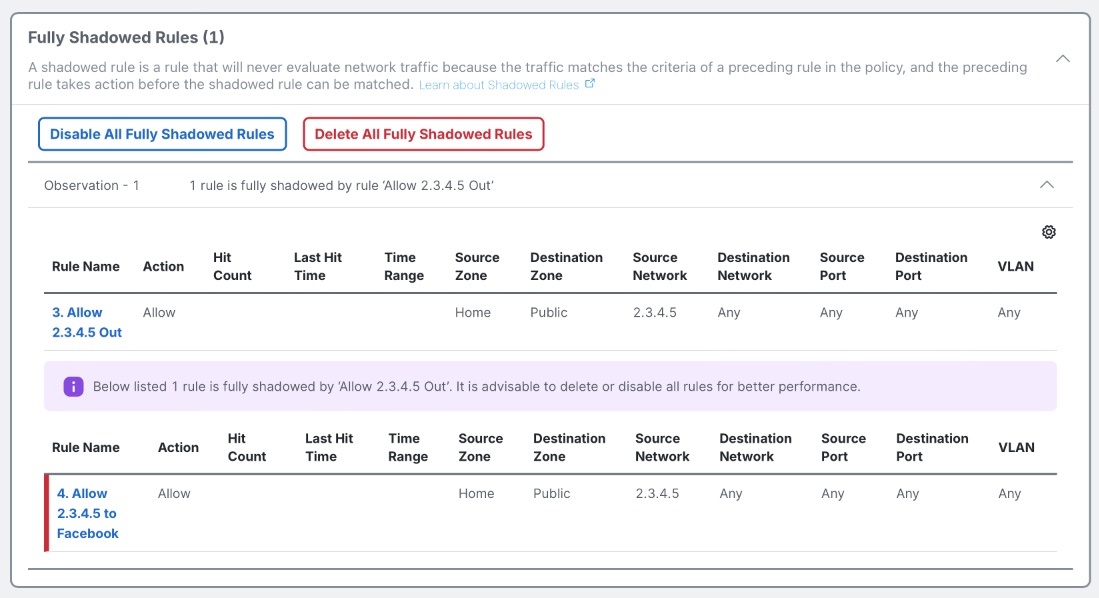
Fully Shadows Rules view
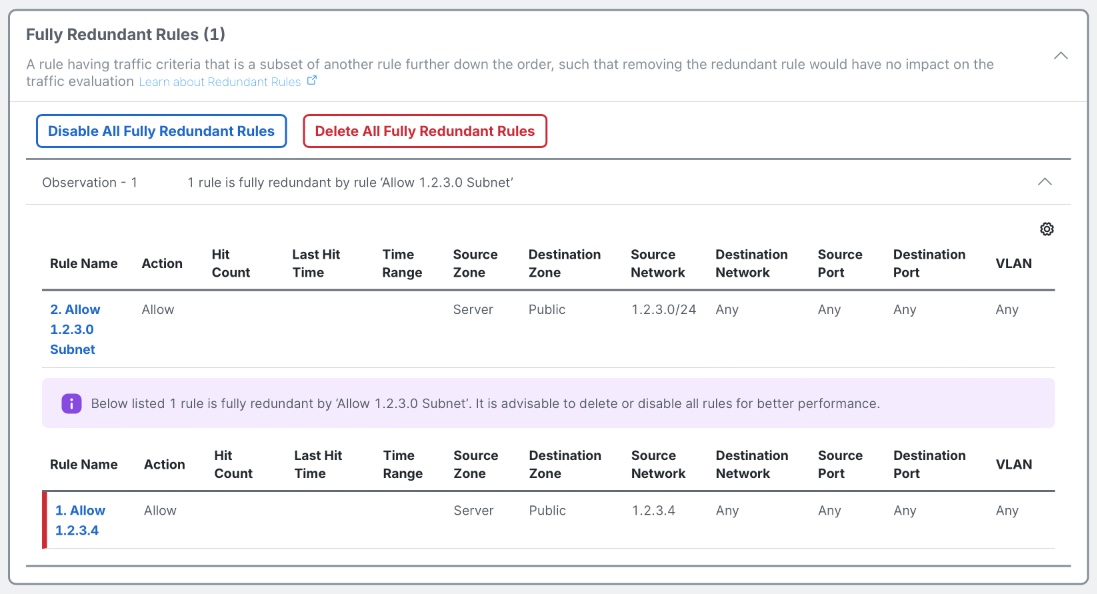
Fully Redundant Rules view
Overlapping Objects
When creating an Access Control rule, it is possible to add multiple objects which overlap one another within the same set of rule criteria. For example, entering a Network Object defined as 1.2.3.0/24 would fully overlap with a Host Object defined as 1.2.3.4. The rule's definition can be made more concise by removing the unnecessary object (in this case 1.2.3.4), which can also benefit firewall performance.
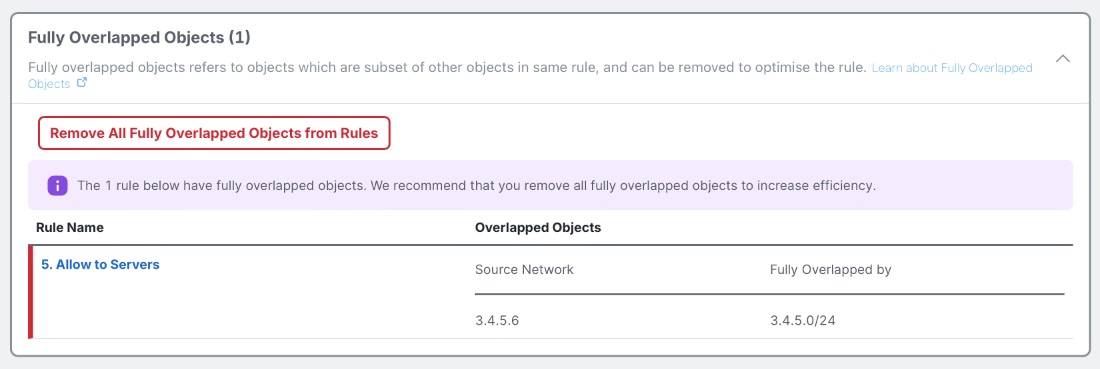
Fully Overlapping Objects view
Expired Rules
If an Access Control rule is defined with a Time Object which sets an end date, the rule expires after the end date has passed and effectively acts in the same manner as a Disabled Rule, while still being compiled into the running firewall configuration. Disabling and removing Expired Rules improves firewall performance and is also a good maintenance task if the rule will not be used again.
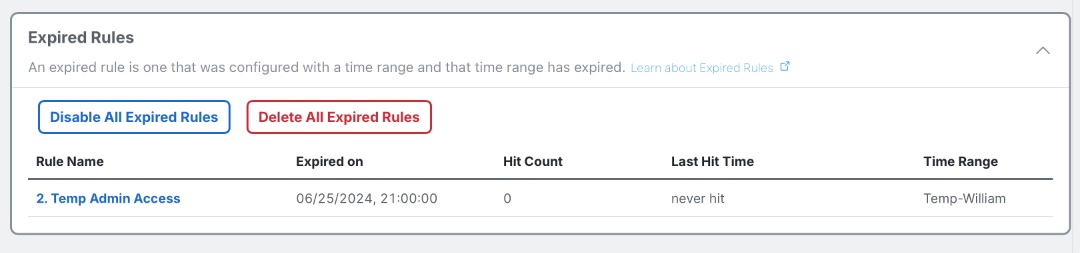
Expired Rules view
Mergeable Rules
In many cases, several Access Control rules can exist which do the same thing for multiple sources or destinations. For example, there might be a rule blocking access to Social Media for multiple departments, each within their own Access Control rule. It is often possible to merge these rules into a single rule, combining the multiple source or destination objects into a single rule. (In the preceding example, all departments which need Social Media blocked can be named in a single Block rule.)
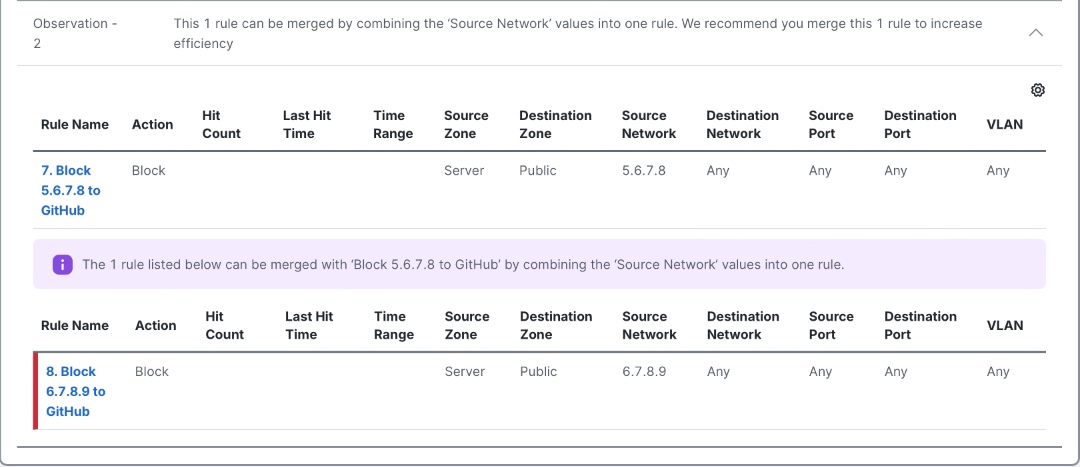
Mergeable Rules view
Hit Counts
Under the Policy Insights tab, a user can get insights into the Hit Counts of their firewall, filtering by time to understand which rules are hit often, which rules have not been hit during a certain lookback, and which have never been hit at all. Disabling and removing dead rules can improve firewall performance and is a good maintenance practice.
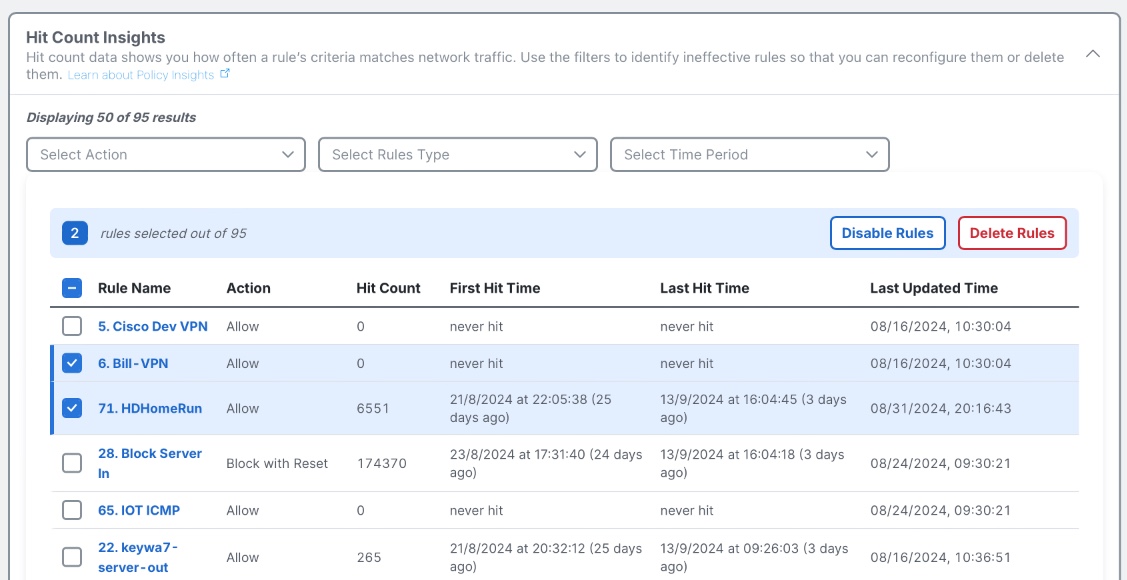
Policy Insights - Hit Counts Insights
Remediating Anomalies
Policy Analyzer and Optimizer makes it easy to remediate highlighted anomalies. Within each of the sections reviewed above, there are buttons to quickly perform remediation:
- Duplicate Rules can quickly be disabled or deleted.
- Overlapping Objects can be removed from rules in which they appear.
- Expired Rules can be quickly disabled or deleted.
- Mergeable Rules can be merged.
- Individual Access Control rules can be disabled or deleted based on Hit Counts analysis.
It is considered a best practice to have Policy Analyzer and Optimizer disable rules instead of deleting them. Disabled rules can easily be re-enabled if needed in the future, and have the same firewall performance benefits as deleted rules.
When selecting Remediations to perform, it is possible to quickly remove any Remediations before applying them by clicking the Undo button that appears next to each selected one.
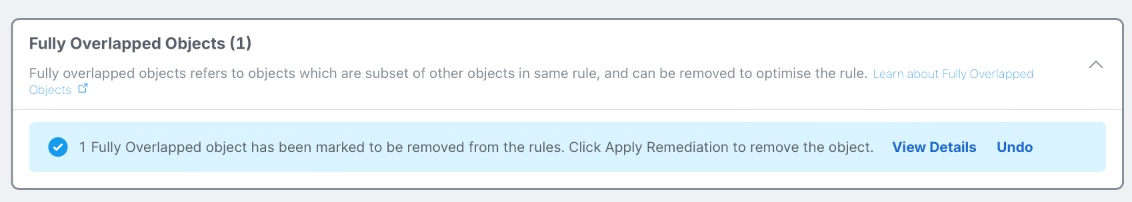
View after selecting to apply a Remediation
Once all Remediations from the various tabs have been selected to perform, you must click Apply in the top-right of the screen to proceed with the Remediations. It is also possible to abandon all Remediations by clicking Discard.
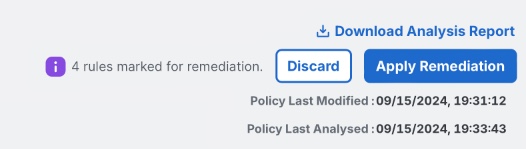
Applying or discarding the selected Remediations
When applying Remediations, status updates will appear on the screen as the Remediations are compiled and performed. The Firewall Management Center's Access Control Policy will be locked while Remediations are being performed to ensure no conflicts arise with other administrators that might attempt changes at the same time.
It is recommended to complete a full backup of the Firewall Management Center or Policy Export before performing remediations. After remediations are completed, it is not possible to revert them without restoring a backup.
When Remediations are complete, a confirmation message will appear on the screen. It is possible to download an Optimization Report which gives a high-level summary of the changes performed. Additionally, each modified rule in the Firewall Management Center has a comment added to describe the change that was performed.
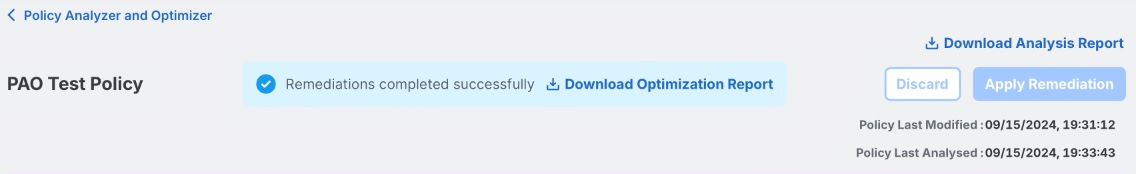
Remediations successful confirmation message
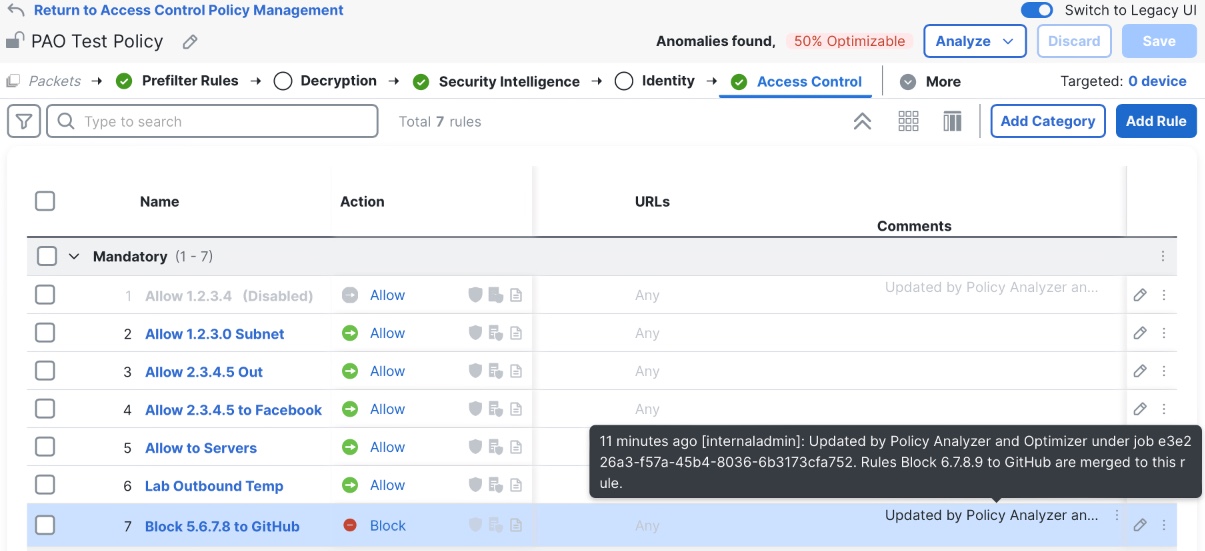
Rule comment example in Firewall Management Center
Updated 6 days ago
