Intelligent Decryption Bypass
Overview
Cisco Secure Firewall 7.7 introduces new features which simplify the process of setting up a successful decryption policy. The new Intelligent Decryption Bypass feature leverages the power of the Encrypted Visibility Engine (EVE), combined with insights from Talos Server Reputation to assess both client and server risk in real-time, allowing very low-risk connections to dynamically bypass decryption. Only Cisco can offer this combined client and server analysis, conserving system resources and improving security outcomes.
Intelligent Decryption can be enabled with a few clicks for new Decryption Policies, using our improved Decryption Wizard. For those with existing policies, or those wanting more fine-grained control over the specifics of this feature, a manual rule can be specified to customize the elements of this functionality.
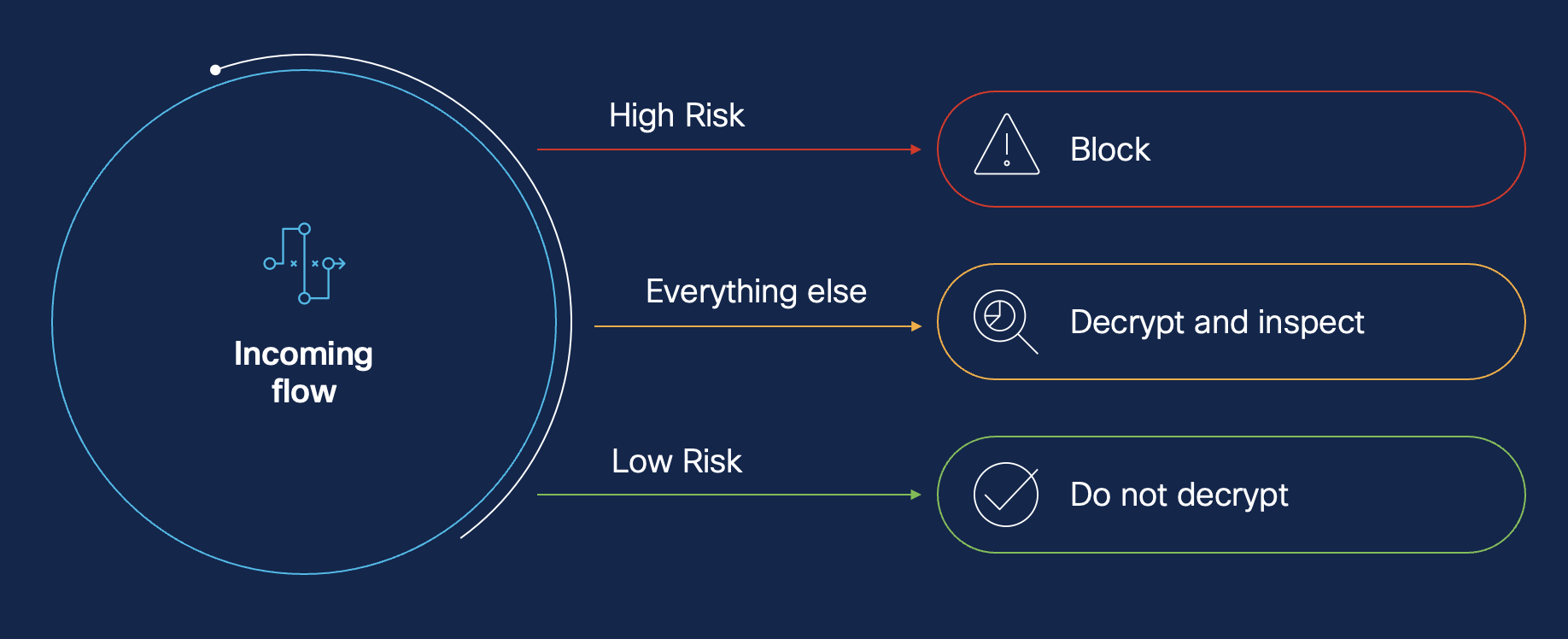
How Intelligent Decryption Works
Intelligent Decryption leverages two distinct components of the system to perform in-the-moment risk-based analysis, inspecting both the client and server. It's the combination of these two data points that allows Cisco Secure Firewall to confidently bypass decryption without risking your security.
Client Threat Inspection
The Encrypted Visibility Engine (EVE) performs advanced, Machine Learning-based analysis of the initiating client, supporting both HTTPS and QUIC. EVE combines the client request fingerprint with other contextual data points (such as the destination) to derive a Client Threat score, which can range from Very Low to Very High.
Note
The Encrypted Visibility Engine logs client threat scores under the EVE Threat Confidence field in Connection Events. These can be viewed by navigating in Firewall Management Center to Analysis > Unified Events and searching for HTTPS and QUIC events.
URL Reputation
Cisco Talos Intelligence Group performs extensive analysis of websites across the internet, as part of their URL Reputation and Categorization service (used by all Cisco products which perform URL filtering). Websites are assigned a Reputation score, which is an assessment of the trustworthiness of any given site. Reputation scores range from Trusted to Untrusted.
Putting it all Together
The Intelligent Decryption Bypass feature works by allowing the lowest risk connections to dynamically bypass decryption. These connections are defined as ones in which EVE has assigned a Client Threat score of Very Low and Talos has assigned a Server Reputation score of Trusted.
Configuring Intelligent Decryption Bypass
Prerequisites
The following prerequisites must be met in order to configure Intelligent Decryption Bypass:
- Your Firewall Management Center (FMC) and Secure Firewall (FTD) devices must be running version 7.7 or later. Intelligent Decryption Bypass is not available on earlier versions of the platform.
- The Secure Firewall device must have both the IPS and URL licenses applied.
- Encrypted Visibility Engine must be enabled:
- Navigate to the Access Control Policy linked to your Secure Firewall device.
- Navigate to Advanced Settings and find the Encrypted Visibility Engine settings at the bottom-right of the page. Ensure that the feature is enabled.
For New Decryption Policies
If you are just beginning your decryption journey, the simplest way to enable Intelligent Decryption Bypass is using the Decryption Policy wizard:
-
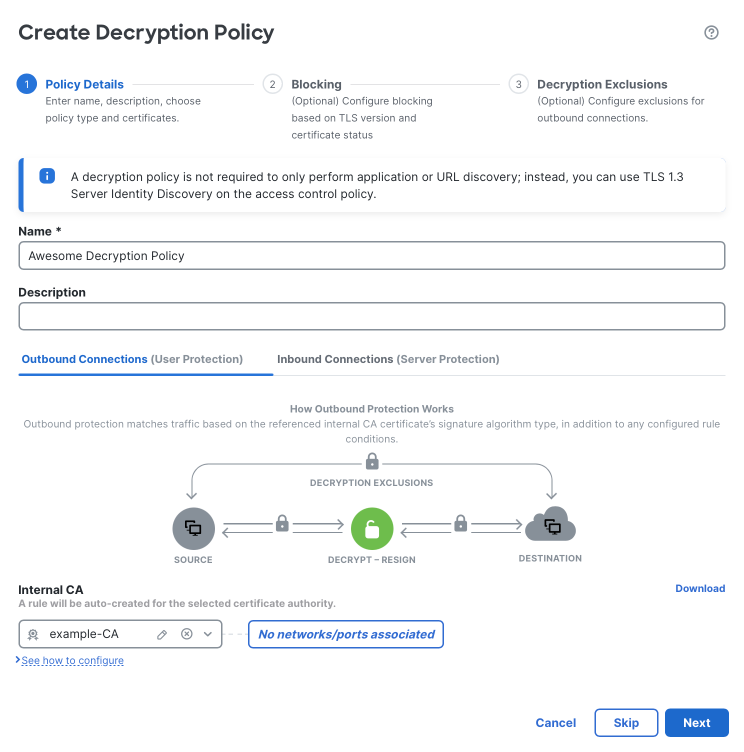
In the Firewall Management Center (FMC) navigate to Policies > Decryption and click Create Decryption Policy. This launches the Decryption Policy wizard.
-
On the first screen enter a Name and optionally a Description. Since this feature is specific to outbound traffic, also select an Internal CA. (If needed, you can also Upload or Generate a CA from this screen.) Click Next.
-
The following screen allows you to configure blocking for older TLS versions and certificate issues. Optionally enable these settings, and click Next.
-
The final wizard screen allows for the configuration of decryption exclusions, covering a variety of scenarios. At the bottom of the screen, check the box for Intelligent Decryption Bypass to enable the feature. When finished click Create Policy.
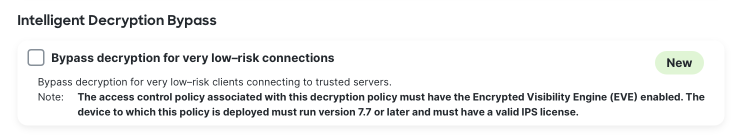
You are now left with an initial Decryption Policy which can be further tweaked or configured based on your business needs.
For Existing Decryption Policies or Advanced Users
If you already have an existing Decryption Policy and wish to enable this new functionality, follow the steps below:
-
In the Firewall Management Center (FMC) navigate to Policies > Decryption and locate your Decryption Policy. Click Edit (the pencil icon) to open the policy.
-
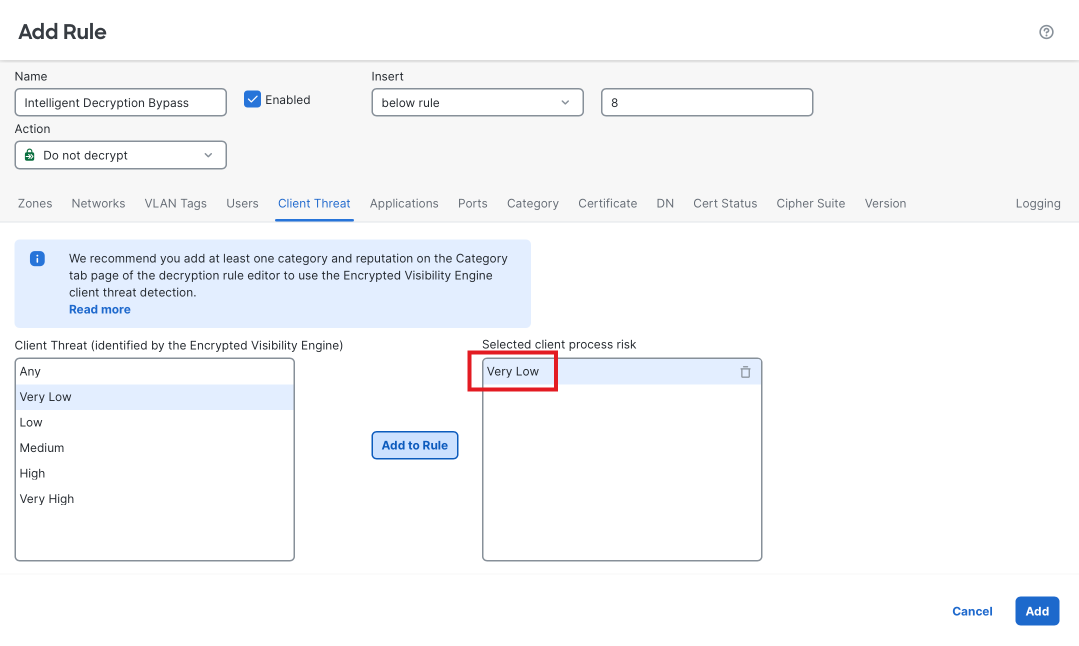
Within the Policy Editor, click Add Rule which pops up the Rule Editor. Give the rule a Name, ensure the Action is set as Do not decrypt.
-
Click on the Client Threat tab and set the Client Threat to Very Low. Click Add to Rule.
-
Click on the Category tab. Set the Category to Any (Except Uncategorized) and set the Reputation to 5 - Trusted. Deselect the checkbox which says Apply to unknown reputation. Click Add to rule.
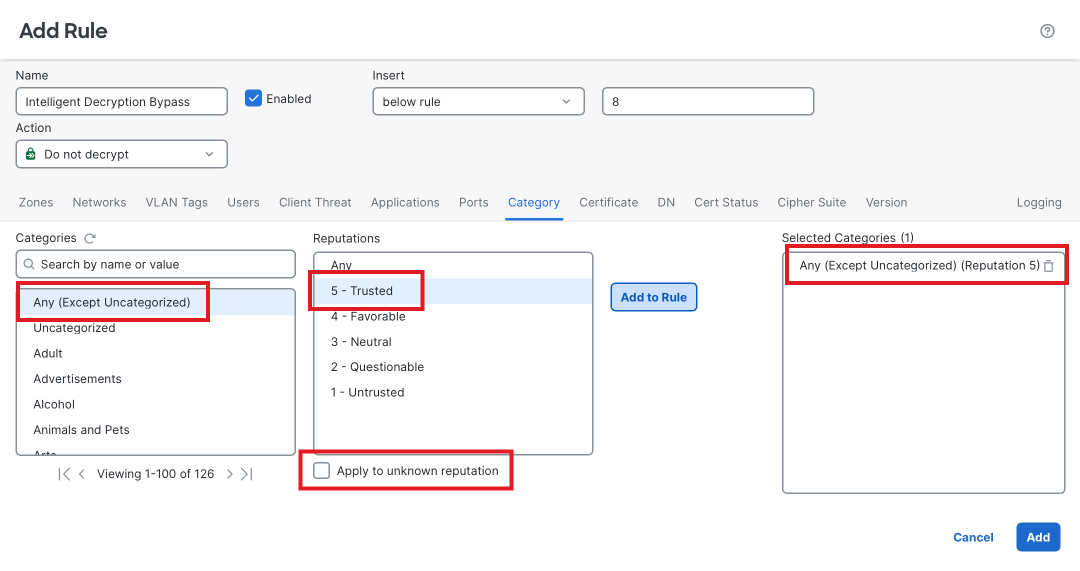
-
It is recommended, but not necessary, to also configure the Zones tab to set the directionality of your outbound traffic. Typically this might be from a Source Zone like Inside to a Destination Zone like Outside. (Your configuration might vary based on your unique firewall design.)
-
Click Add to add save the firewall rule. Click and drag the newly-created rule to place it appropriately within your policy. Typically this rule should be placed somewhere above your outbound Decrypt-Resign rules.
Note for Advanced Users
Intelligent Decryption Bypass is designed to allow easy bypassing for very low-risk connections. However, the underlying data points (Client Threat and URL Reputation) can be used within advanced policies in any way that an admin wishes to configure them. Here are some examples:
- A simplistic Decryption Policy might be designed to only decrypt Client Threat scores of Medium or High (while using Access Control to block those with a Very High risk outright)
- An admin might wish to only decrypt websites with a URL Reputation of Neutral or Unfavorable.
Please note, these are only suggestions and not specific policy recommendations!
Updated 8 months ago
