EVE Exception List
Introduction
Introduced in release 7.2, Encrypted Visibility Engine (EVE) identifies client applications and processes that utilize TLS encryption. It enables visibility and allows administrators to take action and enforce policy within their environments.
In release 7.4, enhancements were added to EVE to block malicious traffic based on threat score. Administrators can adjust the threat score required for EVE to block potentially malicious traffic. This means that as EVE analyzes traffic, it assigns a score based on the probability that the traffic is malware. If the incoming traffic is deemed to be malicious, then based on the threat score, EVE can be configured to block the connection.
However, scenarios like Internal Penetration Testing can create a need to bypass EVE's block verdict. Hence, in release 7.6, an EVE Exception List has been introduced which aims to ensure the continuity of connections and services when EVE’s block feature is enabled.
Configuration
The EVE Exception List allows administrators to bypass EVE’s verdict for blocking a connection based on the below attributes:
- Process Name
- Destination IP Address
The configuration of the EVE Exception List can be done in two ways - proactively and reactively.
Proactive EVE Exception List
-
Navigate to Policies > Access Control. Click on the pencil icon of the Parent Policy.
-
Go to More > Advanced Settings. Click on the Edit icon against Encrypted Visibility Engine.

Encrypted Visibility Engine Settings
-
Ensure that the below sliders are turned on:
- Recommended Settings
- Encrypted Visibility Engine (EVE)
- Use EVE for Application Detection
- Block Traffic Based on EVE Score
The block threshold configured in the below example is Very High, which means that traffic detected as malicious with Encrypted Visibility Threat Confidence Score 99% and above will be blocked. To add an exception to this block verdict, click on Add Exception Rule.
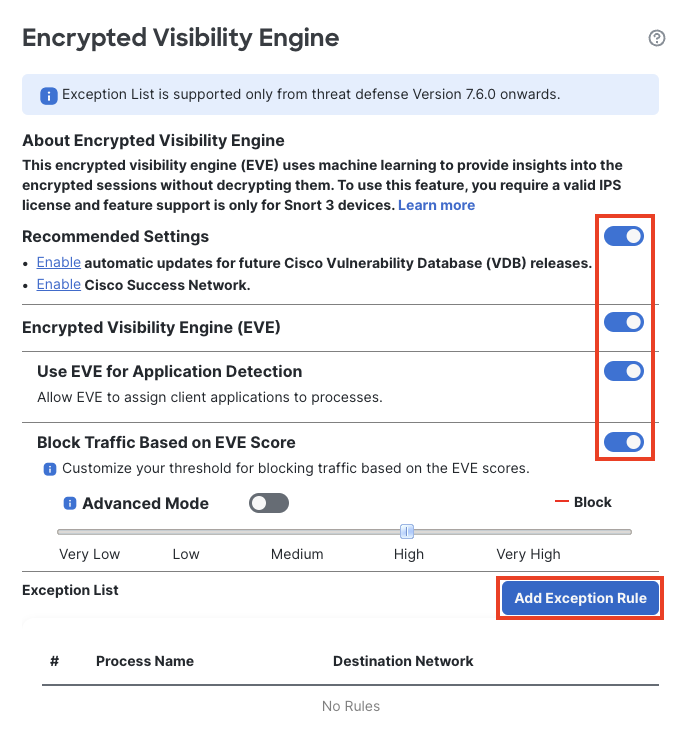
Encrypted Visibility Engine settings
-
Navigate to the tab Process Name. Type in the Process Name box "malware-adware" and click on Add to Process. Optionally, choose to enter a comment related to the EVE Exception Rule.
Note that the Process Name should exactly match the EVE Process Name seen in Unified Event Viewer. It is both case and space-sensitive.

EVE Exception Rule Configuration Pane
-
Click Save.
-
The Exception Rule gets added as shown below. Click OK.
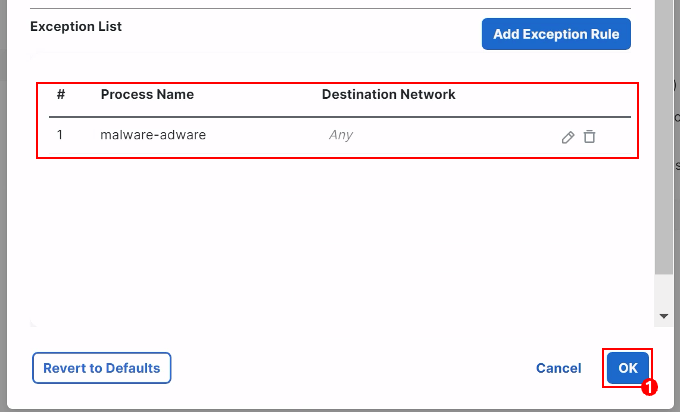
-
Click Save in the upper-right to save the changes to the Access Control Policy and then click Deploy > Deploy All to deploy the changes to the firewall.
Wait!
Wait for the deployment to complete before moving to the next step.
-
Navigate to Analysis > Unified Events. In the search bar filter with the value configured in the exception list -- i.e for the columns Encrypted Visibility Process Name.
- Encrypted Visibility Process Name: malware-adware
- Press enter.
- Click Apply to the right of the search bar.
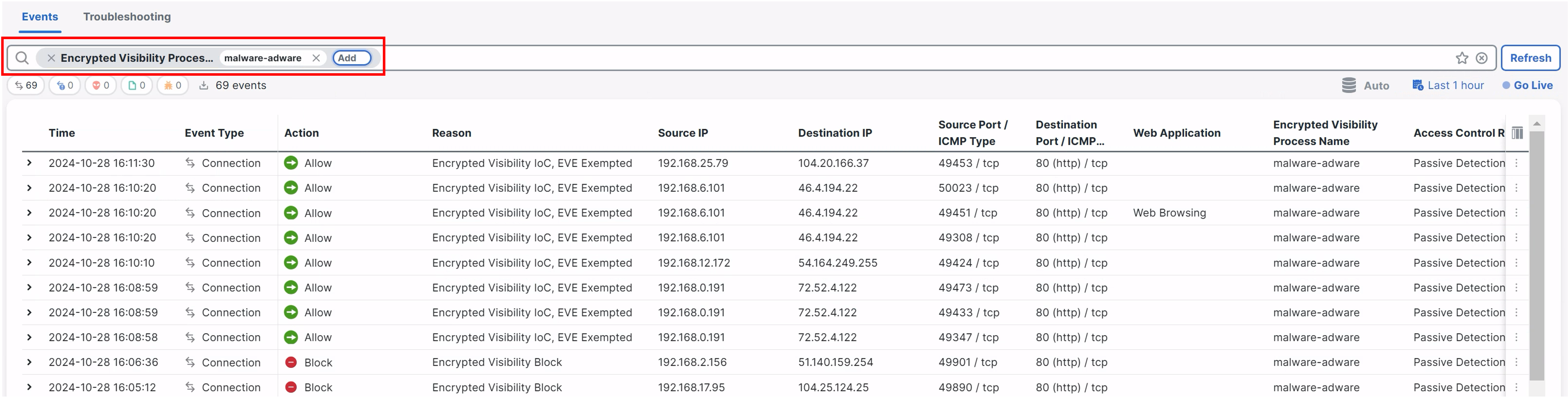
EVE Exempted Traffic in Unified Event Viewer
-
Click on > against the event to expand it.
-
Note that the traffic has been allowed even though EVE detected it as malicious with Encrypted Visibility Threat Confidence Score equal to 100%. The Reason is seen as EVE Exempted.
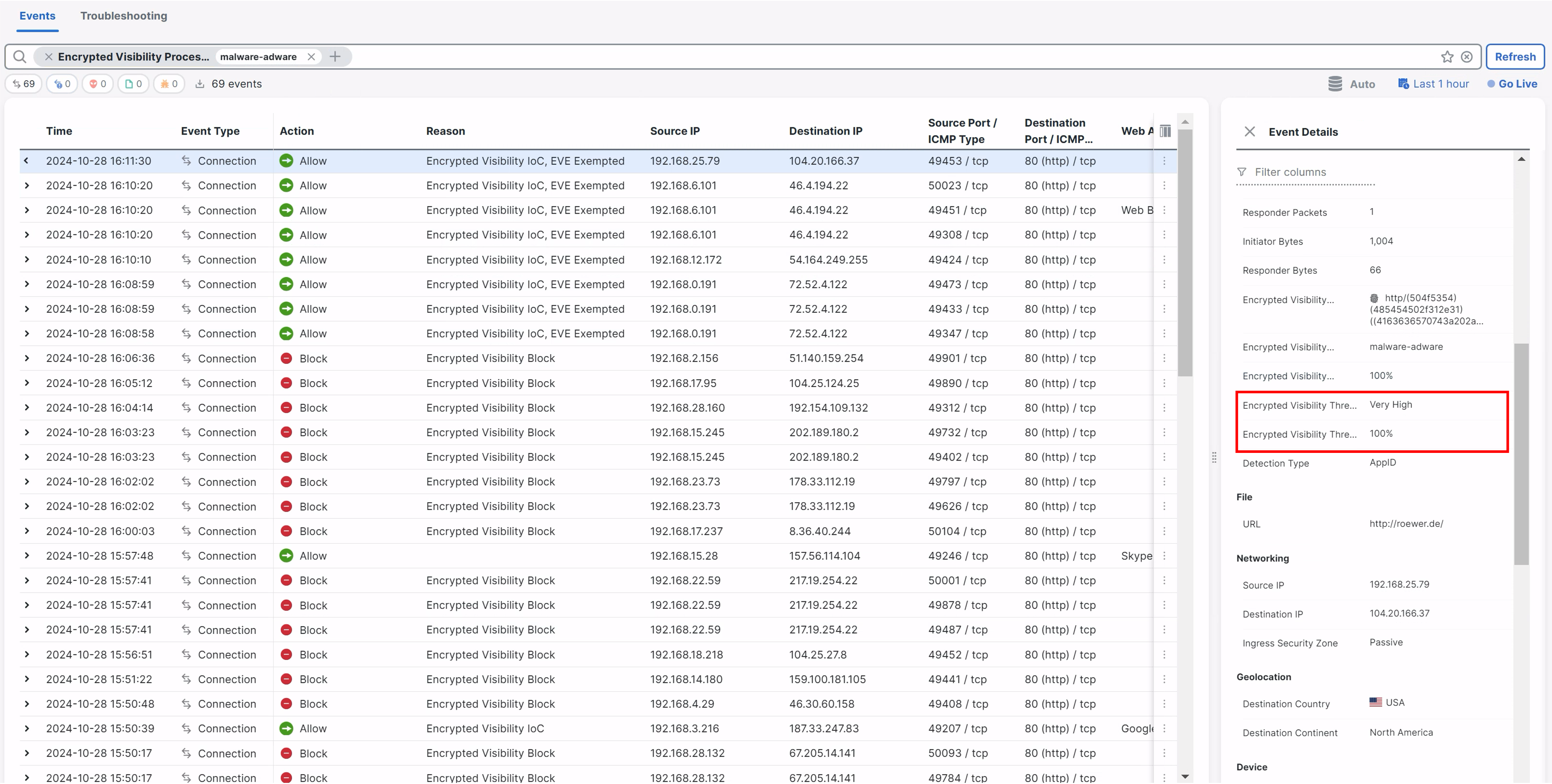
EVE Exempted Traffic in Unified Event Viewer
Reactive EVE Exception List
- Navigate to Analysis > Unified Events. In the search bar filter with Reason: Encrypted Visbility Block to view all the traffic blocked based on EVE block threshold.
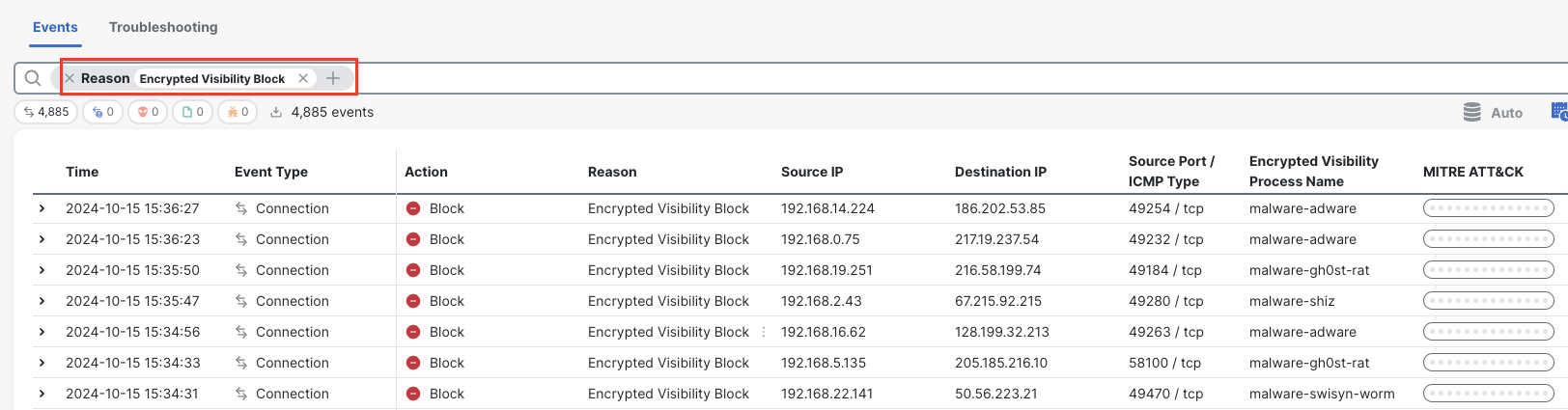
EVE Blocked traffic in Unified Event Viewer
- Click on the three dots against Encrypted Visibility Block for any event that requires an exemption from the EVE block verdict.
Note
For this lab exercise, choose any event for which EVE has blocked and given an Encrypted Visibility Block verdict in the Unified Event viewer.
- Click Add EVE Exemption Rule.
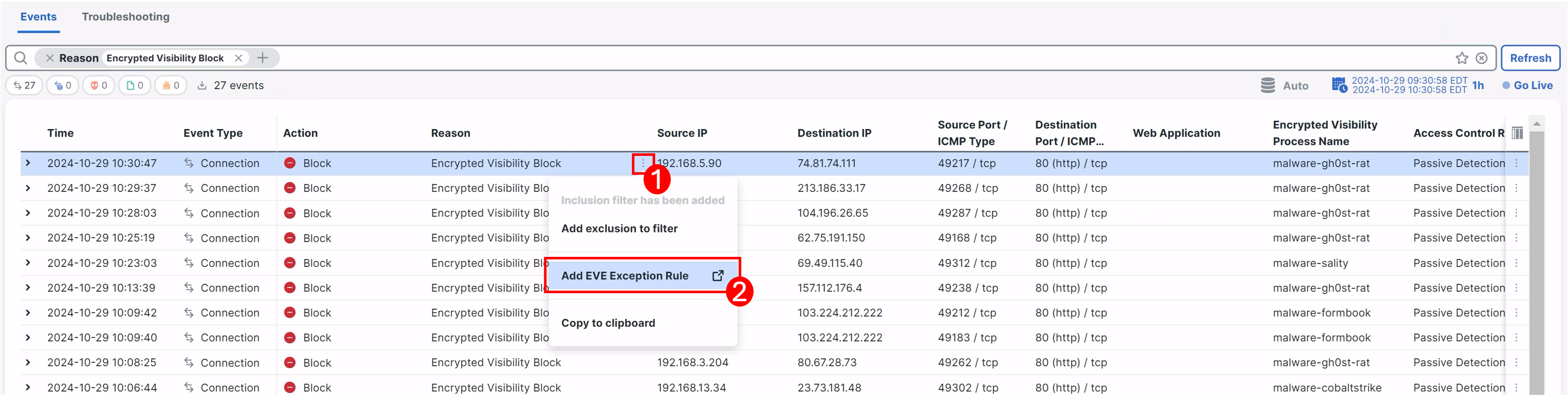
Adding EVE Exception Rule from Unified Event Viewer
-
This opens the Encrypted Visibility Engine settings page under the Access Control Policy mapped to the Device, with the newly added rule at the bottom of the EVE Exception List.
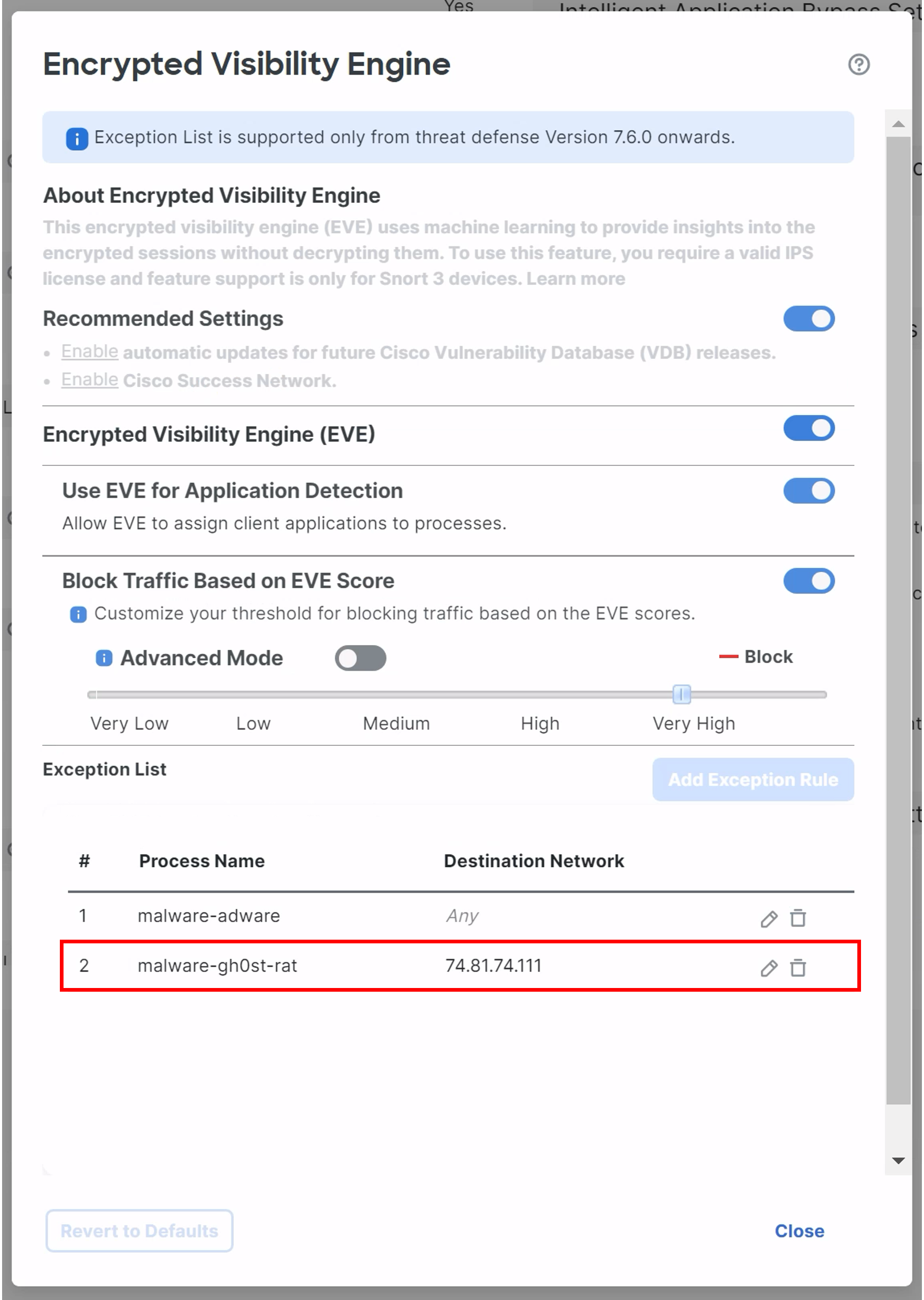
- Click on Close and then Save on the top right corner to save the changes to the Access Control Policy. Click on Deploy > Deploy All to deploy the changes to the firewall.
-
Go back to Analysis > Unified Events. In the search bar filter with the values in the exception list i.e. the columns Encrypted Visibility Process Name and Destination IP. The exempted event is now allowed through the firewall with the Reason: EVE Exempted.
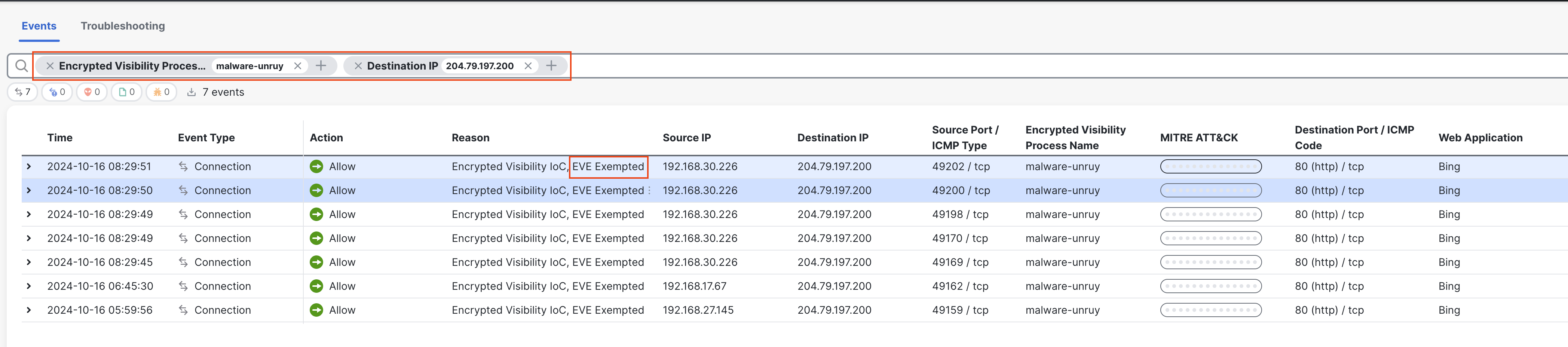
EVE Exempted traffic in Unified Event Viewer
Summary
With EVE Exception List, trusted networks and penetration testing scenarios can be easily exempted while continuing to block other malicious traffic with Encrypted Visibility Engine.
Tell us how we are doing
We are doing our best to ensure the scenarios in this lab guides are useful, clear and work as expected.
Please share your thoughts to help us improve or fix any problems you may run into..
Click here to provide your feedback or report an issue with this guide
Updated 11 months ago

